
Chinese APT Exploits Cisco IOS XE Vulnerabilities (CVE-2023-20198 & CVE-2023-20273) in Global Attacks
An ongoing cyber campaign targets unpatched Cisco IOS XE software used in telecommunications networks worldwide. This campaign exploits two vulnerabilities – CVE-2023-20198 and CVE-2023-20273 – allowing attackers to gain unauthorized access and escalate privileges.
The Chinese APT group Salt Typhoon has been identified as a key threat actor behind these intrusions, affecting organizations like telecommunications providers and ISPs globally.
How Are Cisco IOS XE Vulnerabilities (CVE-2023-20198 & CVE-2023-20273) Being Exploited?
Cisco first warned about these vulnerabilities in late 2023, highlighting their severity and the need for immediate patching. Despite this, threat actors continue to exploit them, as many organizations have yet to secure their systems.
CVE-2023-20198: Privilege Escalation via Web UI
The first and more severe vulnerability, CVE-2023-20198 (CVSS Score: 10.0 – Critical), is a privilege escalation flaw in the web user interface (UI) of Cisco IOS XE. It allows remote, unauthenticated attackers to create accounts with full administrative privileges, granting them complete control over affected devices. This flaw is particularly dangerous as it requires no prior access or authentication, making exploitation straightforward for attackers.
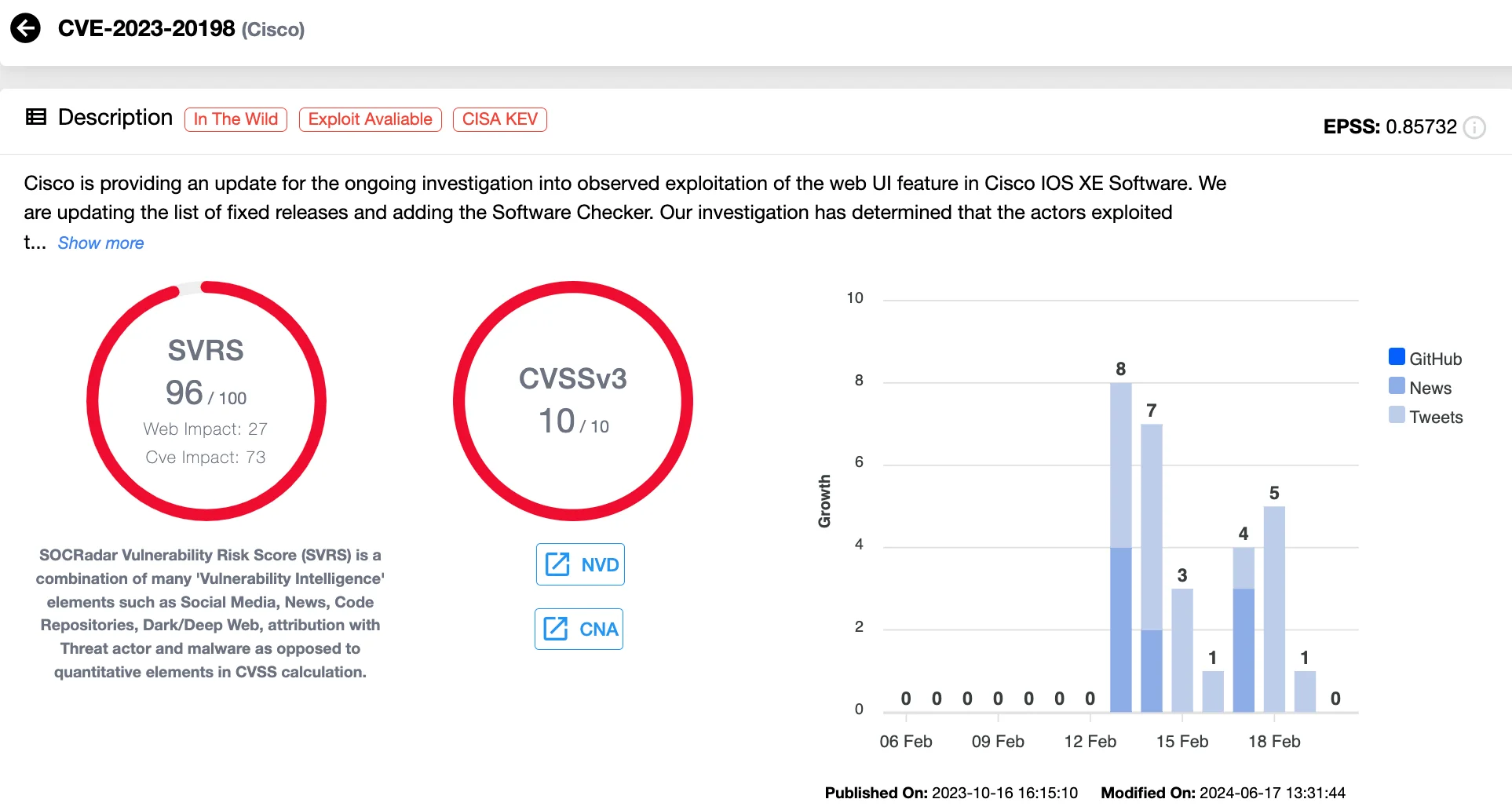
Vulnerability card of CVE-2023-20198 (SOCRadar Vulnerability Intelligence)
You can find Cisco’s official advisory for the critical vulnerability here.
