
Analysis of UK Password Dictionary: The Ultimate Wordlist
Passwords should be strong and unique. They act as the first line of defense in safeguarding our personal and business digital assets. As we explore the most commonly used passwords in the UK, we hope to shed light on the patterns and trends that emerge, as well as the implications for cybersecurity.
As cyber threats become more advanced, understanding the specifics of password security is critical for both individuals and organizations. Join us on this journey as we explore the complex world of password security in the UK.
Our Password List
In the field of cybersecurity, password lists are crucial resources that provide insights into the nuances of online security behaviors. These lists offer a comprehensive collection of the words, phrases, and character combinations frequently chosen as passwords by individuals navigating the digital world. While these lists serve as learning tools for security practitioners to discourage the use of weak passwords, they can also be exploited by malicious actors to orchestrate their attacks.
We explored the weaknesses of commonly used passwords in our previous blog post here, providing a global snapshot of the most prevalent passwords. This research served as a springboard for further investigation. The password dictionary, named srwordlist.txt, was curated by our team of analysts at SOCRadar, using various sources like dark web forums and Telegram channels. This list encapsulates 1,788 of the most popularly used passwords.
To delve deeper, we extracted the most commonly used passwords in the UK using swordlist_uk_250.txt for this analysis. If you’re interested in our previous research on the USA, you can delve into our in-depth analysis in this article.
Exploring the UK Password List
The list we’ve compiled for the UK is organized based on the frequency of each password’s use. The most frequently used password, ‘123456’, occurred as many as 69,208 times, while the least common among the top 10, ‘12345678’, was detected 14,945 times. Here’s a look at the top 10:
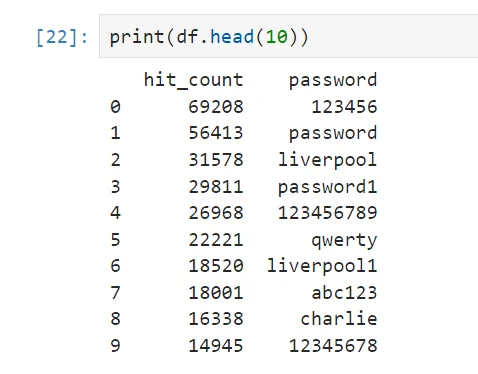
Top 10 passwords from the list
When comparing the UK’s top 10 passwords to the global and USA top 10 lists, some interesting patterns emerge. The password ‘123456’ tops all three lists, indicating its widespread use across different regions. Similarly, ‘password’, ‘123456789’, ‘qwerty’, and ‘abc123’ feature in all three top-10 lists, suggesting a universal trend of using simple, easy-to-remember passwords.
A unique trend in the UK data is the inclusion of ‘liverpool’ and ‘liverpool1’, reflecting the popularity of football in UK culture. This trend of using popular sports teams as passwords is not observed in the USA or global top 10.
However, regardless of the region, the top passwords are predominantly simple and predictable, indicating a widespread disregard for strong password practices. This underscores the need for continuous education on the importance of robust, unique passwords in safeguarding digital assets.
NIST Guidelines
The National Institute of Standards and Technology (NIST) outlines specific guidelines to ensure robust password creation. These guidelines typically suggest the following for strong passwords:
- The password should be at least 8 characters long (though longer is always better).
- It should include a mixture of letters and numbers.
- Both uppercase and lowercase letters should be used.
- Special characters should be incorporated to increase complexity.
To evaluate the strength of each password in our UK list, we assigned them scores based on these parameters. For each guideline met, a password receives one point. However, if a password is shorter than 8 characters, it will receive a score of zero, regardless of how many other guidelines it fulfills.
We implemented the following Python code in a Jupyter Notebook to assign these scores and derive new attributes from our existing dataset, ultimately allowing us to measure the complexity of each password.
