Black Basta’s Internal Chats Leak: Everything You Need to Know
(21.02.2025) Update: List of Domains in Leaked Chats
(21.02.2025) Update: SOCRadar’s Intelligence Findings of Black Basta Leak, IoCs, TTPs, Victimology
Quick Summary:
- On February 11, 2025, a leak of Black Basta’s internal Matrix chat logs exposed conflicts within the group, allegedly linked to attacks on Russian banks.
- The leak mirrors previous ones, revealing leadership instability, low morale, and internal strife.
- Key members defected to rival groups, weakening Black Basta’s operations.
- SOCRadar’s preliminary findings provide critical IoCs, including IPs, domains, and hashes.
- These IoCs might help organizations detect and defend against Black Basta’s attacks but require further verification and research.
- Further investigation is ongoing, and the blog will be updated with more information as it becomes available.
If you want to check whether your IP address, domain, or email appears in these leaked communications, you can sign up for SOCRadar Free CTI.
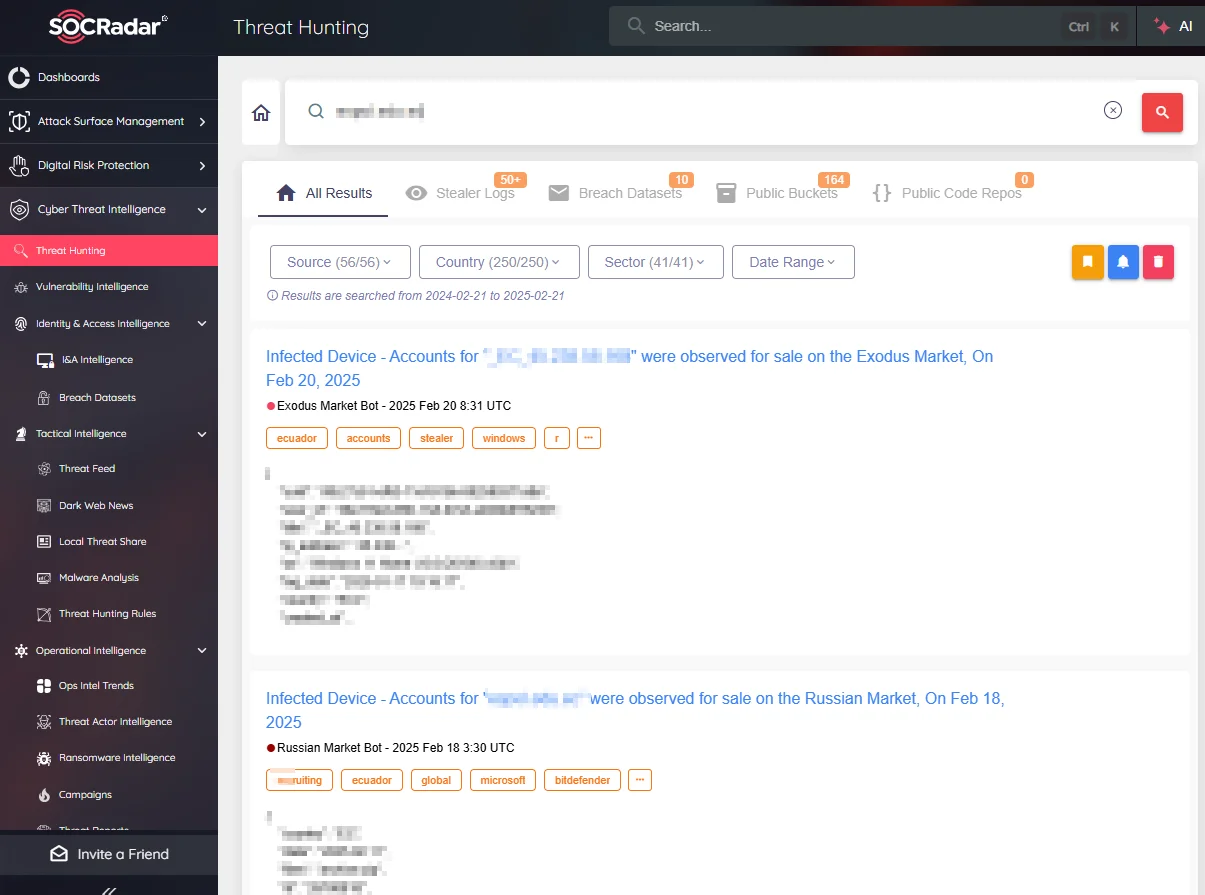
SOCRadar Threat Hunting allows users to search for domains found in logs, providing insights into their history, from marketplace sales to acquisition by ransomware groups.
