
Exploring the NIST Cybersecurity Framework: Strengthening Digital Resilience
In today’s rapidly evolving digital landscape, the term “cybersecurity” has become synonymous with safeguarding our most valuable assets: information and data. As we continue to witness an increasing number of cyber threats and attacks, ranging from data breaches to ransomware incidents, the significance of robust cybersecurity measures cannot be overstated.
Safeguarding the Digital Frontier: Unveiling the NIST Cybersecurity Framework
The criticality of cybersecurity is not confined to just a few sectors; it extends across industries, affecting businesses, governments, and individuals alike. With this escalating threat landscape, the need for a comprehensive and structured approach to cybersecurity has become evident. This is where the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) steps in.

Developed by NIST, a non-regulatory federal agency within the United States Department of Commerce, the NIST CSF offers a systematic way to manage and mitigate cybersecurity risks, ensuring the resilience of organizations in the face of potential cyber threats. In this blog post, we enter the world of the NIST Cybersecurity Framework, understanding its components, objectives, and the benefits it brings to the realm of cybersecurity. From its inception to its latest version, we’ll explore the evolution of the framework and highlight the key features that make it an essential tool in the fight against cyber threats. So, why exactly do we need a cybersecurity framework like NIST CSF? Let’s explore this question in detail.
Unleashing Cyber Guardians: What is NIST Cybersecurity Framework (NIST CSF)?
The NIST Cybersecurity Framework (NIST CSF) is a comprehensive set of guidelines, standards, and best practices designed to help organizations manage and mitigate cybersecurity risks effectively. Developed by the National Institute of Standards and Technology (NIST) in the United States, the framework provides a structured approach for organizations to assess, improve, and communicate their cybersecurity posture.
Empowering Digital Immunity: What is the Aim of NIST CSF?
The primary aim of the NIST CSF is to provide organizations with a practical and adaptable framework that facilitates the creation of strong cybersecurity programs. By offering a common language and a standardized set of processes, the framework enables organizations to:
- Identify and prioritize cybersecurity risks
- Implement cybersecurity best practices
- Detect and respond to cyber threats
- Recover quickly from cyber incidents
In essence, the NIST CSF empowers organizations to build a resilient cybersecurity infrastructure that can withstand and recover from various cyber threats and attacks.
Building Cyber-Strong Fortresses: What are the Parts of NIST CSF?
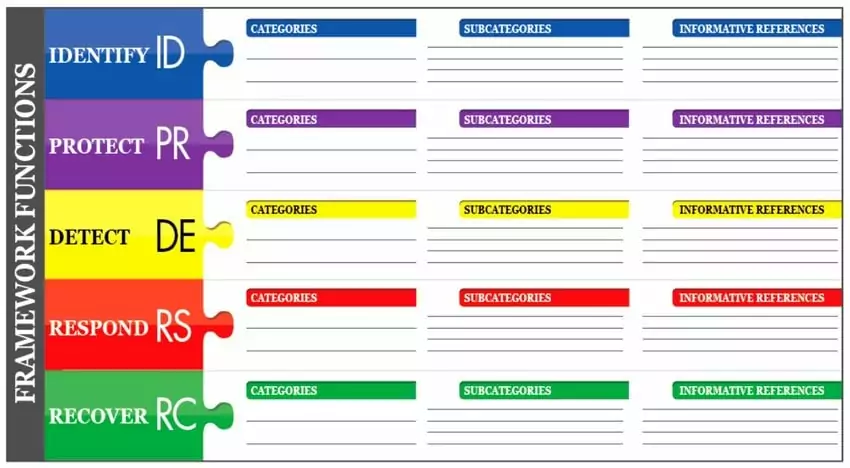
The NIST CSF is structured around a core set of functions, categories, and subcategories that form the foundation of effective cybersecurity practices. These parts are:
Functions: The framework is built upon five high-level functions, namely Identify, Protect, Detect, Respond, and Recover. Each function represents a key aspect of cybersecurity management.
Categories: Each function is further divided into categories that provide a specific focus on various cybersecurity activities. These categories help organizations address specific aspects of cybersecurity risk.
Subcategories: Subcategories are specific statements that outline the desired outcomes within each category. These subcategories offer actionable guidance for organizations to achieve their cybersecurity objectives.
Informative References: Informative References are external standards, guidelines, and practices that organizations can consult to further enhance their cybersecurity measures. While the Framework Core provides the foundational structure, Informative References offer additional resources that organizations can consider for implementing specific controls or addressing industry-specific requirements.
Mastering the Cyber Chessboard: How Does NIST CSF Help?
