
QatarRat Tool Emerges, GST Data Sold, and LockBit Gets Breached
SOCRadar’s Dark Web Team has identified a range of notable activities across underground forums this week. Key findings include the sale of a new multi-functional RAT named QatarRat, and a massive dataset allegedly stolen from India’s GST portal. Meanwhile, LockBit’s own infrastructure was compromised, leaking internal data and nearly 60,000 Bitcoin addresses. Additional posts include crypto stealer logs targeting wallet users, underscoring ongoing threats across malware, finance, and government sectors.
Receive a Free Dark Web Report for Your Organization:
New QatarRat Tool Sale is Detected
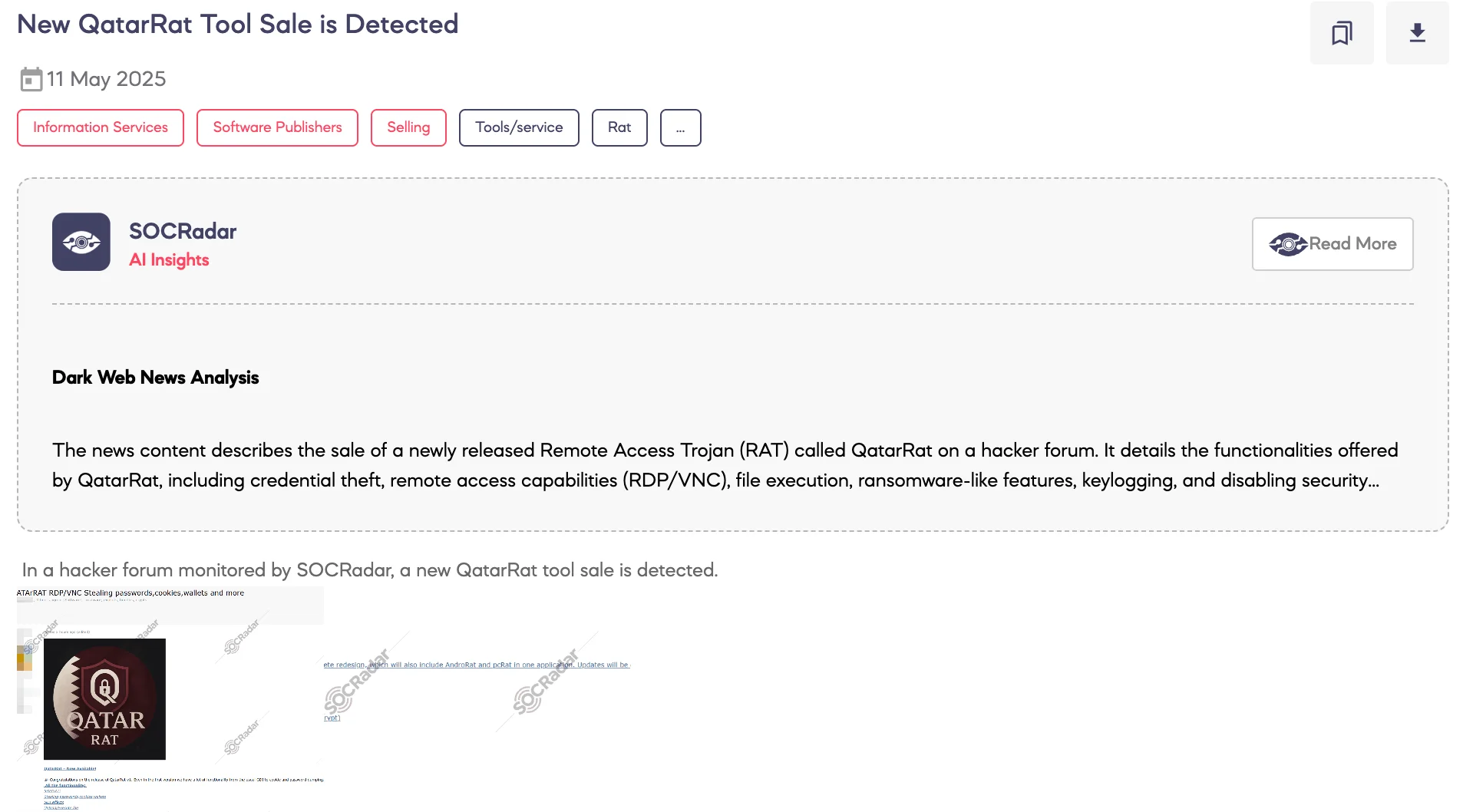
SOCRadar has detected a dark web post announcing the sale of a newly developed remote access trojan (RAT) tool named QatarRat v1. Shared by a threat actor on a cybercrime platform, the post promotes an all-in-one RAT with features such as RDP/VNC access, password and cookie theft, remote audio streaming, keylogging, GDI effects, ransomware deployment, and the ability to disable Windows Defender and UAC. The author also hints at a future QatarRat v2 version, expected to merge AndroRat and pcRat functionality into a single application. The tool is being sold under various subscription models, ranging from $75 for one month to $600 for a full year. SOCRadar continues to monitor related Telegram communities and underground forums for further developments.
