
Seraph Stealer Malware Hits the Market, Black Basta’s Internal Chaos, New Data Leak Claims
Cybercriminal activity continues to escalate on hacker forums, with SOCRadar’s Dark Web Team identifying several key threats this week. Notable discoveries include the alleged breach of Al Hilal SFC, exposing sensitive financial records, and a disputed data sale linked to Free Mobile, which may be a reappearance of an old breach. Additionally, a hacker claims to have exploited a vulnerability in Investing.com, leading to a large-scale data leak. Other concerning trends include the rise of the Seraph Stealer malware, the sale of stolen Japanese credit cards, and leaked internal chat logs from the Black Basta ransomware group, exposing internal conflicts.
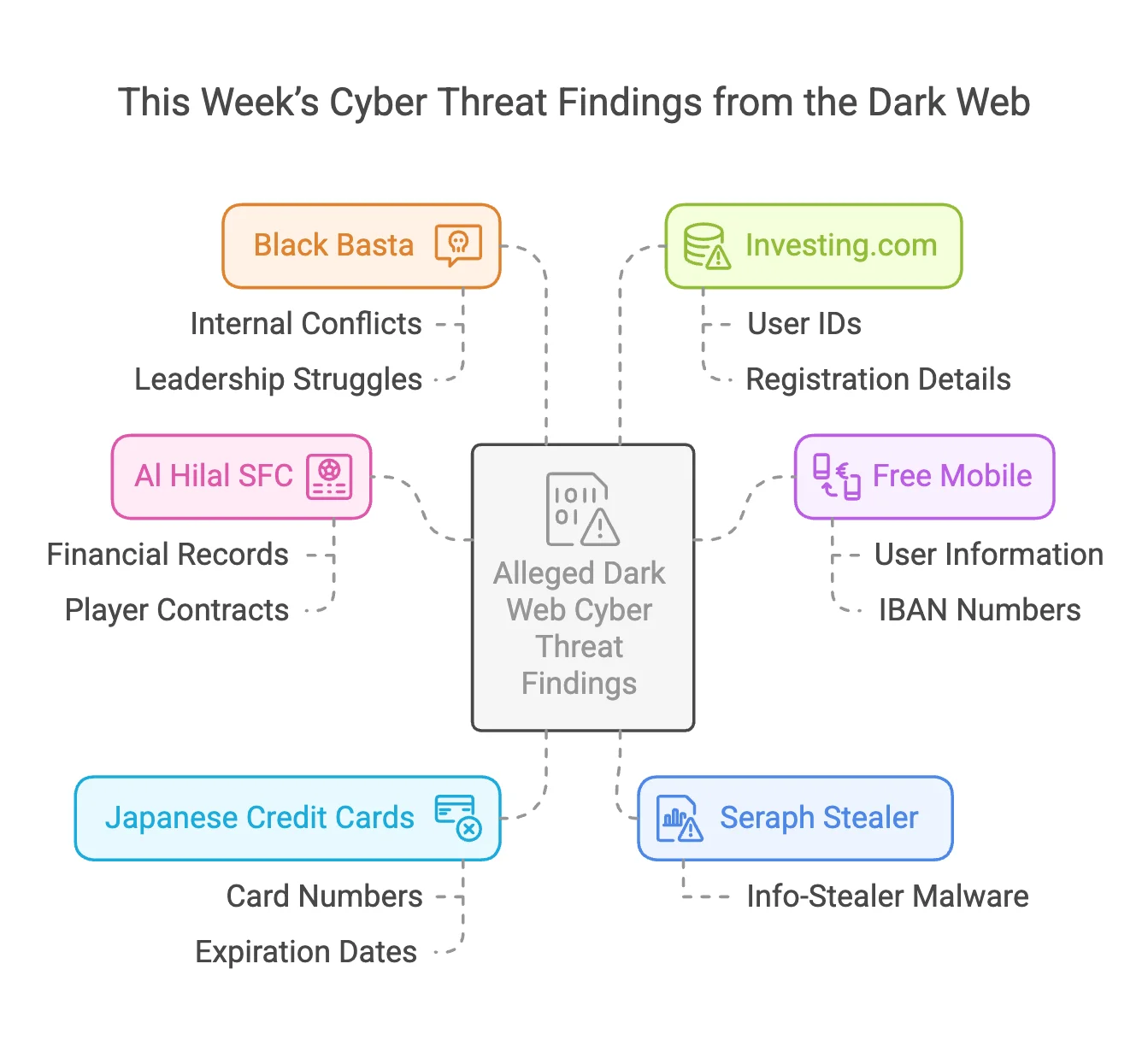
SOCRadar Dark Web News: Key highlights of this week’s detected threat actor activities
Receive a Free Dark Web Report for Your Organization:
Alleged Data of Al Hilal is Leaked
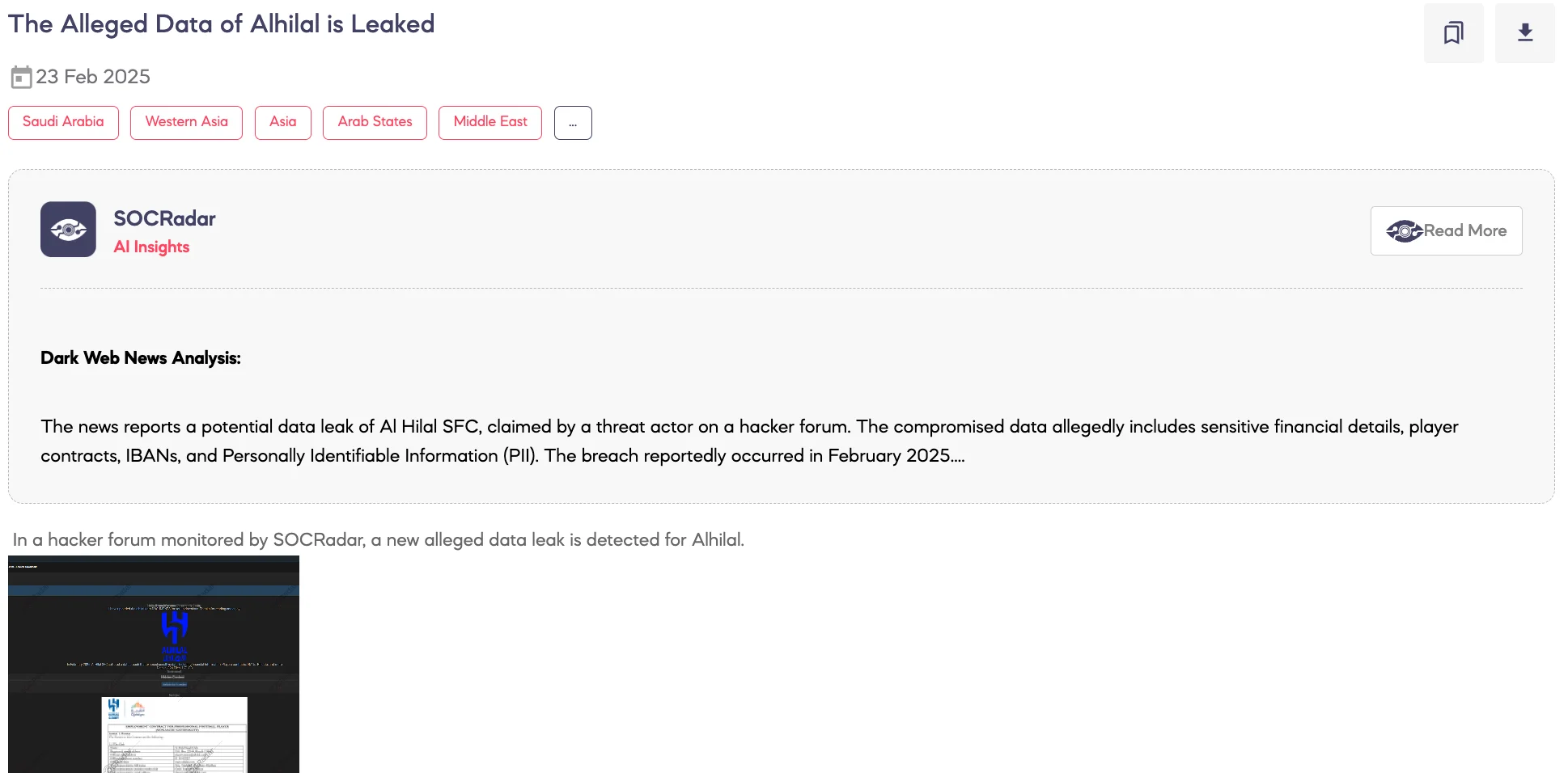
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to have leaked sensitive data allegedly associated with Al Hilal SFC. According to the threat actor, the February 2025 breach exposed financial records, player contracts, IBANs, Personally Identifiable Information (PII), and other confidential data.
Al Hilal Saudi Football Club (Al Hilal SFC) is a professional multi-sports club based in Riyadh, Saudi Arabia.
