
A New Wave of Ransomware Campaigns Targeting Microsoft Teams
For companies all over the globe, Microsoft Teams is becoming an essential tool for teamwork. Nevertheless, because of its extensive use, it has also become a prime target for malicious cyber assaults, especially ransomware campaigns.

DALL-E illustration of Microsoft Teams being under siege
Recent cybersecurity reports have uncovered two distinct ransomware campaigns, orchestrated by STAC5143 and STAC5777, that exploit Microsoft Teams settings to infiltrate organizations undetected. By leveraging Microsoft Teams’ built-in trust mechanisms, these attackers bypass traditional security defenses, tricking employees into opening malicious links or downloading harmful files.
The Increasing Cyber Risk Environment
Worryingly, threat actors are increasingly making use of Microsoft Teams’ communication infrastructure, according to recent cybersecurity information. These threat groups’ tactics involve:
- Social engineering: Using deceptive messages and impersonation, as well as techniques such as phishing, vishing, email bombing, and others, users are manipulated into interacting with malicious content.
- Exploiting protocol vulnerabilities: Taking advantage of weak security settings and exploiting permission vulnerabilities within Teams to gain unauthorized access.
- Abusing user trust: Impersonating legitimate accounts to deceive employees into granting them system privileges or exposing sensitive information.

Microsoft Teams has become a lucrative attack vector for cybercriminals, especially ransomware actors looking to disrupt businesses and make financial gain.
Key Security Vulnerabilities
- Phishing Attacks: Cybercriminals embed malicious URLs in deceptive messages disguised as official communications, leading employees to fake login pages or malware-infected sites.
- Malicious File Transfers: Attackers use Teams’ file-sharing capabilities to distribute ransomware-laden documents that automatically execute upon opening.
- External Collaboration Risks: Misconfigured settings allow unauthorized users to initiate contact and spread malware, sometimes without internal monitoring detecting their presence.
- Credential Harvesting: Attackers employ Teams-based scams to steal login credentials, allowing them to compromise entire networks and spread ransomware internally.
A successful infiltration can cause critical data encryption, operational disruption, and significant financial and reputational damage.
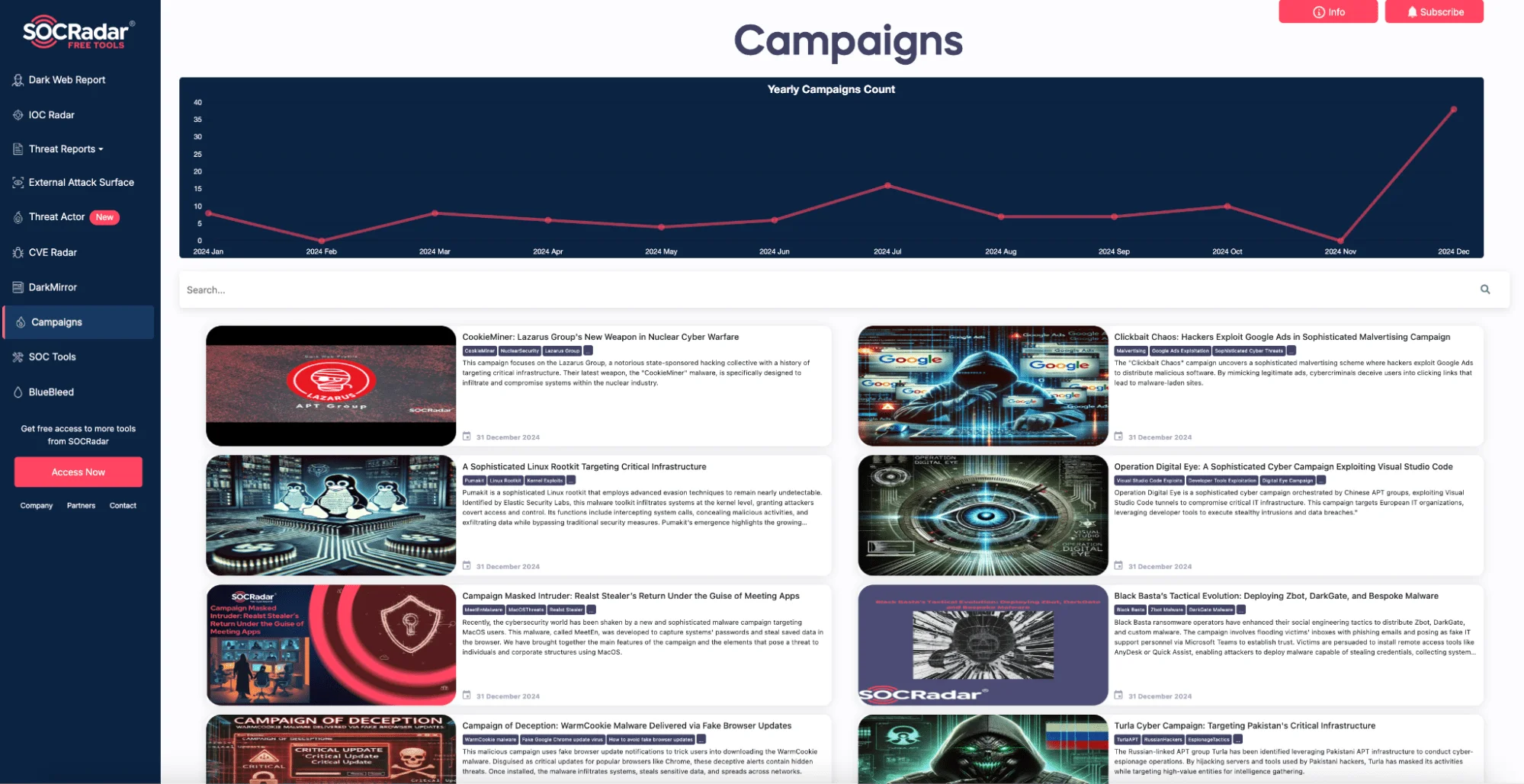
Find information on more Campaigns through SOCRadar LABS