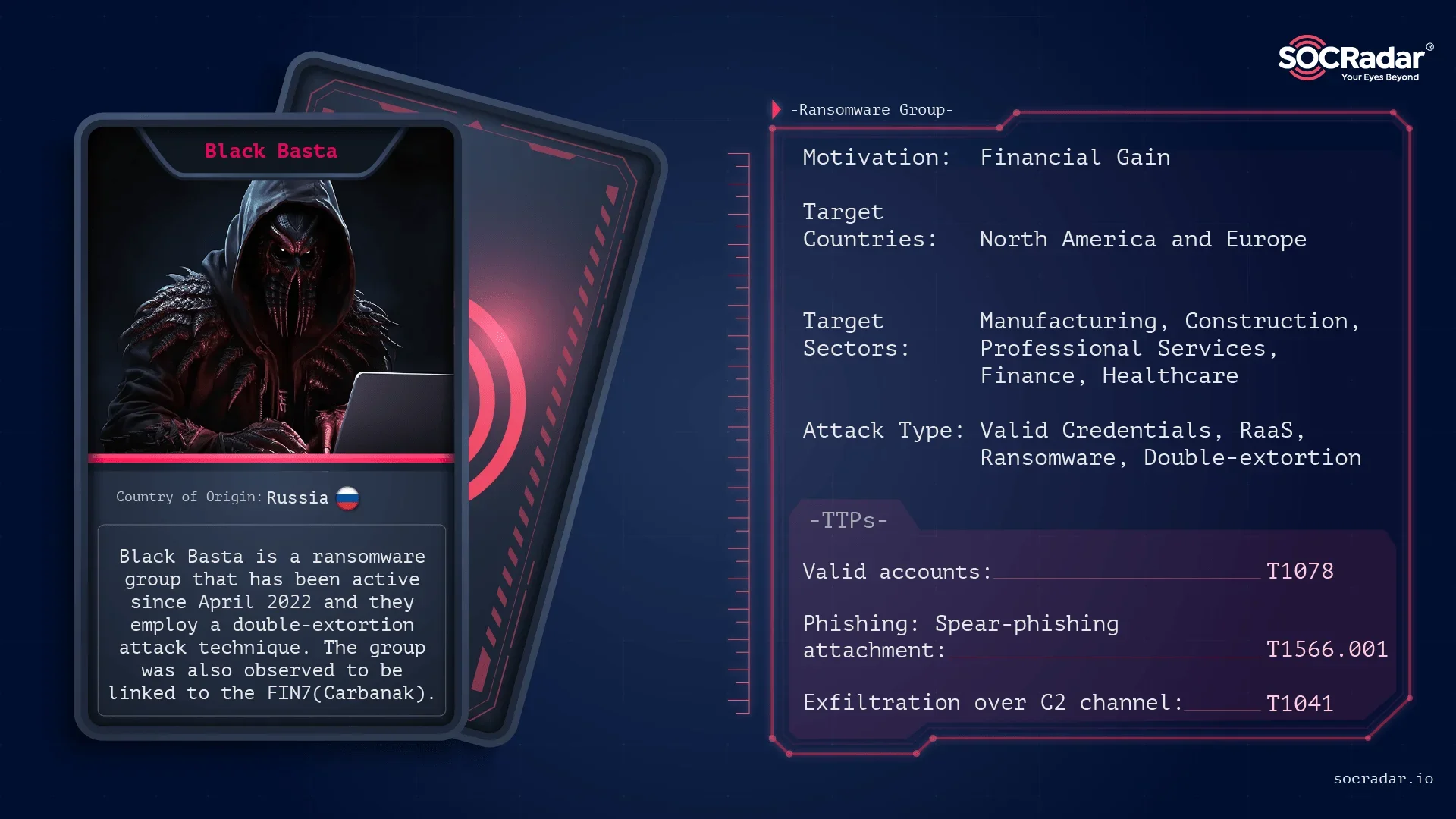
Black Basta’s Internal Chats Leak
The infamous Black Basta ransomware gang has once again found itself in turmoil. On February 11, 2025, a major leak exposed the group’s internal Matrix chat logs, allegedly because they targeted Russian banks. This leak echoes past incidents like the infamous Conti leaks, highlighting a recurring theme in the cybercriminal underworld: betrayal and internal discord.
Black Basta’s Decline and Internal Struggles
Although they never disclosed the reason for this move, cyber threat intelligence firm PRODAFT suggested today that the leak might be directly linked to the ransomware gang’s alleged attacks on Russian banks.
As PRODAFT stated, Black Basta—also tracked as Vengeful Mantis—has been largely inactive since the beginning of the year. The primary reason? Internal conflicts and deception among its own ranks. Some operators reportedly scammed victims by collecting ransom payments without providing functional decryptors, further damaging the group’s reputation.
Moreover, Black Basta’s ransomware has been deemed less effective compared to other major groups. This inefficiency, combined with leadership instability, led several key members to defect. Many have since joined rival cybercriminal operations, including Cactus Ransomware and other illicit enterprises.
Chat leaks in a Telegram channel
A pivotal figure in Black Basta’s downfall is ‘Tramp’ (LARVA-18), a notorious threat actor responsible for operating a large-scale spamming network used to distribute QBOT malware. His influence within the group fueled internal tensions, further destabilizing an already fragile operation.
The Leak: A Repeat of Conti’s Fate?