Alleged Customer Database of Free Mobile is on Sale
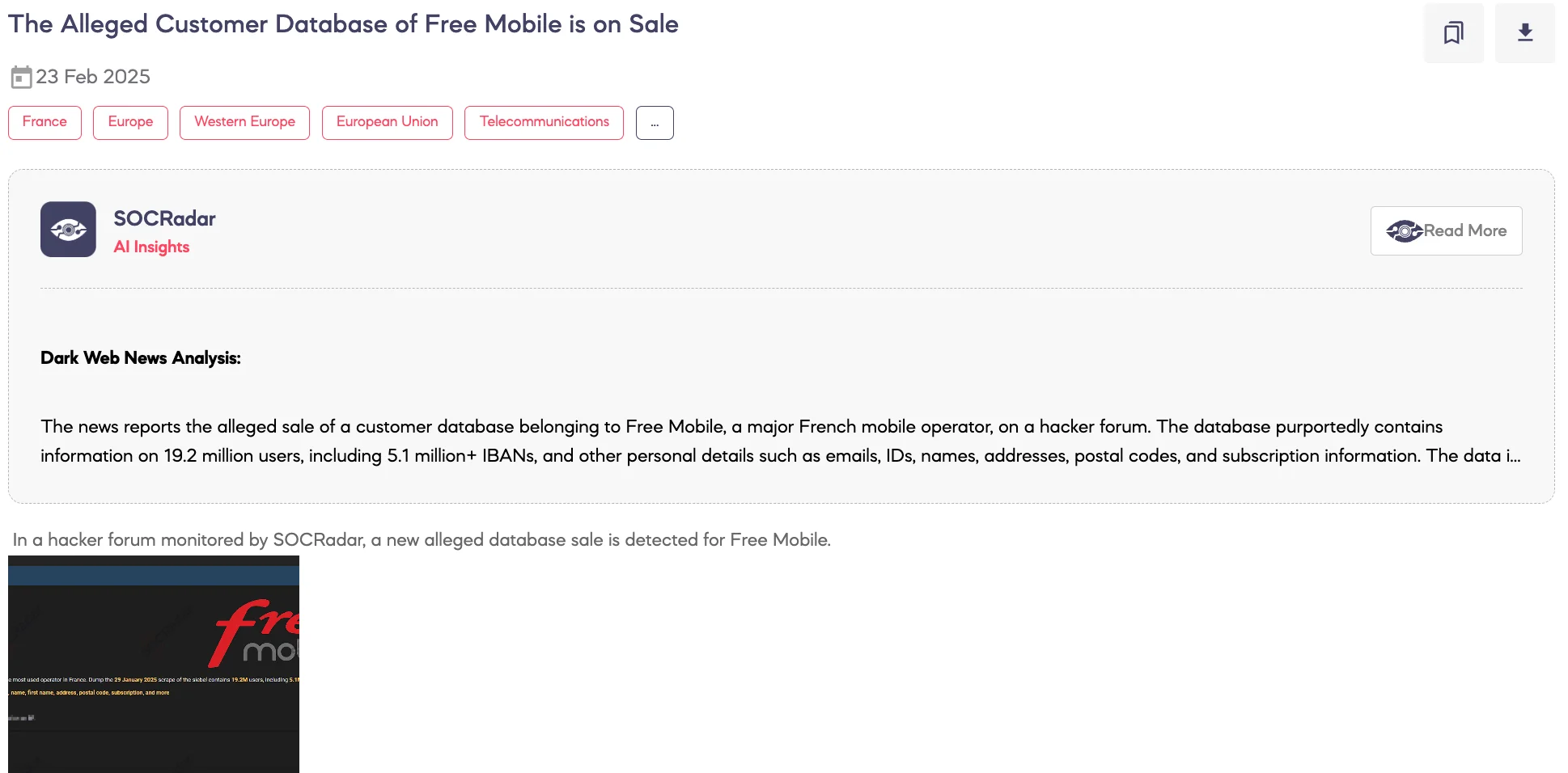
February 23, 2025 a hacker forum post in which a threat actor claims to be selling an alleged Free Mobile database
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling an alleged database of Free Mobile, a major telecommunications provider in France. According to the post, the dataset allegedly scraped on January 29, 2025, contains information on 19.2 million users, including 5.1 million IBAN numbers. The exposed data reportedly includes email addresses, user IDs, names, postal addresses, subscription details, and additional personal information.
This is not the first time such a claim has appeared on the same hacker forum. A similar post was shared on October 21, 2024, allegedly offering an identical dataset with the same 19.2 million records and 5.1 million IBANs, but under a different username and breach date.
