
Critical Kibana Vulnerability (CVE-2025-25012) Exposes Systems to Code Execution, Patch Now
A critical security vulnerability has been discovered in Kibana, the widely used data visualization platform for Elasticsearch. Tracked as CVE-2025-25012, the vulnerability stems from prototype pollution, which could allow attackers to execute arbitrary code on affected systems, posing a significant risk to organizations relying on Kibana for data analysis and monitoring.
Given the platform’s extensive use in various industries, this vulnerability raises serious concerns about data security, integrity, and overall system stability.
How the Kibana Vulnerability Works
The CVE-2025-25012 (CVSS 9.9) flaw arises due to prototype pollution, a type of vulnerability that manipulates an object’s properties, leading to unintended behaviors in an application. In this case, attackers can exploit Kibana by uploading a specially crafted file and sending malicious HTTP requests, ultimately achieving code execution. This means an adversary could gain unauthorized access, execute commands, manipulate data, or even take full control of a compromised system.
Such vulnerabilities are particularly dangerous because they require minimal prerequisites to exploit. If an attacker has the necessary permissions within Kibana, they can leverage this flaw to inject malicious code and bypass traditional security controls.
Which Kibana Versions Are Affected by CVE-2025-25012?
Various versions of Kibana exhibit different levels of susceptibility to this security flaw:
- Versions 8.15.0 and later, up to 8.17.3: In these releases, the vulnerability can be exploited by users with the Viewer role, making a broader range of accounts potential entry points for attackers.
- Versions 8.17.1 and 8.17.2: For these versions, the risk is limited to users possessing elevated privileges, such as fleet-all, integrations-all, and actions:execute-advanced-connectors.
Organizations running any of these vulnerable versions must take immediate action, as even lower-level access roles could be used as an entry point for attackers. It is crucial to assess internal access permissions and restrict unnecessary privileges to minimize potential risk.
