Overview of Cloudflare’s 2023 Q2 DDoS Threat Report
Cloudflare, a renowned internet security company, has recently released a comprehensive report concerning DDoS attacks (Distributed Denial-of-Service), elucidating the evolving methodologies employed in these attacks and presenting the latest statistical data for the second quarter of 2023.
For those interested, we have previously provided an overview of the first quarter report. It is accessible at the following link: Change of Tactic in DDoS: Attackers Now Use VPS for Improved Botnet Attacks
Rise of Darknet Parliament: Killnet, Anonymous Sudan, REvil Launch DDoS Attacks
The Darknet Parliament, consisting of infamous pro-Russian threat actors KillNet, Anonymous Sudan, and REvil emerged as the most prominent DDoS activity in the second quarter.
On June 16, 2023, they initiated a targeted campaign primarily focusing on European banking systems. This marked the beginning of a series of DDoS attacks targeting entities such as the European Investment Bank (EIB), SWIFT, the US Federal Reserve System, SEPA, IBAN, Wire, Wise, and the International Finance Corporation.
To delve deeper into the alliance, explore the background of its members, and understand the motive behind its formation, we invite you to read our Darknet Parliament blog.
The report highlights an alarming number of 10,000 DDoS attacks by the Darknet Parliament trio, launched against Cloudflare-protected websites in recent weeks.
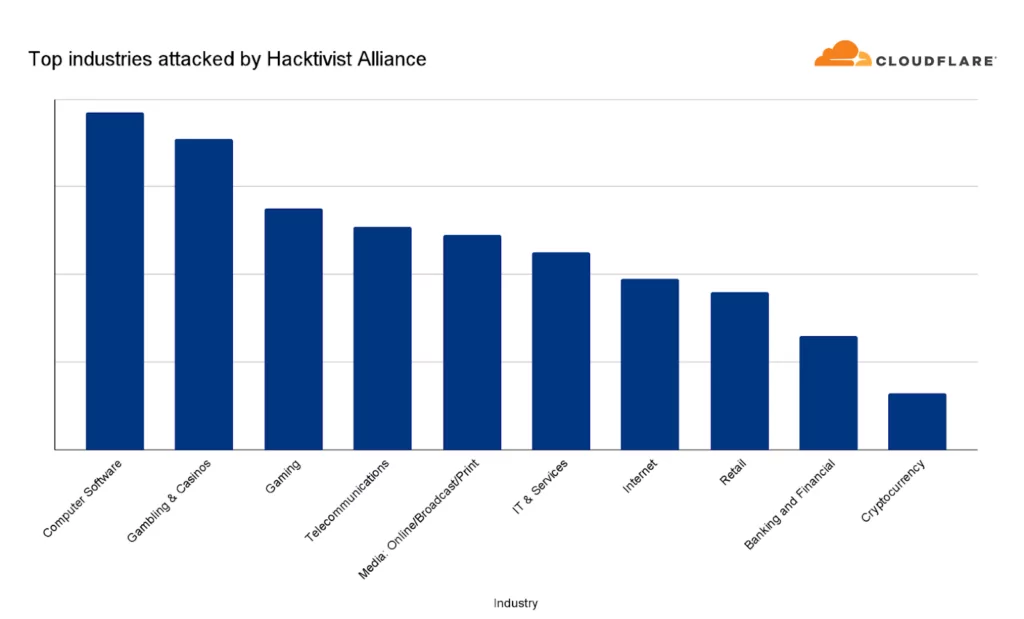
Contrary to the alliance’s claims, the report reveals that Banking and Financial Services websites ranked only ninth among the most attacked industries. It was observed that the top three sectors targeted by the alliance were the Computer Software, Gambling, and Gaming industries.
HTTP DDoS Attacks Have Increased in Q2
HTTP DDoS attacks have experienced a 15% increase in the quarter, even though there has been a significant 35% decrease year over year. These attacks specifically target HTTP Internet properties, such as websites and API gateways.
In recent months, there has been a concerning rise in highly randomized and sophisticated HTTP DDoS attacks. Notably, it seems that the threat actors orchestrating these attacks have intentionally tried to avoid mitigation systems by expertly mimicking browser behavior. Previously, this level of sophistication was primarily associated with state-sponsored threat actors. However, it is now apparent that cybercriminals have gained access to similar capabilities, showcasing the evolving landscape of security threats.