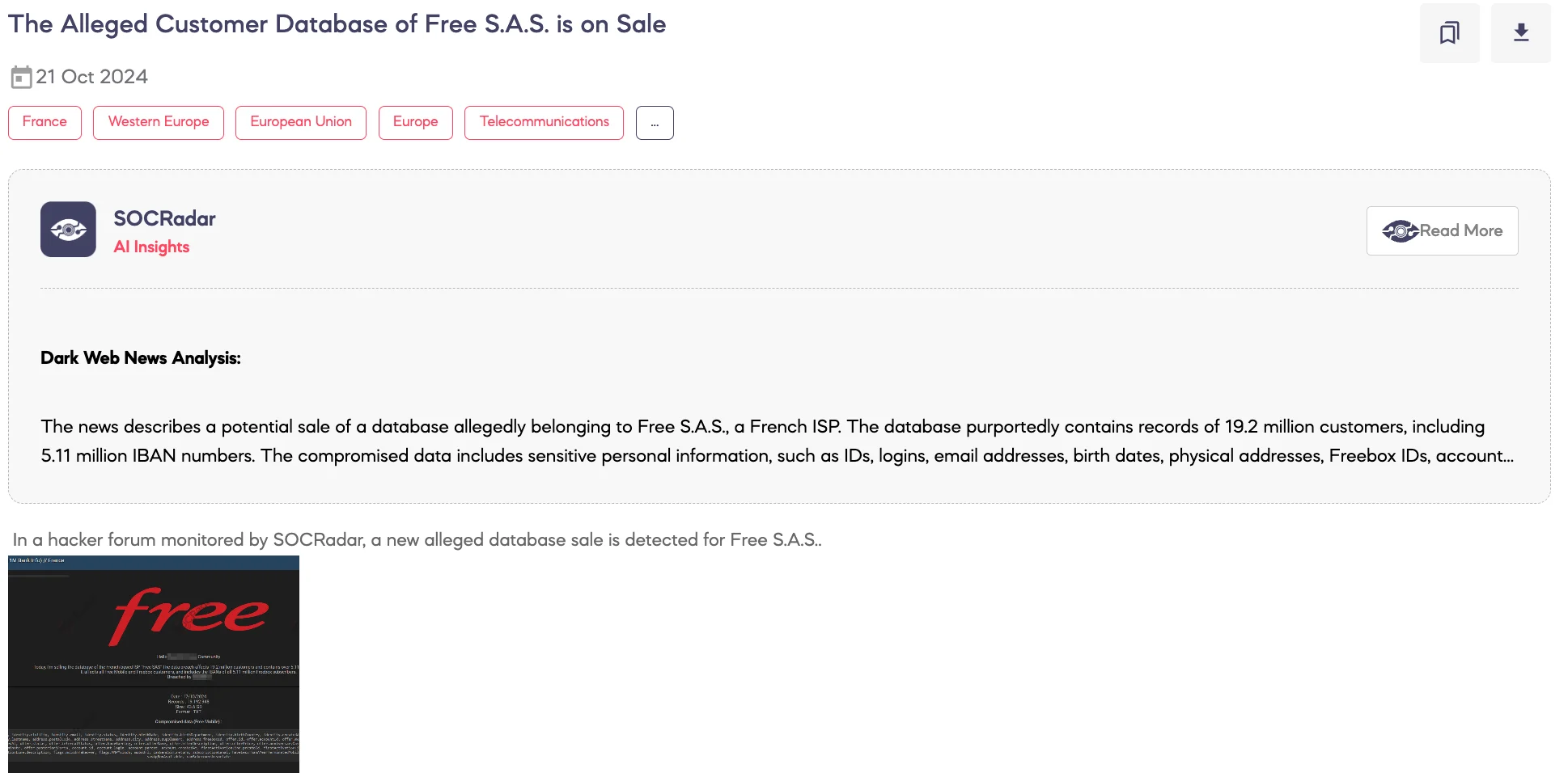
October 21, 2024, a previously shared forum post by a different threat actor allegedly offering the similar Free Mobile dataset for sale
If the dataset is valid, the recurring appearance of similar database sales under different threat actor accounts suggests that either:
- The data has been previously leaked and is being resold repeatedly under new identities to make it appear as a fresh breach.
- Multiple actors have obtained access to the same dataset, attempting to monetize it separately.
- The breach may be exaggerated or manipulated to generate interest among buyers.
Such tactics are common in underground forums, where old databases are often repackaged and redistributed to mislead potential buyers. Organizations should investigate whether this dataset is new or a re-emergence of previous leaks to assess the actual risk level.