The recent chat log leak follows a familiar pattern. Much like the infamous Conti leaks, an insider—disgruntled with the gang’s operations—decided to expose sensitive internal communications. The leaker’s justification? Retaliation against Black Basta’s targeting of Russian financial institutions.
The Conti Ransomware gang faced a similar fate back in the day when an insider leaked over 60,000 internal chat messages in retaliation for Conti’s public support of Russia’s invasion of Ukraine. The leaks provided unprecedented insight into the group’s operations, financial transactions, and inner conflicts. Now, Black Basta follows suit, proving that even the most formidable cybercriminal organizations are not immune to betrayal and exposure.
According to 3xp0rt, a Cyber Threat Intelligence Analyst at PRODAFT, the leaked chat logs span from September 18, 2023, to September 28, 2024, revealing critical details about the group’s internal dynamics:
- Lapa, a key administrator, was constantly burdened with administrative tasks and frequently insulted by his boss. Despite his high-trust role, he earned significantly less and seemed to rely on ransom payments for financial support. Under his administration, brute-force attacks were launched on Russian banks, raising concerns about potential retaliation from law enforcement.
- Cortes, linked to the Qakbot group, distanced himself from the attacks on Russian banks, seemingly surprised that a Russian group would target its own country. This might explain Qakbot’s lack of participation in these attacks.
- YY, another administrator, handled support tasks and was well-compensated. However, the arrest of Black Basta’s leader posed serious risks to the group. Operations were seemingly dictated by Oleg, the group’s boss, with little regard for the team’s interests.
