BRATA Malware Becomes an Advanced Threat
Originally a banking trojan, BRATA acquires new capabilities and becomes a more advanced threat. Malware can now be much more effective at stealing user information. Cleafy’s analysis shows BRATA’s activities are almost identical to APT activity patterns.
Threat actors behind BRATA have changed their attack methods, staying longer in victims’ systems. Thus, they aim to access sensitive data.
History of BRATA Malware
BRATA (Brazilian Remote Access Tool, Android) was first detected in January 2019. It was available for download from Google Play Store and some unofficial app stores. Sending victims suspicious links via SMS, email, or WhatsApp is BRATA’s general attack vector.
BRATA was known to exploit CVE-2019-3568, a buffer overflow vulnerability that allows RCE on WhatsApp. Threat actors could also gain access to other apps on the device when they successfully exploited the vulnerability.
The new variant of BRATA appeared in 2021. It directed victims to download malware onto their devices and gained “super admin” privileges during installation. After taking control of the system, it could have abilities such as random file modification and deletion. Another infection vector was to redirect the victim to a phishing page and have them enter their login information. As BRATA developed, it began to choose its victims at the organizational and corporate levels.
Evolution of BRATA
The latest version of the BRATA malware features:
- Phishing techniques can imitate the home page of the target bank.
- New “classes” for getting GPS, location sharing, SMS, and device management permissions.
- Downloading the codes (second stage payload) used to perform the event logging via C2.
How Does It Work?
Credential Harvesting
The new version of BRATA entices its victims by imitating the login screen of the targeted banking app. Cybersecurity researchers found that the login screen of an Italian bank was created for phishing purposes.
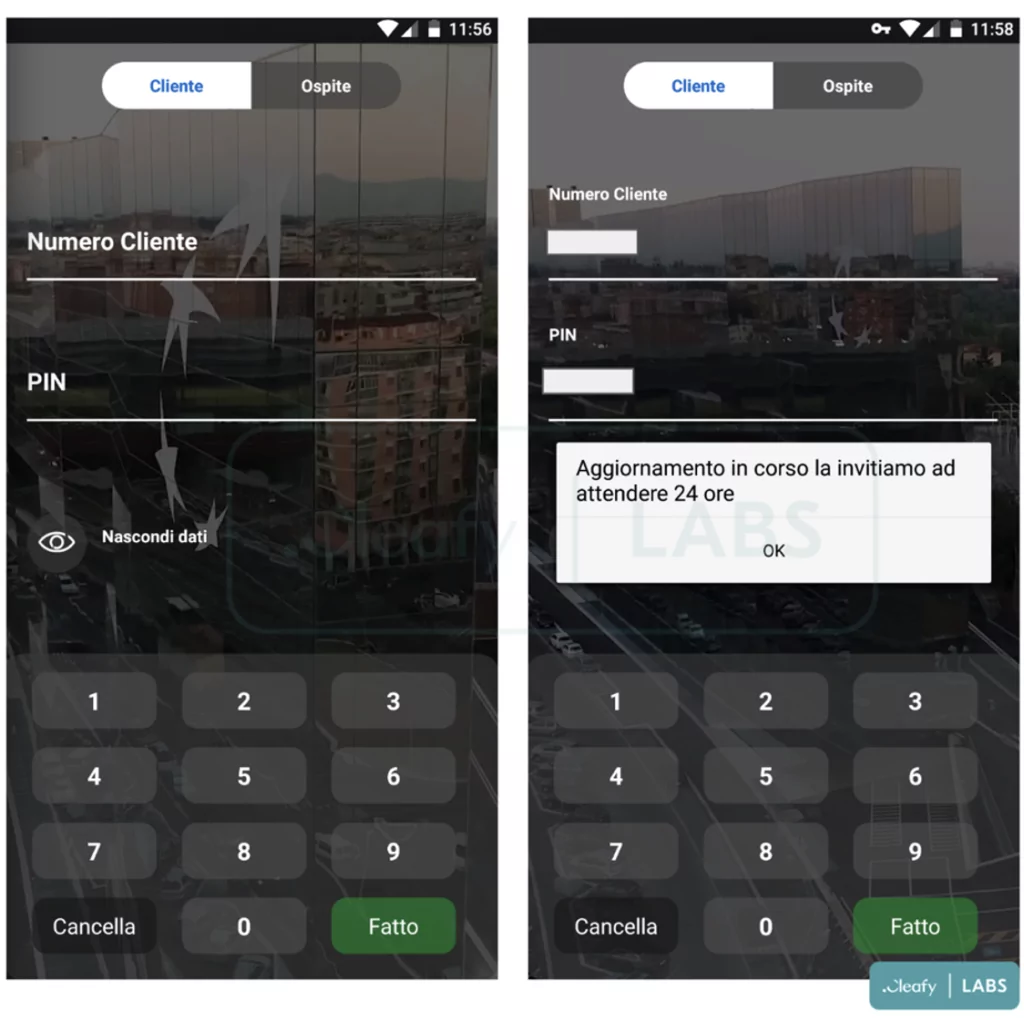
In the new version of BRATA, there are two new features in the AndroidManifest file, “RECEIVE_SMS” and “SEND_SMS.” These features are used with the phishing page to receive and read the victim’s SMS. Thus, the victim’s account can be compromised.
Event Logging
After BRATA is installed on the device, it downloads a [.]zip file named “unrar.jar” from the C2 server. This file is used to monitor events created by applications.
