
LoyLap Database Leak, New Jason RAT, and Supercell Exploit for Sale on Dark Web
In the past week, the SOCRadar Dark Web Team has uncovered a series of significant cyber threats, such as the alleged leak of a LoyLap database, exposing sensitive customer and transaction data. Additionally, a new remote access tool, Jason RAT, has surfaced. The team also detected a data breach involving Grayscale, a cryptocurrency asset manager, and the sale of 1,300 U.S. credit cards. Lastly, a zero-day vulnerability targeting Supercell’s gaming platforms is being offered for sale, posing a serious risk to user security.
Receive a Free Dark Web Report for Your Organization:
Alleged Database of LoyLap is Leaked
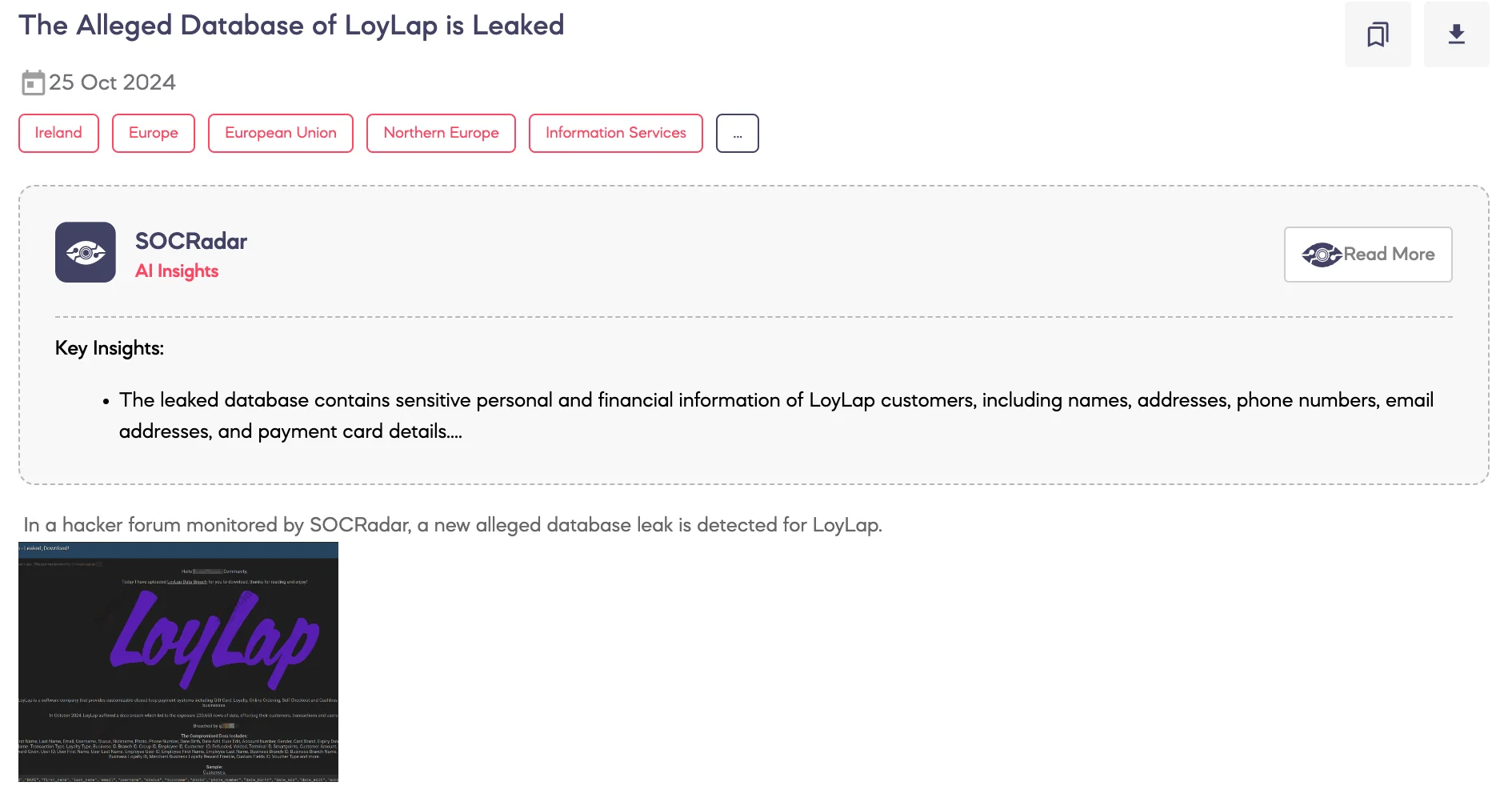
SOCRadar Dark Web Team detected that a threat actor has allegedly leaked a database belonging to LoyLap, a software company specializing in customizable closed-loop payment systems such as gift cards, loyalty programs, online ordering, self-checkout, and cashless systems. The platform is currently used by 3,300 businesses.
