Everything You Need to Know About Oracle Cloud Security Incident by rose87168
rose87168 is the alias of a hacker who claims to have breached Oracle Cloud, allegedly stealing around 6 million sensitive records, including encrypted passwords, key files, and authentication data. The hacker has been active since at least January 2025, selling the data on forums like BreachForums and attempting extortion against affected organizations. Despite Oracle’s denial of the breach, evidence from “rose87168” suggests a significant compromise. The breach is believed to have impacted over 140,000 Oracle Cloud tenants globally.
Threat actor’s BreachForums’ profile
1. Who is “rose87168”?
“rose87168” is the alias of a threat actor who claims to have breached Oracle Cloud, stealing approximately 6 million records. The hacker has been active since at least January 2025 and is selling the data on dark web forums like BreachForums, while also engaging in extortion attempts against affected organizations.
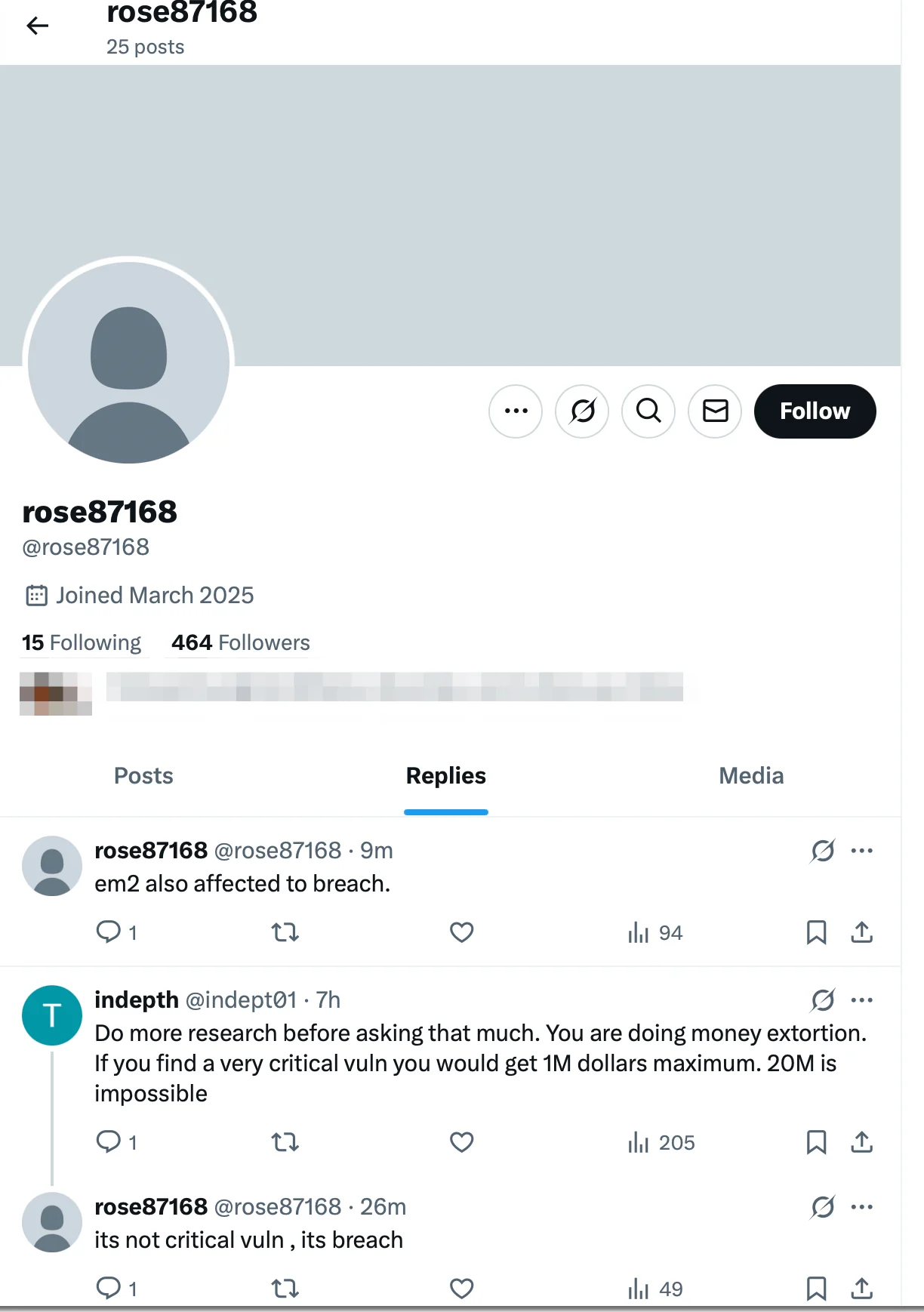
X (previously Twitter) account of the threat actor
2. What Data did “rose87168” Allegedly Steal from Oracle Cloud?
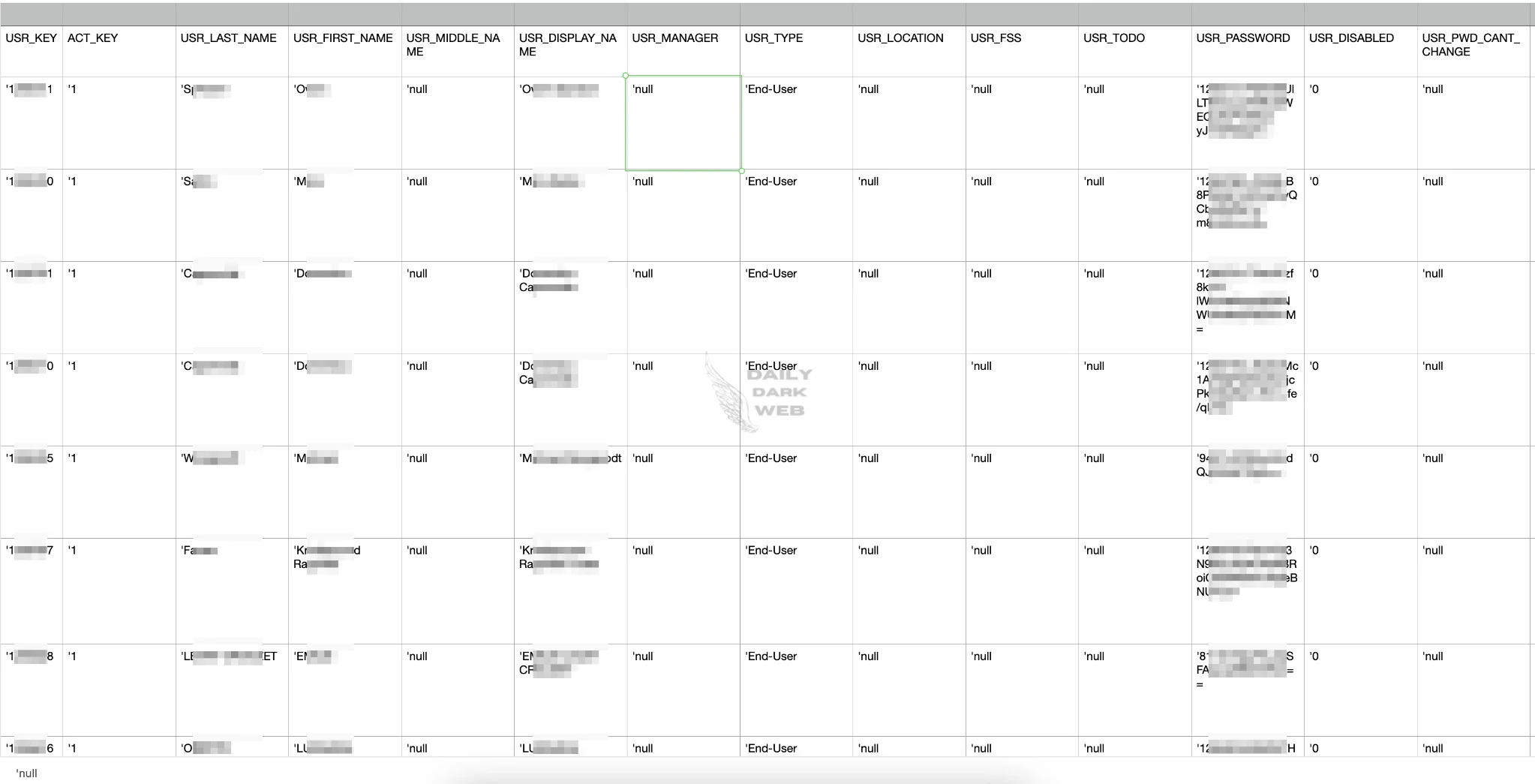
The hacker claims to have exfiltrated 6 million records, including
- Java KeyStore (JKS) files,
- Encrypted Single Sign-On (SSO) passwords,
- Encrypted Lightweight Directory Access Protocol (LDAP) passwords, key files, and
- Enterprise Manager JPS keys.
This alleged leak data is critical for authentication and security within Oracle Cloud systems.
