
Best Threat Detection and Response (TDR) Practices
The ability to detect and respond to threats swiftly is more critical than ever. Organizations must adopt a robust Threat Detection and Response (TDR) strategy to safeguard their assets and ensure operational continuity, but how?
SOCRadar offers a range of specialized modules like Cyber Threat Intelligence, Attack Surface Management, Brand Protection , and Supply Chain Intelligence that enhance TDR practices, providing the tools needed to stay ahead of cyber adversaries. This article will guide you through the best practices for TDR and how these modules can be integrated to fortify your defenses.
Understanding Threat Detection and Response (TDR)
Threat Detection and Response (TDR) is a cornerstone of modern cybersecurity, playing a crucial role in protecting organizations from a wide array of cyber threats. TDR encompasses the continuous monitoring, identification, and mitigation of potential security threats within an organization’s network and systems. By leveraging advanced tools, such as artificial intelligence, machine learning, and real-time analytics, TDR solutions provide security teams with the ability to detect threats at their earliest stages.
TDR goes beyond traditional security measures by focusing not only on preventing breaches but also on understanding and responding to threats that have already bypassed initial defenses. This proactive approach ensures that security teams can swiftly respond to incidents, minimizing the impact on the organization. TDR involves a combination of automated threat detection, which identifies suspicious activities and anomalies, and manual intervention, where security experts analyze and respond to threats.
One of the key benefits of TDR is its ability to provide comprehensive visibility into an organization’s security posture. By continuously monitoring all endpoints, networks, and cloud environments, TDR solutions ensure that no threat goes unnoticed. This level of visibility is essential for detecting sophisticated attacks, such as Advanced Persistent Threats (APTs), that can evade traditional security measures.
In addition, TDR integrates threat intelligence to enhance its detection capabilities. By analyzing data from global threat databases, TDR solutions can identify emerging threats and adapt to new attack vectors. This intelligence-driven approach allows organizations to stay ahead of cybercriminals and respond to threats before they cause significant harm.
Ultimately, TDR is not just about detecting and responding to threats—it’s about creating a resilient security environment where threats are anticipated, and responses are swift and effective.
SOCRadar’s suite of cybersecurity modules is designed to enhance TDR by offering comprehensive insights and proactive measures tailored to your organization’s unique needs. Curious about how these tools can strengthen your security posture? Let’s delve into how each module plays a critical role.
For further information and use cases you may also check out our blog post “What are the Different Methods of Threat Detection?”.
Best Practices for Threat Detection and Response with SOCRadar Modules
1. Continuous Monitoring with Attack Surface Management
Continuous monitoring is fundamental to effective Threat Detection and Response (TDR), enabling the early identification of potential threats. SOCRadar’s Attack Surface Management module provides real-time visibility into your digital assets, including networks, applications, and cloud environments. This comprehensive view allows you to detect vulnerabilities and exposures across your entire attack surface, proactively addressing risks before they can be exploited. By continuously mapping and monitoring your assets, you can ensure that no weak point goes unnoticed, creating a resilient security posture.