- Bio, formerly known as Pumba while working in Conti, managed high-level risks and disputes over payments. His recent arrest likely caused distress among Black Basta’s members.
- Trump, GG, and AA were aliases used by Oleg Nefedov, Black Basta’s boss, according to Bio’s statements in the leaked chats.
Final Thoughts: The Self-Destructive Nature of Cybercrime
While Black Basta once ranked among the most formidable ransomware groups, its internal chaos has significantly weakened its operations. The combination of ineffective ransomware, leadership disputes, and high-profile leaks has made it increasingly difficult for the group to sustain itself.
As history has shown with Conti and other ransomware syndicates, cybercriminals often become their own worst enemies. Their hunger for profit and lack of trust ultimately lead to their downfall—one betrayal at a time.
Stay ahead of cyber threats with SOCRadar’s continuous monitoring and threat intelligence services. Keep your organization protected from emerging ransomware tactics and underground activities.
SOCRadar’s Intelligence Findings of Black Basta Leak, IoCs, TTPs, Victimology
This finding serves as an update to our existing story on Black Basta. The findings shared here are based on preliminary information and provide additional context to the group’s recent activities. As our investigation continues, we will update this blog with new insights and more detailed analysis if necessary. Please check back for further updates as new information becomes available.
IoCs for Black Basta Group (IP Addresses, Domains, Hashes, Malicious Files, etc.)
IP Addresses
- 95.216.29.185 (Various ports: 4743, 4747, 4750, 4755, 4758, 4761, 4763, 4768, 4769, 4773, 4774, 4775, 4776, 4779, 4782, 4783, 4797, 4798, 4799, 4800, 4804, 4807, 4822, 4824, 4826, 4827, 4829, 4831, 4838, 4843, 4844, 4855, 4881, 4888, 4892, 4896, 4899, 4901, 4911, 4912, 4921, 4922, 4924, 4925, 4932, 4939, 4941, 4944, 4949, 4955, 4962, 4964, 4966, 4967, 4969, 4982, 4983, 4986, 4989, 4990, 4991, 4993, 4994, 4996, 4997, 5006, 5016, 5018, 5022, 5024, 5025, 5026)** – False IP, VPS IP
- 109.107.182.10 – 109.107.182.19 (Server IPs with root access)
- 5.8.18.20 (SSH access, VPN usage)
- www.dandh.com (Access IP related to Cisco VPN)
- 13.57.243.97 (Used for Shell, SOCKS, and FTP services)
- 131.228.32.204:443,38.81.3.13:443, 8.39.107.12:443, 199.33.86.13:443, 80.169.86.90:443, 213.242.92.6:443, 138.99.0.106:443, 212.123.201.244:443, 198.11.114.20:443, 212.84.43.187:443, 180.178.67.130:443, 208.87.12.200:443, 103.117.255.8:443, 208.87.14.110:443, 208.87.12.10:443, 216.245.80.8:443, 203.206.180.163:443, 69.26.105.196:443, 164.47.3.5:443, 52.202.132.150:443 – Target IP ports
Domains
- bestflowers247.online (Primary communication infrastructure)
- innophos.com (Attempted attack on company infrastructure)
- russellco.vdi.zone (Targets within systems)
- sheeheyvt.local (Targets within systems)
- vdi.bargatemurray.com (Botnet connections)
Hash Values
- c5793613219a782eb08205921a3f9ed97c2c74de18e0cd36008046d1a5e1288e (Remcos RAT)
- 0fd52ebb37e4e5c41756133e47215547478097f9a6ff170cc442cb21276e3f36 (Remcos RAT)
- 6a5702c106666c1b89bcb12a450d393e6506fa387865328d06e1e230d4782548 (Remcos RAT)
- 50d414576bf441cca754e6e3b96dabdf35fed443ecb98f865dc89e623bc2f0e9 (Agent Tesla)
- e19dfc72ad2eea815ef6b4eb9b812471b3bb3cf40333d97e3c552c87db86e65a (Formbook)
- 47480cd2666b1a60419731fe9795afb8a9a386079118c6a2509da375ad5aa19d (Formbook)
- 8589fd14aab509787fcfef35543a634aea6db383ff617176a35a7cede8c38031 (Malicious file)
Malicious Files
- CVE-2022-27925-zimbra_Revshell.zip (Zimbra Exploit)
- rundll32.exe dll.dll,Enter (Malicious DLL execution method)
- drs1312_signed.zip (Possible malware)
- e6393196-f020-4c2f-88fc-45ff7e22794f_encrypt_release_allsystem_x64.zip (Encryption tool, potentially related to ransomware)
The IoCs identified in this analysis provide critical data on the Black Basta group’s infrastructure and attack methods. The IP addresses, domains, hashes, and malicious files listed here offer essential information for threat hunting and enhancing detection capabilities. These indicators can help better understand the group’s operations and improve defensive strategies against potential attacks.