Alleged Data of GST Portal are on Sale
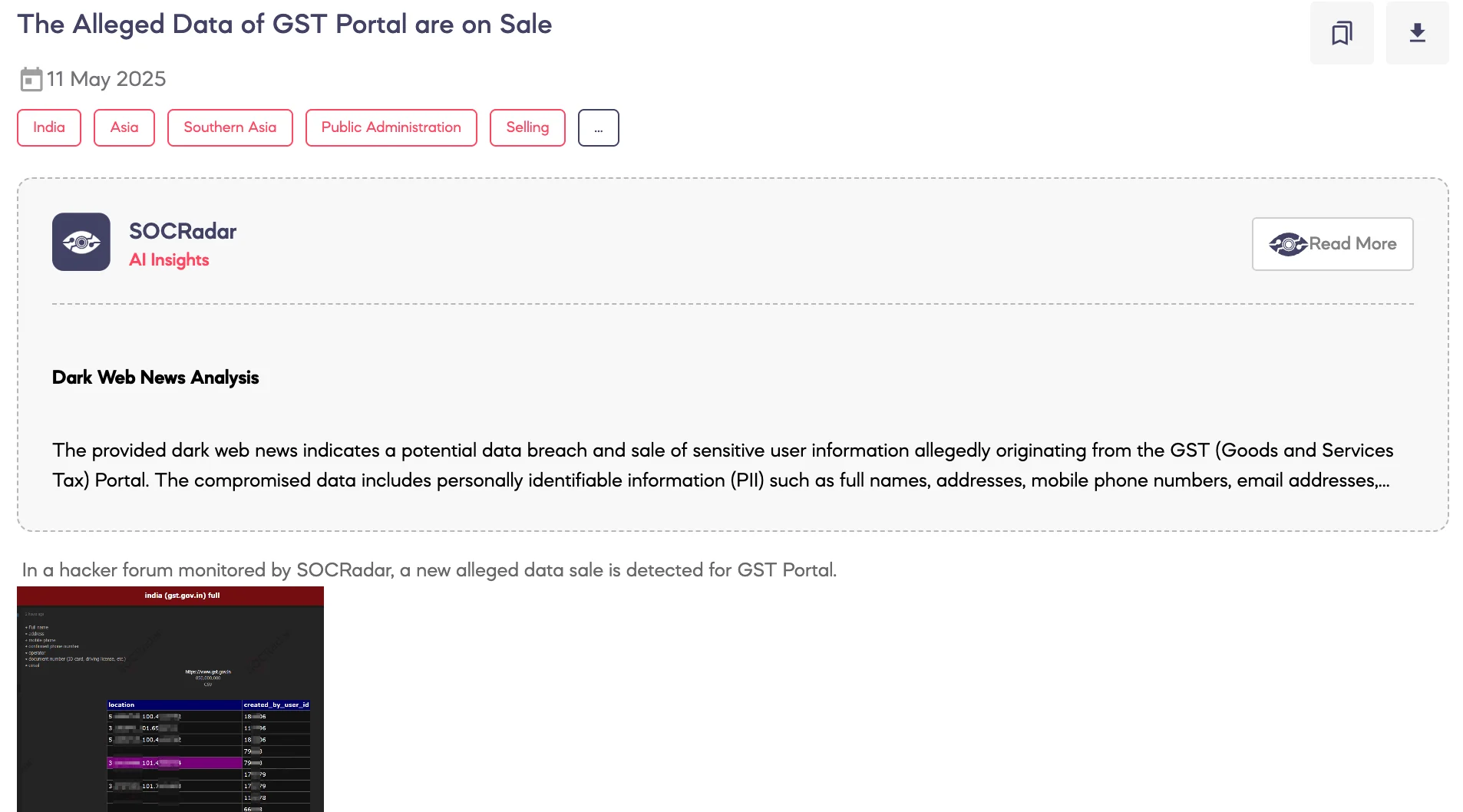
SOCRadar has detected a dark web post claiming to sell a massive dataset allegedly sourced from the official Indian government portal for Goods and Services Tax (GST), gst.gov.in. Shared on a cybercrime platform, the post advertises a CSV file containing 850 million records, allegedly including full names, addresses, mobile numbers, confirmed phone numbers, telecom operators, ID or driver’s license numbers, and email addresses. While the exact number of affected individuals remains unclear, the threat actor provides a Telegram contact for purchase. SOCRadar is monitoring the forum for further developments and signs of potential data exposure affecting Indian citizens.