# A function to calculate the score and parameters for each password
def calculate_score_and_parameters(password):
score = 0
uppercase = 0
lowercase = 0
numbers = 0
symbols = 0
# If password has less than 8 characters, return 0 for all parameters
if len(password) < 8:
return pd.Series({‘score’: 0, ‘uppercase’: 0, ‘lowercase’: 0, ‘numbers’: 0, ‘symbols’: 0})
# Check if password contains uppercase letters, lowercase letters, numbers, and symbols
if any(char.isupper() for char in password):
score += 1
uppercase = 1
if any(char.islower() for char in password):
score += 1
lowercase = 1
if any(char.isdigit() for char in password):
score += 1
numbers = 1
if any(not char.isalnum() for char in password):
score += 1
symbols = 1
return pd.Series({‘score’: score, ‘uppercase’: uppercase, ‘lowercase’: lowercase, ‘numbers’: numbers, ‘symbols’: symbols})
# Calculate the score and parameters for each password
new_columns = df[‘password’].apply(calculate_score_and_parameters)
df = pd.concat([df, new_columns], axis=1)
display(df)
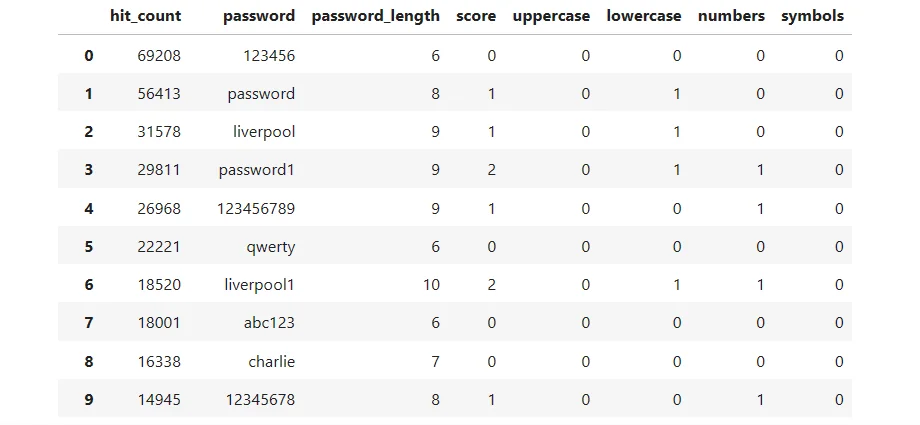
List of passwords based on the set parameters
Our analysis of the UK password list has yielded some intriguing insights. To begin, we calculated the average strength of the passwords based on the parameters they satisfy. Given that many passwords are shorter than 8 characters, which is a clear indicator of password strength, the average score was 0.684 which is so close to 0.
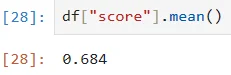
The average score of the passwords
However, to gain a more accurate understanding of password strength, we decided to exclude the short passwords and recalculate the average score. This approach gives us a more nuanced view of the strength of passwords that meet the minimum length requirement.
The average score of the passwords, excluding those shorter than 8 characters, is 1.71 out of 4. This score is a clear improvement over the overall average of 0.684, which includes all passwords. However, it still falls short of the maximum score of 4, indicating that even the longer passwords in our list are not as strong as they could be
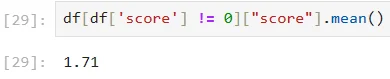
The average score of the passwords excluding the short ones
Our analysis of password strength in the UK reveals an interesting comparison with the USA. The average password strength score in the USA was 1.5, while for The UK it is 1.71 out of 4, suggesting that UK users are, on average, using slightly stronger passwords.
Password Parameters Score Distribution
From our analysis, we found that a significant 60% of the passwords in the UK list scored zero, indicating that they did not meet any of the strength parameters. On the other end of the spectrum, a mere 0.4% of the passwords managed to satisfy all four parameters, achieving the maximum score.