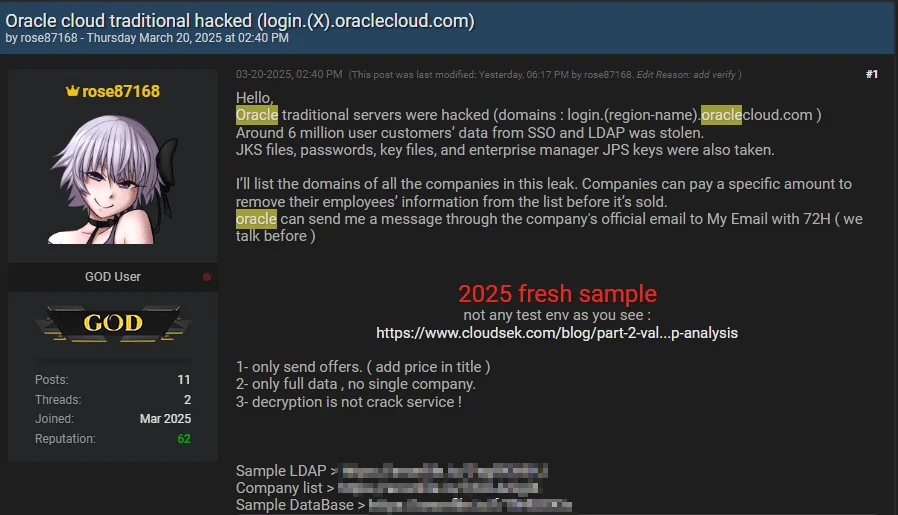
Threat actor’s post in BreachForums
3. When did the Alleged Oracle Hack Occur?
According to “rose87168,” the breach took place approximately 40 days before March 21, 2025, when the stolen data was first advertised for sale. This places the infiltration around mid-February 2025.
Initial post of threat actor (X)
3.1 What is the Timeline of the Incident?
- Feb 9–15, 2025 – Initial Breach
Rose87168 allegedly breaches login.us2.oraclecloud.com, exploiting a vulnerability (possibly CVE-2021-35587) in Oracle Fusion Middleware 11G. Claims to steal 6M records (JKS files, encrypted SSO/LDAP passwords, etc.) affecting 140,000+ tenants. No public evidence yet. - Late Feb 2025 – Contact with Oracle
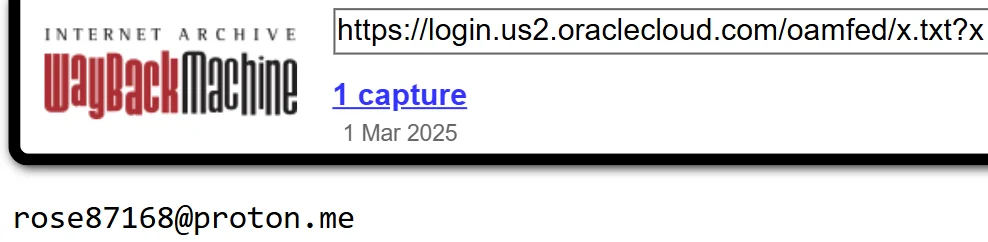
Rose87168 contacts Oracle, demands $200M+ (100,000 XMR) for vulnerability details. Oracle refuses, seeks full disclosure first. Negotiations fail. Text file with hacker’s ProtonMail uploaded to server (exact date unclear). - Mar 3, 2025 – Wayback Machine Capture
Internet Archive’s Wayback Machine captures a snapshot of login.us2.oraclecloud.com, showing Rose87168’s uploaded text file with a ProtonMail address, proving some level of access. - Mar 21, 2025 – Public Disclosure on BreachForums
Rose87168 announces the breach on BreachForums, offers 6M records for sale (price undisclosed or zero-day exploits), seeks decryption help, and offers data removal for a fee to affected companies. - Mar 22, 2025 – Oracle’s Denial
Oracle issues a statement: “No breach of Oracle Cloud. Published credentials not for Oracle Cloud. No customer data lost.” Server login.us2.oraclecloud.com taken offline (reason unstated). - Mar 23–24, 2025 – Speculation and Investigation
Cybersecurity outlets (e.g., The Register, BleepingComputer) report on the incident. CloudSEK speculates CVE-2021-35587 or a zero-day exploit. Reports emerge of Oracle requesting password resets from some customers. - Mar 25, 2025 – Data Sample Released & Analysis
The threat actor “Rose87168” escalates the situation by releasing a 10,000-line sample of the allegedly stolen data. This sample is intended to substantiate their claim of exfiltrating 6 million records from Oracle Cloud’s federated Single Sign-On (SSO) and Lightweight Directory Access Protocol (LDAP) systems. Situation remains unresolved.
