
NodeStealer’s Evolution: A Growing Threat to Facebook Accounts and Beyond
NodeStealer, a Python-based infostealer, has resurfaced in a more dangerous form, raising the stakes for global cybersecurity teams. This malware, first identified in 2023, now has enhanced capabilities, making it a significant threat to both individual users and organizations. Its primary targets include Facebook Ads Manager accounts, credit card data, and sensitive browser-stored information.
Let’s look at how this malware works, its latest campaigns, and what businesses can do to defend themselves.
The Rise of NodeStealer
NodeStealer first surfaced in 2023 as JavaScript malware intended to compromise Facebook Business accounts. By May 2023, it had evolved into a Python-based infostealer capable of exploiting Facebook credentials and cookies to hijack accounts. However, its most recent evolution, observed in November 2024, demonstrates an alarming increase in its capabilities.
NodeStealer now:
- Targets Facebook Ads Manager Accounts: Extracting financial details and business-related data to fuel malicious ad campaigns.
- Steals Credit Card Information: Harvesting cardholder names, numbers, and expiration dates stored in browsers.
- Abuses Windows Restart Manager: Unlocking browser database files locked by other processes to facilitate data theft.
These advancements indicate a highly adaptive malware designed to expand its reach and disrupt victims on multiple fronts.
A New Wave of Malicious Campaigns
The latest campaigns leveraging NodeStealer demonstrate its growing sophistication and reach:
Malvertising Through Facebook Ads
In one campaign, attackers used verified Facebook accounts to distribute malicious ads. These advertisements promoted a fake Google Chrome extension that resembled the Bitwarden password manager, tricking victims into downloading malware. Using trusted brands, attackers gained access to personal data and compromised Facebook accounts, resulting in financial losses and reputational damage for businesses.
Facebook Ads Manager Exploitation
NodeStealer actively targets Facebook Ads Manager accounts, using cookies to generate access tokens through the Facebook Graph API. Using these tokens, the malware obtains data such as account budgets, daily limits, and campaign spend, which could be used in malicious advertising campaigns.
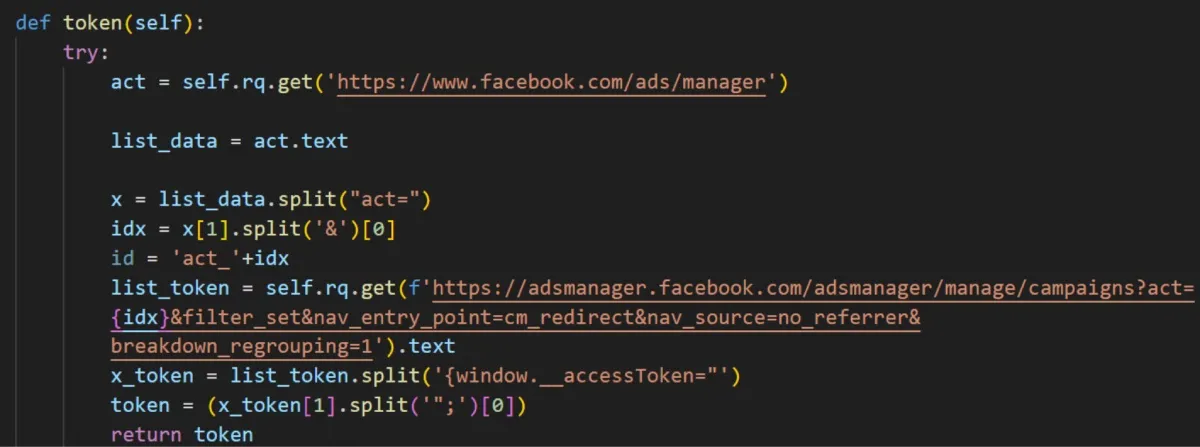
Collecting tokens from Facebook Ads Manager
Advanced Techniques for Data Theft
One of the most notable techniques is the use of Windows Restart Manager, a legitimate tool for reducing system reboots during updates. NodeStealer uses this tool to unlock locked SQLite database files, allowing it to steal sensitive data such as credit card information from web browsers.
