Cisco Warns of Exploitation of a Maximum Severity Zero-Day Vulnerability in IOS XE: CVE-2023-20198
[Update] October 24, 2023: “CISA Adds New IOS XE Vulnerability CVE-2023-20273 to Its Known Exploited Vulnerabilities Catalog.”
[Update] October 23, 2023: Cisco has released a patch for vulnerabilities affecting IOS XE devices. Additional information has been added to the blog post. See the patch section and the subheading: “New Zero-Day Vulnerability (CVE-2023-20273) Linked to Cisco IOS XE Exploitation Activity.”
[Update] October 18, 2023: See the subheading: “30,000 Devices Compromised in Cisco IOS XE Vulnerability Surge, and Various PoCs Are Spread”
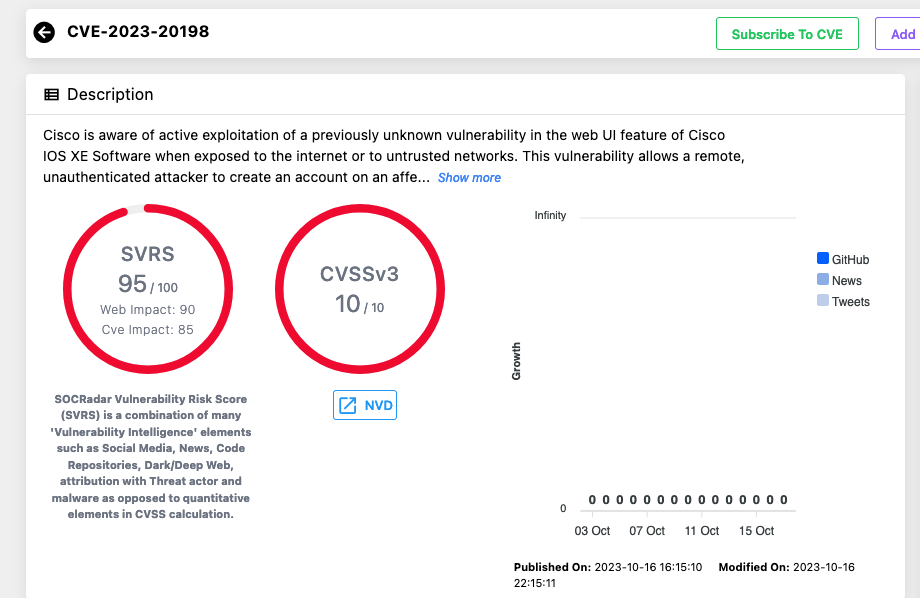
Cisco has released an advisory, acknowledging active exploitation of a previously undisclosed critical vulnerability. This zero-day, identified as CVE-2023-20198, holds a maximum CVSS score of 10.0 and is located within the web UI feature of Cisco IOS XE Software, which serves as the operating system for Cisco’s next-generation enterprise networking equipment.
What is the vulnerability in Cisco IOS XE about? (CVE-2023-20198)
Cisco has disclosed that the zero-day vulnerability represents a privilege escalation problem, allowing a remote and unauthenticated attacker to create an account on a vulnerable system with privilege level 15 access. This high privilege level provides unrestricted command access, which includes the ability to reload the system and modify configurations. As a result, the attacker can exploit this account to gain control of the affected system.
CVE-2023-20198 affects all Cisco IOS XE devices with the Web UI feature enabled, and the vulnerability can be exploited when the system is accessible via the internet or untrusted networks.
SOCRadar, by diligently monitoring digital assets, has already notified users affected by the vulnerability through its platform, offering proactive protection against CVE-2023-20198 in Cisco IOS XE.
How do attackers exploit CVE-2023-20198 to target Cisco IOS XE?
On September 28, 2023, Cisco discovered early indications of potentially malicious activity, with related activity dating back to September 18. The suspicious activity involved an authorized user creating a local account named “cisco_tac_admin” from the IP address 5.149.249[.]74. This activity ceased on October 1, with no other associated behavior.
On October 12, Cisco identified another cluster of related activity that began on the same day. Here, an unauthorized user created a local account called “cisco_support” from the IP address 154.53.56[.]231. Unlike the September incident, the October activity involved further actions, including deploying an implant written in Lua and consisting of a configuration file, “cisco_service.conf,” which defined a new web server endpoint for interacting with the implant and allowed the attacker to execute arbitrary commands.
The attacker used CVE-2021-1435, a command injection vulnerability in the Web UI component of IOS XE, to install the implant after gaining access to the device. Interestingly, Cisco reports that it has also observed the implant being installed on devices patched against CVE-2021-1435 through a yet ‘undetermined’ mechanism.