The threat actor claims to have uploaded the LoyLap data breach on a hacker forum, revealing that the breach occurred in October 2024, resulting in the exposure of 233,658 rows of data. The compromised information reportedly includes customer details, transaction records, and gift card data. The leaked data contains various fields, such as ID, first and last names, email, username, phone number, date of birth, account number, card brand, expiry date, transaction type, loyalty type, terminal ID, user and employee information, merchant details, and more.
New Jason RAT Tool Shared on Dark Web
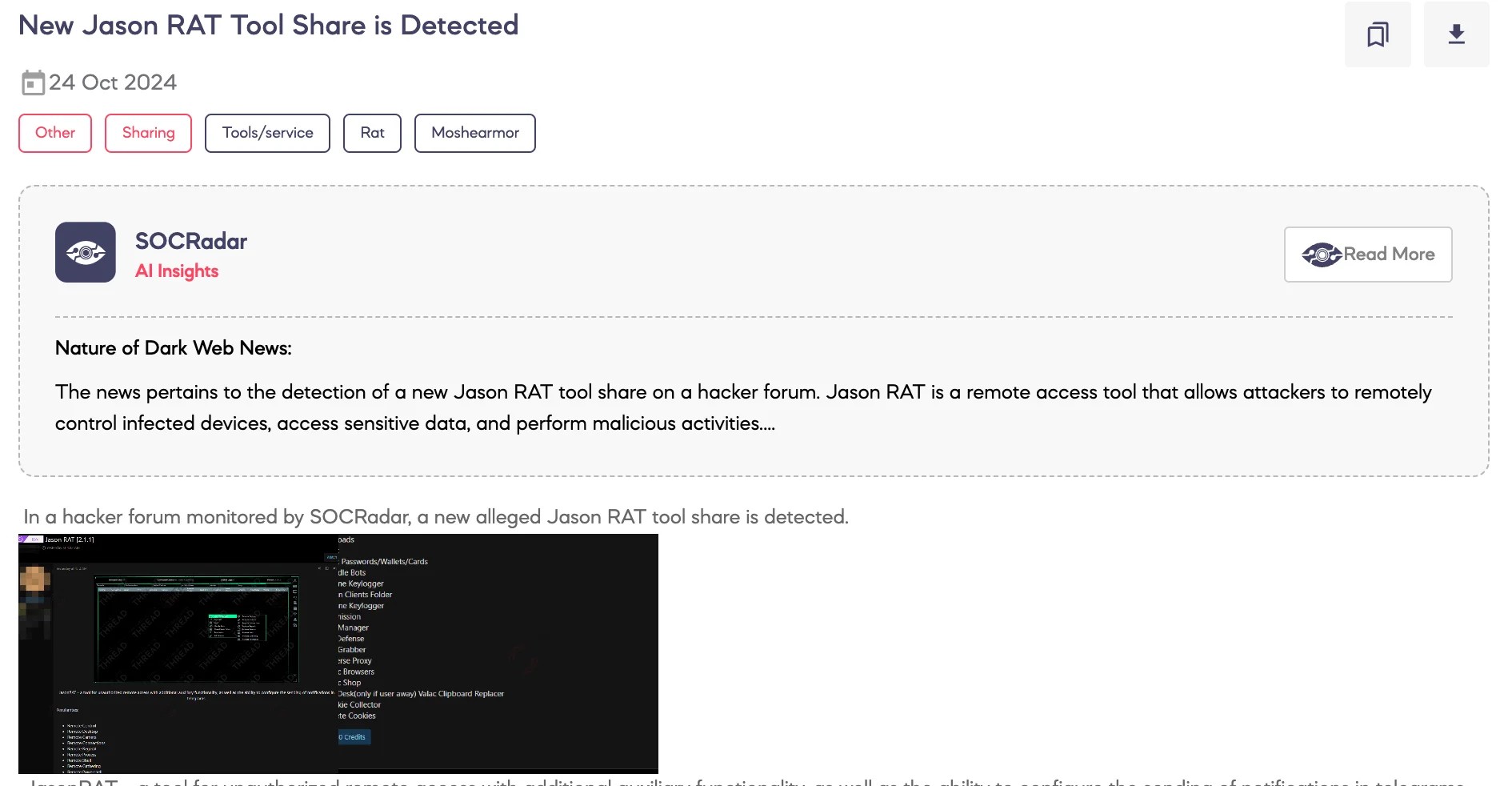
SOCRadar Dark Web Team detected that a threat actor has allegedly shared a new Remote Access Tool (RAT) called Jason RAT on a hacker forum.
The threat actor describes Jason RAT as a tool designed for unauthorized remote access, featuring auxiliary functionalities and the ability to configure notification delivery via Telegram. The tool is promoted with a wide range of