For organizations looking to track ransomware trends and gain deeper insights into emerging cyber threats, SOCRadar LABS Campaigns page provides a centralized hub of intelligence. This platform compiles information on ongoing attack campaigns, including those targeting Microsoft Teams. Security teams can leverage this resource to anticipate cybercriminal tactics, adjust their defenses, and stay informed about the latest campaigns.
Recommended Security Strategies
To mitigate these evolving threats and strengthen Microsoft Teams security, organizations must adopt a multi-layered security approach:
- Implement Multi-Factor Authentication (MFA): Adds an extra layer of protection against unauthorized access by requiring additional verification beyond passwords.
- Enable Advanced Threat Protection (ATP): Uses AI-driven detection mechanisms to identify and block suspicious activities in real-time, preventing malware execution.
- Conduct Regular Security Awareness Training: Employees should be trained to recognize phishing attempts, impersonation tactics, and other social engineering threats.
- Restrict External Collaboration: Limit Teams interactions to trusted domains and vetted third-party partners to reduce exposure to external threats.
- Monitor Communication Channels: Continuously track chat activity for signs of unauthorized access, suspicious file transfers, or unusual login attempts.
- Deploy Endpoint Detection and Response (EDR) Solutions: Implement real-time endpoint monitoring to detect and respond to suspicious activity before an attack escalates.
Identifying New Threats with Proactive Monitoring
Cybercriminal tactics evolve rapidly, making real-time threat intelligence essential for organizations looking to stay ahead. Businesses can strengthen their defenses by:
- Deploying AI-powered threat detection to analyze communication patterns and detect anomalies indicative of an attack.
- Utilizing real-time security analytics to identify potential breaches early and prevent ransomware execution.
- Conducting regular security audits to uncover misconfigurations, enforce security policies, and eliminate potential attack vectors.
- Tracking Dark Web Activity: Monitoring underground forums for leaked credentials, discussions about exploiting Microsoft Teams, and other potential indicators of an imminent attack.
How SOCRadar Enhances Your Security
Beyond employee training and system hardening, Threat Intelligence plays a crucial role in preventing ransomware attacks. SOCRadar’s Cyber Threat Intelligence (CTI) module provides deep visibility into:
- Emerging threats targeting Microsoft Teams, including ransomware campaigns, phishing attempts, and exploit discussions.
- Leaked credentials on the dark web that could be exploited for unauthorized access and privilege escalation.
- Potential vulnerabilities in enterprise VPNs and remote access gateways, reducing exposure to Teams-related cyberattacks.