Alleged 300 Credit Cards Belonging to Japan are on Sale
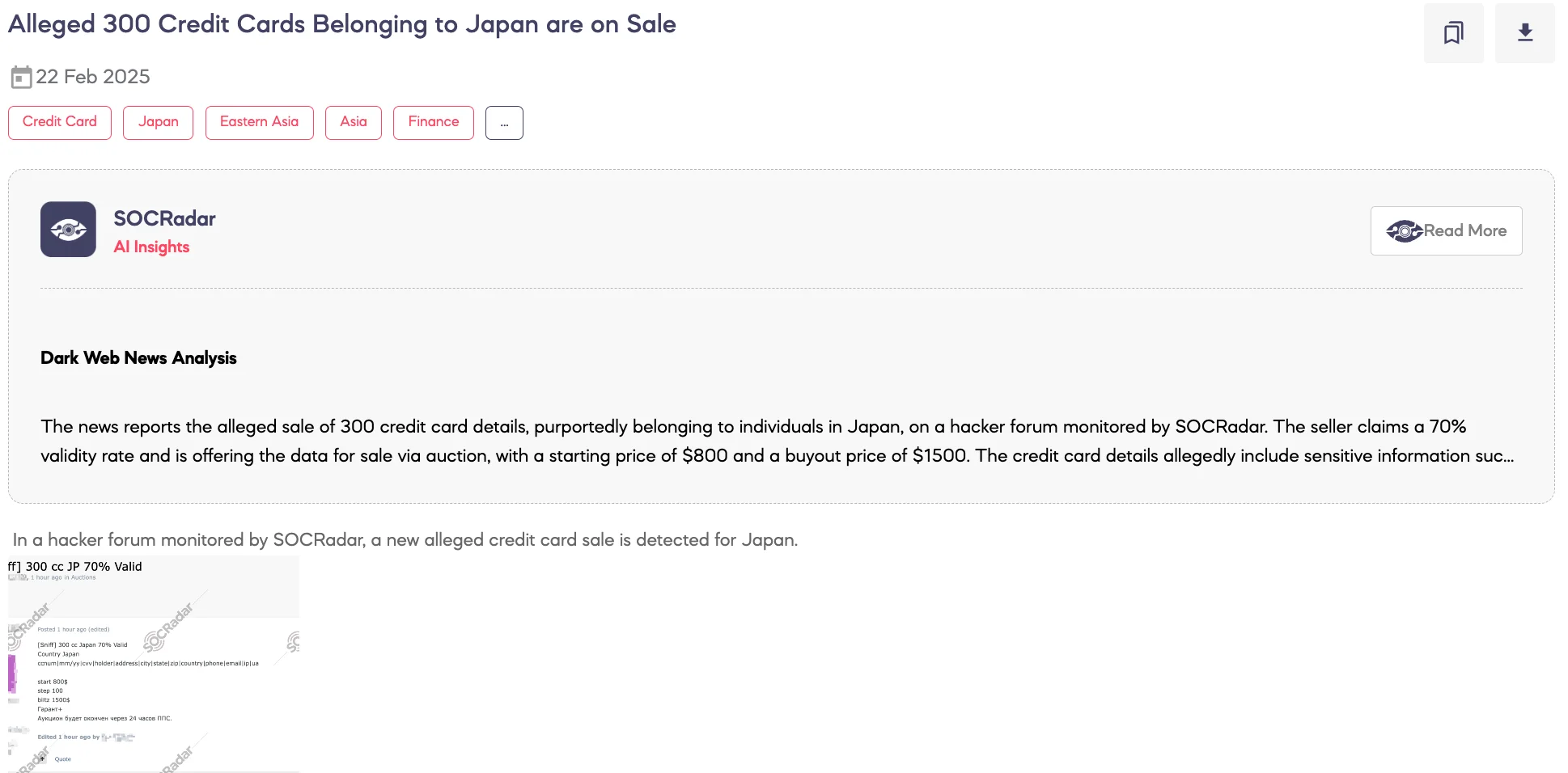
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claimed to be selling 300 allegedly compromised credit card records from Japan. According to the post, the dataset has a 70% validity rate and includes card numbers, expiration dates, CVVs, holder names, addresses, phone numbers, email addresses, and IP details. The auction for the dataset starts at $800, with bid increments of $100, and a blitz (instant purchase) price of $1,500. The auction is set to conclude within 24 hours.