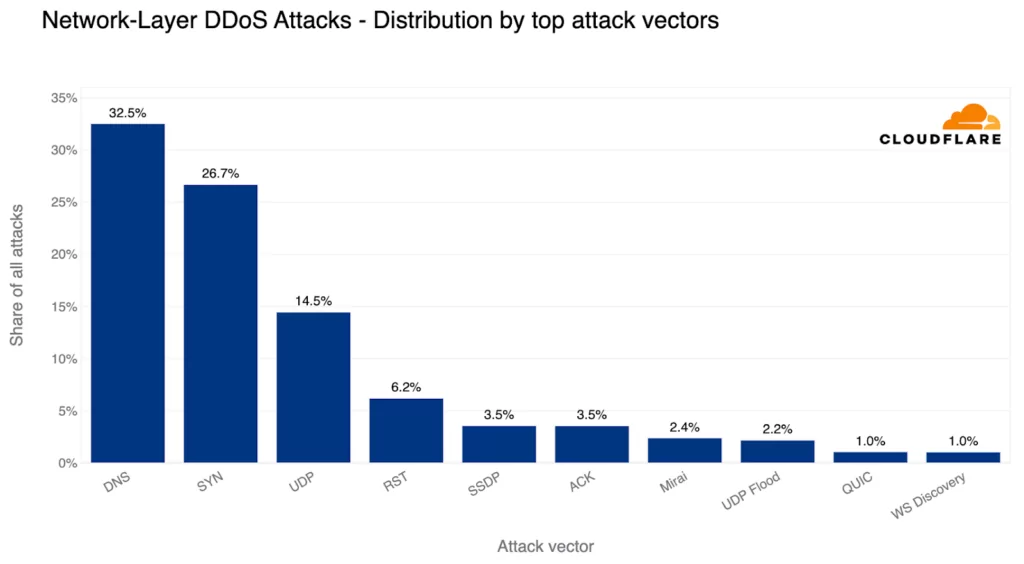
The Top DDoS Attack Vectors in Q2: DNS-based Attacks Are the Most Common
DNS-based DDoS attacks emerged as the predominant attack vector during the previous quarter, representing 32% of all DDoS attacks. In DNS-based DDoS attacks, malicious actors disrupt DNS servers, impeding the ability of machines to establish connections with targeted websites. Consequently, these websites become inaccessible to users.
Of particular concern is the increasing prevalence of DNS Laundering attacks. The DNS Laundering attack method disguises malicious traffic as legitimate traffic by channeling it through reputable recursive DNS resolvers, thereby evading detection and causing further complications. This type of attack presents significant challenges for organizations that run their own authoritative DNS servers.
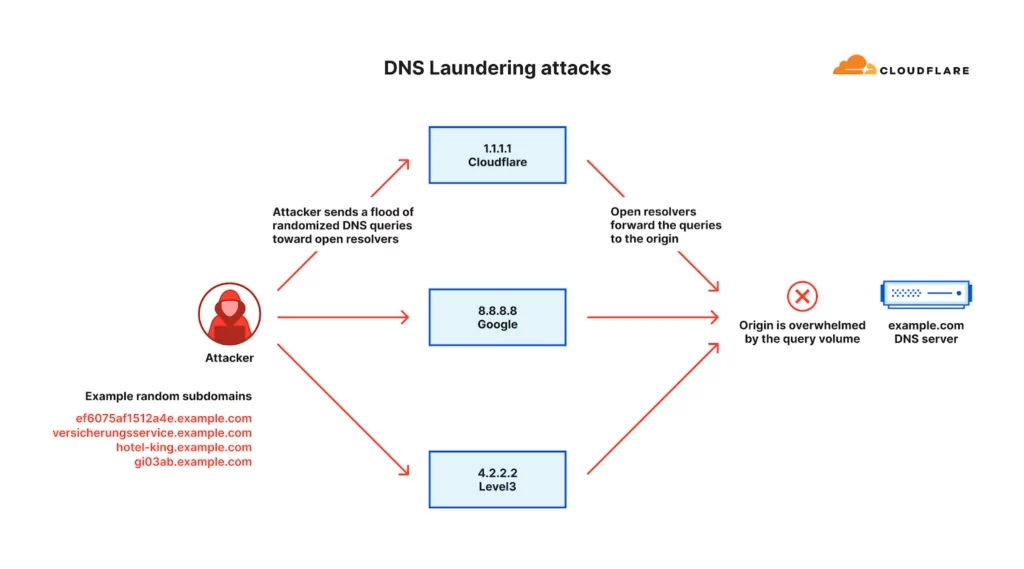
The report states that, from a security standpoint, DNS administrators cannot block the attack source because it includes reputable recursive DNS servers such as Google’s 8.8.8.8 and Cloudflare’s 1.1.1.1. It is also not possible to block all queries to the targeted domain because administrators would still want to access legitimate queries. These obstacles make it difficult to distinguish between legitimate and malicious queries.