4. How did “rose87168” Allegedly Breach Oracle Cloud?
The hacker claims to have exploited a vulnerability in Oracle Cloud’s login infrastructure, specifically targeting the endpoint login.(region-name).oraclecloud.com. Cybersecurity researchers, including CloudSEK, speculate that the breach may involve CVE-2021-35587, a known flaw in Oracle Access Manager within Oracle Fusion Middleware, though “rose87168” hints at a possibly undisclosed vulnerability.
4.1 What’s About CVE-2021-35587?
The suspected vulnerability is CVE-2021-35587, a flaw in Oracle Access Manager (OAM) within Oracle Fusion Middleware. It’s a Remote Code Execution (RCE) vulnerability with a CVSS score of 9.8, allowing unauthenticated attackers to execute arbitrary code on affected systems. Patched in October 2021, it targets un-updated systems. “Rose87168” hinted at exploiting this or a similar undisclosed flaw in Oracle Cloud’s login infrastructure (login.(region-name).oraclecloud.com), though no definitive proof ties it to the breach.
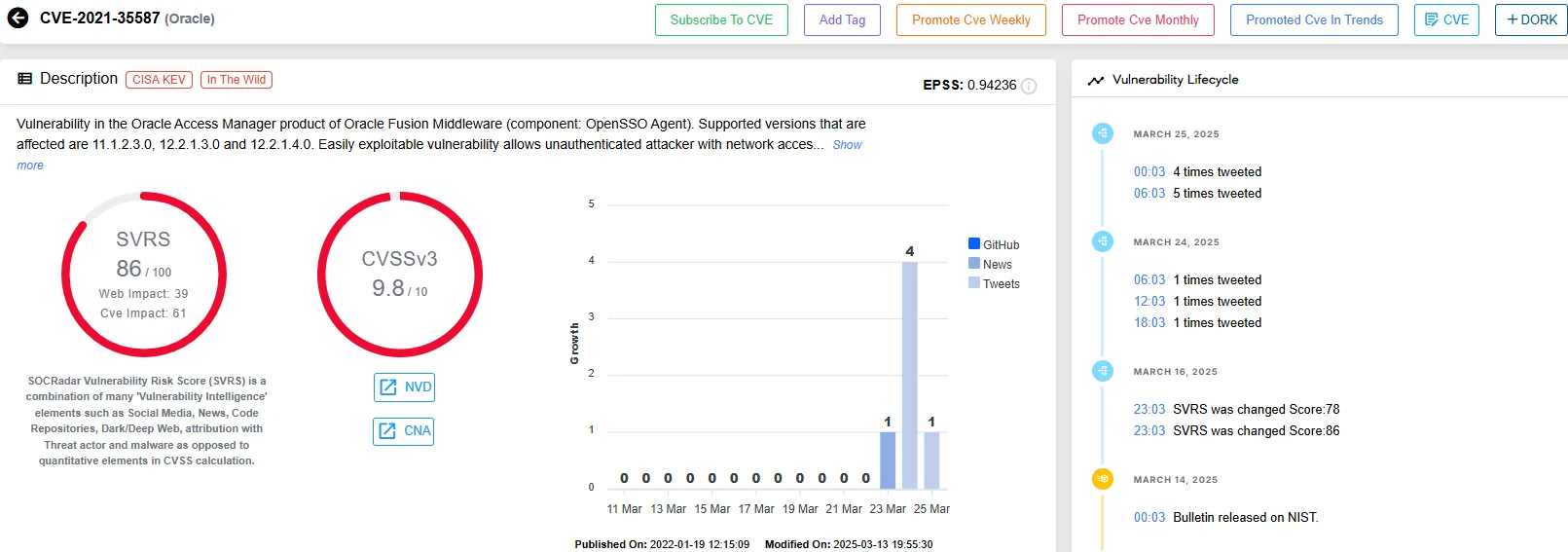
SOCRadar’s Vulnerability Intelligence, CVE-2021-35587
5. Did Oracle Confirm the Hack by “rose87168”?
No, Oracle has denied the breach, stating, “There has been no breach of Oracle Cloud. The published credentials are not for the Oracle Cloud. No Oracle Cloud customers experienced a breach or lost any data.” This stance contrasts with evidence presented by “rose87168” and findings from cybersecurity firms like CloudSEK.
6. What Evidence has “rose87168” Provided to Support the Hack Claim?
As seen above, “Rose87168” has shared sample data, including text files with database records and LDAP information, and uploaded a file containing their email address to login.us2.oraclecloud.com, archived on the Internet Archive. This action suggests some level of access, though its legitimacy remains unverified by independent sources.