New Seraph Stealer Tool Sale is Detected
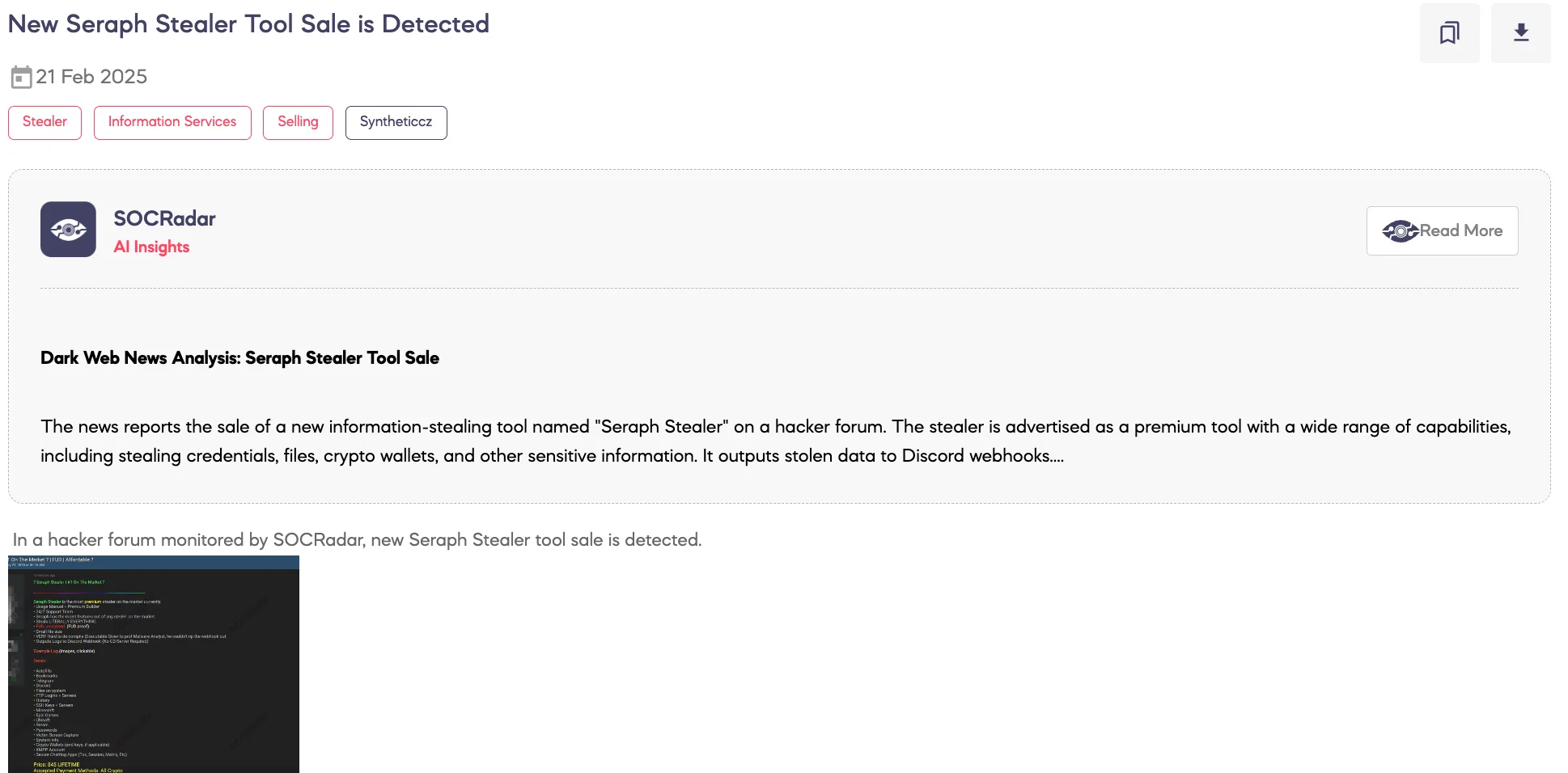
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling an info-stealer malware named Seraph Stealer. According to the threat actor’s statements, the tool is designed to extract a wide range of sensitive data from compromised systems while operating in a manner that allegedly avoids detection.
The threat actor claims that Seraph Stealer is capable of exfiltrating:
- Login credentials, including passwords, autofill data, and bookmarks
- System files and application data, including information from Telegram, Discord, FTP, SSH keys, and secure messaging applications
- Gaming platform credentials, such as those for Minecraft, Epic Games, Ubisoft, and Steam
- Cryptocurrency wallets and associated private keys
- System information and victim screen captures
The tool allegedly does not require a command-and-control (C2) server and instead utilizes Discord webhooks to transmit stolen data. The threat actor offers the tool for sale at $45 for lifetime access, with payment exclusively in cryptocurrency, and provides contact details via Telegram and Session.