Startblast DDoS Attacks on Mitel
In March 2023, a zero-day vulnerability (CVE-2022-26143) called TP240PhoneHome was disclosed in Mitel MiCollab. This flaw allows for UDP amplification DDoS attacks by reflecting and amplifying traffic off vulnerable servers.
In the past quarter, emerging threats like DDoS attacks leveraging TeamSpeak3 protocol increased significantly by 403%. Attackers target TeamSpeak servers to disrupt real-time multiplayer gaming communication, impacting team performance.
In this post, we mentioned the increasing occurrence of cyber attacks on the Entertainment Industry. Lately, prominent entities like RiotGames, Nickelodeon, and Razer, a gaming equipment company, have fallen victim to successful breaches carried out by threat actors. This suggests a noticeable rise in cyberattacks targeting organizations associated with the entertainment sector.
While HTTP DDoS attacks rose by 15%, network-layer DDoS attacks decreased by approximately 14% quarter-over-quarter (QoQ). The US was the primary source of HTTP DDoS attacks, followed by China and Germany.
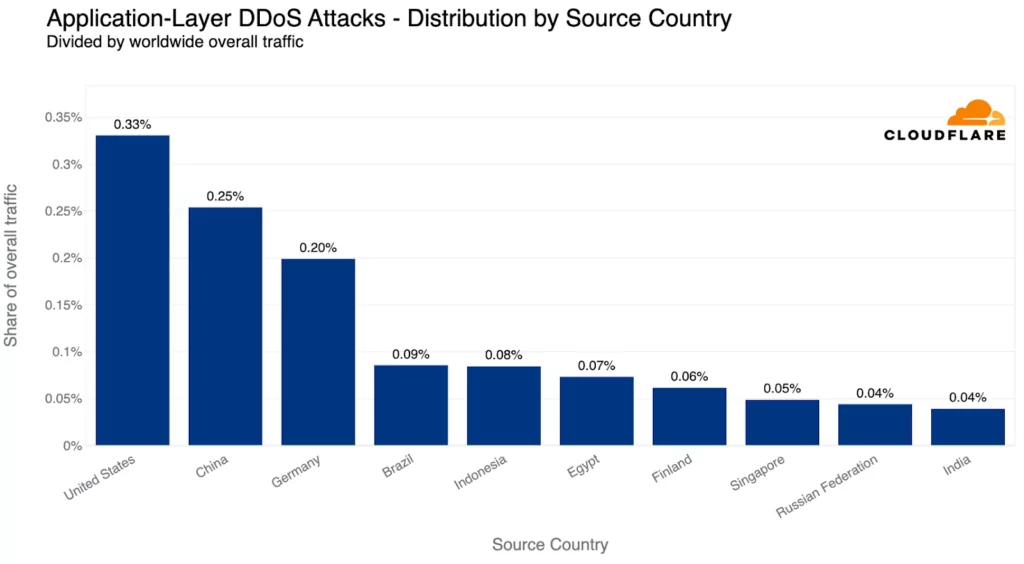
Countries with larger market sizes naturally attract more traffic and, as a consequence, face a higher risk of attacks. However, when normalized for traffic volume, Mozambique, Egypt, and Finland became the top three countries for the most relative HTTP DDoS attack traffic. Mozambique had nearly a fifth of its HTTP traffic involved in DDoS attacks.