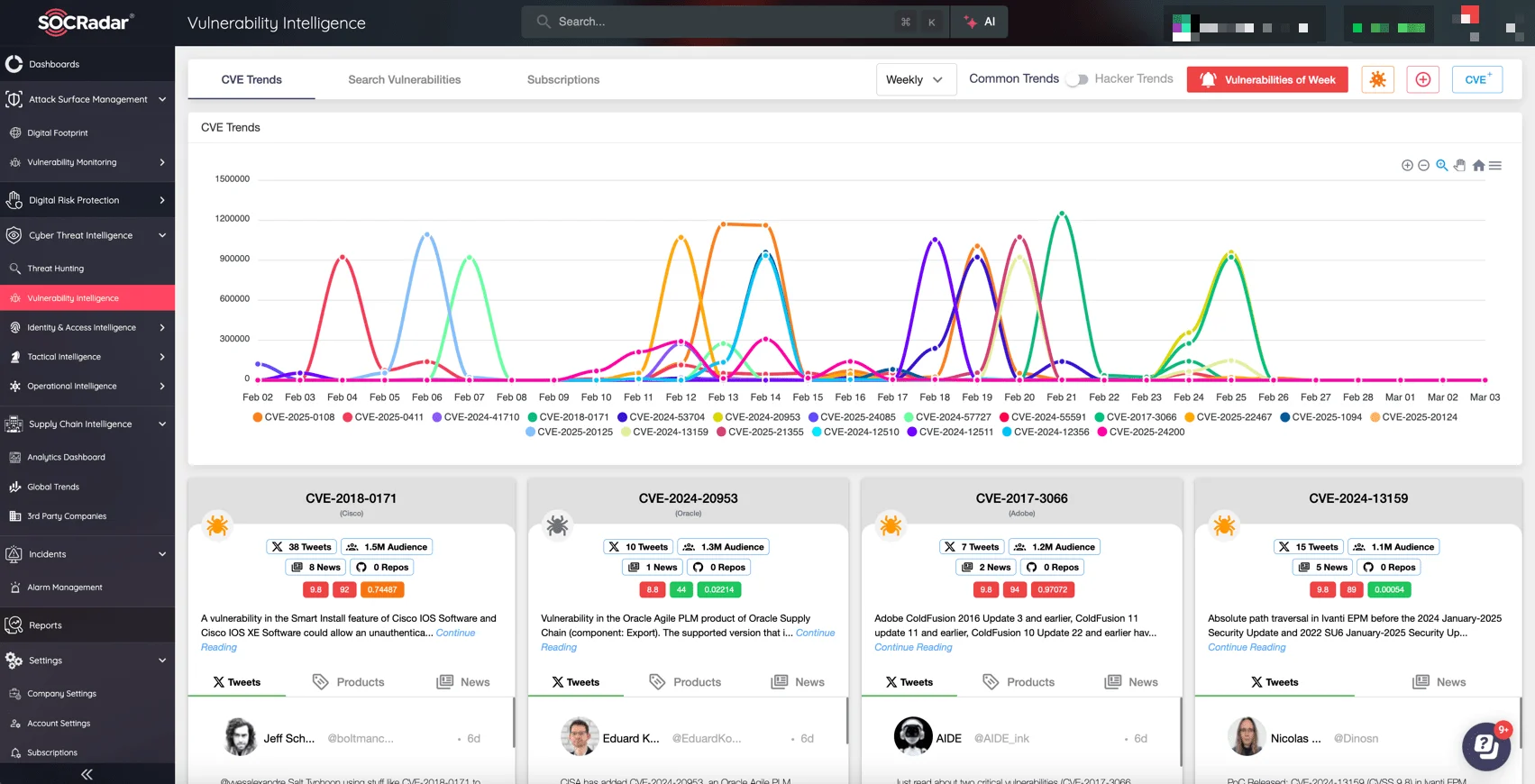
Easily track the newest CVEs and hacker trends with SOCRadar’s Vulnerability Intelligence
Kibana is an essential tool for many organizations, making this high-risk vulnerability a prime target for attackers. Organizations that rely on Kibana for real-time monitoring, security analytics, or business intelligence are particularly vulnerable. Exploiting prototype pollution to gain arbitrary code execution could lead to data breaches, system compromise, and operational disruptions.
Security teams must act swiftly to patch vulnerable systems or apply mitigations while reinforcing their defensive security strategies.
Your security team can keep up to date on new threats by using SOCRadar’s Vulnerability Intelligence to track vulnerabilities as they are discovered. As part of our platform’s Cyber Threat Intelligence module, Vulnerability Intelligence provides actionable insights that can help you prioritize remediation efforts, determine the severity of vulnerabilities, and identify exploit trends.
SOCRadar’s ability to integrate real-time intelligence into your security operations reduces the risk of exploitation, allowing your team to respond to vulnerabilities more quickly.
How Can You Secure Your Kibana Deployment?
To address CVE-2025-25012, Elastic has released Kibana version 8.17.3, which contains a patch to eliminate the risk. Upgrading to this version is strongly recommended to prevent potential exploitation.
If upgrading is not immediately feasible, apply the recommended mitigation strategy, as shown below, to minimize risk.
Disable the Integration Assistant by adding the following configuration setting:
xpack.integration_assistant.enabled: false
For best protection, you should also adhere to security best practices, such as:
- Reviewing and restricting user permissions, ensuring only necessary access is granted.
- Monitoring system logs closely for unusual activity, particularly unusual API calls or unexpected file uploads.
- Implementing network segmentation to limit the impact of a potential compromise.
For details, refer to Elastic’s announcement. Stay proactive in securing your infrastructure to mitigate emerging threats.