Black Basta’s Internal Chat Logs Leaked, Exposing Group Conflicts and Defections
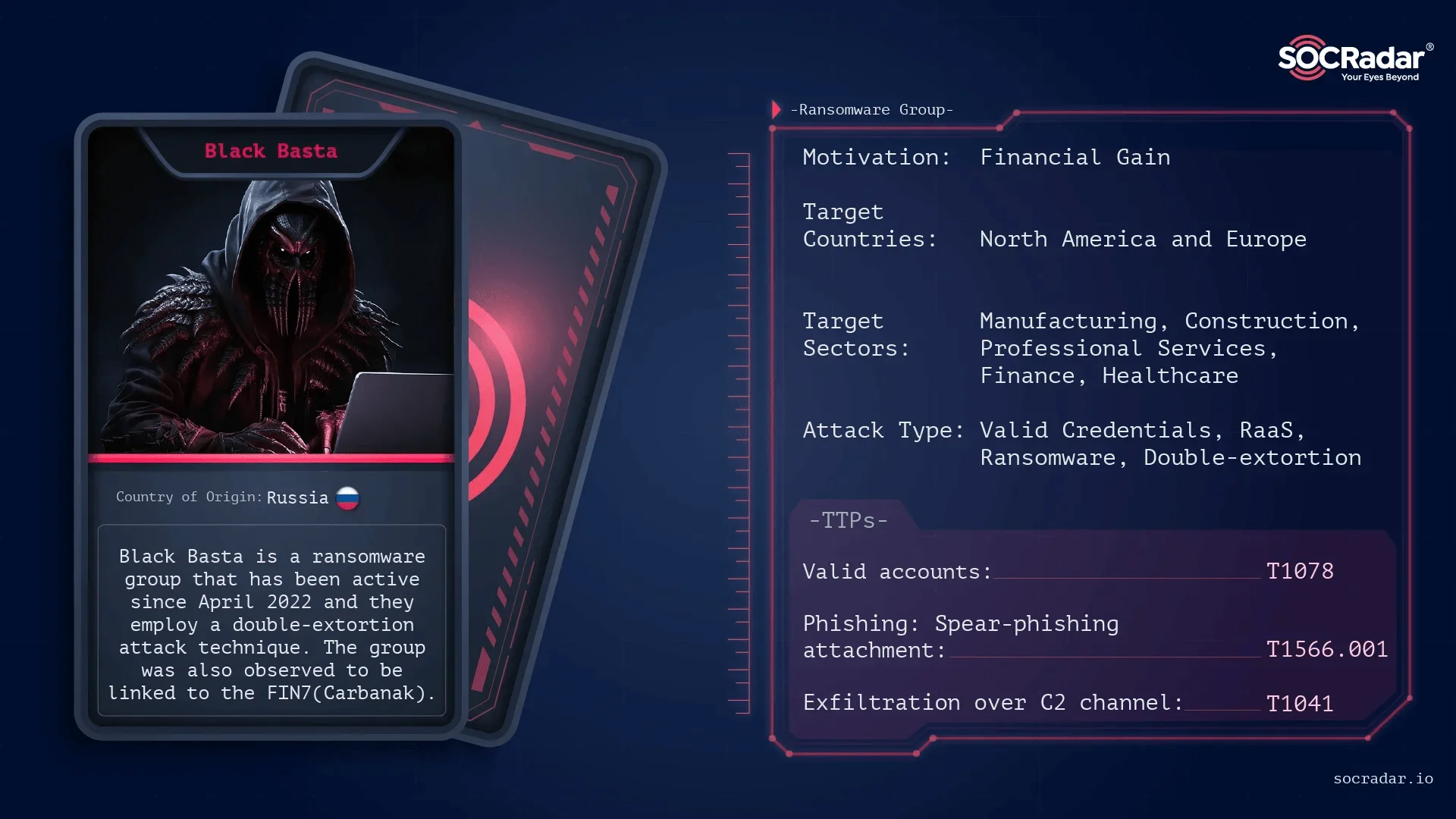
Dark Web Profile: Black Basta
Cybersecurity researchers have detected a leak of Black Basta’s internal chat logs, allegedly exposing internal conflicts and leadership struggles. The leak reportedly linked to attacks on Russian banks, reveals low morale, ransom payment scams by operators, and key members defecting to rival groups. The chat logs, covering over a year, highlight disputes among administrators and concerns over law enforcement retaliation.
SOCRadar’s analysis of the leaked chats has identified Indicators of Compromise (IoCs), including IP addresses, domains, and hashes, which can help organizations detect and mitigate potential threats.