Cybersecurity researchers think BRATA is abusing the Accessibility Service to get data from other applications.
SMS Stealers
Researchers from Cleafy noticed that there was an application connected to the C2 server belonging to BRATA. When they analyzed these applications, they observed that they used the same class names and framework as BRATA. Threat actors aim to develop new types of malware or attacks with this application.
The malicious application detected by the researchers targets the UK, Spain, and Italy. Once installed on the victim’s device, this app can capture all incoming messages and prompts the user to replace the default messaging app with malware.
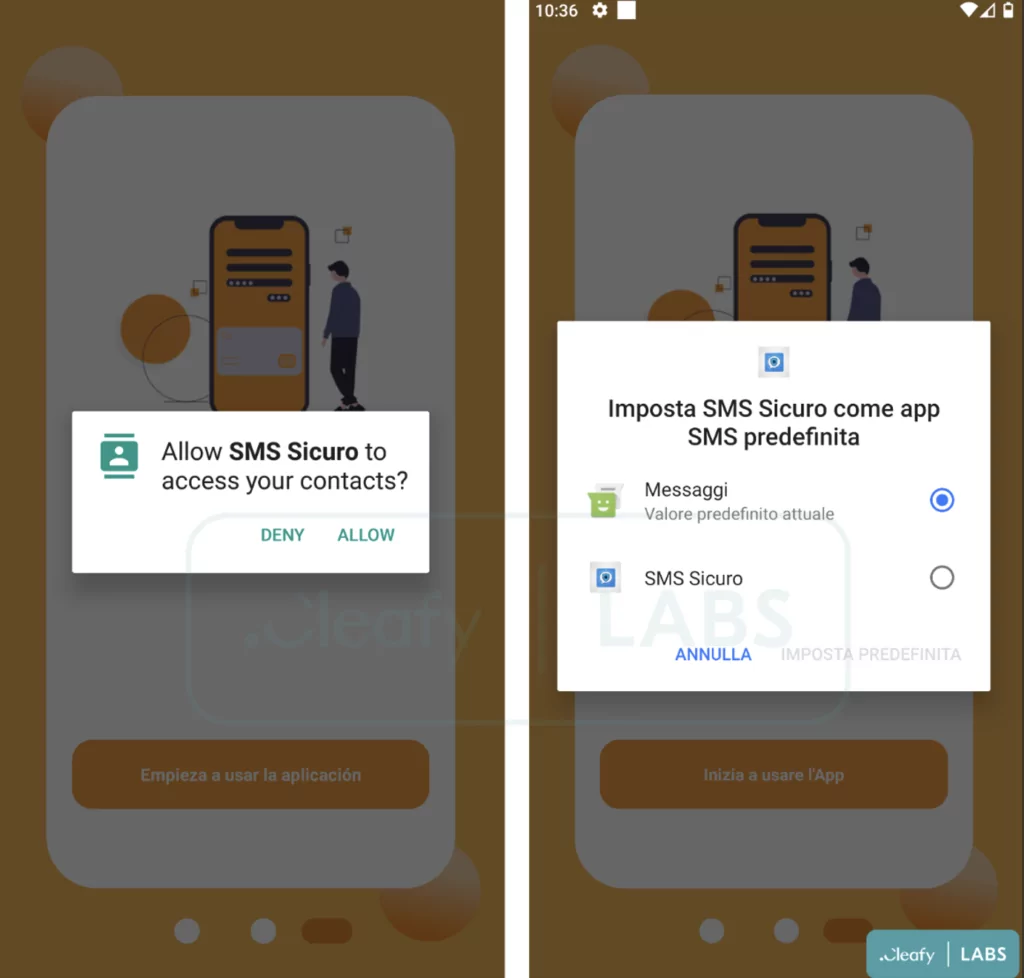
With the malicious application, BRATA uses similar endpoints and the following ports:
- Port 19999: Used to notify the C2 server that the malicious application has been installed on the victim device.
- Port 18888: Used to forward received SMS to C2.
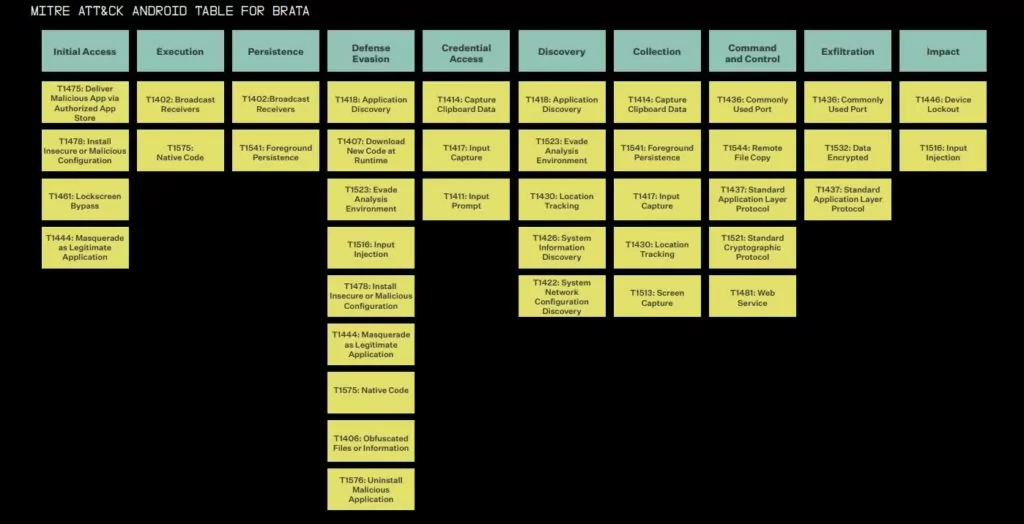
TTPs
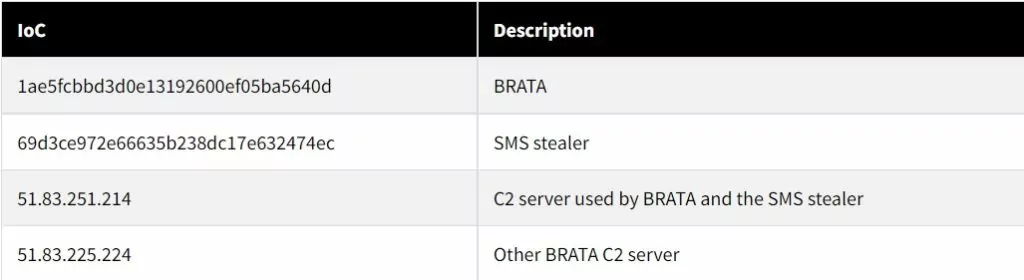
IoCs
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.