The Bigger Picture
NodeStealer’s most recent variants are thought to have originated from Vietnamese threat actors, as evidenced by embedded code designed to bypass Vietnamese systems—likely to avoid legal ramifications in their home country. NodeStealer exfiltrates data, including credit card details and Facebook Ads Manager data, and sends it to attackers via Telegram, a platform that cybercriminals continue to use despite policy changes.
The evolution of malware reveals a clear trend: using legitimate tools and platforms to evade detection and improve efficiency. Its focus on Facebook’s advertising infrastructure highlights the profitability of malvertising campaigns, which frequently spread malware disguised as legitimate software.
Strengthening Your Defenses
Organizations can adopt proactive measures to mitigate the risks posed by NodeStealer and similar threats. By combining robust security practices with advanced monitoring tools, organizations can significantly reduce their exposure to such sophisticated malware campaigns.
- Harden Facebook Accounts
- Enable Multi-Factor Authentication (MFA) on all accounts to add an extra layer of security.
- Regularly audit and monitor ads manager activity to identify and respond to unusual spending or unauthorized changes.
- Update Endpoint Security
- Deploy tools that can detect and prevent the abuse of legitimate libraries like Windows Restart Manager. This minimizes the risk of unauthorized access to locked browser database files.
- Educate Your Workforce
- Conduct regular training sessions to help employees recognize phishing attempts and malicious advertisements.