CVE-2023-20273: Root Privilege Execution
The second vulnerability, CVE-2023-20273 (CVSS Score: 7.2 – High), allows attackers to execute arbitrary commands with root privileges. While not as severe as CVE-2023-20198, this flaw is often chained with the first vulnerability to gain complete system takeover, making it a critical concern when exploited in tandem.
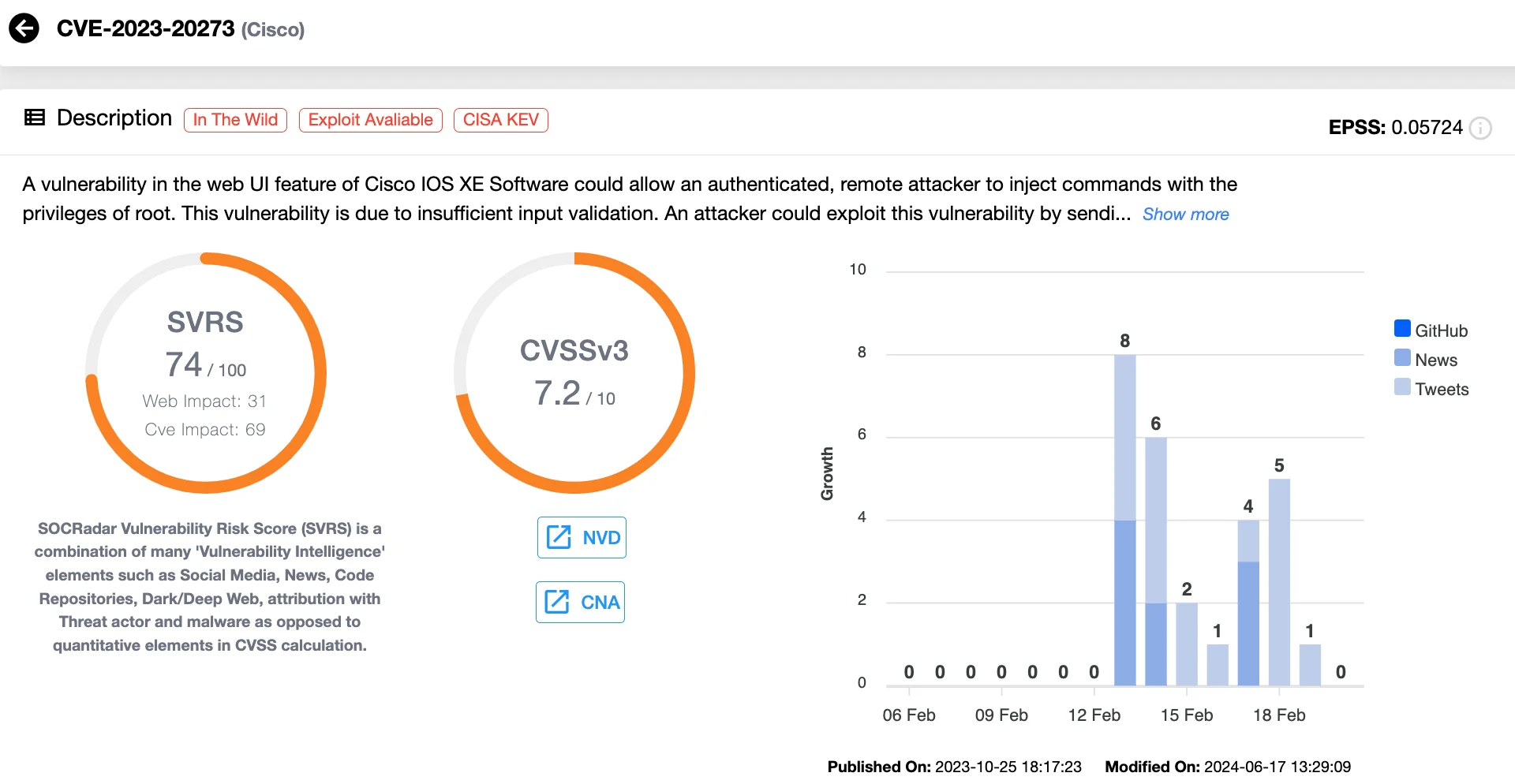
Vulnerability card of CVE-2023-20273 (SOCRadar Vulnerability Intelligence)
Cisco released patches to address these issues, but many organizations remain vulnerable. You can read our initial coverage from October 2023 here: Cisco Warns of Maximum-Severity Zero-Day Exploitation.
How Salt Typhoon is Exploiting Cisco IOS XE Vulnerabilities
The Chinese APT group Salt Typhoon (a.k.a. Earth Estries, GhostEmperor, UNC2286, RedMike) has leveraged these vulnerabilities to compromise more than a thousand Cisco devices worldwide.
