
Financial Software Company Finastra Investigates Recent Security Incident
Finastra, a prominent financial services software provider, is currently investigating a cybersecurity incident that has raised concerns across the industry. The breach involves its Secure File Transfer Platform (SFTP), which attackers allegedly accessed using compromised credentials. The company serves many of the world’s largest banks, making any potential breach a matter of significant attention.
Preliminary findings suggest that the breach was isolated to the SFTP system, with no indication of lateral movement to other platforms. However, claims of stolen data on a hacking forum earlier this month, raised further concerns.
As the company works with cybersecurity experts to determine the scope and impact of the incident, the situation demonstrates the importance of secure data management in the financial technology sector.
What Happened in the Finastra Breach?
On November 7, 2024, Finastra detected unusual activity within its internally hosted Secure File Transfer Platform (SFTP). The breach was traced to an attacker who leveraged compromised credentials to gain access. Initial investigations, supported by security experts, confirmed that the breach was confined to this platform, with no evidence of lateral movement to other systems or networks.
A day later, on November 8, they began notifying customers of the incident. Around the same time, a threat actor using the alias “abyss0” surfaced on the popular Dark Web forum “BreachForums,” claiming to possess 400GB of stolen data from the company. The data, allegedly exfiltrated via the SFTP platform, was auctioned for thousands of dollars.
While the exact scope of the breach remains under investigation, Finastra has assured customers that the compromised SFTP platform was not its default file-sharing system. Impacted clients are being contacted directly, and the company has implemented an alternative secure platform to maintain operations.
Dark Web Activity Linked to the Breach
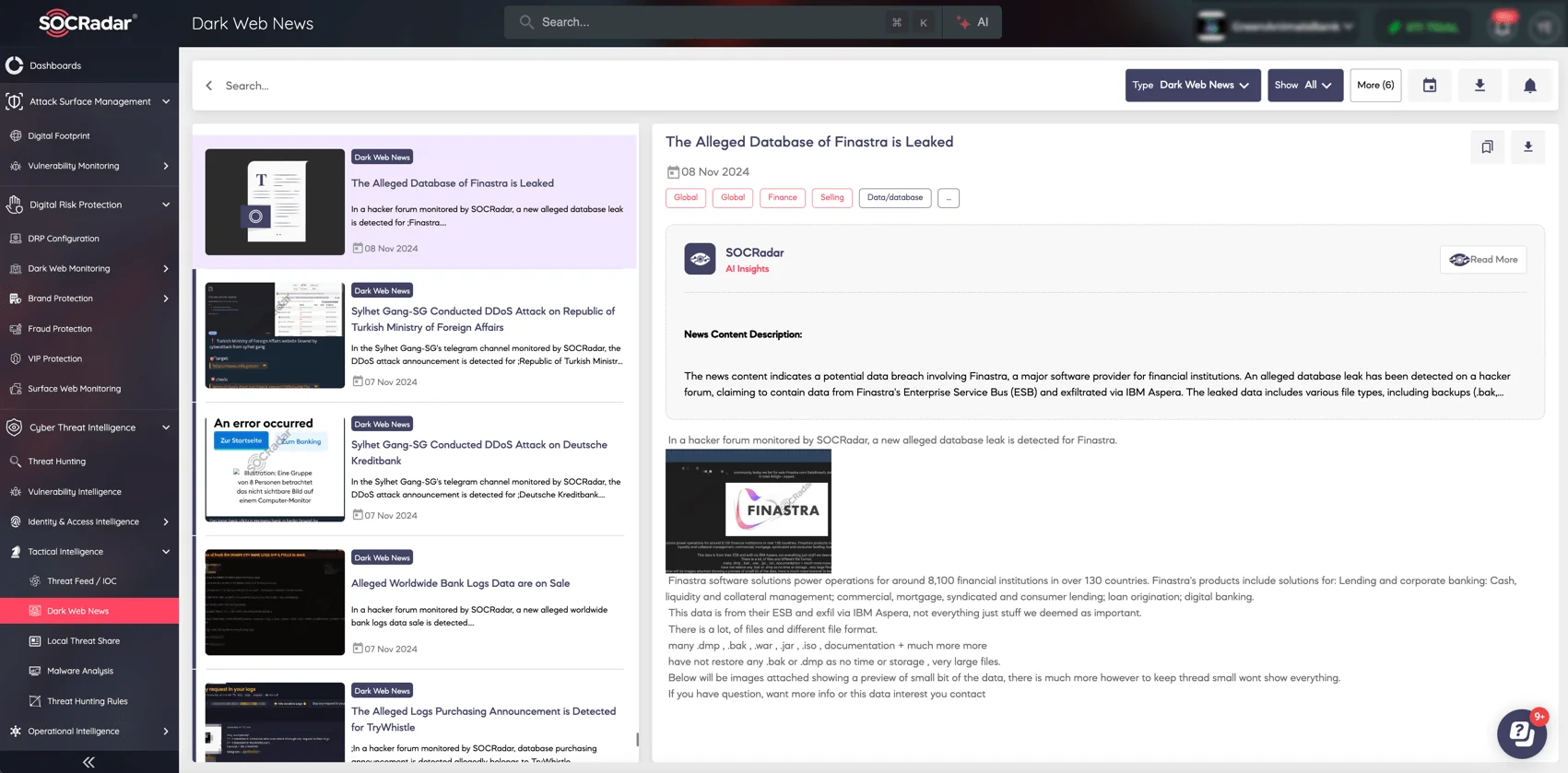
On November 8, 2024, our customers were notified about a threat actor’s post regarding the Finastra data breach by SOCRadar’s Dark Web News module. And on November 1, it alerted our customers to an access sale post by the same threat actor, which is also related.