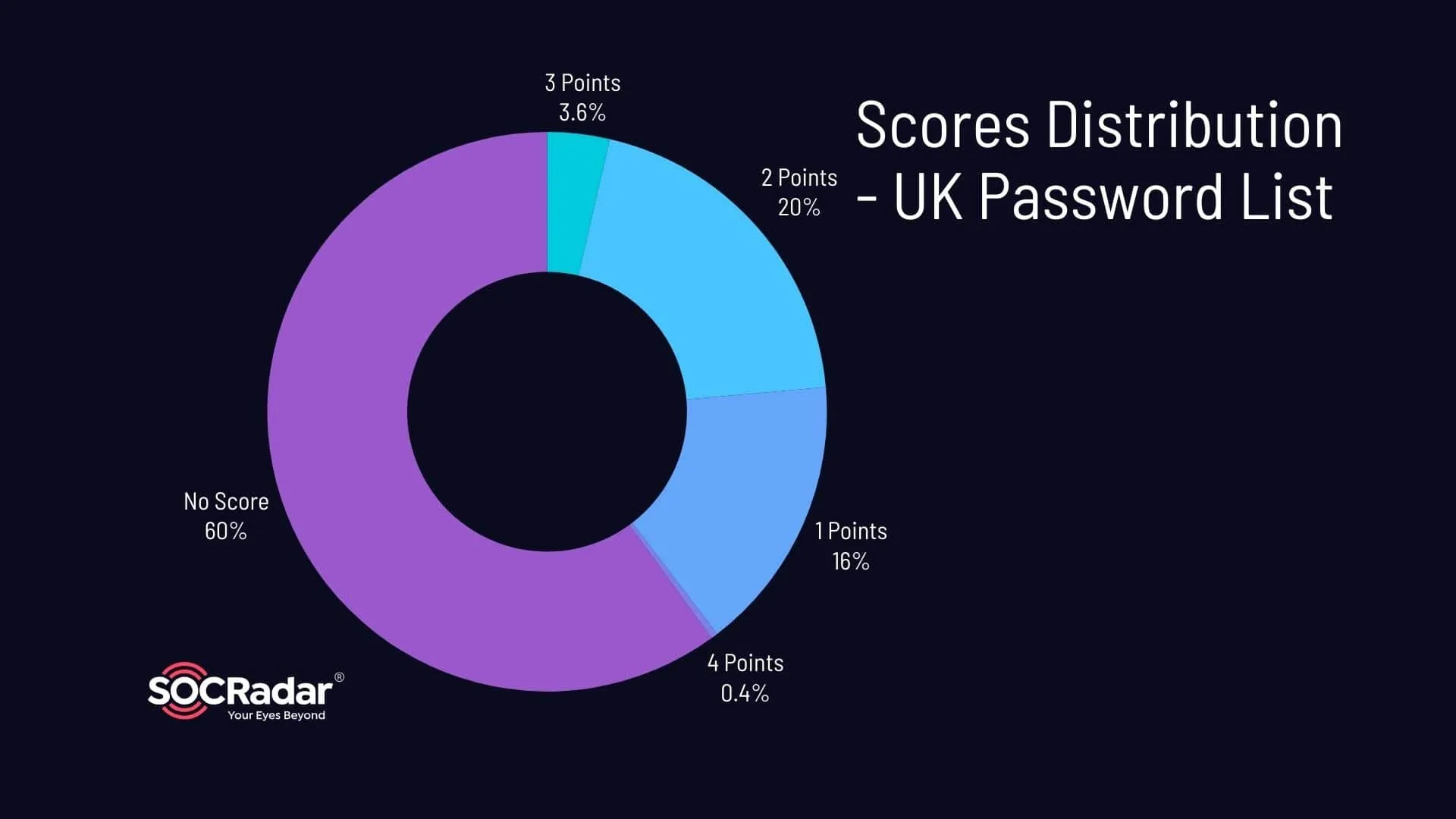
Distribution of the Scores – UK Password List
When we break down the parameters, we find that only 31.6% of the passwords included lowercase letters, and a slightly lower 24% incorporated numbers. The use of uppercase letters was even less common, with only 4.8% of the passwords including at least one uppercase letter. The use of symbols was almost non-existent, with a mere 0.1% of the passwords incorporating symbols.
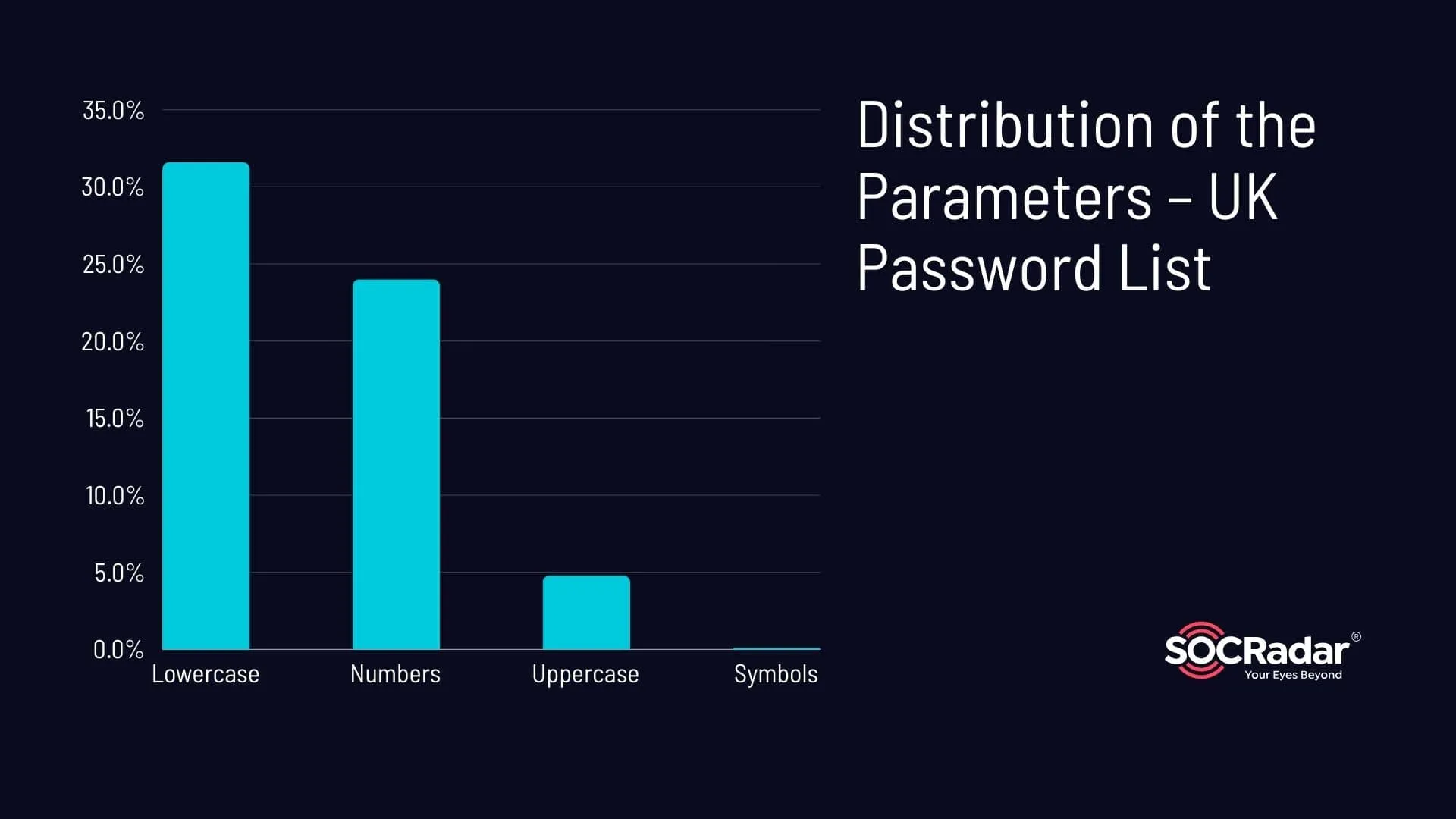
Distribution of the Parameters – UK Password List
UK Banned Weak Password Devices
In recent times, the UK has taken significant steps to strengthen cybersecurity across the nation, particularly in the realm of password security. The statistics from our earlier analysis of UK password lists suggest a clear need for such measures.
Echoing the need for more robust password practices, the UK government has recently enacted new regulations that enforce legal requirements on manufacturers of internet-connected devices to ensure these devices are safeguarded against cybercriminal access.
These laws specifically target the use of weak and commonly used passwords such as ‘admin’ or ‘12345’, which, as our analysis revealed, represent a significant proportion of passwords in use. Such passwords are now prohibited in the UK, and all smart devices must comply with these minimum security standards.