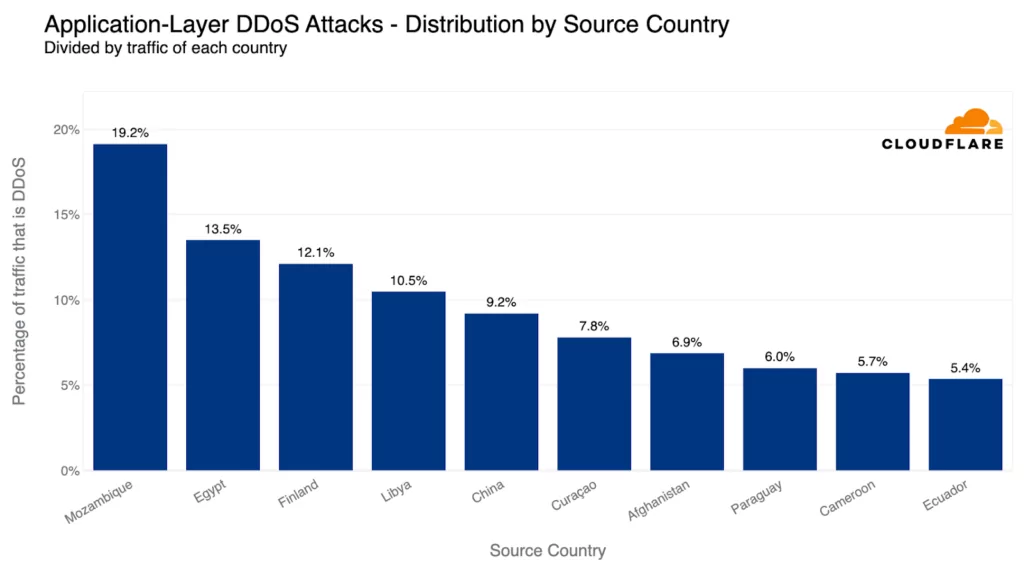
Vietnam continues to be the primary source of network-layer DDoS attacks for the second quarter in a row. The volume of attacks increased by 58% QoQ. More than 41% of all bytes received by Cloudflare’s Vietnam data centers were associated with L3/4 DDoS attacks.
DDoS Attack Trends by Industry and Region
In Q2, Cryptocurrency websites faced the largest amount of HTTP DDoS attack traffic, with a substantial 600% increase from the previous quarter.
Non-profit organizations were the most attacked when considering the relative amount of attack traffic compared to all traffic. HTTP DDoS attacks accounted for 12% of the traffic directed towards Non-profits. These organizations have faced an average of 67.7 million cyber attacks per day in recent months.
The Management Consulting industry became the most targeted with 18.4% of its traffic being DDoS attacks. The Internet networks of the Information Technology and Services industry were the primary target for L3/4 DDoS attacks.
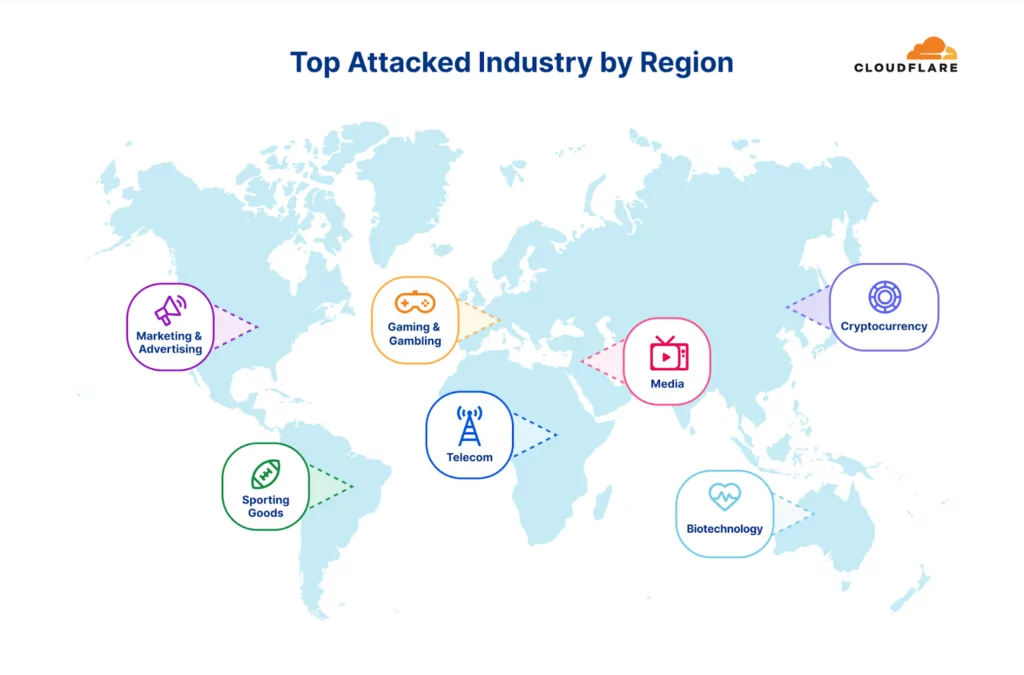
The top attacked industries varied by region, with Cryptocurrency websites being the most targeted worldwide, while different industries took the lead in specific regions.