- Implement phishing simulations to gauge employee readiness and improve response mechanisms.
- Advanced Dark Web Monitoring with SOCRadar
Leverage SOCRadar’s Dark Web Monitoring to proactively detect stolen credentials, exposed sensitive information, and potential threats linked to your organization. SOCRadar continuously scans forums, marketplaces, and hidden communication channels on the dark web to deliver real-time alerts about leaked data and emerging risks.
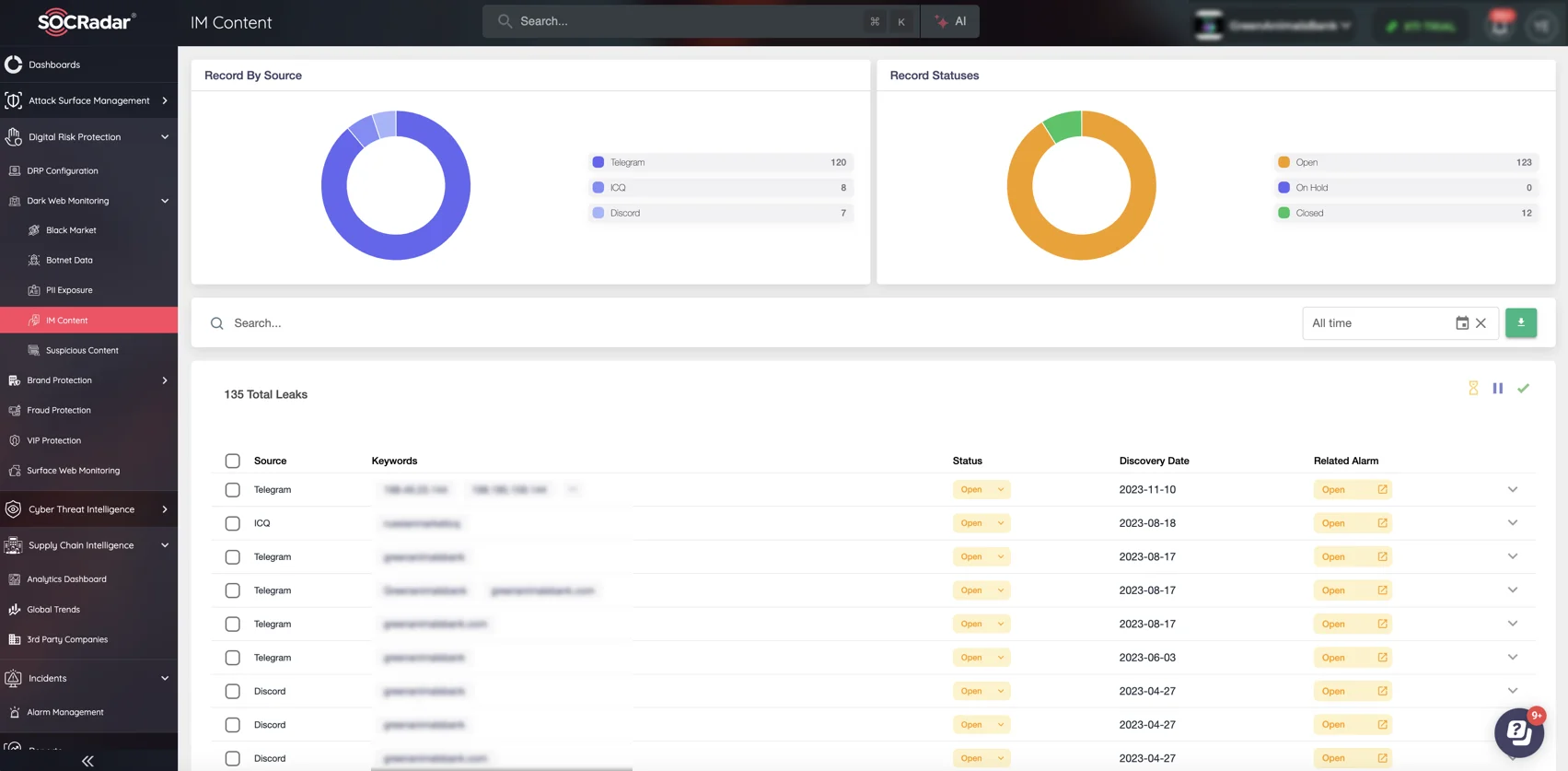
Keep an eye on recent threat actors activities using socradar Dark Web Monitoring
By integrating dark web insights into your overall threat intelligence strategy, you can prevent attackers from capitalizing on stolen information.
- Phishing Domain Takedown with SOCRadar
Rely on SOCRadar’s Integrated Takedown Service to detect and eliminate phishing domains and fake websites targeting your organization.
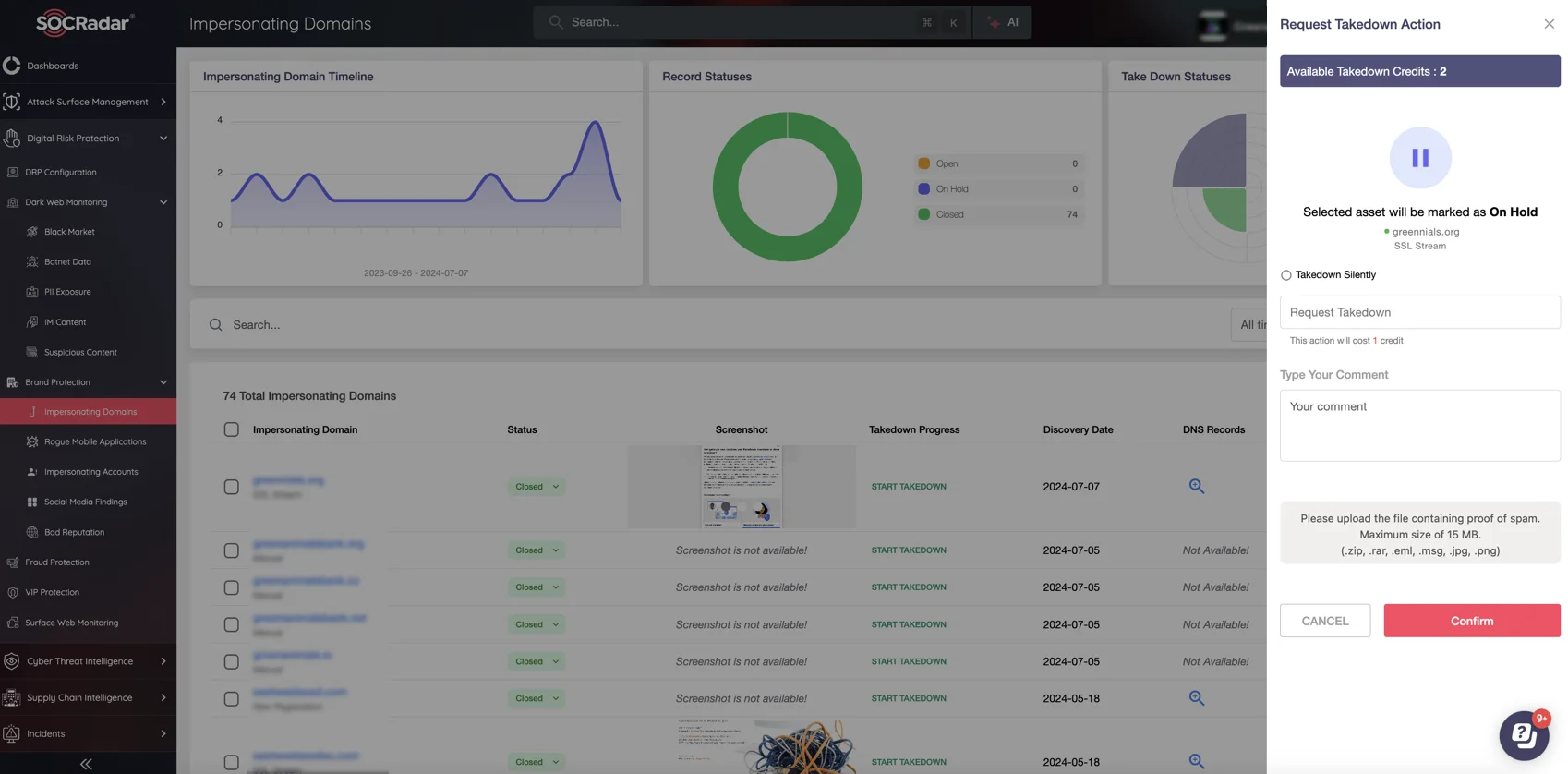
Use SOCRadar’s Integrated Takedown Service to remove fake domains
This service not only identifies domain spoofing attempts but also initiates takedown procedures, protecting your brand integrity while safeguarding employees and customers from impersonation attacks. Quick and effective takedown actions prevent phishing campaigns from gaining traction, significantly reducing potential losses.
Indicators of Compromise (IOCs)
Security teams should remain vigilant for these IOCs associated with NodeStealer, which are listed below from online resources:
MD5 Hashes:
- 173b17e195b0a80611c22f333c3d2ec2
- 2dc191275434b6afe6c6117ad76051ed
- 13f94cda395bfdd2c87a024ee497e576