The NIST CSF offers numerous benefits to organizations seeking to enhance their cybersecurity posture:
Risk Assessment: The framework helps organizations assess their current cybersecurity practices and identify potential vulnerabilities, enabling them to prioritize their efforts effectively.
Customization: NIST CSF is not a one-size-fits-all solution. Organizations can customize the framework to align with their unique business needs and risk tolerance.
Communication: The framework provides a common language for communicating cybersecurity requirements among stakeholders, making it easier to collaborate with partners and suppliers.
Continuous Improvement: NIST CSF supports a cyclical process of improvement. Organizations can repeatedly assess their cybersecurity practices, identify gaps, and implement targeted enhancements.
Building the Foundation of Cybersecurity: Framework Core
At the heart of the NIST Cybersecurity Framework (NIST CSF) lies the Framework Core, a structured set of functions, categories, and subcategories that provide a clear roadmap for organizations to establish a robust cybersecurity program. The Core serves as the foundation upon which organizations can build their cybersecurity strategies, assess their current practices, and identify areas for improvement.
Framework Core Functions:
The Framework Core is organized into five distinct functions, each representing a critical aspect of effective cybersecurity management:
Identify: This function involves understanding and managing cybersecurity risks to systems, people, assets, and data. It forms the basis for developing a comprehensive understanding of an organization’s cybersecurity landscape.
Protect: The Protect function encompasses safeguarding assets and limiting the impact of cybersecurity incidents. It includes implementing safeguards to ensure the delivery of critical services and managing access to sensitive data.
Detect: Detecting potential cybersecurity events is the focus of this function. Organizations establish mechanisms to identify anomalies, intrusions, and other unauthorized activities promptly.
Respond: In the event of a cybersecurity incident, the Respond function guides organizations in developing effective response and mitigation strategies. This function emphasizes minimizing damage and restoring normal operations.
Recover: After a cybersecurity incident, the Recover function assists organizations in swiftly recovering their normal operations. This includes restoring affected systems and services to minimize downtime.
Categories and Subcategories:
Each function within the Framework Core is further divided into categories and subcategories, offering a more detailed breakdown of specific cybersecurity activities. Categories provide a thematic grouping of related cybersecurity outcomes, while subcategories define specific desired outcomes within each category.
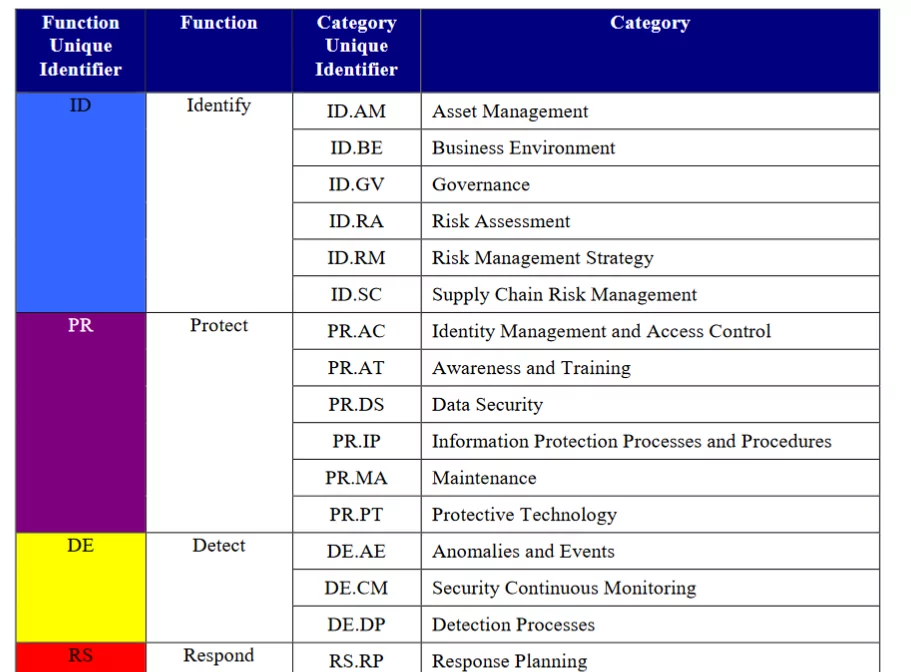
For instance, within the “Identify” function, the category “Asset Management” covers activities related to managing and understanding an organization’s assets. Under this category, there are subcategories like “ID.AM-1: Physical devices and systems within the organization are inventoried” and “ID.AM-2: Software platforms and applications within the organization are inventoried.”
Using the Framework Core:
Organizations can utilize the Framework Core in several ways:
Assessment: By assessing their cybersecurity practices against the Core’s functions, categories, and subcategories, organizations can identify gaps and areas of improvement.