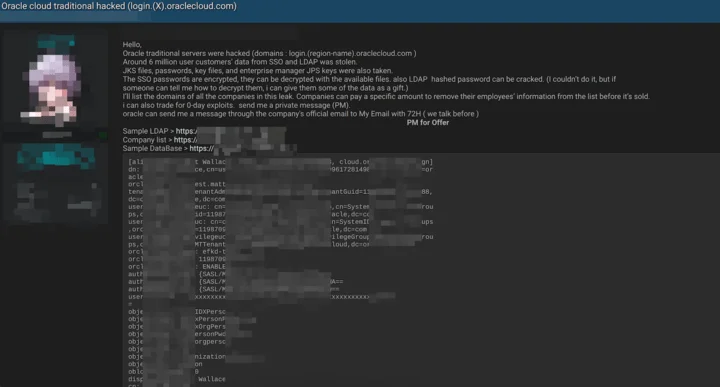
Initial post in BreachForums
“The threat actor has provided three sample files as proof: Sample_LDAP.txt, Company.List.txt, and Sample_Database.txt. Some sample data is as follows:”
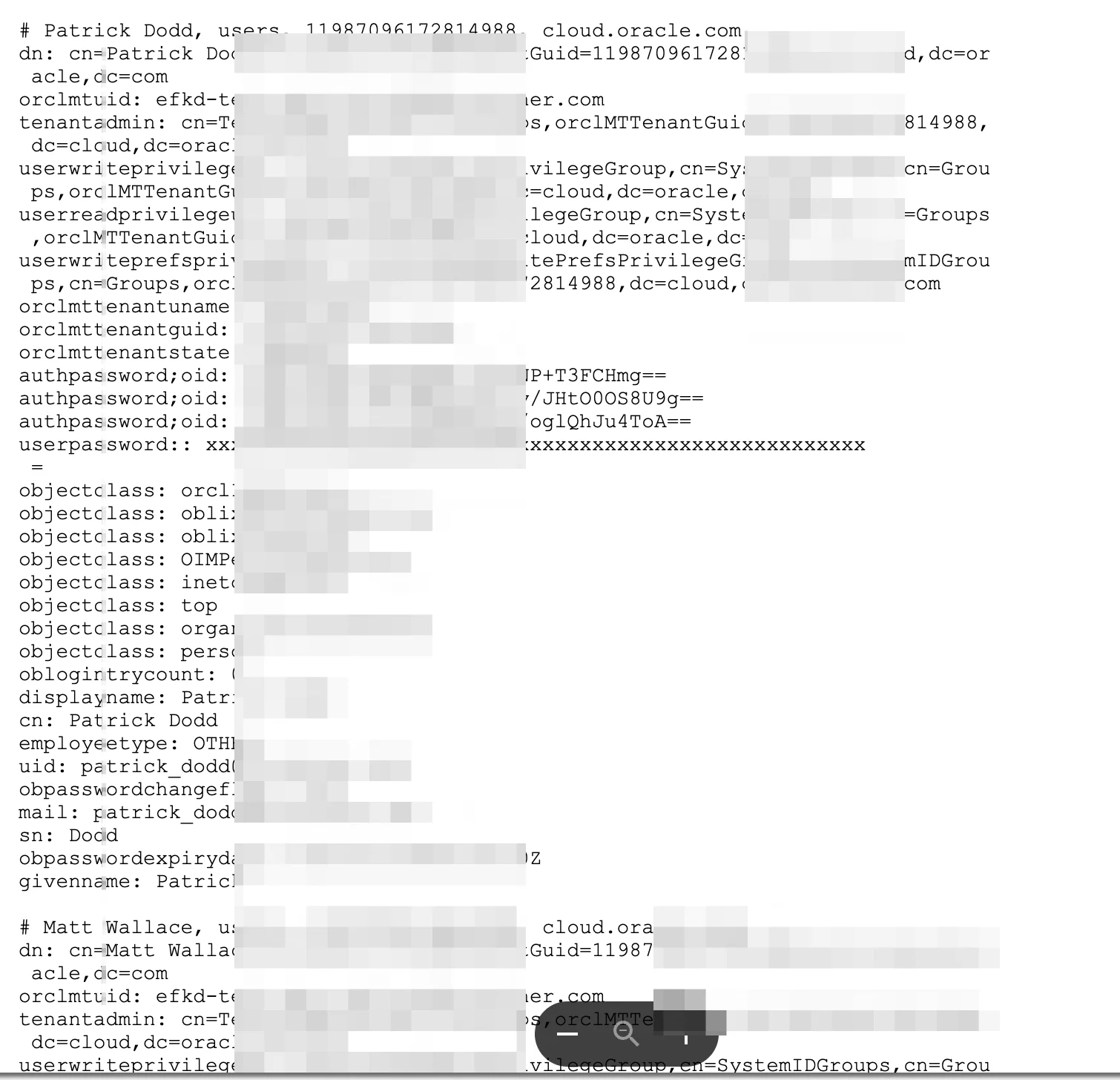
Sample data #1
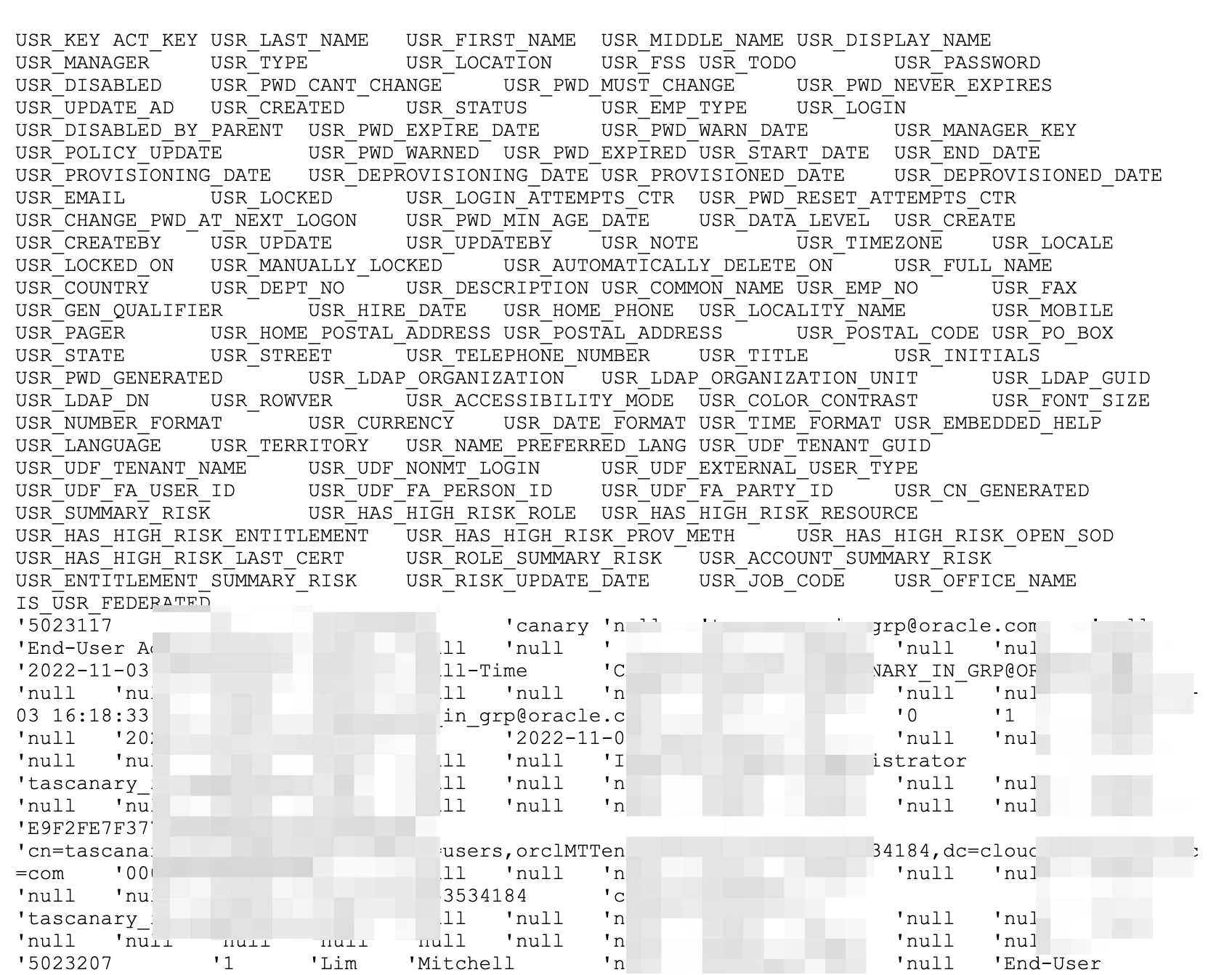
Sample data #2
Furthermore, The image below corroborates the claim that ‘Rose87168’ uploaded sample data, including an email address and a linked text file, to an Oracle Cloud URL. The presence of this record in the Internet Archive further indicates that, at least some part of the data was accessible by the threat actor at some point.
