
AWS Elastic IP Transfer Feature Could Be Exploited in Attacks
Researchers have discovered a new security risk to a recently added feature in Amazon Web Services (AWS).
Elastic IP transfer, an Amazon Virtual Private Cloud feature, is the attack vector. Moving Elastic IP addresses between AWS accounts is much easier with this feature.

How Could It Affect?
A public, static IPv4 address that can be accessed via the internet is known as an elastic IP (EIP) address. The researchers discovered that a threat actor might be able to compromise an IP address by taking advantage of elastic IP transfer. Depending on the level of confidence and reliance others have in the hijacked IP, they can launch various attacks.
These include using the transferred elastic IP address to communicate with network endpoints discovered behind other external firewalls used by the victims if an allow rule is present. Utilizing an Elastic IP address to carry out malicious operations, such as serving as a command and control server for malware campaigns, is another strategy that threat actors might use to evade detection by defense tools.
How Does It Work?
Threat actors need proper credentials and permissions to carry out exploitation. These permissions include some actions in the attached Identity and Access Management, which enables viewing current elastic IPs and their status and IP transfer option.
The Identity and Access Management policy must include ec2:DescribeAddresses on all the IP addresses and ec2:EnableAddressTransfer on the EIPs attacker wants to transfer.
To transfer an already associated EIP, the attacker must have the ec2:DisassociateAddress action on the EIPs and the network interfaces to which the IP addresses are attached.
Is There a Mitigation Available?
You can take the following steps to mitigate the threat:
- Using AWS service control policies, apply the principle of least privilege. This reduces the possibility of a threat actor moving your Elastic IP.
- To obtain CloudTrail logs and generate an automated response, use the EnableAddressTransfer API.
- If you use AWS’s BYOIP (Bring Your Own IP) feature, EIP transfer is not possible. This feature enables users to share IP addresses while maintaining control over them.
- Reverse DNS protections. EIP transfer is not possible if the EIP is associated with a reverse DNS name.
How Can SOCRadar Help?
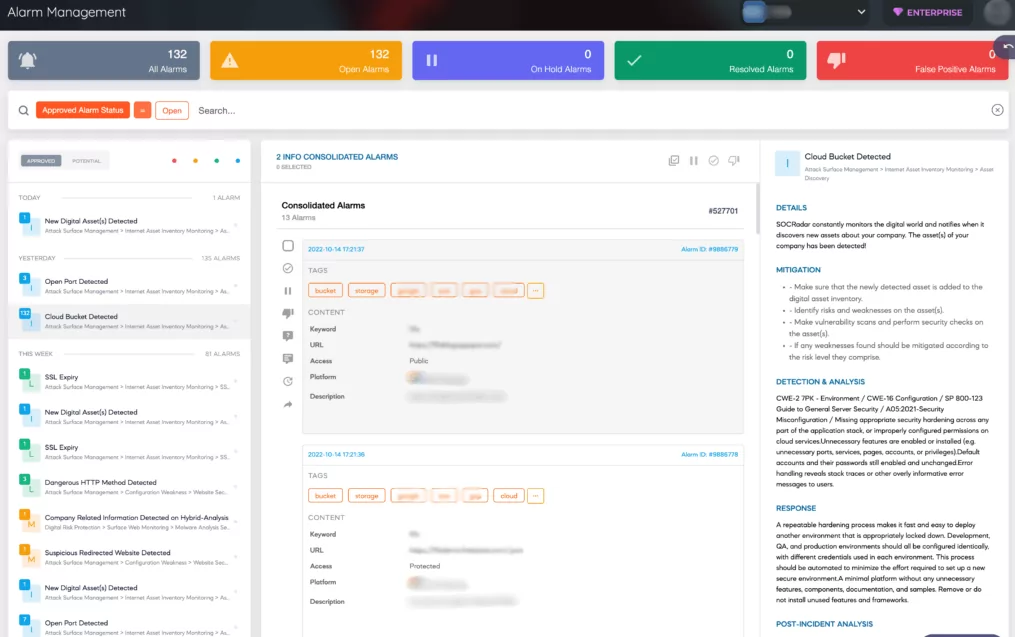
The cloud is the primary storage location for almost all digital assets, including services, databases, IT assets, and apps. This migration, of course, had an unavoidable effect, like increasing the attack surface.
With the addition of the new Cloud Security Module (CSM) designed to ensure the security of its customers’ cloud storages, SOCRadar has increased the scope of its External Attack Surface Management (EASM) services.
You can find cloud buckets using EASM, and a new module that can determine whether a bucket is “public,” “private,” or “protected” allows buckets to be defined as assets. When SOCRadar locates new cloud storage owned by users, it adds it to digital assets and issues a “Cloud Bucket Detected” alert.
Organizations continue to rely heavily on IP addresses for user authentication and identity verification despite a growing awareness of the risks associated with IP address-based security.
Also, through sophisticated internet-wide monitoring algorithms, our external attack surface management solution gives security teams immediate access to all currently in use internet-facing technological assets as well as assets attributed to IP, DNS, Domain, and cryptographic infrastructure.



































