ASUS Routers Under Risk of RCE Attacks: Critical Vulnerabilities Found (CVE-2023-39238, CVE-2023-39239, CVE-2023-39240)
Security researchers have recently unearthed three security vulnerabilities affecting several ASUS router models.
ASUS, renowned as one of the leading networking manufacturers, boasts a substantial global user base of gamers, streamers, and various other consumers who rely on ASUS routers for their networking needs.
What are the vulnerabilities in ASUS about?
Taiwan’s Computer Emergency Response Team (TWCERT/CC) disclosed the three vulnerabilities as format string vulnerabilities.
The vulnerabilities primarily arise from verification issues within the ASUS routers, potentially granting attackers the ability to execute code remotely, disrupt services, or even seize control of devices:
- CVE-2023-39238: iperf-related API module ‘ser_iperf3_svr.cgi’ does not properly verify the input format string.
- CVE-2023-39239: Another format string vulnerability, which resides in the API of the general setting function.
- CVE-2023-39240: The iperf-related API module ‘ser_iperf3_cli.cgi’ also lacks proper input format string verification.
To exploit these vulnerabilities, attackers employ carefully crafted input that is sent to the compromised devices. In the context of ASUS routers, their focus would be on specific administrative API functions within these devices.
How critical are the ASUS vulnerabilities?
The three security vulnerabilities, CVE-2023-39238, CVE-2023-39239, and CVE-2023-39240, all share a critical CVSS score of 9.8. Notably, attackers can exploit these vulnerabilities remotely without the need for authentication.
Which ASUS products and versions are affected by the vulnerabilities?
The security vulnerabilities affect the following ASUS firmware and versions:
- RT-AX55 – 3.0.0.4.386_50460
- RT-AX56U_V2 – 3.0.0.4.386_50460
- RT-AC86U – 3.0.0.4_386_51529
Are there any reports of exploitation related to ASUS vulnerabilities?
Currently, there are no reported instances of exploitation associated with these vulnerabilities. However, it is important to consider that due to their recent identification, the possibility of malicious activities emerging in the near future cannot be dismissed.
Are security patches available for these vulnerabilities?
Firmware updates by ASUS are available to address the critical vulnerabilities. It is advised to update to the following versions or later:
- RT-AX55 – 3.0.0.4.386_51948
- RT-AX56U_V2 – 3.0.0.4.386_51948
- RT-AC86U – 3.0.0.4.386_51915
As another mitigation method, it is highly recommended to deactivate the WAN Web Access feature. This feature allows the configuration of routers over the internet, and disabling it can provide effective protection against unauthorized access.
How can SOCRadar help?
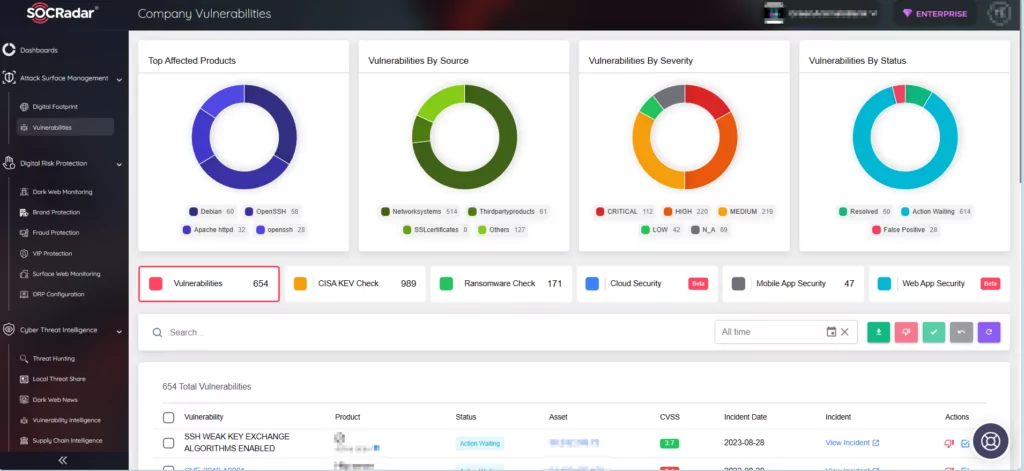
SOCRadar offers you in-depth insights into security vulnerabilities, along with their associated activities and lifecycle data. Our Vulnerability Intelligence module diligently monitors all security vulnerabilities, ensuring you stay informed about emerging hacker trends and empowering you to protect your organization effectively against potential exploitation.
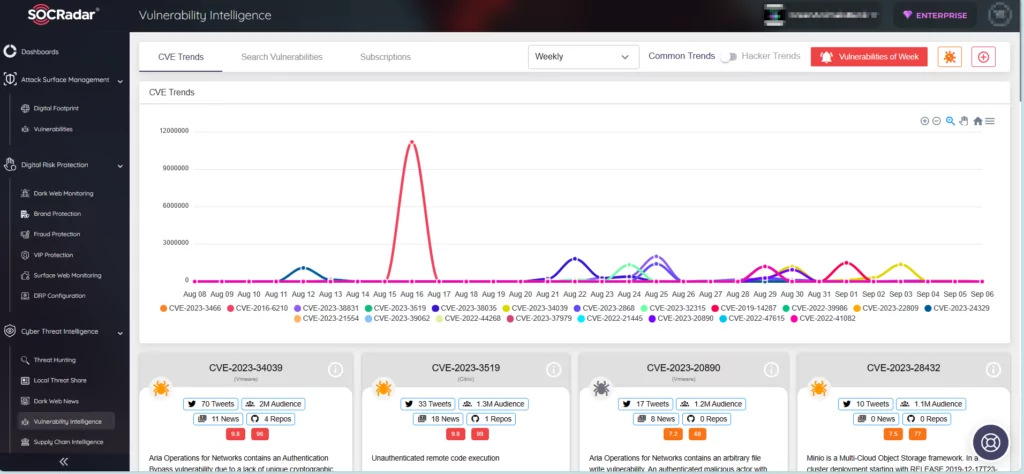
Moreover, through our Attack Surface Management (ASM) module, you can effectively monitor vulnerabilities impacting your digital assets and receive timely alerts regarding any identified issues. SOCRadar’s ASM serves as a reliable partner for your digital footprint, assisting you in determining which vulnerabilities and updates should take precedence in your security efforts.