This information can also be used to improve security measures, identify compromised systems, and track the group’s infrastructure more effectively.
Black Basta Group Targets (Organizations, Industries, Systems)
Targeted Organizations: The organizations listed below were identified in leaked logs as having been targeted by the Black Basta group. These are not the group’s entire list of victims, but they represent those observed in the specific logs:
- Financial and insurance companies
- Energy and utilities firms
- Automotive and manufacturing companies
- Security and defense organizations
- Postal and logistics services
- Accounting and auditing firms
Targeted Industries: The following industries have been observed as specific targets in leaked logs from the Black Basta group:
- Finance & Insurance: Financial institutions and insurance companies have been targeted, including those with high-profile services.
- Energy & Utilities: Energy companies, especially those in the oil, gas, and renewables sectors, were affected.
- Manufacturing & Automotive: Manufacturing firms, including those involved in the automotive sector, have experienced targeted attacks.
- Security & Defense: Companies involved in national security and defense have been compromised.
- Postal & Logistics: National postal services, along with logistics providers, were included in the targeted sectors.
Targeted Systems: The systems listed below were targeted according to the leaked logs:
- Citrix & RDP Servers: Access to critical business services and internal networks was achieved via these platforms.
- VPN Portals: The group exploited vulnerabilities in VPN systems to gain unauthorized access.
- FTP & SOCKS Proxies: These servers were used for data exfiltration and remote access.
- Active Directory Systems: Internal directory services were targeted to manage and control user access.
These targets are based on the leaked logs, which provide specific information on the breaches. However, they do not represent all the organizations or industries affected by the Black Basta group.
Black Basta Group Attack Techniques and Tools
Based on the leaked logs, the Black Basta group has demonstrated a broad range of sophisticated attack techniques, tools, and exploits in their campaigns. These actions have primarily targeted organizations in various sectors such as finance, energy, and manufacturing, using tactics that involve privilege escalation, lateral movement, and Remote Code Execution (RCE). Below are the key techniques and tools identified from the logs.
Attack Techniques:
- Privilege Escalation & Persistence:
- Mimikatz & Credential Dumping: Used to extract Windows credentials from the LSASS process, facilitating access to sensitive systems.
- DLL Injection & Process Hollowing: Malicious code is injected into legitimate processes, allowing the group to maintain a foothold without detection.
- Windows Scheduled Tasks & Registry Manipulation: Changes to the Task Scheduler and system registry ensure persistence by enabling the group to regain access even after initial removal attempts.
- Lateral Movement:
- RDP & Citrix Usage: With stolen credentials, the group establishes RDP and Citrix sessions to move across internal networks, making it easier to exfiltrate data or deploy further attacks.
- VPN & Proxy Tunnels: The group bypasses firewalls using VPN login details and sets up SOCKS proxy or SSH tunnels to facilitate secure internal communication and data transfer.
