
Reflections of the India–Pakistan Kashmir Escalation on the Cyber World
The Kashmir region, long a flashpoint between India and Pakistan, has once again become the center of a volatile escalation. On May 7, 2025, both nations exchanged heavy fire and conducted cross-border strikes, leading to dozens of civilian casualties on either side. The conflict was triggered after a militant attack in Pahalgam on April 22, which India blamed on Pakistan-backed actors, a charge Islamabad has denied.
Missile strikes, drone shootdowns, and shelling across the Line of Control (LoC) have followed, each side accusing the other of provocation. As has often been the case in recent years, these physical clashes are increasingly mirrored in cyberspace.
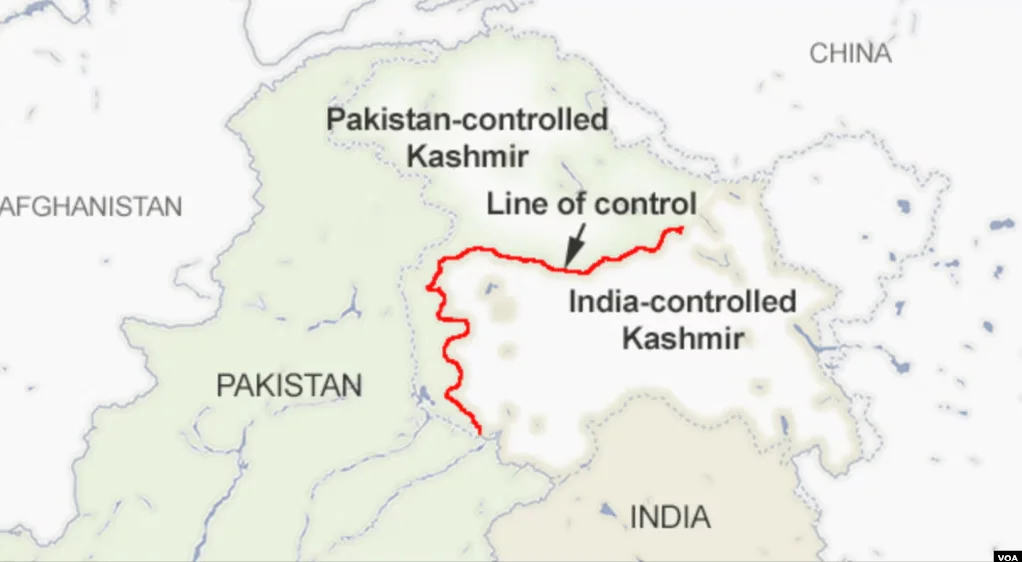
LoC on the disputed Kashmir region (VOA)
This blog tracks the cyber reflections of the latest military standoff, organizing key developments in chronological order. As with prior flare-ups, cyber threat actors ranging from hacktivists to possibly APTs, have begun to align their operations.
Cyber Retaliation Between India and Pakistan: A Snapshot
India and Pakistan’s rivalry often plays out online, especially during moments of real-world tension like the current situation in Kashmir. Over the years, cyber activity has followed a familiar pattern. When political or military events flare up, so do digital skirmishes.
Hacktivist groups from both sides have been active, launching website defacements, Denial-of-Service (DoS) attacks, and at times leaking stolen data. These actions usually come in response to attacks on civilians, national holidays, or even cricket matches. Pro-Pakistan groups often justify their actions on religious or ideological grounds, while Indian-affiliated groups respond with retaliatory campaigns of their own or carry out attacks with similar justifications.
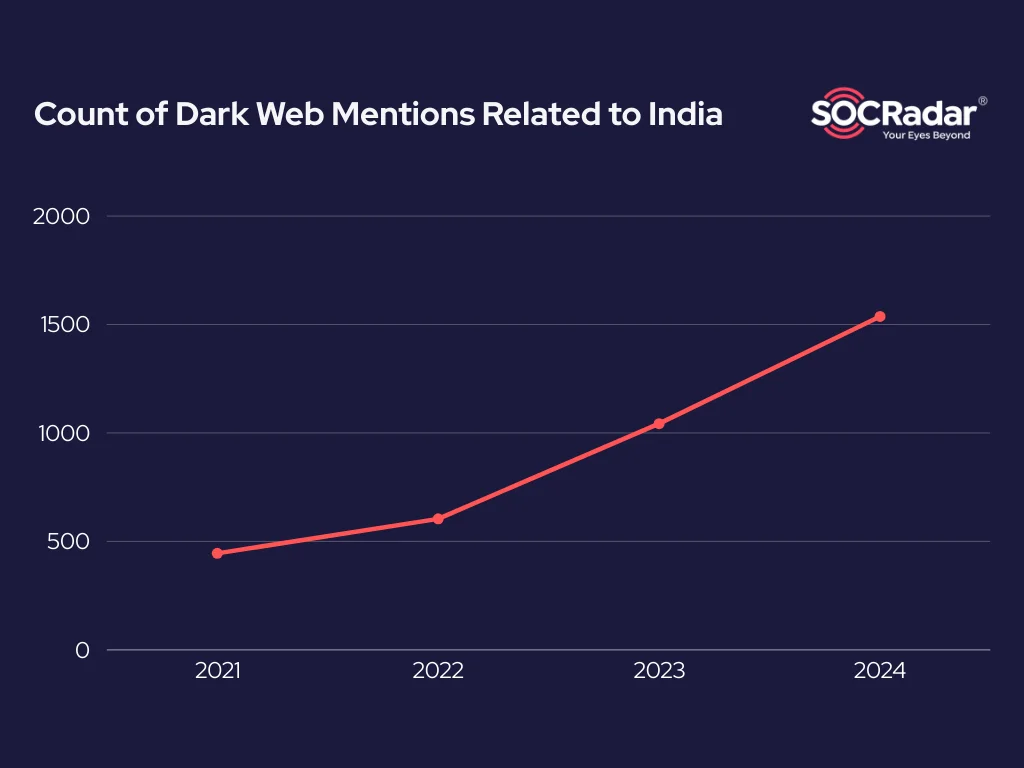
Count of Dark Web mentions related to India over the years, cyber attacks, leaks, sales and more
Over the years, cyber activity related to India has kept growing. This includes not just hacktivist campaigns but also mentions on the Dark Web like data leaks, and the sale of stolen information. Most of these are publicly visible and reflect a mix of political, criminal, and opportunistic motives. While some incidents are low impact or symbolic, they often line up with events on the ground, showing how the conflict now plays out online as well.
