
DeepFaceLive Tool, Royal Mail and Lyca Mobile Data Leaks, DDoS Attack on Sony NNC
The SOCRadar Dark Web Team has uncovered a range of alarming cyber threats, including the distribution of a deepfake tool called DeepFaceLive, designed to create real-time deepfakes during video conferencing and live broadcasts. Additionally, a significant data breach involving Royal Mail has surfaced, exposing thousands of customer records. Further threats include a DDoS attack on Sony’s Neural Network Console, and an alleged breach of Lyca Mobile’s systems, compromising 1.5 million records. Lastly, unauthorized access to an American cable television provider is being offered for sale.
Receive a Free Dark Web Report for Your Organization:
The Alleged Deepfake Tool is Shared
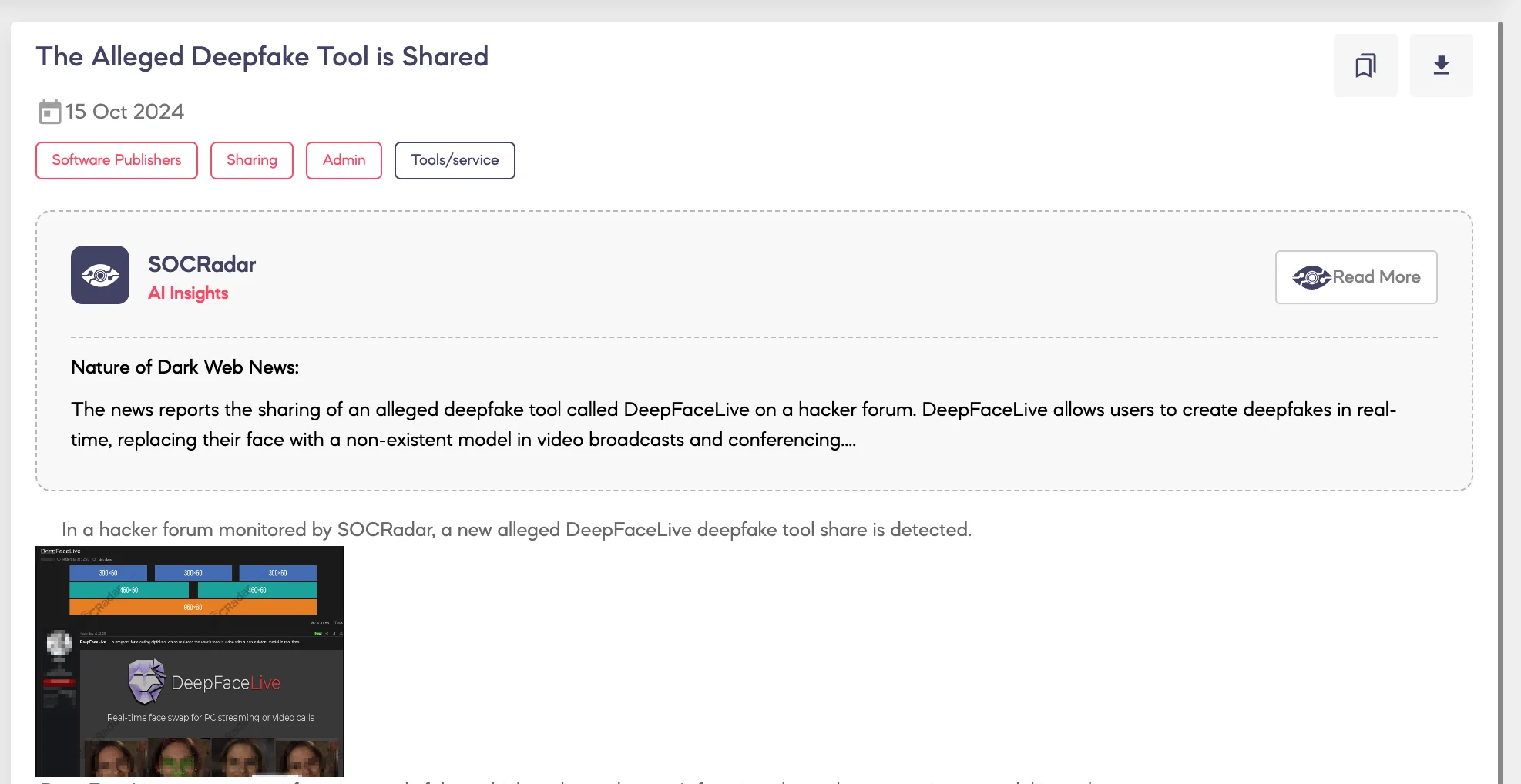
SOCRadar Dark Web Team detected the distribution of an alleged deepfake tool called DeepFaceLive on a hacker forum.
