
Advanced Strategies for Effective Network Security Monitoring
Network Security Monitoring (NSM) is critical for safeguarding an organization’s IT infrastructure against cyber threats. It involves collecting and analyzing security data to detect and identify unauthorized activities within an IT network. Its primary goal is to identify and correlate suspicious network behaviors indicative of potential intrusions.
Cybersecurity experts often highlight that Network Security Monitoring offers more than just a tactical advantage; it’s a critical defense against modern threats like ransomware. 2023 marked the most profitable year in history for ransomware groups, with payments surpassing $1.1 billion; this year is no different. It continues to accelerate even amid successful crackdowns on significant players like LockBit and ALPHV. This underscores the importance of NSM in detecting prolonged intrusions, where attackers can dwell within networks for months, and in identifying breaches as they happen.
Key Strategies Include:
- Real-time Data Collection and Analysis: Effective NSM requires the aggregation of logs and data from all network endpoints in real time. This data is analyzed for Indicators of Compromise (IoCs) or other signs of malicious activity.
- Integration with Security Information and Event Management (SIEM): SIEM platforms consolidate data from multiple sources, enabling automated threat detection and response. This integration is vital for correlating events across the network and improving overall situational awareness.
- Threat Intelligence Integration: Incorporating threat intelligence feeds into NSM enhances the detection of emerging threats by providing context and actionable insights. It allows for the identification of known malicious IPs, domains, and other indicators that may not be visible through internal monitoring alone.
- Scalability and Flexibility: Modern IT environments generate vast amounts of data, necessitating scalable solutions that can handle multi-structured data streams. A robust, scalable data platform is essential for maintaining the efficiency of NSM processes, even as the network grows.
Purposes of Network Security Monitoring
The primary purposes of NSM are to detect, prevent, and respond to security threats. This is achieved through the following objectives:
- Threat Detection: Identifying potential security incidents at an early stage is crucial. NSM helps in detecting unusual patterns, such as abnormal login attempts or unauthorized data access, that may indicate a breach.
- Incident Response: Once a threat is detected, NSM systems enable swift action to mitigate risks. This may involve isolating compromised systems, blocking malicious traffic, or initiating forensic investigations.
- Compliance and Reporting: Many industries are subject to regulatory requirements that mandate the monitoring and reporting of security incidents. NSM helps organizations meet these requirements by providing detailed logs and audit trails.
- Continuous Improvement: NSM also plays a role in refining an organization’s security posture. By analyzing past incidents and trends, security teams can adjust their strategies and defenses to better protect against future threats.
Elevating Network Security Monitoring with Advanced Threat Intelligence
This part is about taking the traditional NSM into one step further. Integrating advanced threat intelligence into network security monitoring significantly enhances an organization’s ability to detect, respond to, and mitigate cyber threats. SOCRadar’s advanced threat intelligence platform exemplifies how such tools can elevate traditional network security monitoring by offering comprehensive insights, real-time threat detection, and proactive defense capabilities.
Comprehensive Threat Intelligence Integration
SOCRadar’s platform integrates a wide range of intelligence sources, including Dark Web Monitoring, Vulnerability Intelligence, and Threat Actor Tracking. This broad visibility allows security teams to anticipate and respond to threats more effectively. The platform provides insights into adversarial Tactics, Techniques, and Procedures (TTPs) and keeps security teams informed of the latest activities by state-sponsored groups and cybercriminal organizations. By leveraging millions of data points, SOCRadar delivers actionable intelligence that informs network security monitoring efforts, ensuring that organizations stay ahead of emerging threats.

SOCRadar Platform can be integrated with many Network Security Monitoring technologies. Click here for further information.
Proactive Threat Hunting and IOC Management
One of SOCRadar’s key strengths is its proactive threat hunting capabilities. Security teams can leverage enriched threat intelligence to identify potential threats before they materialize into full-blown attacks. This proactive approach is essential for preventing incidents and reducing the time attackers can dwell within a network. Additionally, SOCRadar offers integrated Indicator of Compromise (IoC) management, which helps security teams prioritize and act on the most relevant threats, reducing the noise that often plagues traditional security monitoring efforts.