- Remote Code Execution (RCE):
- Microsoft Outlook Zero-Click RCE Exploit: Exploits a vulnerability in Microsoft Outlook to run code on a target system without user interaction.
- Windows 10 Sandbox Escape & ASLR/DEP Bypass: Targets flaws in Windows 10 to execute remote code and escape the sandbox environment by bypassing ASLR and DEP protections.
- Juniper SRX Firewall RCE (Zero-Click Exploit): Allows remote exploitation of Juniper SRX firewalls, requiring no authentication, granting direct access to the target network.
- Malware & Tools:
- Cobalt Strike: Used for managing attack infrastructure and establishing Command and Control (C2) communication with compromised systems.
- AgentTesla & Formbook: Keyloggers and credential stealers designed to capture sensitive information from victims.
- Custom Python Reverse Shell: Custom scripts used to create reverse shells, allowing the group to maintain remote control over compromised systems.
- Ransomware:
- Black Basta Ransomware: Deployed to encrypt files on target systems, using the .basta file extension after encryption. Ransom demands are issued for decryption keys, with the malware observed in a specific encrypted file named e6393196-f020-4c2f-88fc-45ff7e22794f_encrypt_release_allsystem_x64.zip.
Exploits and Vulnerabilities Used:
- Microsoft Outlook RCE: A zero-click exploit that executes malicious code on Windows systems via Microsoft Outlook, bypassing the need for user interaction.
- Juniper SRX Firewall RCE: A zero-click vulnerability that allows attackers to gain unauthorized access to Juniper SRX firewalls without authentication.
- Windows 10 ASLR/DEP Bypass: Exploits weaknesses in Windows 10, enabling the attackers to execute remote code and bypass virtual machine protections.
- D-Link NAS Auth Bypass: An exploit targeting D-Link NAS devices that provides unauthorized access to these systems, further expanding the attack surface.
These attack techniques have been verified through analysis of logs from targeted systems. The use of these sophisticated methods allows Black Basta to gain initial access, escalate privileges, move laterally within networks, and deploy ransomware—all while maintaining persistence and evading detection.
Ransom Demands and Negotiation Process
Ransom Amount:
- Initial Offer: $479,000
- Final Offer: $1,750,000 (Negotiated at a 50% discount)
- Payment Deadline: Discount applied if payment is made within 48 hours.
Initial Offers & Company Responses:
- Black Basta’s Initial Demand: $1,750,000
- Company’s Counteroffer: $1,000,000
- Negotiation Progress: Throughout the negotiation, demands increased, and companies were pressured into payment.
Payment Strategies:
- Discount Offer for Quick Payment: 20% discount offered for faster payments.
- Extension of Payment Deadlines: Payment deadlines were extended for higher ransom amounts.
- Threats of Data Leakage: Some victims failed to pay and were threatened with data leaks.
Ransom Notes and Threats:
- Data Leak Threats: Victims were warned that their data would be leaked if ransom was not paid.
- Timer Usage: A timer was used to threaten the victim with data release.
- Messages: Messages included “an automatic decryption key will be provided post-payment,” although there were also discussions suggesting manual intervention.