According to the threat actor, DeepFaceLive is a program designed to create real-time deepfakes by replacing the user’s face in video content with a non-existent model. Built on the artificial intelligence of DeepFaceLab, the tool can generate deepfakes during both live broadcasts and video conferencing, such as Zoom. Users can apply the likeness of a famous individual or a custom image created using DeepFaceLab.
The system requirements specified for DeepFaceLive include a graphics card compatible with DirectX12, a modern processor supporting AVX instructions, 4GB of RAM, a 32GB swap file, and Windows 10. The post contains a download link, providing access to other forum members.
The Alleged Database of Royal Mail is Leaked
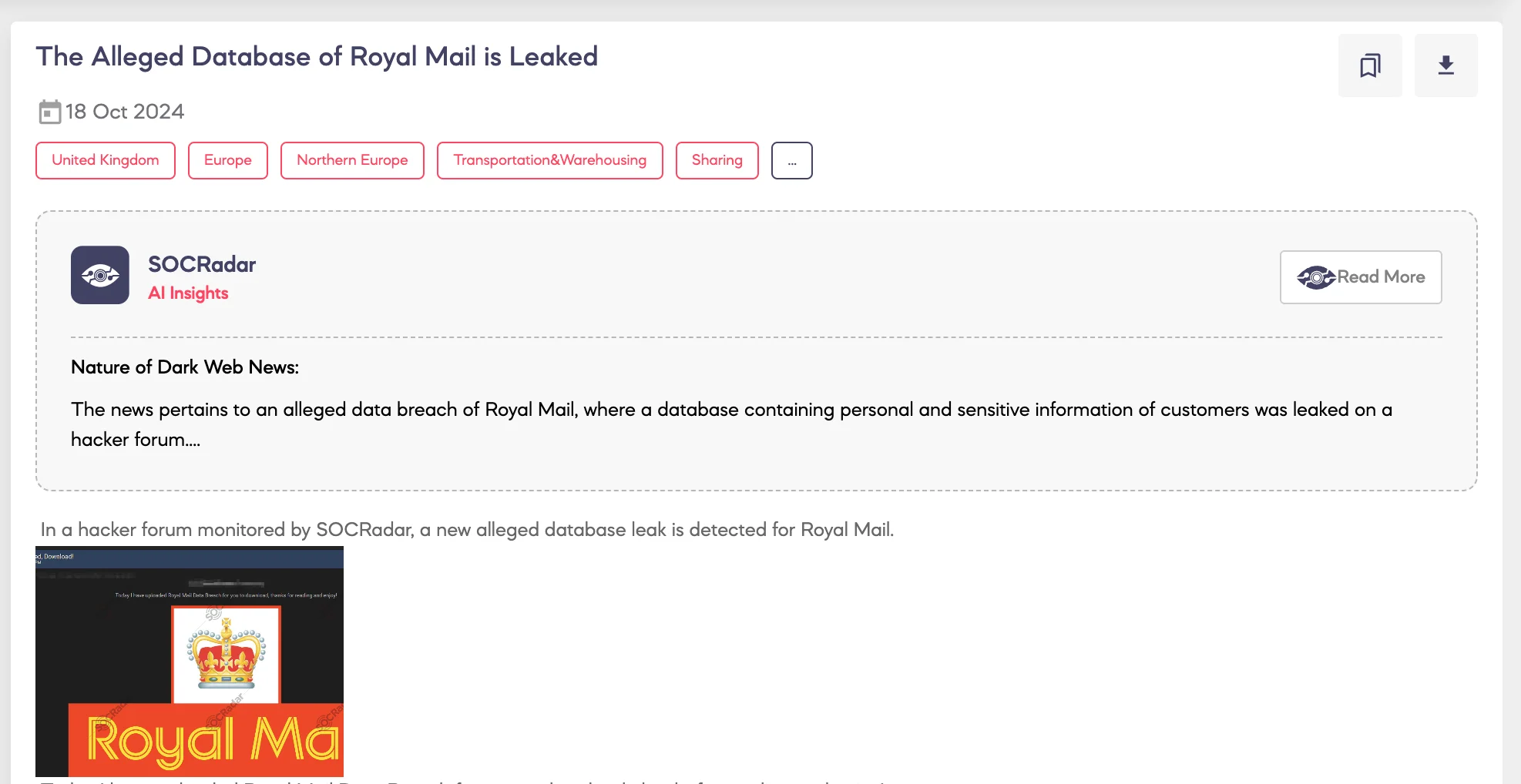
SOCRadar Dark Web Team detected that a threat actor is claiming to have leaked a database allegedly belonging to Royal Mail on a hacker forum.