- 10f53e5d2eacf8912ca5d0516a8dc89f
- 64f4b6f2b2dfdd2e0c8c47e726f75e9a
- bfcce5cd48cc23071052120338df1226
SHA-256 Hashes:
- 4613225317e768d6d69b412843a314e2af64960856a0cfd798ed52285867bc36
- AE0712C02E750C35219214437D8794DA3BCD9FF608C3F59CDCA0934A958189D3
- C6C0000ECF6AF93D0750C45FBD8AF0F8E2289F051DFD523C9550675017F27B53
- 58ED336B7AB7B84BA05892F9839ADCB13390D66B53532B62EC37CBCD6A7DE3FF
- C5D4E4D9FA2C201D74A14FD1972B670FDE243F087451A3A7DC52A9A6DB61A1CB
- 641F2DB9E9FB8255337672FB8DA9226225FA8E393B651C7C7EBBB5B555D4B755
- EA25DD47B43DDAA3DF11E6D16544702A8FABBCD0031BA11D1DF51461704A8973
- 4613225317e768d6d69b412843a314e2af64960856a0cfd798ed52285867bc36
- 8dcced38514c8167c849c1bba9c3c6ef20f219a7439d2fc1f889410e34d8f6c9
- ea25dd47b43ddaa3df11e6d16544702a8fabbcd0031ba11d1df51461704a8973
SHA1 Hashes:
- 50406e911960d5b6a552c378ce0bd236518194bf
- 8c54843a3d643c08c805d5205f9220e40c07377a
- f3152afb08e7e45735285064079aa75b99b3ab05
- 354bf3e5b82a705d311759338d5e3db28f5e6ad4
- e3112cc5082c05da587c81589e47a37065364d5b
Conclusion
The emergence of the new NodeStealer variants underscores the evolving tactics of cybercriminals, leveraging legitimate platforms and advanced techniques to maximize their impact. From targeting Facebook Ads Manager to stealing sensitive data stored in SQLite browser databases. NodeStealer represents a clear and present danger to individuals and businesses alike.
By staying informed, implementing robust security measures, and monitoring for emerging threats, CISOs and security teams can safeguard their organizations against this and other evolving cyber threats.




