This significant move places the UK among the first countries to legally enforce such stringent cybersecurity measures on smart devices, potentially inspiring other nations to follow suit. These regulations align with the findings of our password analysis, underscoring the need for stronger password practices to protect against potential cyber threats.
Passwords Lengths Distribution
import matplotlib.pyplot as plt
# Calculate the length of each password
df[‘password_length’] = df[‘password’].apply(len)
# Specify the groups for password lengths
groups = [1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14]
# Group passwords based on their length
passwords_grouped = df.groupby(pd.cut(df[‘password_length’], bins=groups, right=False)).size()
# Plot the distribution of password lengths
plt.bar(range(len(passwords_grouped)), passwords_grouped, align=’center’, tick_label=[f'{i}’ for i in groups[:-1]])
plt.xlabel(‘Password Length’)
plt.ylabel(‘Frequency’)
plt.title(‘Distribution of Password Lengths’)
plt.show()
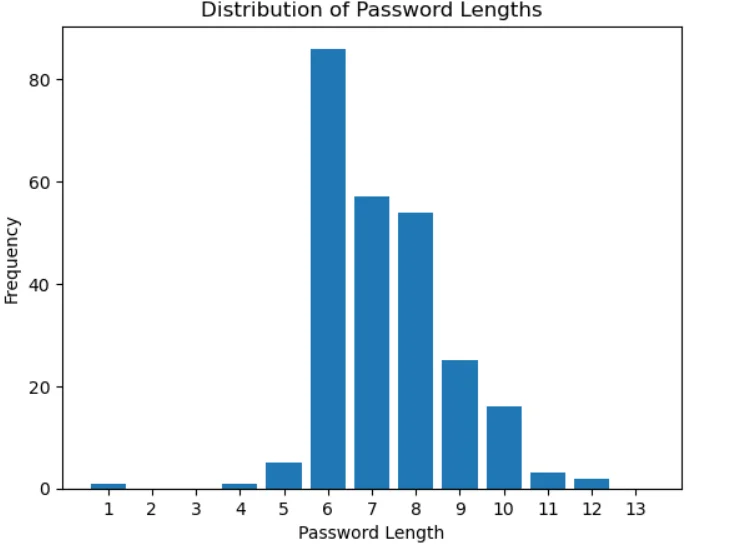
Password length distribution
Understanding password length distribution helps organizations spot trends, like the common use of short, guessable passwords. This knowledge enables proactive enforcement of robust password policies. The following chapter highlights the severe risks associated with short passwords and lax password policies.