Cryptocurrency Wallets and Payment Methods
Cryptocurrencies Used:
- Bitcoin (BTC)
- Monero (XMR)
- Tether (USDT – TRC-20)
Wallet Addresses:
- Bitcoin (BTC):
- bc1qfn6vndc6mhlvvtx54ehyq7z6vel8kkctj0e0sa
- bc1qvwntvw5sxtsavaya85up958pjn2eysaqcflffe
- bc1qn0z8etys62cljzwjxl80k9y5nag7pq42s9lyes
- bc1qsvukyqlpxpnzhedsxeyp7mmza3d9c43fslvs5e
- bc1qyu9vwxthn2s0zhe8rqae5m2mg0w7lct3fxkk96
- bc1qj8k6hx9xz2rv5usvt4r2fs5agyudhr5uzxcle8
- bc1qyvaa2uwwgf34m3qggzmptcrm45tppfppyhhhde
- Monero (XMR):
- 84JskFBoUddXz1bUn329NeSLw7rfxZkbJiQN7eJdtkDvZDHTPMvHEJkDGNaW47sQfC9jaQ4EDFkgxGJxof4uEgonCdY2HnK
- 88M7PZfDZSs3DWB6BY99uKVcnSFAsHr6eEhPmBD2psSyU6hv4EHYB6cGjpysZwEbQKTHCz3JfsiWMZLiDMoZZMSKQddFS66
- 86e6VhUFFHdZDrm4QJHag915m4zGxuXsi3UAyGpTDsPR4CLCnvmJ7zzanmx7Q7KJg846ZrmT911TBEMAZQq24Kqn2xpPqVZ
- Ethereum (ETH):
- 0x010165F27A933Ac77534Ee72CE58550dC241AB16
- 0x2b48f85312a7e6F952A773e1234cB340FD472D9e
- Tether (USDT – TRC-20):
- TCws332kET8czTuhcBemmmeSrCbTDb2nyD
- TNgjeQgr8dPSwK2UkhFtNpGK795cJ3yKjL
The Black Basta group attempts to maximize ransom payments through strategic negotiations, using pressure tactics and various methods to ensure anonymity and facilitate money laundering. Bitcoin, Monero, and Tether (TRC-20) are actively used for these transactions. The listed wallet addresses are tied to ransom payments and possible money laundering activities, highlighting the group’s complex financial operations.
Black Basta Group Leaders and Executive-Level Members
Below are the leaders, managers, and notable members affiliated with Black Basta.
Identified Key Users
| Username | Role/Task | Relevant Conversations & Notes |
| @usernamegg | Potential Leader/Manager | Active in technical discussions, operational management, and negotiations |
| @n3auxaxl | Technical Lead/Developer | Discusses ransomware (locker) development, backdoors (backdoor) |
| @staffer | Group Coordinator | Organizes various operations |
| @cameron777 | Senior Member | Manages server accesses, Citrix systems, and AD DS (Active Directory) |
| @usernameboy | Authorized Member | Active in system access and password management |
Leadership Structure
- @usernamegg plays a prominent role in technical operations, negotiations, and overall group management.
- @n3auxaxl focuses on developing ransomware and specialized tools for attacks.
- @staffer is responsible for overseeing and coordinating operations.
- @cameron777 manages system accesses and infrastructure-related tasks.
Black Basta’s leadership structure places @usernamegg at the forefront, with @n3auxaxl handling technical development, @staffer overseeing operational activities, and @cameron777 directing system access and planning.
Black Basta Group’s Internal Disputes and Issues
Below are the key disputes, payment problems, and internal conflicts within the Black Basta group, highlighting tensions among leaders and senior members.
Disputes Over Payment and Profit Sharing
There have been significant issues related to payments within the group, particularly concerning the coding team. Leader @usernamegg pointed out problems with payments made to the coding team (MAKAP – coder ssd), where a 10% payment was expected, but only 5% was offered, and payments were delayed. Complaints such as “You promised the money, but it hasn’t arrived yet” were raised, with leaders disputing who should be paid first.
Tensions Between @nickolas and @usernamegg
@nickolas expressed a desire to remove a member from the leadership team, stating, “I don’t think they will make decisions, so I will slowly exclude them.” @usernamegg opposed this idea, emphasizing fairness and stating, “You must be fair, they need to prove their worth.” @nickolas implied that the member would be excluded for not contributing enough.
Disagreements Over Commercial Decisions
@nickolas also noted conflicts about contributions from team members and disagreements over business relations within the group. He said, “We are just defending our commercial interests, but changing working conditions abruptly and claiming ‘the rules are different now’ is pure manipulation.” He further commented on the lack of loyalty in situations where significant effort had been invested.