The threat actor posted that they had uploaded the Royal Mail data breach for download, describing Royal Mail Group Limited as a British postal service and courier company. According to the actor, the breach occurred in October 2024, involving over 100 files with a total of 2,698 rows of data. However, the actor claims to have lost access quickly, preventing the full exfiltration of the database. The breach allegedly did not occur directly through Royal Mail.
The compromised data allegedly includes trading names, first and last names, company names, addresses, cities, counties, postcodes, countries, emails, phone numbers, package details (weight, size, and service code), signatures, and order notifications (both email and SMS). The actor behind this breach remains unidentified, and the leak represents a significant security concern for Royal Mail and its customers.
Cyber Army of Russia Reborn Conducted DDoS Attack on Neural Network Console – Sony
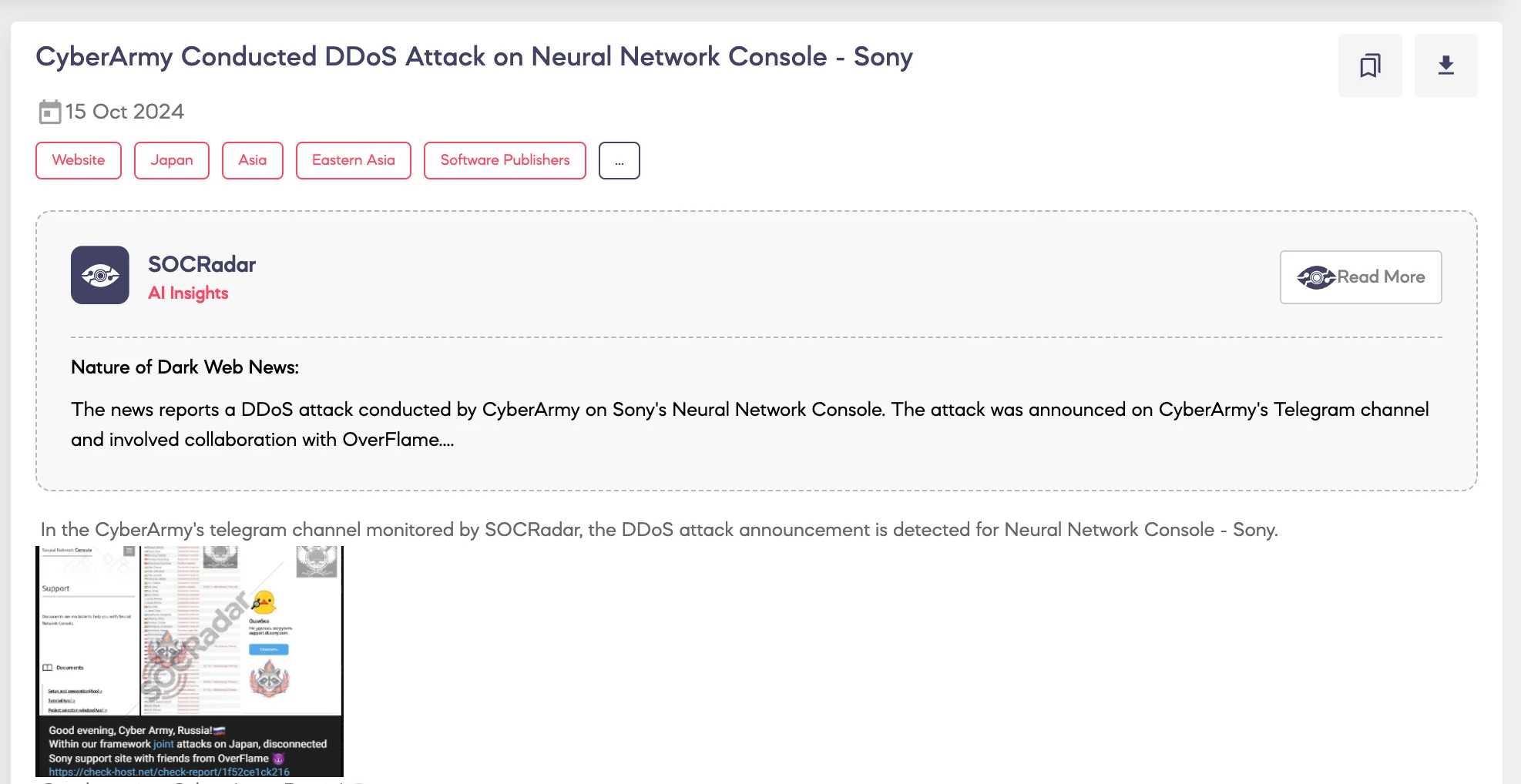
SOCRadar Dark Web Team detected that a post on a Telegram channel, “Cyber Army of Russia Reborn, announced a Distributed Denial-of-Service (DDoS) attack targeting Sony’s Neural Network Console on a Telegram channel.
The threat actor claims to have coordinated the attack as part of a joint operation with the hacking group OverFlame, specifically aimed at Japanese targets. They posted a link to a check-host report as evidence of the attack’s success, boasting about taking down Sony’s support site.
Cyber Army of Russia Reborn, known in Russian as “Народная CyberАрмия” (People’s CyberArmy), is a prominent hacktivist group that frequently engages in disruptive attacks on critical infrastructure and financial systems. The group demonstrates significant DDoS capabilities and strategic motivations, often aligning with political objectives.