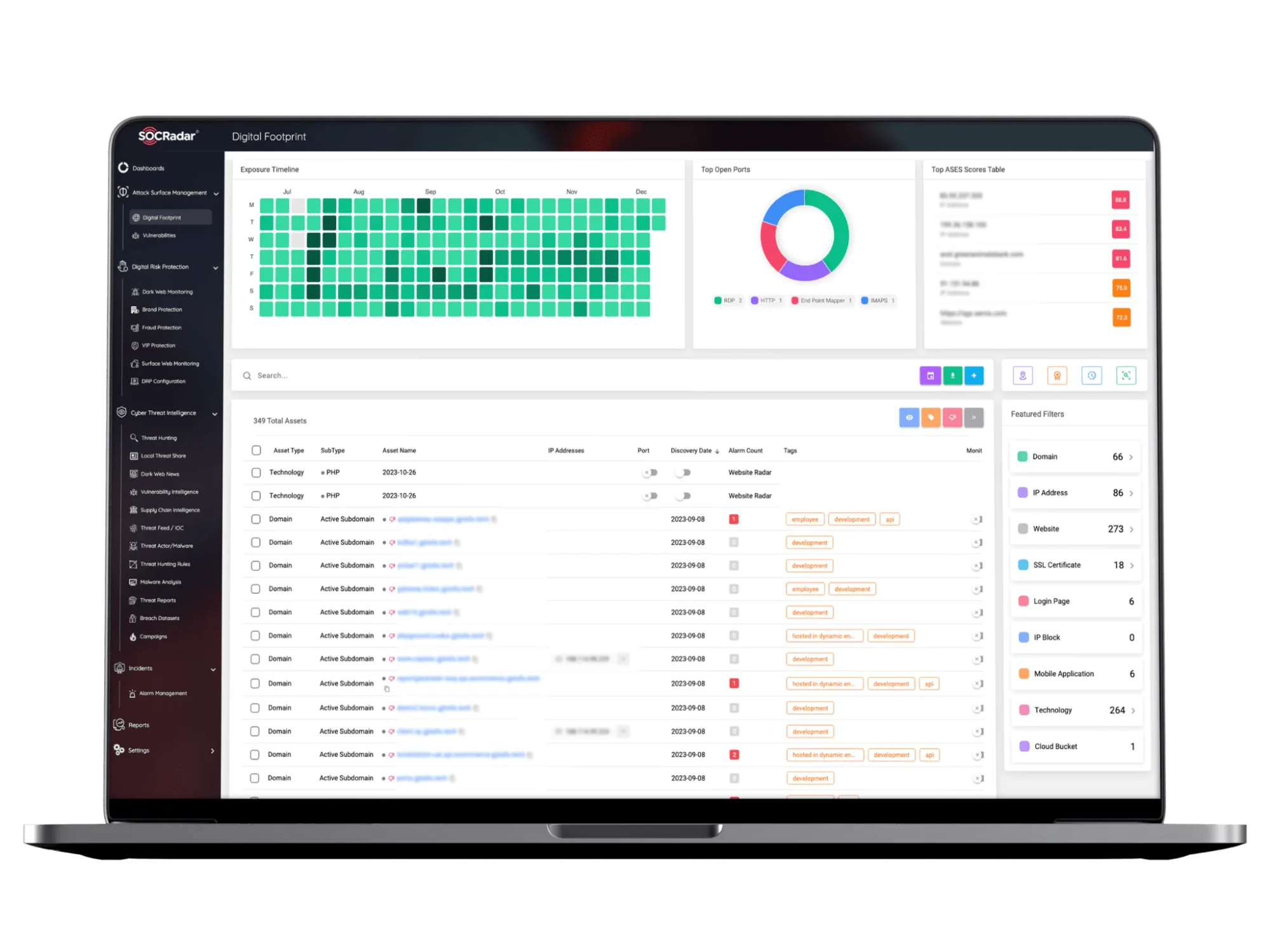
SOCRadar’s Attack Surface Management
2. Informed Decision-Making with Cyber Threat Intelligence
High-quality intelligence is the cornerstone of any successful TDR strategy. SOCRadar’s Cyber Threat Intelligence (CTI) module delivers real-time insights on emerging threats, adversary tactics, and potential attack vectors, allowing you to prioritize threats and make data-driven decisions. Integrating CTI into your TDR processes ensures that your team is always equipped with the latest intelligence, enabling them to respond swiftly and effectively to any threat. By leveraging this intelligence, you can anticipate attacks and enhance your overall threat detection capabilities.