In Africa, Telecommunications faced a higher number of attacks, while Cryptocurrency was the main target in Asia. Europe experienced more attacks on Gaming and Gambling sectors, Latin America on Sporting Goods, the Middle East on Media and Newspaper, North America on Marketing and Advertising, and Oceania on Biotechnology.
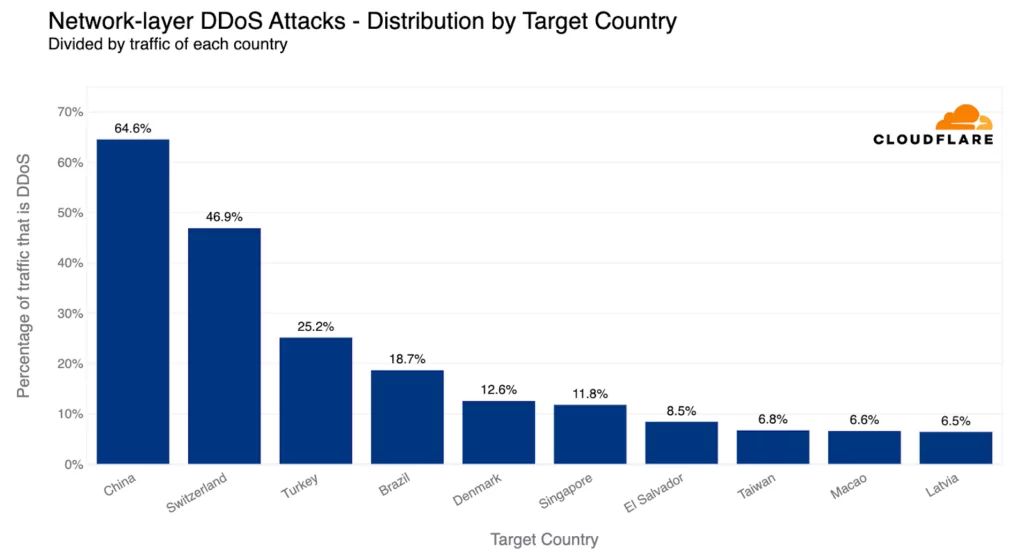
The US was the most attacked country when looking at the total volume of attack traffic, but Palestine emerged as the most attacked country when normalized per total traffic. Chinese Internet networks saw the highest proportion of malicious traffic, followed by Switzerland and Turkey.
Ransom DDoS (RDDoS) Attacks
Ransom DDoS (RDDoS) attacks involve malicious parties extorting money from individuals or organizations by threatening to launch a Distributed Denial-of-Service (DDoS) attack. The attackers may execute a DDoS attack and then demand a ransom to stop it, or they may send a ransom note threatening a DDoS attack as a means of coercion.
Ransom DDoS attacks are simpler for threat actors to execute compared to traditional Ransomware attacks. Unlike Ransomware attacks that rely on deceptive tactics and network breaches, Ransom DDoS attacks bypass these requirements. Reports of Ransom DDoS attacks decreased in the past quarter, with one out of ten respondents reporting being threatened or targeted by such attacks.
Free Services by SOCRadar Labs: DoS Resilience and Country Threat Landscape Report
SOCRadar Labs offers the DoS Resilience service, which provides website owners and network administrators with valuable information to evaluate the resilience of their systems against DoS (Denial-of-Service) attacks.
By utilizing the DoS Resilience service, you gain the ability to effortlessly assess the resilience of your domain or subnet against prevalent DoS attack types, including slowloris, amplification, and reflection attacks. Such assessment empowers you to proactively implement preventive measures, safeguarding the security and functionality of your system.
Check out the Country Threat Landscape report on SOCRadar Labs and acquire valuable insights into the prevalent threats within your country. The page provides information regarding the number of Dark Web threats, stealer logs, ransomware and phishing threats, as well as active threat actors operating in the country. Additionally, it highlights the most targeted industry.
Download the report for free to learn more about your region’s threat landscape.