According to Cisco, it is likely that these clusters of activity originated from the same threat actor, with the October activity appearing to build upon the September activity.
Cisco Talos details the exploitation activity in a separate advisory, which you can find here.
Further notes by Cisco regarding the malicious implant, and how to detect it
To activate the implant, the web server requires a restart. Notably, in at least one observed instance, the server was not restarted, preventing the implant from becoming active, as highlighted by Cisco. The implant itself lacks persistence, allowing organizations to eliminate it by simply rebooting the device.
Conversely, the local user accounts that attackers can create through CVE-2023-20198 exhibit persistence, granting the attackers continuous administrator-level access to affected systems, even following a device restart.
Cisco Talos researchers advised organizations to remain vigilant for any suspicious users appearing on Cisco IOS XE devices, as potential indications of an exploited vulnerability. They also provided a command for organizations to verify the presence of the implant on any affected device:
curl -k -X POST “https[:]//DEVICEIP/webui/logoutconfirm.html?logon_hash=1”
If the request yields a hexadecimal string, it indicates the presence of the implant.
30,000 devices compromised in Cisco IOS XE vulnerability surge, and various PoCs are spread
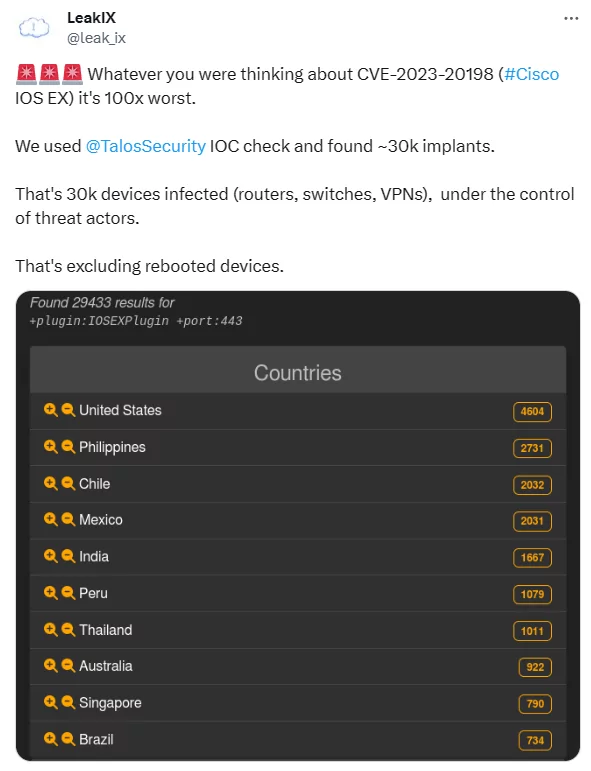
LeakIX (on X) reported that a Talos Security IoC check has confirmed the infection of at least 30,000 devices, including routers, switches, and VPNs, all under the control of threat actors exploiting CVE-2023-20198.
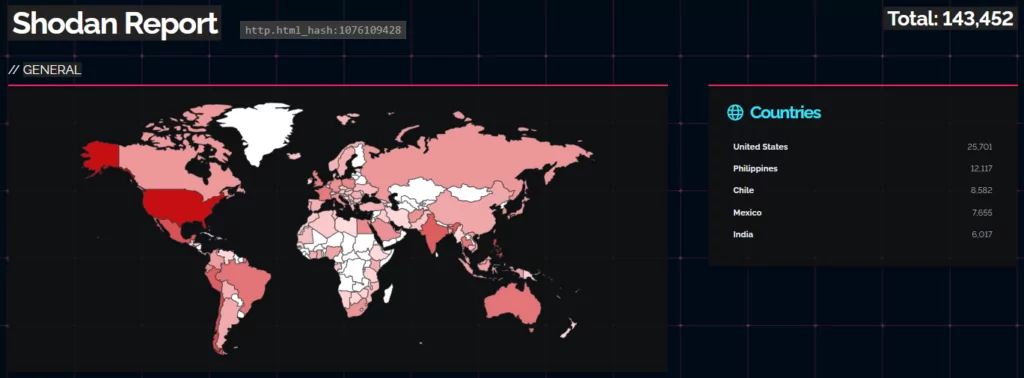
Simultaneously, a Shodan search revealed that more than 143,000 devices are exposed on the internet and susceptible to CVE-2023-20198.
Researchers have created a scanner to detect vulnerability indicators, aligning with Cisco’s IoC checks. This scanner sends an HTTP POST request to /webui/logoutconfirm.html?logon_hash=1 and checks for the presence of an 18-byte hexadecimal string in the response. The scanner is available on GitHub for public use.