LockBit Hacked: 60,000 Bitcoin Addresses Leaked
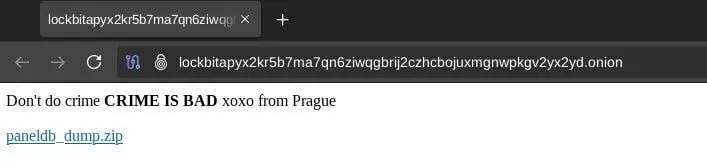
LockBit’s dark web panel was hacked, exposing a MySQL database with nearly 60,000 Bitcoin addresses, affiliate credentials, ransom negotiations, and internal tools. The breach likely exploited a PHP 8.1.2 vulnerability (CVE-2024-4577). Turns out LockBit’s biggest threat was their own attack surface, not law enforcement, and definitely not good hygiene.
For more details, please read: LockBit Hacked: 60,000 Bitcoin Addresses Leaked
Alleged Crypto Logs are on Sale
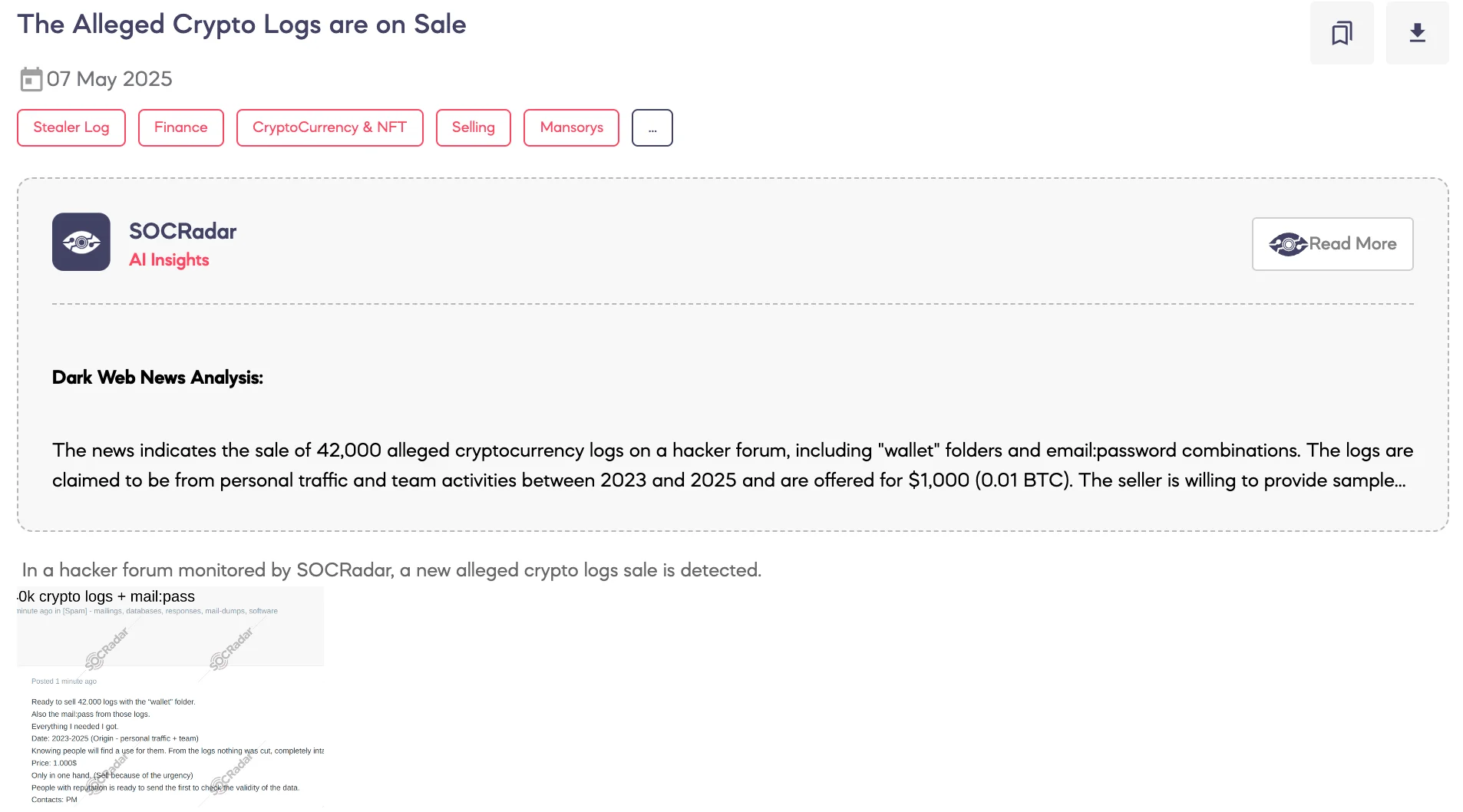
SOCRadar Dark Web Team has identified a new post offering 42,000 stealer logs for sale, including files related to cryptocurrency wallets and mail:pass combinations. The logs, allegedly collected between 2023 and 2025, are said to be complete and untouched. The threat actor is requesting $1,000 and plans to sell the package to a single buyer, citing urgency. Reputation-based buyers are reportedly allowed to verify a sample before purchase.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.

