Conclusion
After examining the UK password list, it’s evident that many passwords used to protect sensitive information, such as emails, are alarmingly weak. While the data does not represent all UK password usage, it does give insight into those exposed in breaches, indicating a concerning trend.
The recent UK regulations banning weak passwords on internet-connected devices demonstrate a significant move towards improving platform security. But it’s also a stark reminder of the ongoing threat of stealer logs, which can capture even the strongest passwords if not appropriately managed.
In our previous posts, we’ve discussed Password Monster, a tool that can help users understand the strength of their passwords. For instance, Password Monster shows that the password “charlie” can be guessed in just 0 seconds. This password is in the top 10 on the UK list, highlighting the need for stronger passwords.
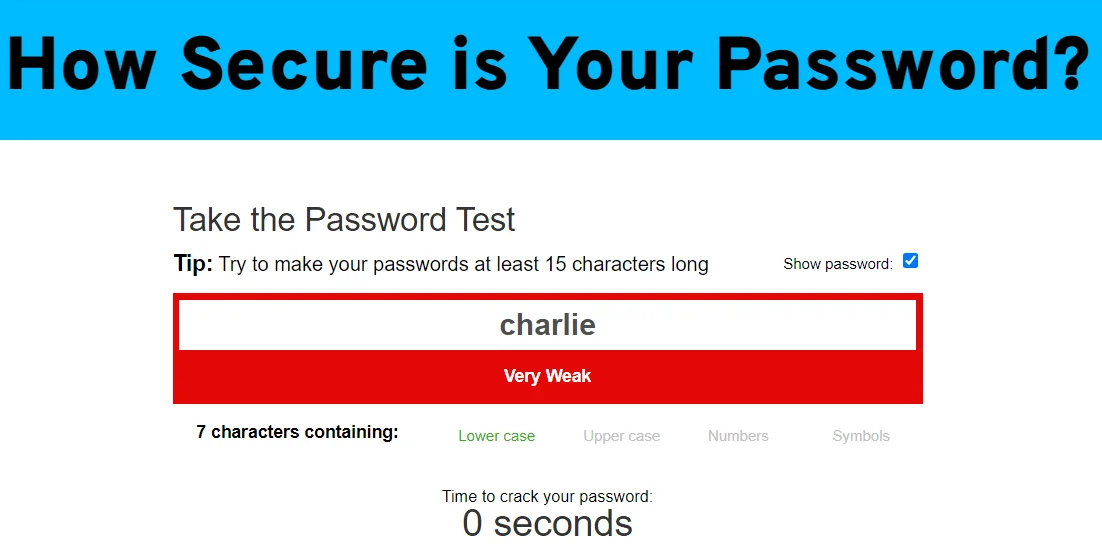
Password Monster shows how easy it is to guess the password charlie
Choosing secure, unique passwords and using two-factor authentication are critical for maintaining good password hygiene. However, we must also consider the importance of platform security and the threat of stealer logs.
SOCRadar’s Account Breach Check service offers a robust solution to the potential risks exposed in our analysis. This service allows you to check whether your personal or professional email accounts have been compromised in a data breach. It’s an invaluable tool for staying ahead of potential threats and securing your data against cybercriminals.
SOCRadar’s Account Breach Check service
With the Free Edition, you can explore the Breach Dataset features of the SOCRadar XTI platform:




