Screenshot of the the text file uploaded by the threat actor on the Oracle Cloud on WayBackMachine
6.1 Has the Breach Been Confirmed?
To this day threat actor continued to supply numerous sample screenshots, including the following novel sample data:
A sample data shared by rose87168 (DDW)
Furthermore, recent news indicate that some Oracle Cloud customers are taking independent steps to verify the breach claims made by “rose87168.” Several organizations have begun closely reviewing their security logs and access records, with some reporting anomalies such as unexpected authentication attempts and irregularities in key file activity. These early customer verifications are Indicators of Attack(IOAs), and suggest that there may be unusual activity warranting further scrutiny, even as Oracle continues to deny any breach of its systems.
7. How Many Organizations were Affected by the Alleged Hack?
The breach reportedly impacts over 140,000 Oracle Cloud tenants worldwide, spanning multiple regions and industries. These tenants are businesses or entities using Oracle Cloud services, making this a potential supply chain attack with broad implications.
7.1 How can I Check Whether Our Organization is in The List?
SOCRadar’s Threat Hunting module allows organizations to search vast digital sources, including dark web forums, to determine if their data appears in the alleged Oracle Cloud breach. Security teams can quickly query the leaked dataset to identify exposed credentials, domains, or sensitive information. Additionally, SOCRadar has already alerted all its affected users.
You can also access the Threat Hunting module using SOCRadar Free Edition to check if your organization’s data has been leaked.
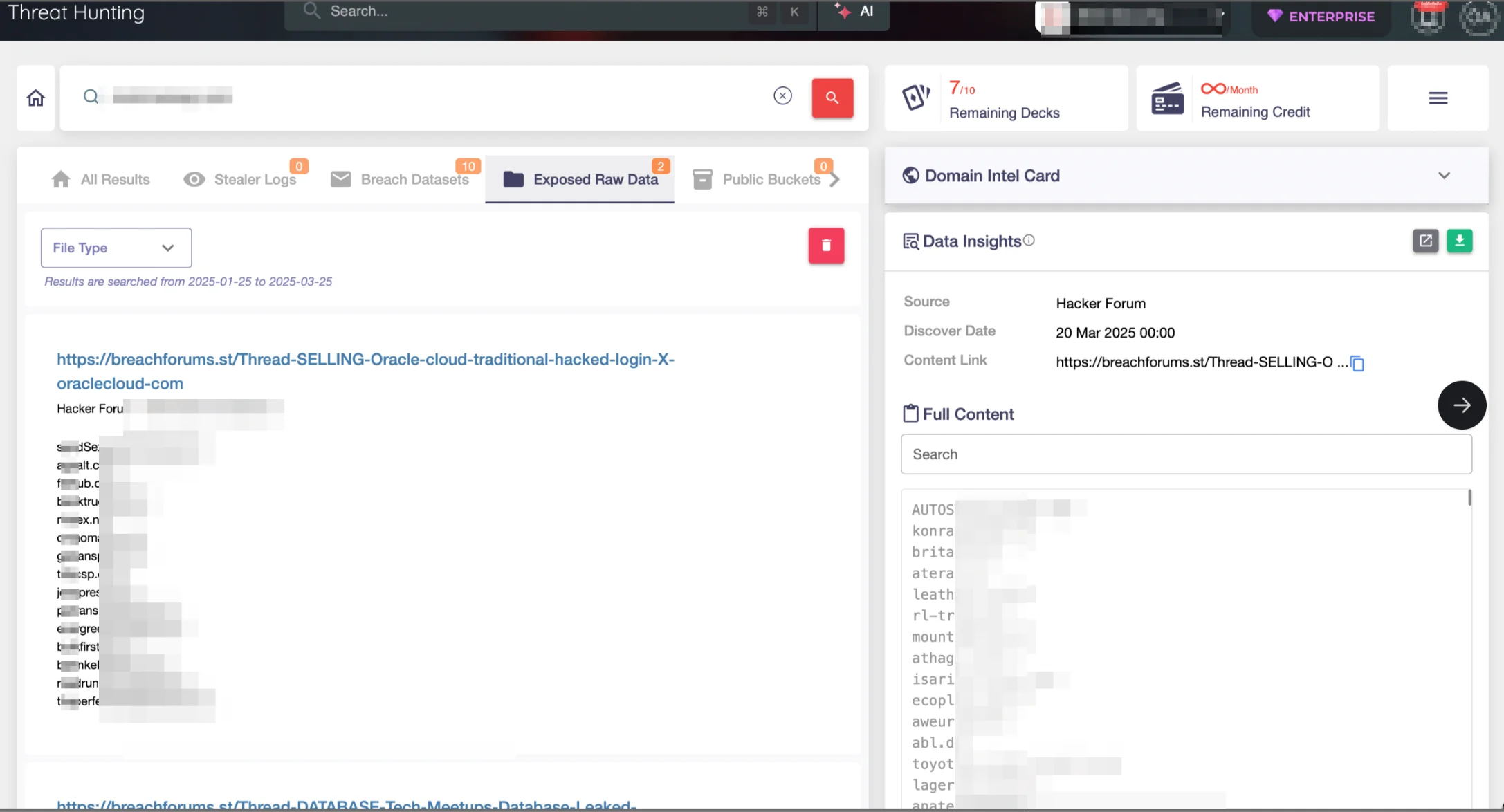
Users can query the stolen dataset using keywords like company name, domains, or email addresses to identify their potential exposure