A hacker using the alias “abyss0” claimed on BreachForums to have stolen 400GB of data from Finastra, including sensitive files linked to major banking clients. The threat actor also noted for buyers to contact them via Telegram.

Finastra.com data breach post from November 8, 2024
Earlier, on November 1, an access sale post by the same actor indirectly referenced Finastra. This post described unauthorized access through IBM Aspera and initially priced the stolen data at $20,000, later reducing it to $10,000.
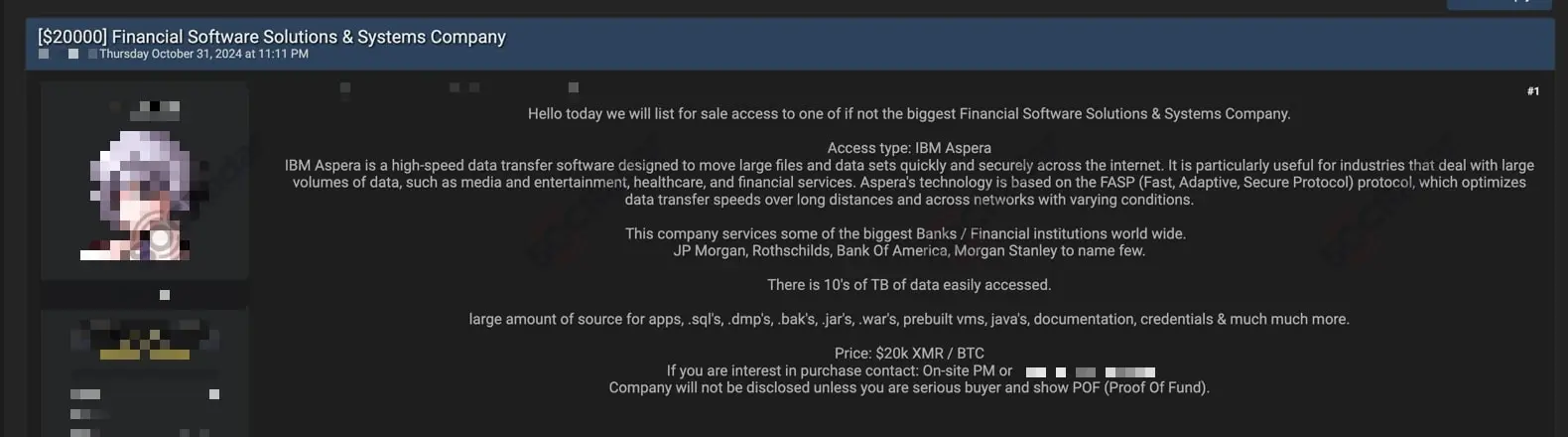
The access sale post, posted on October 31, 2024
The stolen data included diverse file types such as configuration files, database backups, and executable components, according to the threat actor’s claims, raising serious concerns about potential financial fraud and downstream attacks. However, the threat actor’s BreachForums account and Telegram handle have since disappeared, leaving the fate of the data unclear. Whether it was sold or removed due to public scrutiny remains unknown.
Monitoring Dark Web activities is critical to identifying and mitigating such risks early. SOCRadar’s Dark Web Monitoring module helps organizations:
- Detect leaked data and credentials before attackers exploit them.
- Monitor threat actor chatter linked to your organization.
- Receive real-time alerts on emerging risks.
By leveraging actionable intelligence, you can safeguard your business against incidents like Finastra’s breach.
Stay ahead of emerging threats – track hacker activity with SOCRadar’s Dark Web News.
Finastra’s Response and Ongoing Investigation
After noticing suspicious activity on November 7, 2024, Finastra quickly responded to the security breach by isolating the compromised Secure File Transfer Platform (SFTP). According to initial findings, the intrusion was caused by compromised credentials.
Finastra made it clear in its notice that there were no indications of lateral movement to other systems and that the breach was limited to the SFTP platform. Notably, the compromised SFTP platform was not Finastra’s default system for file exchanges, and not all customers had access.

Finastra’s security notice (Source: Krebs on Security)
The company further stated that no malware was deployed and that no customer files were tampered with. However, data exfiltration has been confirmed, and investigations are underway to determine the extent of the stolen information.
Finastra stated that it will share Indicators of Compromise (IOCs) with affected customers as they are contacted directly, with updates provided throughout the ongoing investigation. During this time, the company says it has implemented a secure alternative file-sharing platform to ensure operational continuity.




