Salt Typhoon has been actively exploiting Cisco IOS XE vulnerabilities since at least December 2024, with a series of attacks recorded in December and January. The group has previously targeted major U.S. telecommunications providers, including T-Mobile, AT&T, and Verizon, where it reportedly intercepted law enforcement wiretaps and presidential campaign communications. Additionally, Salt Typhoon has expanded its focus to research universities, such as UCLA and institutions in Argentina, Indonesia, and the Netherlands, many of which conduct telecommunications and engineering research.
Here are the key details regarding Salt Typhoon’s exploitation of Cisco IOS XE vulnerabilities:
- Exploited old and unpatched Cisco vulnerabilities to infiltrate telecom providers, ISPs, and research universities.
- Gained persistent access through Generic Routing Encapsulation (GRE) tunnels, allowing hidden data exfiltration.
- Conducted cyber-espionage activities, including intercepting communications from US law enforcement and presidential campaigns.
- More than 50% of compromised devices are in South America, India, and the United States.
Explore the free Industry Threat Landscape report available on SOCRadar LABS. This report presents an in-depth look at the latest cyber threats targeting various industries, inviting you to understand current risks and prepare your organization accordingly.
Industry Threat Landscape Report, SOCRadar LABS
What Can Organizations Do to Mitigate the Risk?
Given the severity of these vulnerabilities, organizations must act immediately to protect their systems. The Cyber Security Agency of Singapore (CSA) has also issued an alert detailing the risks and necessary mitigation steps. You can read their advisory here. Overall, here are the immediate steps to secure Cisco IOS XE devices:
- Update to the latest Cisco IOS XE version.
- Disable the Web UI feature if it is not required using the following commands:
noiphttpserver
noiphttpsecure-server
- Restrict access to the HTTP server by configuring ACL rules:
iphttpaccess-class75
iphttpsecure-server
!
access-list75permit192.168.0.00.0.0.255
access-list75denyany
- Monitor network traffic for signs of malicious GRE tunneling:
- Unexpected traffic from unfamiliar IPs.
- Encapsulated protocols like RDP or SMB.
- High data transfer volumes in log files.
- Analyze GRE traffic using Wireshark:
- Filter GRE Traffic: Use ‘display filter GRE’.
- Inspect the GRE Header: Look for unusual protocol types (e.g., IPv4 or IPv6).
- Check Encapsulated Payload: Expand the “Encapsulated Protocol” section to examine inner packets.
- Identify Tunnel Endpoints: Compare outer IP headers with NetFlow records.
Conclusion: Act Now to Secure Your Networks
The continued exploitation of Cisco IOS XE vulnerabilities by APT groups like Salt Typhoon underscores the urgency of patching and securing network infrastructure. Organizations should prioritize:
- Applying all necessary patches to Cisco devices immediately.
- Disabling unnecessary web-based management interfaces.
- Monitoring for anomalous network activity, particularly GRE tunneling.
- Implementing access control measures to limit exposure.
A proactive, continuous approach is essential to make this process easier and more reliable. This is where SOCRadar’s Attack Surface Management (ASM) module can help. By providing real-time visibility into your digital assets, SOCRadar ASM enables you to detect vulnerabilities and emerging risks across your entire network and even third-party vendors. With its continuous monitoring and intelligent threat insights, you can identify exposed assets, prioritize remediation, and ensure that your defenses are always ready for the latest vulnerabilities.
SOCRadar ASM module, Digital Footprint page
By combining your patching efforts with SOCRadar’s proactive security solutions, you can mitigate the risks posed by cyber campaigns like Salt Typhoon’s.
Citrix NetScaler Console Vulnerability (CVE-2024-12284) Also Demands Attention
Amid ongoing concerns about Cisco IOS XE threats, organizations should also be aware of a newly reported vulnerability affecting Citrix NetScaler Console. Cloud Software Group recently released updates to address CVE-2024-12284 (CVSS 8.8), a high-severity vulnerability affecting NetScaler Console and NetScaler Console Agent. This flaw arises due to inadequate privilege management, allowing authenticated attackers to execute unauthorized commands.
While exploitation is limited to users with existing access, organizations should prioritize external authentication configurations as a best practice. Affected users running NetScaler Console & NetScaler Agent 14.1 before 14.1-38.53 and 13.1 before 13.1-56.18 are advised to upgrade immediately. More details can be found in the official security bulletin.
Proactively Manage Vulnerabilities with SOCRadar XTI
With the constant rise of critical vulnerabilities, organizations need a proactive strategy to identify and manage emerging risks. SOCRadar’s Vulnerability Intelligence module provides timely insights into newly discovered vulnerabilities, offering detailed risk assessments and actionable intelligence.
SOCRadar’s Vulnerability Intelligence: CVE and exploitation trends, latest insights, critical alarms
By continuously tracking the latest vulnerabilities, including those in products like Cisco IOS XE and NetScaler Console, SOCRadar aids you in prioritizing patches, reducing your exposure, and ensuring your systems are always protected.




