Pakistan has seen a similar pattern of cyber activity over the years, but it doesn’t get targeted as heavily as India on hacker forums, Telegram channels, or by hacktivist groups.
Since the 2010s, especially following the Arab Spring, the center of gravity for hacktivism has clearly shifted toward Asia. South Asian groups, in particular, have become some of the most active players in the space. The majority of hacktivist campaigns today involve collectives based in the eastern hemisphere, from Southeast Asia to the Middle East and South Asia.
This shift has played a major role in how global conflicts unfold online. Hacktivist groups are now quick to align themselves with political causes, and their actions often reflect the broader sentiment of the regions they represent. For example, during the Israel–Palestine conflict, a large number of attacks came from this part of the world, with very few pro-Israeli hacktivist groups in comparison. Many of the pro-Israel actors were Indian, reflecting India’s political stance in that crisis.
Because of this, India found itself targeted in retaliation, even though it was not directly involved in the conflict. Pakistan, on the other hand, was less of a target, partly because its hacktivist ecosystem is already highly active and aligned with many of the same causes driving anti-Israel and anti-India sentiment.
For more details on this connection, check out our dedicated blog post.
Before May 7, 2025
Following the April 22 attack in Pahalgam, several cyber incidents took place. On April 29, Pakistan-based hackers “IOK Hacker” claimed attacks on Indian Army school portals and welfare websites. Soon after, on May 5, “Pakistan Cyber Force” announced alleged breaches of Indian military-linked sites and attempted to deface a defense-related company’s website.
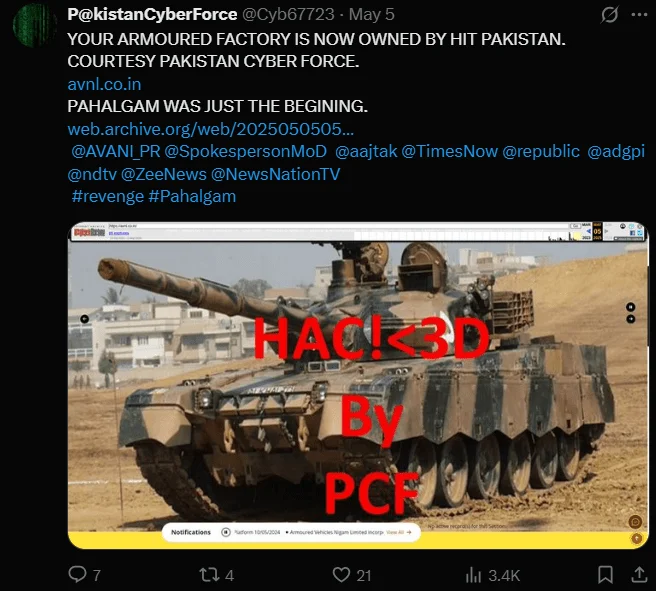
Alleged threat actor in question (X)
Although these attacks were highly publicized, their real impact was probably limited, and many claims likely exaggerated. News outlets often amplify the importance of these incidents, which individually might not cause serious damage. However, hacktivism typically works this way, lots of small, possibly unfounded or minimally damaging incidents but collectively result in significant disruption over time.
On May 7 and 8, 2025
On the day of attack, cyber confrontations significantly escalated, mirroring physical clashes along the Kashmir Line of Control. Hacktivist groups swiftly reacted to the fire exchanges with public announcements and targeted cyberattacks. Some of the highlights are as follows:
IndoHaxSec, an Indonesian hacker collective, announced collaboration with Pakistani group Team Azrael – Angel of Death, explicitly stating their intent to target Indian cyberspace. They framed their cyber-attacks as direct retaliation against India’s missile strikes on Pakistan-administered territories, encouraging other Indonesian groups to join their campaign against India.