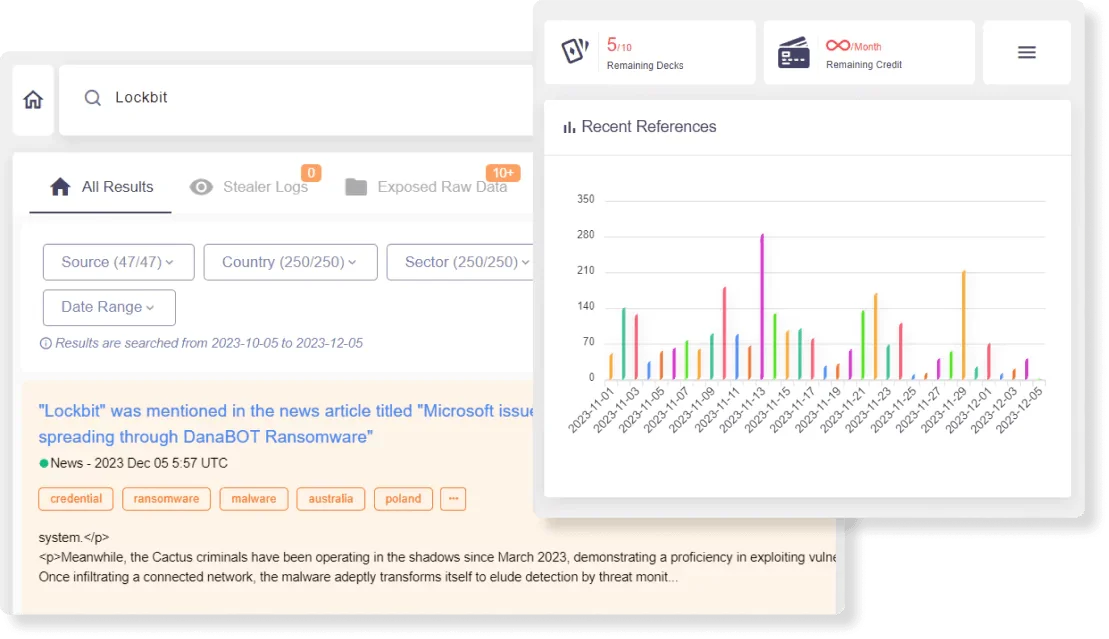
Security teams can also conduct manual threat hunting using SOCRadar’s Dark Web Search Engine.
Real-Time Monitoring and Response
SOCRadar’s platform excels in real-time monitoring, providing continuous visibility into an organization’s digital footprint. This includes monitoring for phishing domains, exposed credentials, and other potential vulnerabilities that can be exploited by attackers. The platform’s ability to detect changes in the attack surface in real-time allows organizations to swiftly address potential threats, ensuring that their defenses remain robust and up-to-date.
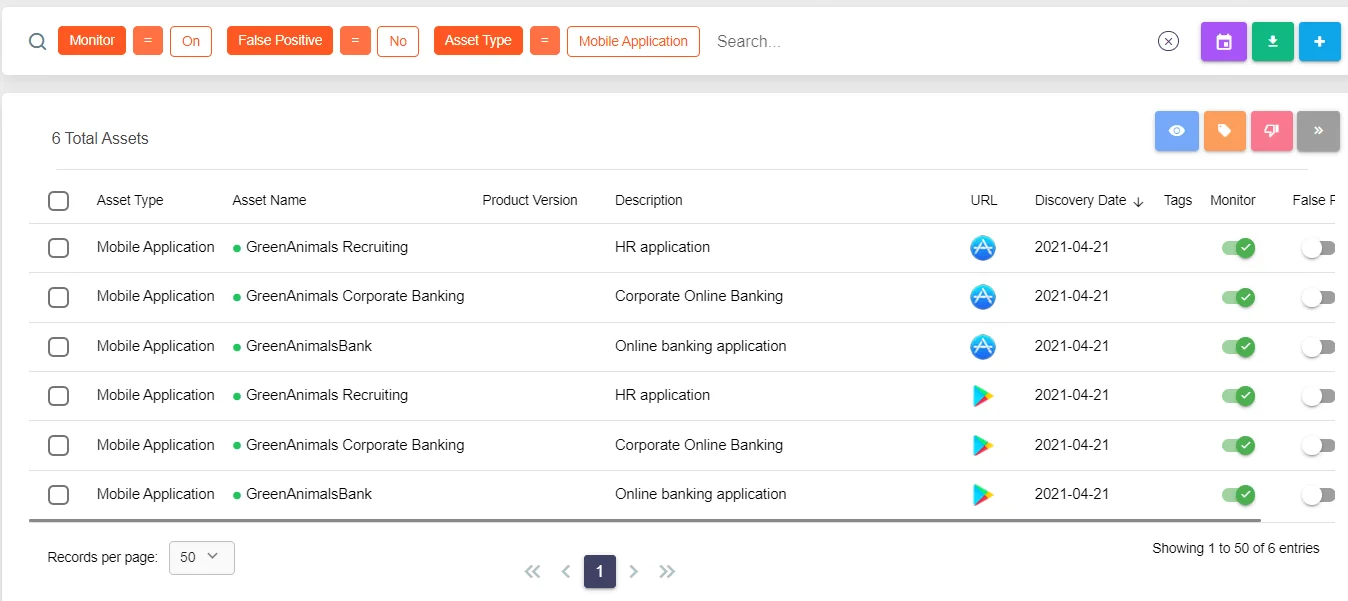
SOCRadar’s Digital Risk Protection Module
Streamlined Incident Response
With SOCRadar’s Extended Threat Intelligence, incident response is more streamlined and efficient. The platform provides detailed intelligence that accelerates investigation processes and aids in the rapid mitigation of identified threats. Security teams can utilize the platform’s intelligence feeds to understand the context and impact of an attack, allowing them to respond more effectively and reduce potential damage.
Conclusion
In summary, robust network security monitoring is crucial for safeguarding organizational assets and maintaining operational integrity. For your help, SOCRadar’s advanced threat intelligence capabilities offer a significant enhancement to network security monitoring. By integrating comprehensive intelligence, proactive threat hunting, and real-time monitoring, organizations can not only strengthen their security posture but also gain a strategic advantage in detecting and mitigating potential threats. This proactive approach enables businesses to stay ahead of cybercriminals, ensuring a resilient defense against the ever-evolving cyber threat landscape.




