Customization: The Framework Core is not a rigid checklist; it’s designed to be adaptable. Organizations can customize it to their specific needs and risk tolerance.
Prioritization: The Core allows organizations to prioritize their cybersecurity efforts based on the identified risks and their potential impact.
Communication: The structured language of the Framework Core facilitates effective communication about cybersecurity practices among stakeholders.
Incorporating the Framework Core into their cybersecurity strategies empowers organizations to establish a comprehensive and effective approach to cybersecurity risk management. As the threat landscape evolves, the Core’s flexible structure ensures that organizations can continuously adapt and strengthen their cybersecurity defenses.
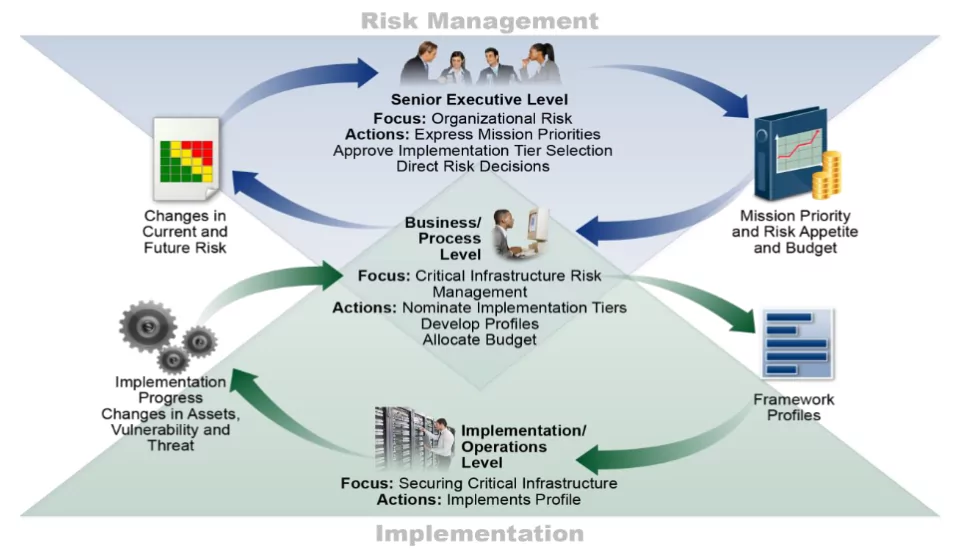
Climbing the Cybersecurity Ladder: Implementation Tiers
While the Framework Core provides a detailed roadmap for cybersecurity practices, the NIST Cybersecurity Framework (NIST CSF) also introduces the concept of Implementation Tiers. These tiers serve as a tool for organizations to assess and communicate their cybersecurity maturity and readiness, allowing them to align their efforts with their specific risk management goals and resources.
Understanding Implementation Tiers:
Implementation Tiers are a reflection of an organization’s overall approach to managing cybersecurity risks. They are designed to capture both the sophistication of an organization’s cybersecurity practices and the extent to which those practices are integrated into its overall risk management strategies.
The NIST CSF defines four Implementation Tiers:
Tier 1 – Partial: Organizations at this tier have an ad-hoc approach to cybersecurity, with practices that are inconsistent or reactive. There might be a lack of awareness about the organization’s critical assets and cybersecurity risks.
Tier 2 – Risk Informed: This tier signifies that an organization has a more structured approach to cybersecurity risk management. It involves the development of risk management processes and the identification of key assets and risks.
Tier 3 – Repeatable: Organizations at this tier have well-defined cybersecurity practices and processes. They can effectively implement and manage their cybersecurity strategies, and they regularly review and update these practices.
Tier 4 – Adaptive: The highest tier indicates that an organization has an adaptive and evolving cybersecurity strategy. It is proactive in identifying and responding to emerging threats and has a strong understanding of its cybersecurity risks and their potential impacts.
Benefits of Using Implementation Tiers:
Implementation Tiers offer several benefits for organizations:
Self-Assessment: Organizations can assess their current cybersecurity posture and determine which tier aligns best with their practices.
Goal Setting: Tiers provide a clear target for organizations to aim for in terms of their cybersecurity maturity.
Resource Allocation: Organizations can allocate resources more effectively by targeting the tier that aligns with their risk management goals.
Communication: Implementation Tiers offer a standardized way to communicate an organization’s cybersecurity maturity to stakeholders, including clients, partners, and regulators.
Selecting the Right Tier:
Choosing the appropriate Implementation Tier involves considering factors such as an organization’s risk tolerance, available resources, industry regulations, and overall business objectives. It’s important to note that the goal is not necessarily to achieve the highest tier, but rather to achieve a tier that aligns with an organization’s risk management strategy and its commitment to cybersecurity.