Questions Around New Member Hiring and Management Disagreements
@usernamegg raised doubts about the hiring of new members, questioning, “What exactly are we going to do? Is this person suitable for the team?” There was a lack of clarity about the roles of new members and concerns over how they would be integrated into the team.
Technical and Operational Issues
Conflicts Over Target Selection
Tensions also arose between @usernamegg and @n3auxaxl over the selection of attack targets. @usernamegg expressed concerns about the risks involved with a target, stating, “This target is too big, I don’t want to take the risk.” In contrast, @n3auxaxl emphasized the high potential reward, saying, “But the potential gain is very high, it’s worth trying.” The team exhibited differing approaches to risk and reward in their operations.
Disagreements on Server and Infrastructure Choices
@usernamegg raised concerns about the reliability of some server providers, asking, “These servers are suspicious, should we switch to another provider?” There was internal debate within the technical team regarding preferred providers and risk management strategies.
Potential Internal Threats Within Black Basta
Below are the internal security issues, including trust concerns, data leaks, and potential threats originating within the group.
Suspicious Behavior and Data Leaks
There have been signs of internal information leaks, particularly involving @nickolas. Discussions about “data leaks” and members systematically pulling data have raised alarms. @nickolas mentioned, “They collect all the leaks themselves, and you get access to everything with one request.” There are indications of a system collecting leaks, though its management remains unclear.
Distrust Between @usernamegg and @nickolas
@usernamegg has openly stated that he doesn’t fully trust some members of the group, suggesting that access levels should be reassessed. He questioned, “Are we sure about who has what kind of access?” There was a discussion about potentially lowering access levels or restricting access for certain users.
Concerns Over ‘Moles’ Within the Group
@lapa mentioned, “Yes, it’s a data aggregator,” hinting at the presence of a system that gathers data. There were concerns whether this system was under the control of external authorities, such as the FBI or other security agencies. The group raised the question, “Are we sure who controls this system?”
Potential Internal Sabotage and Threats
There have been allegations of unauthorized access to servers and suspicious activities within the team. A comment was made about “some RDP sessions being opened at times we didn’t know about.” These sessions were accessed without the knowledge of administrators, though the identity of the user is still unclear.
Suspicion of Code Manipulation for Sabotage
There were suspicions that changes had been made to the group’s code. The question “Why was a change made in the code?” arose, with speculation that someone could have altered the code to allow for identification of group members. There were concerns that certain ransomware modifications might have been intentional..
Black Basta’s Data Collection and Leak Analysis System
Below is a description of the system used by Black Basta to collect and analyze stolen data and leaks.
Identified System and Usage
System Name (Temporary): “Aggregator / Parser System”
Function: This system is used to analyze stolen credentials, data leaked from ransomware-encrypted systems, and information obtained from darknet markets. It operates over VPN, proxy, and SOCKS5 connections and updates data at regular intervals. The system is said to process stolen information more quickly for validation and analysis.
Technical Structure and Logs
The system operates on a Windows-based structure distributed across different machines. Integration with traditional log collection systems such as Splunk or Graylog may exist.
Internal Threats and Security Concerns
Some members have raised concerns about the security of the system. @usernamegg questioned, “Are we sure who controls this system?” @nickolas expressed concerns that too much data is being pulled, hinting that the system may be compromised. There are suspicions that it might have been taken over by external entities, such as the FBI.
Black Basta uses a specialized system to process stolen data and credentials. However, there are doubts about its security, with internal conflicts over who controls the system. These issues raise concerns about the possibility of an internal threat compromising the group’s operations.
List of Domains in Leaked Chats
Once again, the blog post has been updated with an extensive list of samples found in Black Basta’s chats. Organizations can use this list to analyze and assess potential threats related to their infrastructure. Researchers and cybersecurity professionals can also leverage this information to enhance their investigations and refine threat detection strategies.
The post will continue to be updated as more information becomes available.