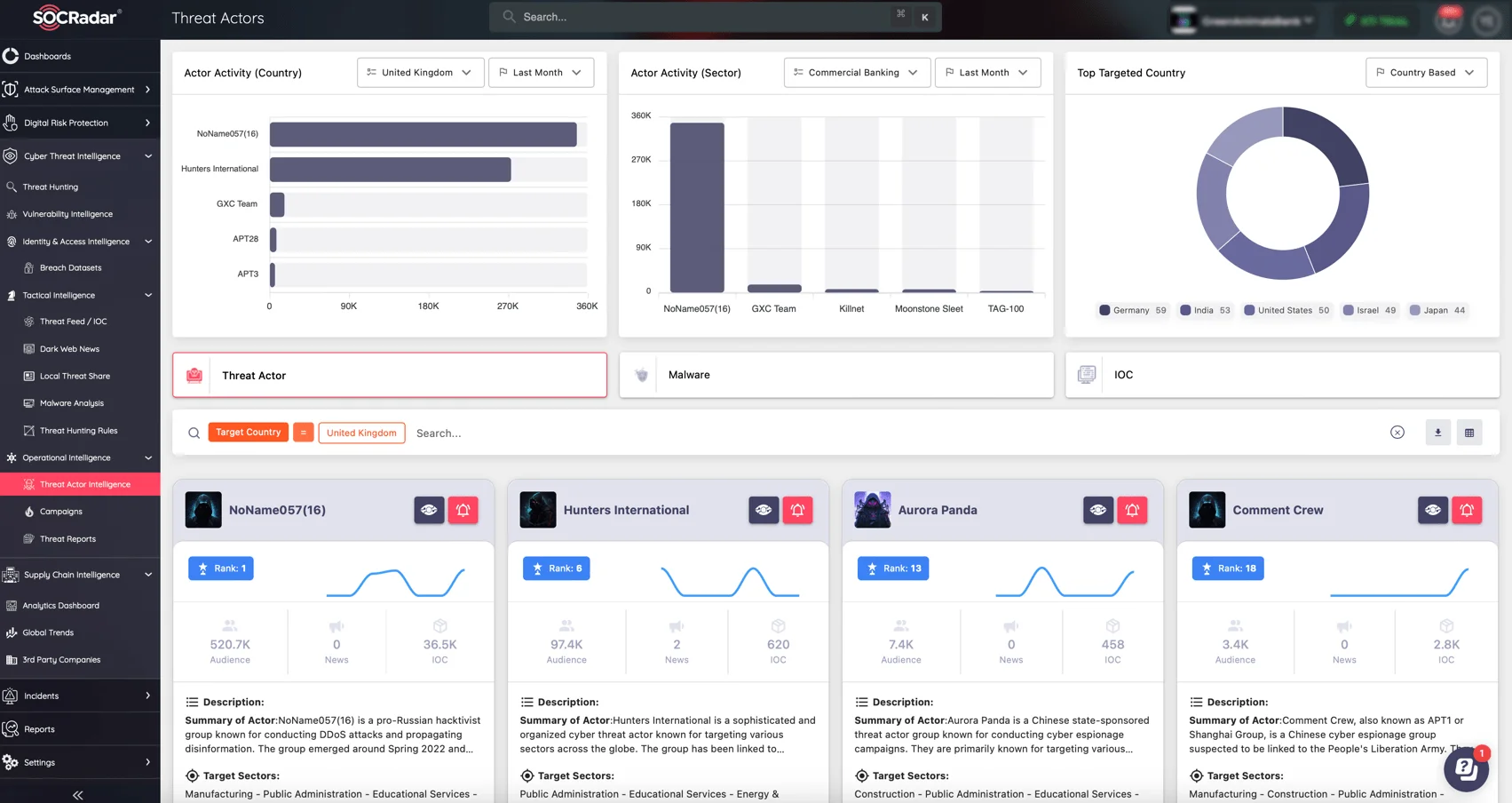
SOCRadar’s Threat Actor Intelligence module
3. Safeguarding Reputation with Brand Protection
Your brand’s reputation is just as critical as your technical defenses. SOCRadar’s Brand Protection module continuously monitors the internet, dark web, and social media for any unauthorized use of your brand, phishing attempts, and other malicious activities that could damage your reputation. By proactively identifying and mitigating these threats, you can protect your brand from being exploited by cybercriminals. This module not only secures your reputation but also builds trust with your customers and stakeholders.