By using Implementation Tiers in conjunction with the Framework Core, organizations can establish a comprehensive and tailored cybersecurity program that not only addresses their unique risks but also allows for continuous improvement and adaptation in the face of evolving cyber threats.
Evolving Stronger: What Are the Differences Between 1.1 and 1.0?
The NIST CSF has seen an evolution from its initial version, 1.0, to its subsequent release, version 1.1. Some key differences include:
Clarifications: Version 1.1 brought clarity to terms like “compliance,” addressing potential confusion among stakeholders. It also introduced a section on self-assessment to guide organizations in using the framework effectively.
Vulnerability Disclosure: A new subcategory related to the vulnerability disclosure lifecycle was introduced in version 1.1, reflecting the changing landscape of cybersecurity threats.
Feedback and Consultation: Version 1.1 incorporated feedback from various stakeholders, including responses to requests for information and comments on proposed drafts. This iterative process ensured that the framework remains relevant and effective.
Arming Against the Unknown: Leveraging Cybersecurity Solutions to Implement NIST CSF
Implementing the NIST Cybersecurity Framework (NIST CSF) can be greatly facilitated by utilizing specialized cybersecurity solutions like SOCRadar Extended Threat Intelligence. These solutions offer tailored tools and capabilities that align with the Framework’s core principles, enabling organizations to enhance their cybersecurity posture effectively. Here, we explore how specific cybersecurity solutions such as SOCRadar`s capabilities like External Attack Surface Management, Digital Risk Protection Services, and Threat Intelligence contribute to the implementation of NIST CSF.
SOCRadar encompasses a range of cybersecurity tools designed to proactively identify, analyze, and mitigate potential threats. SOCRadar`s Capabilities include advanced and early threat detection, vulnerability management, and incident response features. By employing SOCRadar, organizations can achieve several outcomes outlined in the NIST CSF. For instance, the “Identify” function can be strengthened through continuous monitoring and threat detection. Additionally, vulnerability assessment and management offered by these suites directly contribute to the “Protect” and “Respond” functions of the Framework by addressing vulnerabilities promptly and efficiently.
External Attack Surface Management:
External Attack Surface Management focus on monitoring an organization’s external-facing assets and identifying potential points of entry for cyberattacks. This directly aligns with the NIST CSF’s “Identify” and “Protect” functions. By comprehensively identifying their attack surface, organizations can better understand their risk exposure, prioritize protection efforts, and fortify their defenses against potential threats.
Digital Risk Protection Services:
Digital Risk Protection encompasses tools and strategies to safeguard an organization’s digital footprint, including brand reputation, sensitive data, and customer trust. These services contribute significantly to the NIST CSF’s “Detect,” “Respond,” and “Recover” functions. By monitoring online channels for threats, organizations can detect malicious activities early, respond promptly to incidents, and recover more effectively from potential breaches or reputational damage.
Threat Intelligence:
Threat Intelligence solutions provide organizations with real-time insights into emerging cybersecurity threats, attack vectors, and adversary tactics. Incorporating threat intelligence into their cybersecurity strategy allows organizations to enhance both the “Identify” and “Protect” functions of the NIST CSF. By staying informed about evolving threats, organizations can identify potential risks, adapt their protective measures, and proactively defend against emerging cyberattacks.
Incorporating these specialized cybersecurity solutions can amplify an organization’s efforts to implement the NIST Cybersecurity Framework. By aligning with the Framework’s core principles, these solutions provide targeted tools and insights that help organizations achieve the desired outcomes of risk management, threat detection, incident response, and overall cybersecurity enhancement.
Firming the Digital Ramparts: Embracing a Secure Future with NIST CSF
In conclusion, the NIST Cybersecurity Framework stands as a beacon of guidance in the turbulent sea of cyber threats. It serves as a testament to the collaboration between industry, government, and academia in fostering digital resilience.
As technology advances and threats evolve, the Framework Core remains adaptable, providing a solid foundation for organizations to build their cybersecurity strategies upon. Its Implementation Tiers offer a valuable means of self-assessment and goal setting, aligning cybersecurity efforts with business objectives.
Moreover, with the support of specialized cybersecurity solutions like SOCRadar, organizations can seamlessly integrate the principles of NIST CSF into their operations, enhancing their ability to identify, protect, detect, respond, and recover.
As the digital landscape continues to transform, the NIST CSF, with its continuous improvements and dynamic framework, ensures that the global digital ecosystem can thrive securely. Together, through frameworks and strategic solutions, we fortify the walls that shield our digital future.




