Researchers have criticized that Cisco did not emphasize the fact that thousands of internet-facing IOS XE systems have already been compromised.
Attackers are utilizing the CVE-2021-1435 vulnerability to install the malicious implant, despite the fact that Cisco addressed this vulnerability in 2021. It is puzzling how attackers continue to find and exploit instances that remain vulnerable. This situation is concerning since attackers can combine this with the zero-day vulnerability, CVE-2023-20198, gaining privileged access to Cisco IOS XE while also infecting them.
New Zero-Day Vulnerability (CVE-2023-20273) Linked to Cisco IOS XE Exploitation Activity
The previously mentioned CVE-2021-1435 is no longer considered associated with this activity. Instead, Cisco reports that a previously undisclosed vulnerability, identified as CVE-2023-20273 (CVSS score: 7.2), has been exploited in conjunction with CVE-2023-20198 to deploy the implant.
After gaining level 15 privileges to the device and creating a local user, an attacker can utilize the unauthorized local user account to exploit CVE-2023-20273 in another component of the WebUI feature. This action permits the attacker to inject commands with root privileges, granting them the ability to execute arbitrary commands on the device.
On October 21, Onyphe reported that, although the number of exposed Cisco devices remains relatively constant, the number of devices compromised with an implant has decreased from over 40,000 to around 1,200. The significant change in numbers is believed to partly result from device reboots, as the implant cannot persist through reboots. Researchers also speculate that the threat actor behind the exploitation activity may have updated the implant to avoid detection.
CISA Adds New IOS XE Vulnerability CVE-2023-20273 to Its Known Exploited Vulnerabilities Catalog
CISA continues to monitor cybersecurity concerns and warn organizations, recently adding the high-severity vulnerability, CVE-2023-20273, to its Known Exploited Vulnerabilities (KEV) catalog. This new addition follows the previous listing of the Cisco IOS XE vulnerability, CVE-2023-20198, which continues to be a prominent target.
The agency emphasizes the critical nature of these vulnerabilities, recognizing them as “frequent attack vectors for malicious cyber actors.” As such vulnerabilities pose significant risks to the federal enterprise systems, organizations are strongly encouraged to apply necessary patches. The deadline for addressing CVE-2023-20273 is set for October 27, 2023.
Is there a patch available? How to mitigate the Cisco IOS XE vulnerability?
Now, patching Cisco IOS XE devices against these vulnerabilities is of utmost importance. Cisco has made patches available for both CVE-2023-20198 and CVE-2023-20273 starting on October 22. You can find the updates in this support advisory.
When the vulnerability was initially disclosed, no patching solutions were available, and Cisco strongly recommended taking action to mitigate the impact of the issue. The vendor advised customers to promptly disable the HTTPS Server feature on all their Internet-facing Cisco IOS XE devices to shield against potential exploitation.
According to Cisco, you can use the “show running-config | include ip http server|secure|active” command in the Command-line Interface (CLI) to determine if the HTTP Server feature is enabled on a system. This command checks for the presence of either the “ip http server” or “ip http secure-server” command in the global configuration. If either command is detected, it indicates that the HTTP Server feature is active on the system.
How to find Indicators of Compromise (IoCs) on Cisco IOS XE instances?
Cisco has outlined methods for detecting system compromise, which encompass the following recommendations:
- Check system logs for messages like “%SYS-5-CONFIG_P” or “%SEC_LOGIN-5-WEBLOGIN_SUCCESS,” specifically looking for new or unknown usernames.
- Examine logs for the message “%WEBUI-6-INSTALL_OPERATION_INFO” with an unfamiliar filename.
Cisco has also released some Snort rule IDs to detect exploitation activity:
- 3:50118 – Covers the implant installation (CVE-2023-20273).
- 3:62527 – Covers interaction with the implant, but not code execution.
- 3:62528 – Covers interaction with the implant, but not code execution.
- 3:62529 – Covers the passing of code into the installed implant.
- 3:62541 – Covers exploit attempts for initial access (CVE-2023-20198).
- 3:62542 – Covers exploit attempts for initial access (CVE-2023-20198).
For more details and the full IoCs, refer to Cisco’s official advisory.
Enhanced Vulnerability Monitoring with SOCRadar
SOCRadar consistently monitors security vulnerabilities, delivering timely intelligence crucial for safeguarding organizational assets.
With the Vulnerability Intelligence module, you can search for vulnerabilities, access comprehensive information about them, and track associated activities.
Furthermore, the Attack Surface Management module enables you to retrieve vital data about vulnerabilities affecting your assets.