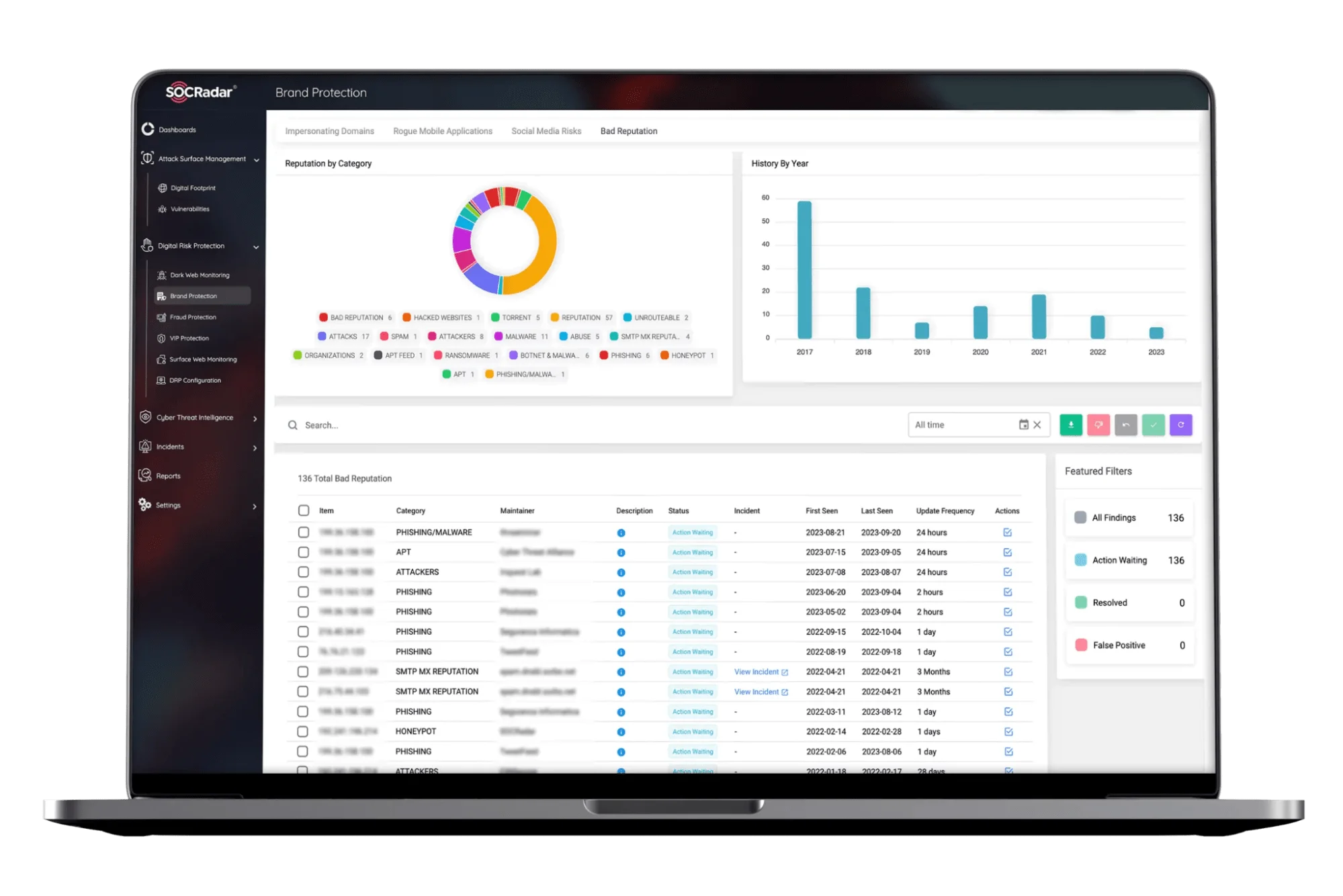
SOCRadar’s Brand Protection
4. Securing Third-Party Risks with Supply Chain Intelligence
As cyber threats increasingly target supply chains, it’s vital to secure your extended network. SOCRadar’s Supply Chain Intelligence module offers deep insights into the security posture of your suppliers and partners, helping you identify and mitigate risks that could impact your operations. By continuously assessing third-party risks, you can ensure that your supply chain is resilient against potential vulnerabilities, reducing the likelihood of disruptions or breaches originating from external partners.