Threat Actor Claims to Have Breached Lyca Mobile, Allegedly Accessing Systems for Over a Year and Exposing 1.5 Million Records
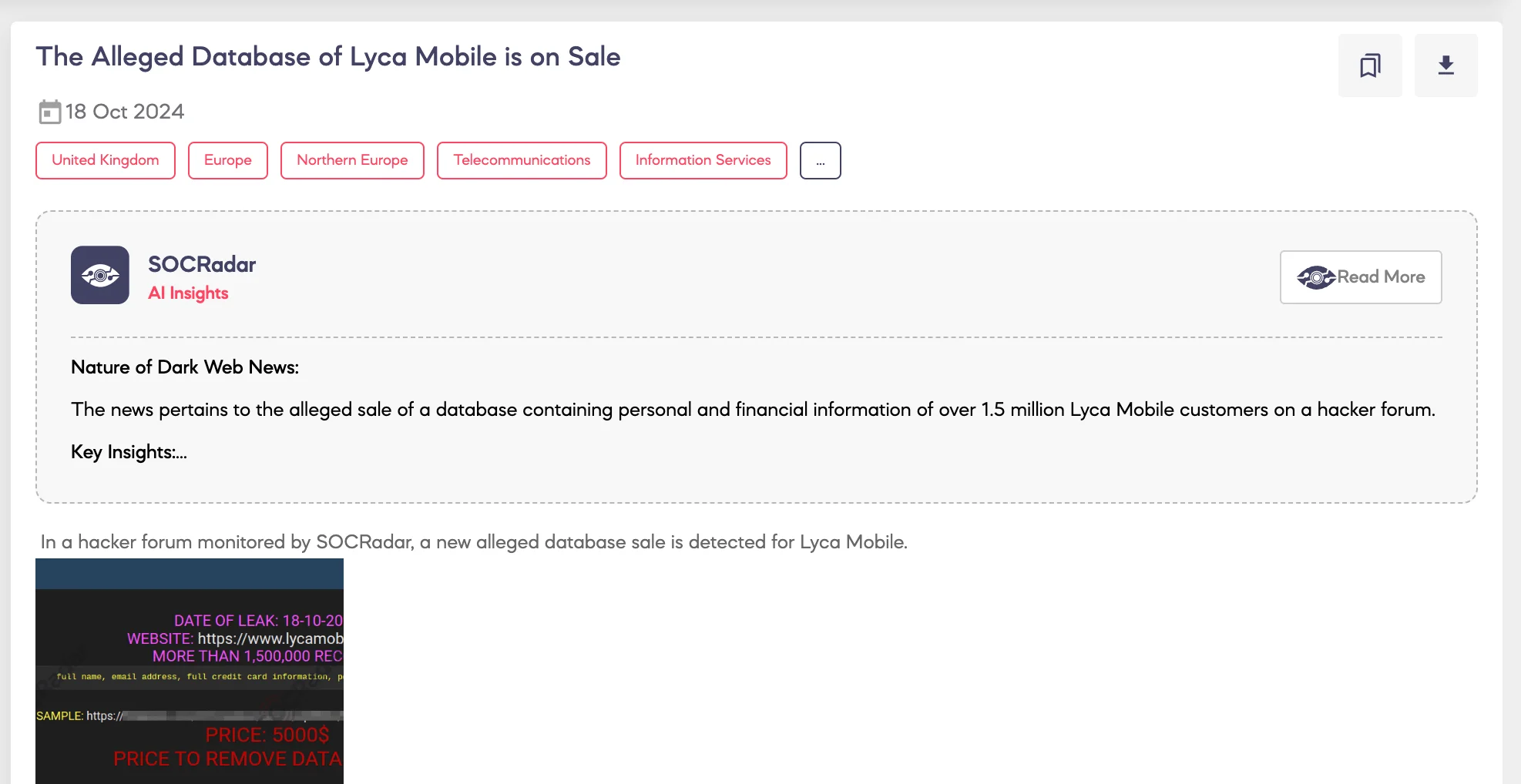
SOCRadar has detected a breach claim involving Lyca Mobile, a British Mobile Virtual Network Operator (MVNO) operating in 23 countries. The claim comes from a well-known threat actor on a monitored hacker forum, notorious for database sales and leaks. On October 18, 2024, the actor claimed to have breached Lyca Mobile’s systems and offered a database containing over 1.5 million records for sale. The database allegedly includes full names, email addresses, complete credit card details, and billing addresses. The threat actor set the price at $5,000, with an option to delete the data for $30,000, sharing a sample of the stolen information to support their claim.