features, including remote control, desktop access, camera manipulation, registry editing, and process management. It also offers capabilities for remote shell access, PowerShell execution, payload delivery, and data gathering, including passwords, wallet information, and credit card details.
Additionally, Jason RAT supports handling bots, online and offline keylogging, file management, reverse proxy setup, and HVNC (Hidden Virtual Network Computing) for browser manipulation. Other functionalities mentioned include AnyDesk access, clipboard replacement, cookie collection, and cookie deletion.
Alleged Database of Grayscale is on Sale
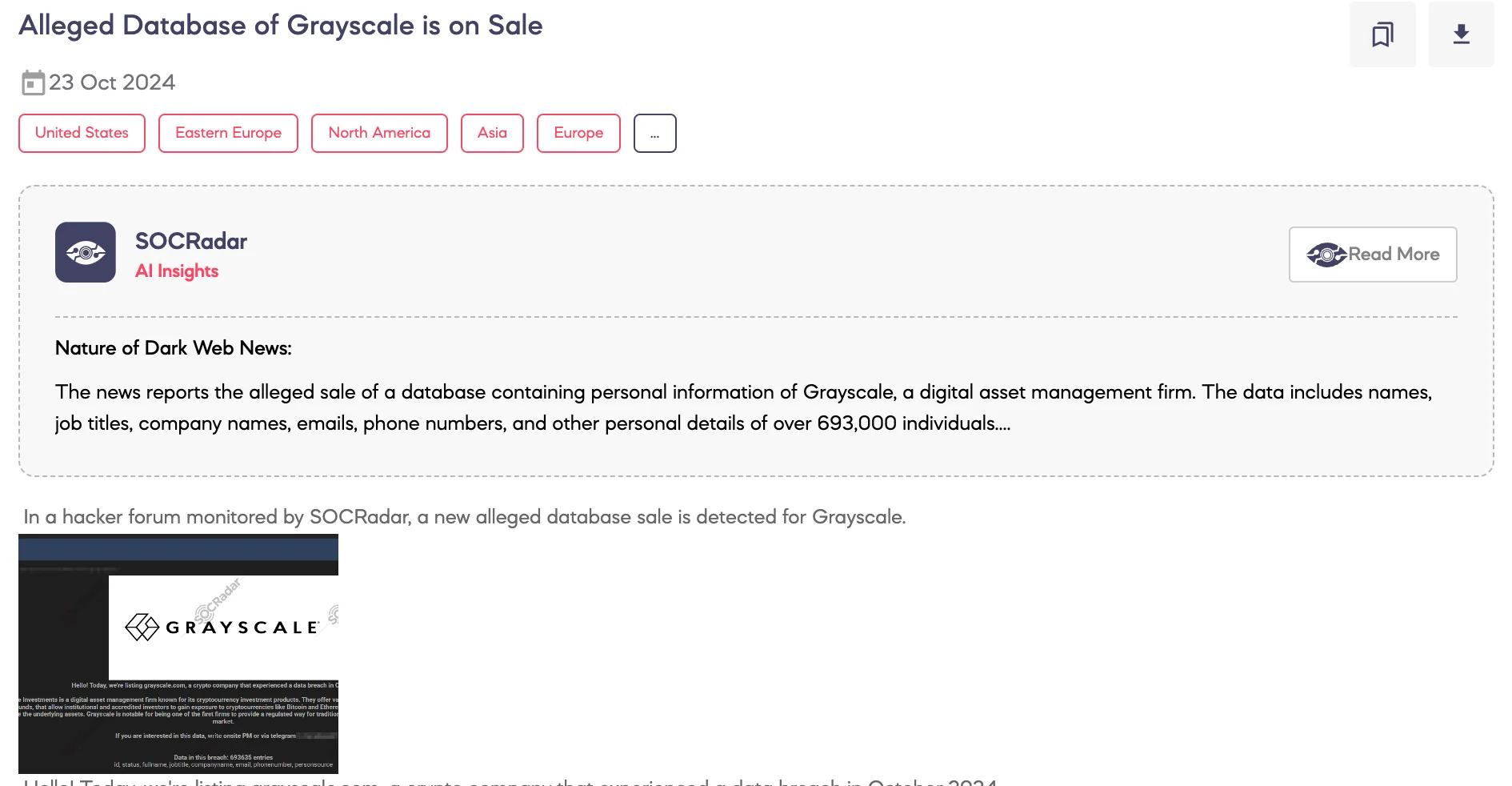
SOCRadar Dark Web Team detected that a threat actor is allegedly selling a database claimed to be from Grayscale on a hacker forum.
The threat actor states that Grayscale, a well-known digital asset management firm specializing in cryptocurrency investment products, experienced a data breach in October 2024. The database allegedly contains 693,635 entries, including fields such as ID, status, full name, job title, company name, email, phone number, and person source.