8. What is “rose87168” doing with the Stolen Data?
The hacker is selling the 6 million records on BreachForums for an undisclosed price or in exchange for zero-day exploits. They’ve also offered affected companies the chance to pay a fee to remove their data from the leak list and are soliciting help to decrypt the stolen SSO passwords and crack LDAP hashes.

However, the threat actor corrected a claim of wanting $200 million, stating that the actual amount was $20 million (X)
9. What should organizations using Oracle Cloud do in response?
Experts recommend immediate action, including:
- Reset the Credentials: Rotate all SSO, LDAP, and related passwords, enforcing Multi-Factor Authentication (MFA).
- Investigate: Conduct forensic checks for unauthorized access.
- Monitor: Watch dark web forums for leaked data.
- Collaborate: Work with Oracle’s security team to assess exposure and apply fixes. These steps are advised regardless of Oracle’s denial, given the potential risks.
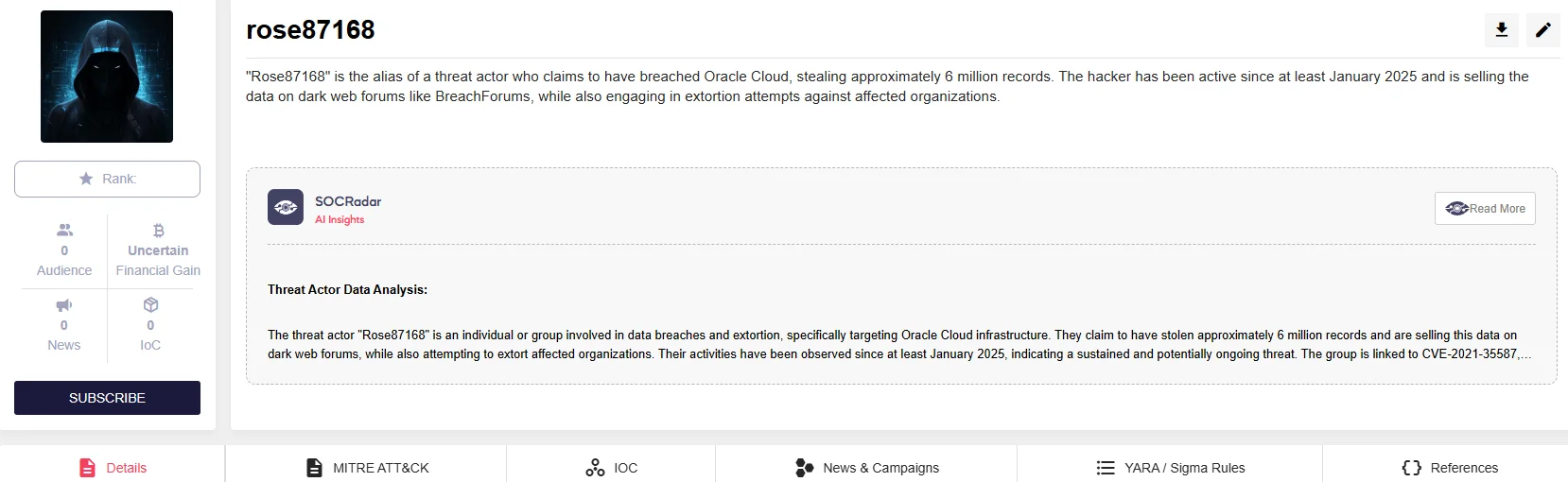
SOCRadar’s Threat Actor Intelligence
10. How can I protect my Oracle Cloud environment from similar attacks?
- Patch Systems: Ensure all Oracle Fusion Middleware instances are updated beyond October 2021 to address CVE-2021-35587.
- Enforce MFA: Require multi-factor authentication for all Oracle Cloud logins.
- Limit Access: Restrict login endpoints to trusted IP ranges via network policies.
- Rotate Keys: Regularly update JKS files, SSO passwords, and LDAP credentials.
- Monitor Logs: Set up real-time alerts for suspicious activity in Oracle Cloud Audit.