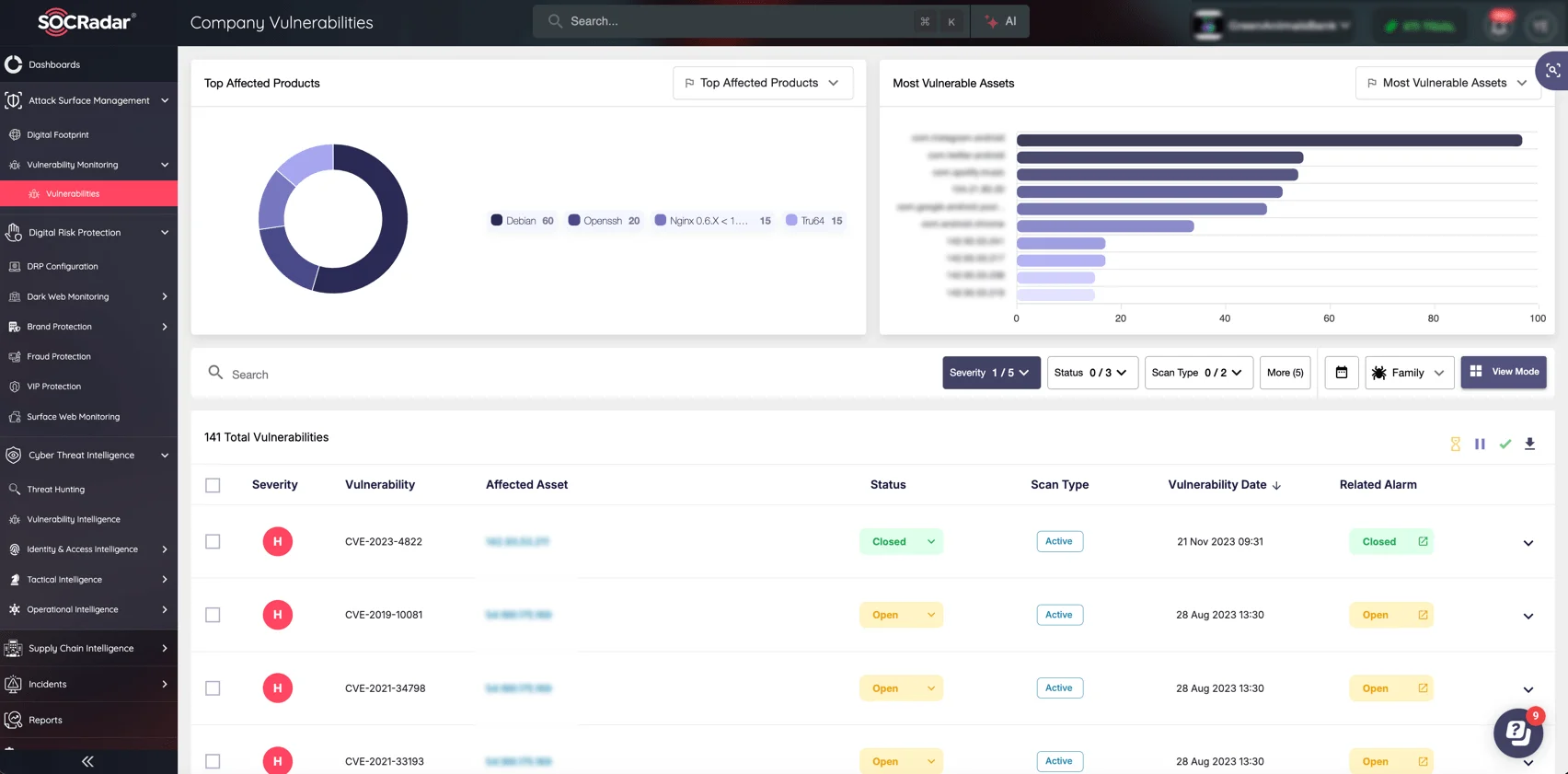
SOCRadar’s Attack Surface Management module, Company Vulnerabilities page
To protect your organization from vulnerabilities like CVE-2025-25012, SOCRadar’s Attack Surface Management (ASM) module offers continuous monitoring and proactive risk assessment. Our ASM solution helps you:
- Monitor External Assets: Track and identify vulnerabilities.
- Gain Full Visibility: Understand third-party risks, shadow IT, and exposed services.
- Prioritize Remediation: Assess vulnerabilities based on real-world impact.
- Receive Timely Alerts: Get proactive notifications to act before threats escalate.
By integrating SOCRadar’s ASM, you’ll strengthen your defense strategy and stay ahead of cyber risks.




