Grayscale is recognized for offering institutional and accredited investors regulated access to cryptocurrency investments like Bitcoin and Ethereum through trusts and funds, allowing participation without direct asset management. The threat actor is seeking interested buyers via private messages on the forum or through Telegram.
1,300 Credit Cards Belonging to the United States are on Sale
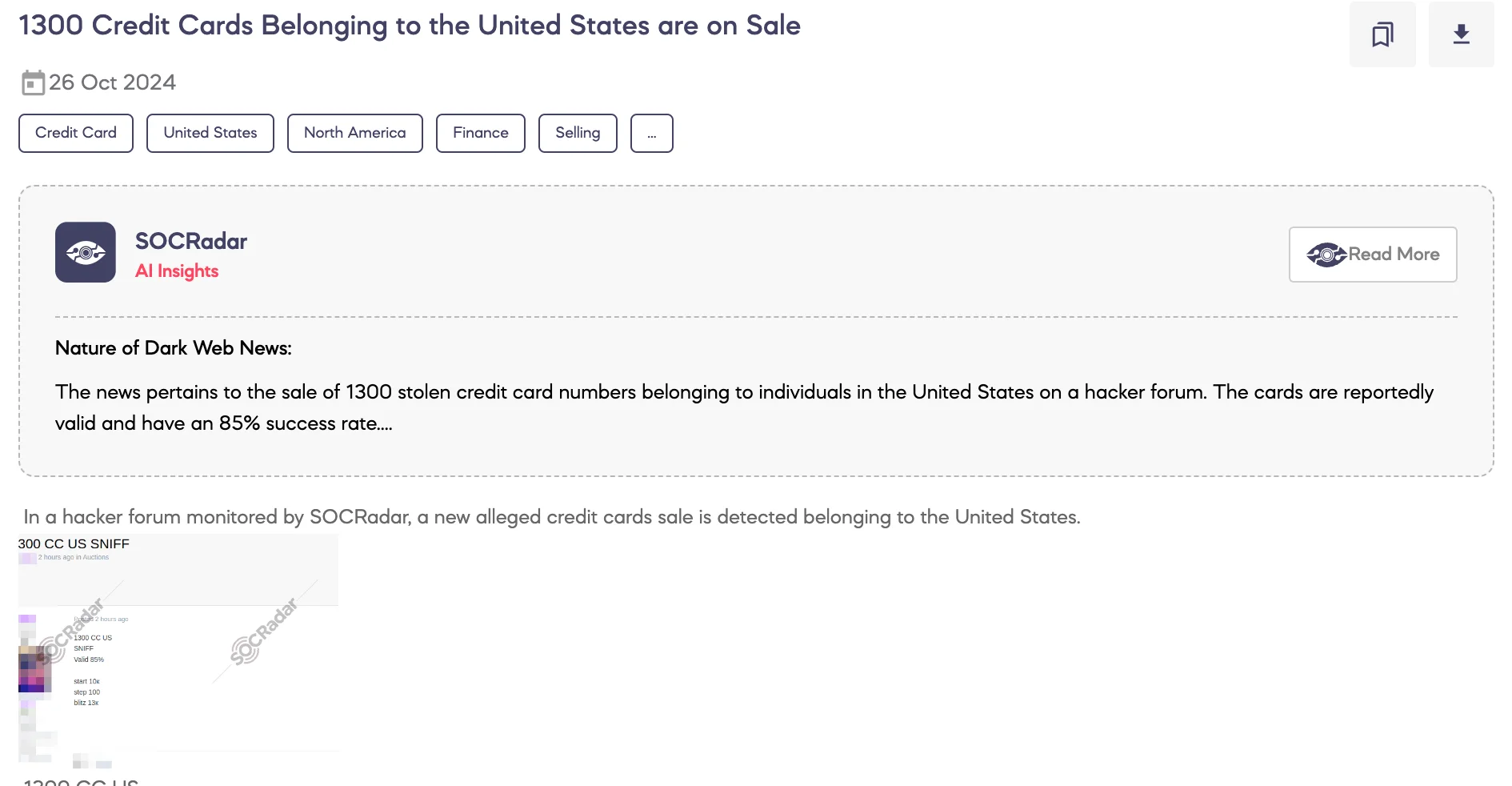
SOCRadar Dark Web Team detected that a threat actor is allegedly selling 1,300 credit cards belonging to individuals in the United States on a hacker forum.
The threat actor claims that the credit card data has been obtained through sniffing and asserts an 85% validity rate. The auction for the dataset starts at $10,000, with bid increments of $100. The blitz price, which allows immediate purchase by bypassing the bidding process, is set at $13,000.
New 0-Day Sale is Detected for Supercell
SOCRadar Dark Web Team detected that a threat actor is allegedly offering a new zero-day vulnerability targeting Supercell, a Finnish mobile game development company known for popular games like Clash of Clans, Clash Royale, and Brawl Stars, on a hacker forum.
The threat actor claims to have discovered this vulnerability and has developed an automation tool that can generate any desired link quickly. They are offering to demonstrate how the tool works to interested buyers and are open to questions via private message or forum replies.
The price for the zero-day exploit is yet to be determined, with the seller accepting offers from potential buyers. Payment can be made in Bitcoin (BTC) or Monero (XMR), with escrow services also accepted. If verified, this exploit could pose a serious threat to Supercell’s gaming platforms and user data, given the zero-day nature of the vulnerability.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.

