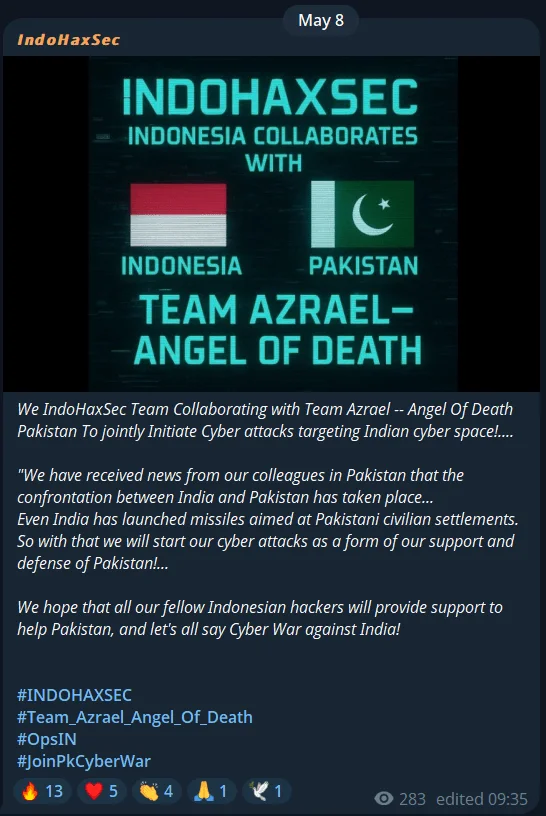
IndoHaxSec’s Telegram post
In another instance, the SYLHET GANG-SG allegedly defaced an Indian website, showcasing a political message supporting Pakistan. The act, seemingly symbolic but with limited impact.
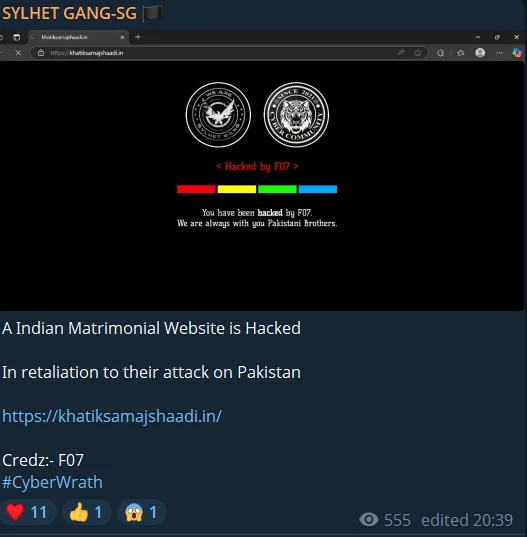
SYLHET GANG-SG’s Telegram post
Meanwhile, one of the bigger groups, Team insane Pakistan claimed responsibility for hacking the Information and Public Relations Department of Rajasthan’s website, leaving a defacement message that accused Indian authorities of spreading misinformation.
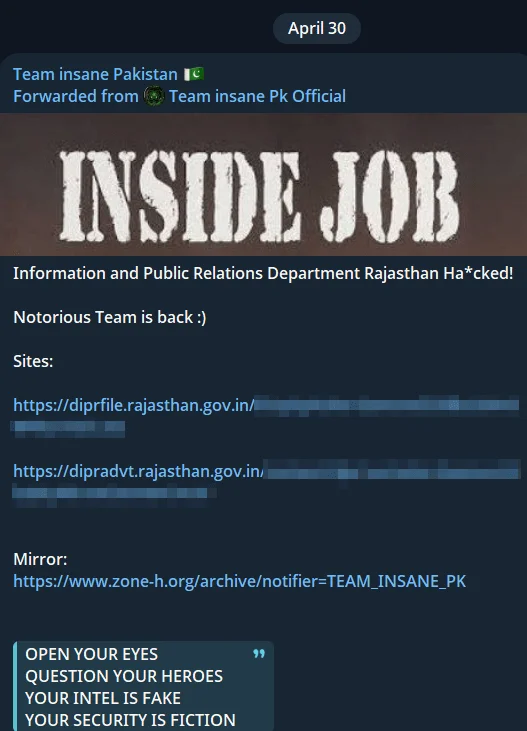
Team Insane Pakistan’s Telegram post
Most notably, a threat actor calling themselves DieNet announced an alleged breach of India’s National Informatics Centre (NIC), claiming extraction of over 247 GB of data. They threatened to gradually release sensitive information depending on India’s future actions.

DieNet’s Telegram post
In Conclusion
Many of these incidents might be symbolic, overstated, or have limited real-world impact. However, the overall psychological influence and the potential to escalate further shouldn’t be overlooked. Even seemingly minor or exaggerated claims can add up, reinforcing the sense of tension in the region.
SOCRadar, Advanced Dark Web Monitoring
To stay ahead in this evolving landscape, SOCRadar’s Advanced Dark Web Monitoring continuously tracks threats across hacker forums, Telegram channels, and many similar sources, providing timely insights into emerging risks and cyber activities.


