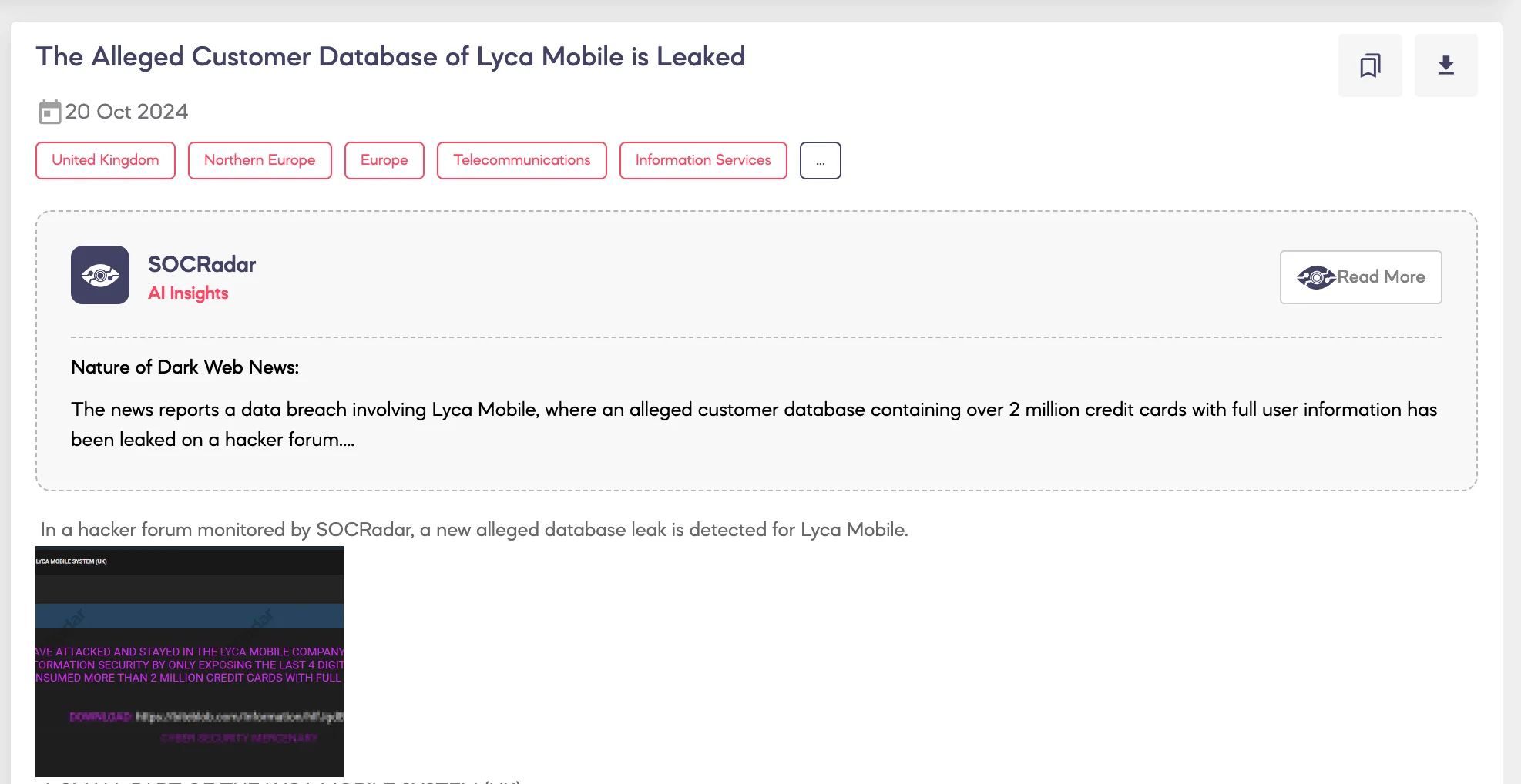
Two days later, on October 20, 2024, the same threat actor announced the leak of part of the database, stating that they had maintained access to Lyca Mobile’s systems for over a year, compromising more than two million credit card records.