For further details and the latest updates, read the full blog: Black Basta’s Internal Chats Leak: Everything You Need to Know
Alleged Data of Investing.com are on Sale
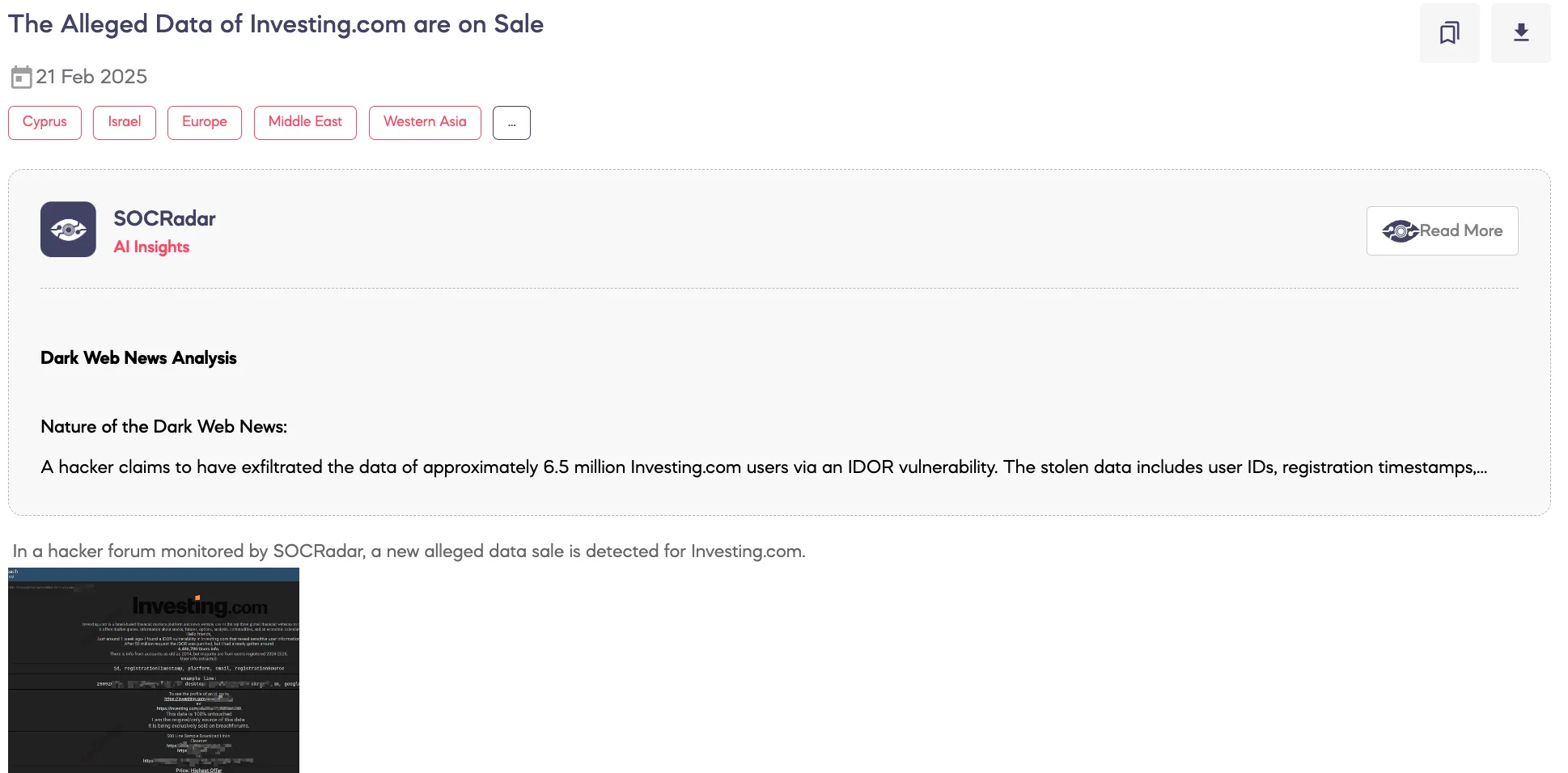
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling a dataset allegedly obtained from Investing.com, a financial markets platform based in Israel. According to the threat actor’s statements, they identified an Insecure Direct Object Reference (IDOR) vulnerability, which allowed access to user information before the issue was patched.
The threat actor alleges that the dataset contains information from 6,486,700 users, with records dating back to 2014, though the majority are from 2024-2025. The dataset allegedly includes:
- User ID
- Registration timestamp
- Platform used
- Email address
- Registration source
The actor claims to be the sole holder of the data, offering it for sale exclusively on the hacker forum, with the price set by the highest bidder. A 500-line sample has been made available via Clearnet and TOR links, and the actor has provided multiple contact methods, including Telegram, Tox, and Session.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