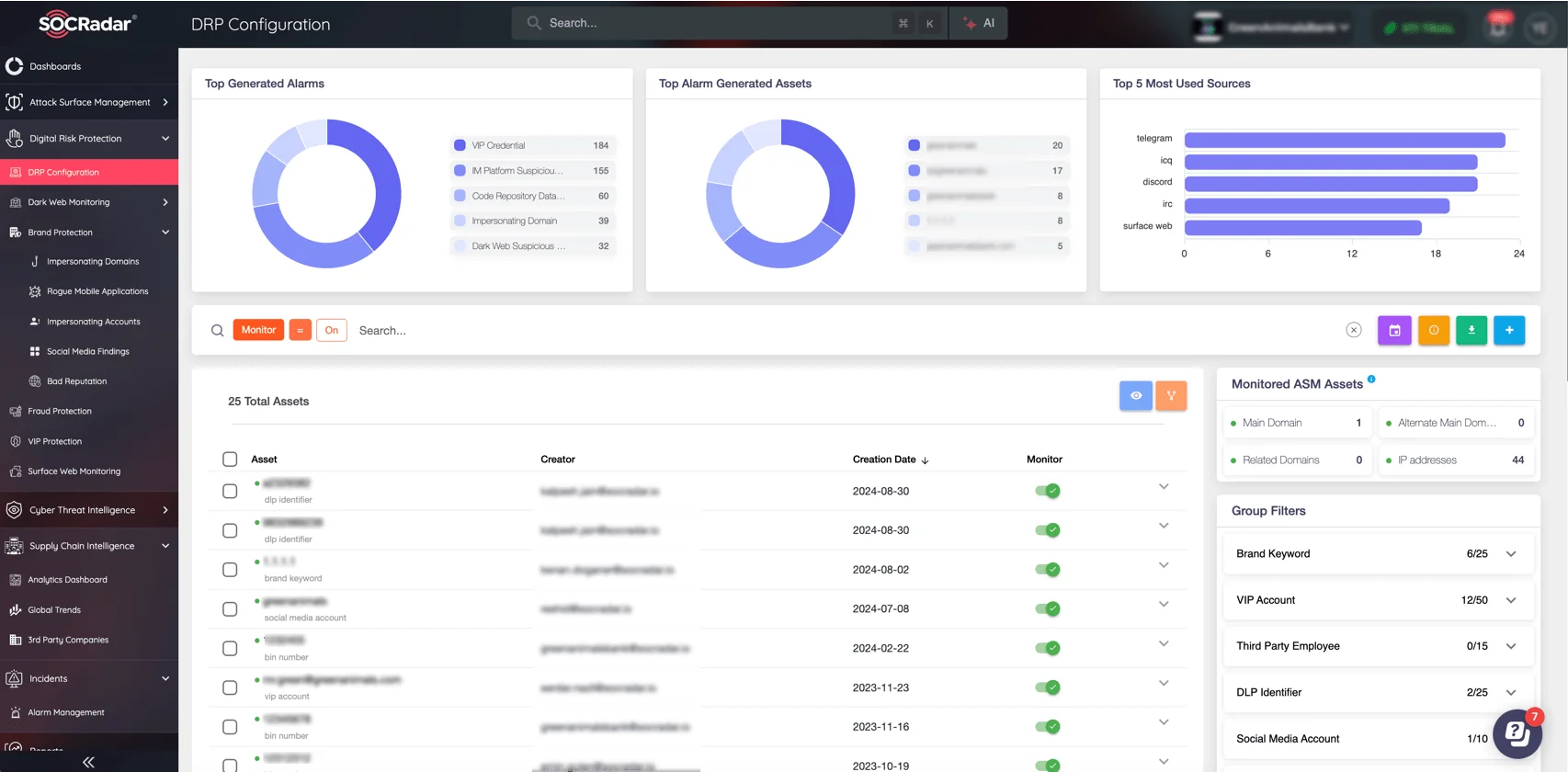
Digital Risk Protection configuration page, SOCRadar XTI platform
Additionally, SOCRadar’s Digital Risk Protection (DRP) ensures businesses remain one step ahead of cybercriminals by continuously monitoring:
- Exposed credentials on the dark web, helping organizations identify compromised accounts before they are exploited.
- Ransomware campaign developments, providing early warnings about new tactics and tools being used against Teams environments.
- Targeted attack trends, enabling organizations to refine security policies and proactively address emerging risks.
- Compromised corporate data, identifying whether sensitive company files have been leaked or are being sold on underground marketplaces.
With SOCRadar’s real-time intelligence and monitoring, organizations can transform Microsoft Teams from a potential risk into a secure collaboration platform. By proactively addressing security vulnerabilities, businesses can safeguard their operations against evolving cyber threats.




