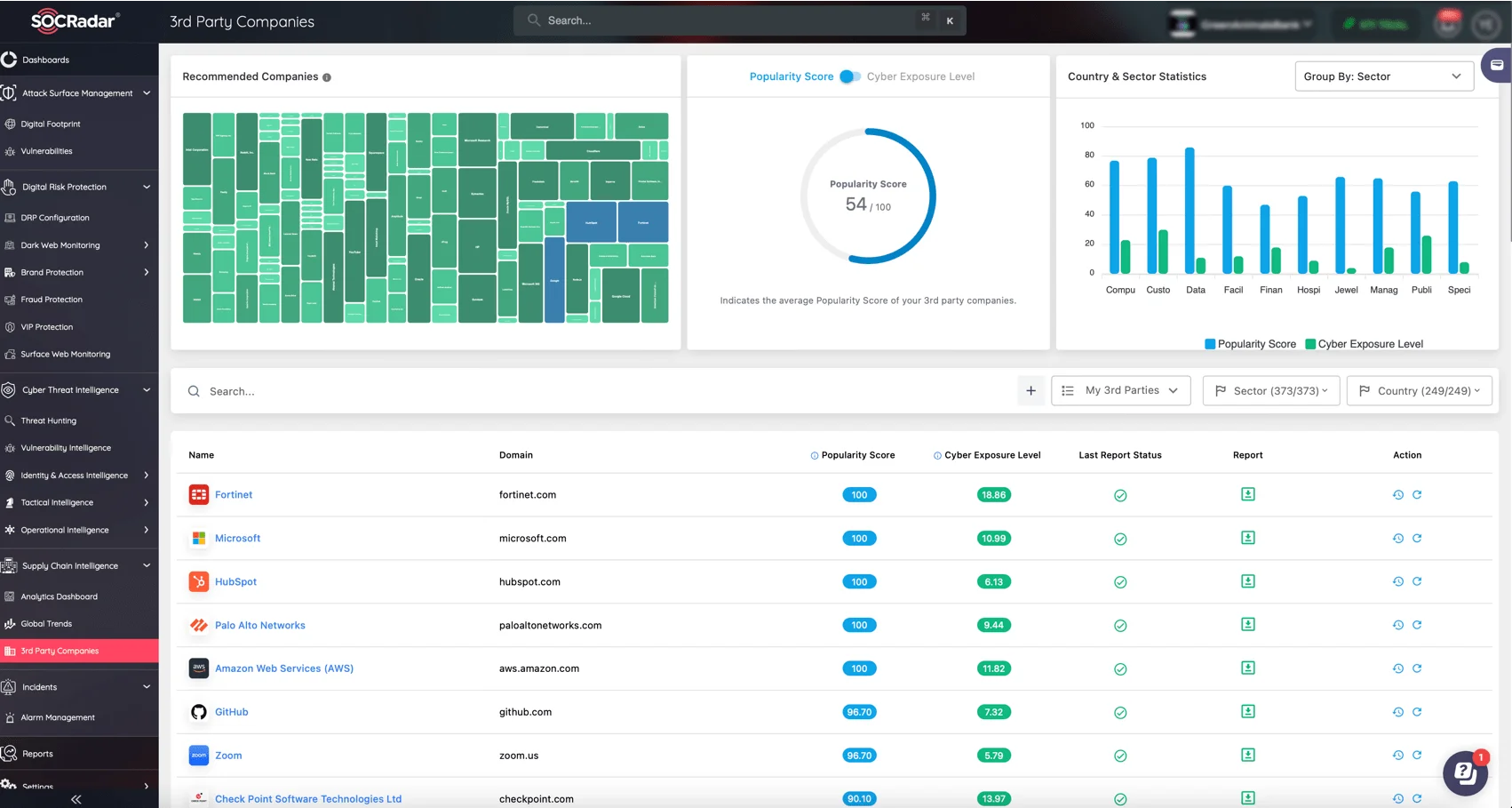
SOCRadar’s Supply Chain Intelligence 3rd Party Companies service
To sum up
As conducted above, SOCRadar’s modules are designed to seamlessly integrate with your existing infrastructure, offering scalable solutions that grow with your organization’s needs. By adopting these best practices and leveraging SOCRadar’s powerful tools, you can stay ahead of emerging threats and ensure the security and continuity of your business. Ready to take your TDR capabilities to the next level? Explore how SOCRadar’s modules can provide the essential tools and insights required to navigate today’s complex threat landscape.
Contact us today to learn more about how our solutions can empower your organization to stay one step ahead of cyber threats.




































