
Analysis of the World-First Cybercrime Index
By organizing and structuring data systematically, indexes provide a compact representation of large datasets, enabling quick access to relevant information when needed. They also play a crucial role in cyber threat intelligence. Intelligence analysts use indexes to determine the severity of attacks or address those sources when they need additional information. CTI relies heavily on the analysis of available data to identify threats and vulnerabilities, and indexing data allows quick retrieval and analysis when required.
Another crucial aspect of indexes is their exponential value growth when employing a multi-stakeholder approach. Cybersecurity threats frequently transcend organizational boundaries. By sharing essential intelligence, organizations can collectively bolster their defenses and enhance readiness for emerging threats, as cyber attackers commonly target multiple organizations employing similar tactics.
When considering indexes or databases, the scenario remains the same. Through collaboration, organizations can gather essential information collectively, rather than each organization independently undertaking the same task repeatedly.
Free External Threat Assessment Report from SOCRadar Labs
In order to get the necessary intelligence for your security needs, you can visit SOCRadar Labs to acquire your External Threat Assessment Report.
What is this Cybercrime Index About?
World Cybercrime Index is an index developed by scholars from the University of Oxford, Sciences Po, the University of New South Wales, and Monash University. This index presents the cybercrime levels of various countries based on expert views.
What sets this index apart from others is its departure from the conventional criteria of evaluating countries or organizations based on adherence to prescribed rules and the security robustness of their systems. Instead, this index adopts a distinctive methodology, focusing on the prevailing cybercrime rates across different nations.

World Cybercrime Index Research Article (source: here)
Background and Methodology of the Cybercrime Index
Technical challenges surrounding the attribution issue in cybersecurity constitute a longstanding and extensively debated topic, particularly within law and policymaking. Attributing crimes is challenging, and providing conclusive evidence for such attributions is even more complicated.
The authors of this index also acknowledge this difficulty and have endeavored to explore alternative solutions for establishing a viable attribution system. They propose to use expert opinions.
The authors collaborated with cybersecurity experts to obtain their opinions instead of relying on technical data, which can be easily falsified when it comes to attribution.
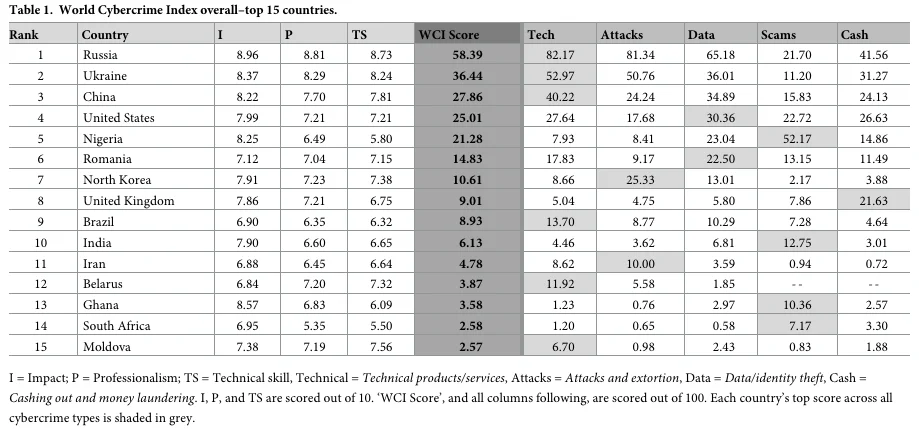
Top 15 countries of World Cybercrime Index
They created a methodology for identifying cybersecurity experts. Subsequently, they administered a survey prompting them to assess five primary categories of cybercrime: Technical products/services, Attacks and extortion, Data/identity theft, Scams, and Cashing out/money laundering.
The experts then nominate the countries they deem to be the most significant sources of each type of cybercrime and subsequently rank each nominated country based on the impact, professionalism, and technical proficiency of threat actors.
Utilizing the responses provided by the experts, the authors generated scores for each cybercrime category, which were then used for an overarching ranking of cybercrime levels by country.
According to the article, they also adhered to a rigorous system for selecting experts, aiming to mitigate bias coming from political views. To achieve this goal, they chose experts with diverse backgrounds from various regions across the globe, including Africa, Asia Pacific, Europe, North America, and South America.
Possible use cases
If this index continues to operate and maintain its current standards, it promises to evolve into an invaluable resource for CTI analysts, policymakers, and international legal professionals. Since it generates valuable information, it has the potential to evolve into a comprehensive database that can be utilized in the preparation of various reports and decision-making processes.
Over time, as this index develops, there is significant potential for creating an even more comprehensive database dedicated to cataloging detailed information about cybercrime. Such an expanded repository could offer extensive data covering various facets of cyber threats, ranging from common attack vectors to emerging trends and tactics employed by cybercriminals based on their countries or regions.
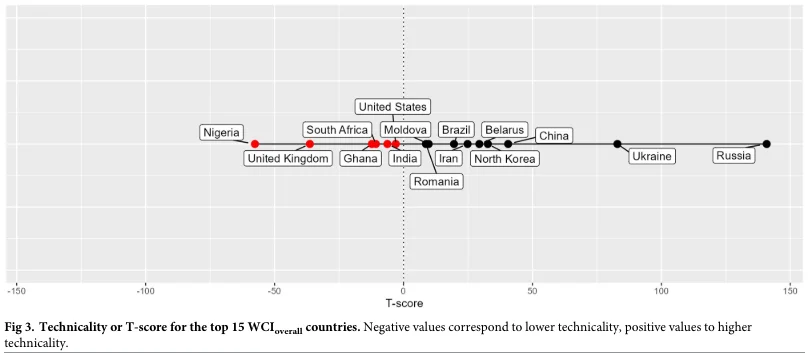
The technicality of the countries in Top 15
Organizations can use the index to assess the cybercrime level of countries they operate in or plan to expand into. This helps understand the potential risks of operating in those regions and allows for better risk management strategies. Governments and businesses can allocate resources more effectively by prioritizing cybersecurity measures in regions with higher cybercrime levels, as indicated by the index. The index can be a benchmarking tool for comparing the cybersecurity posture of different countries over time. Policymakers can use the index to inform the development of cybersecurity policies and regulations.
Country Threat Landscape Report from SOCRadar Labs
For more detailed intelligence about a country and the threats targeting there, check Country Threat Landscape Report
Conclusion
Gathering information is crucial, yet transforming this information into actionable intelligence holds even greater significance. The creation of databases is a vital part of this process since they hold the raw material in a systematic order.
At SOCRadar, we diligently collect information about vulnerabilities, threat actors, breaches, and many more data points. SOCRadar Extended Threat Intelligence generates invaluable intelligence tailored to your needs.




