The Alleged Unauthorized Access Sale is Detected for an American Cable Television Provider Company
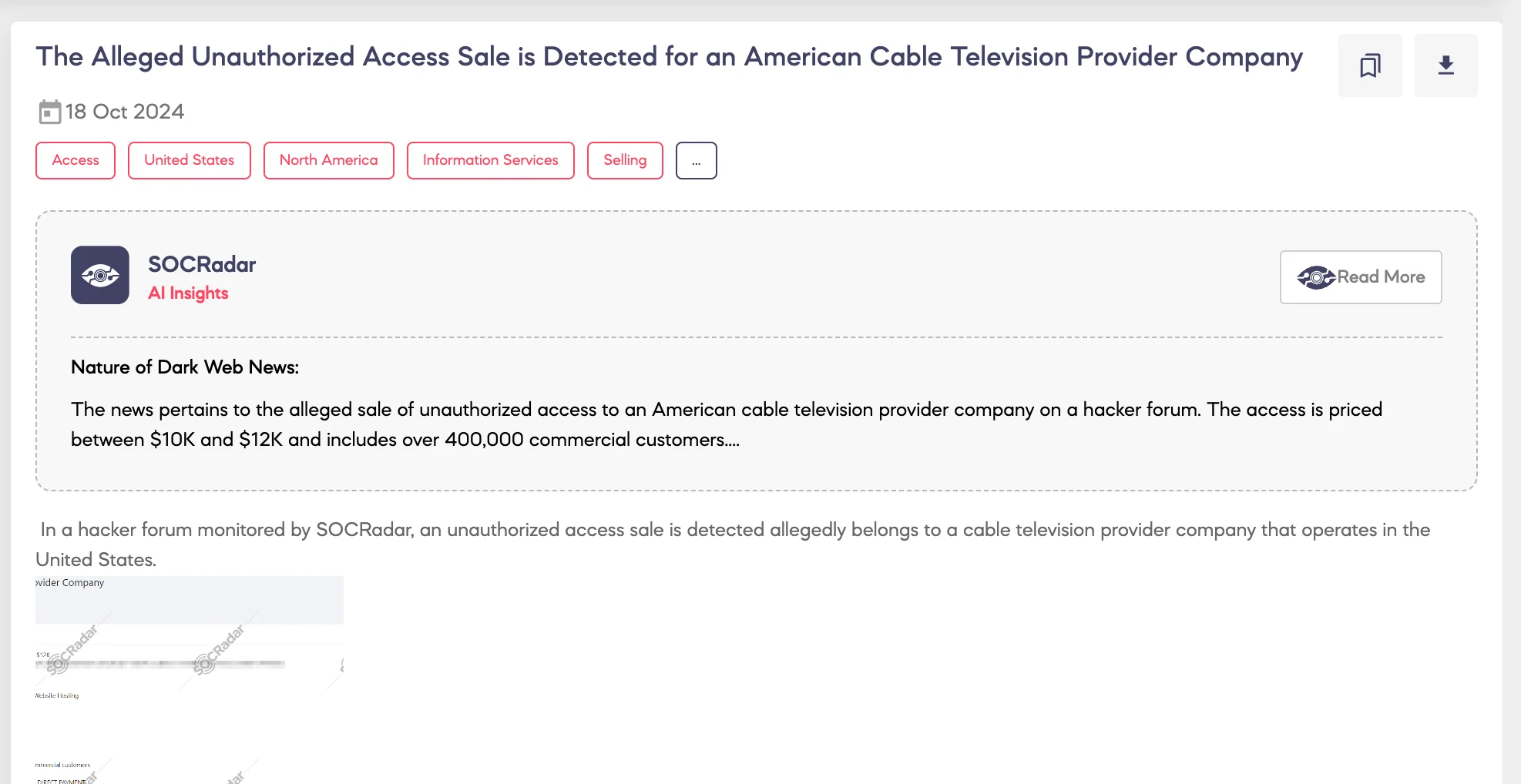
SOCRadar Dark Web Team detected that a threat actor is allegedly selling unauthorized access to an American cable television provider on a hacker forum.
The threat actor claims that the target is a major U.S.-based internet service provider and website hosting company with an estimated revenue of $11 billion and around 18,000 employees. The threat actor claims to have access to information affecting over 400,000 commercial customers. They are offering this unauthorized access for a price ranging from $10,000 to $12,000, with options for escrow or direct payment.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.


































