Massive Card Leak, New Phishing Tool, and Pharma Scam Attempt Detected
Cybercriminal offerings on dark web forums remained active this week, with SOCRadar’s Dark Web Team uncovering a wide range of threats. The BidenCash marketplace publicly leaked over 910,000 credit card records, significantly raising fraud risks. A new Phishing-as-a-Service platform also emerged, equipped with injection tools and Telegram-linked admin panels. Meanwhile, the alleged breach of Motherhood.com.my exposed sensitive data tied to Malaysian users, and a dark web post revealed recruitment efforts for a Europe-based pharmaceutical fraud operation involving high-value cancer drugs.
Receive a Free Dark Web Report for Your Organization:
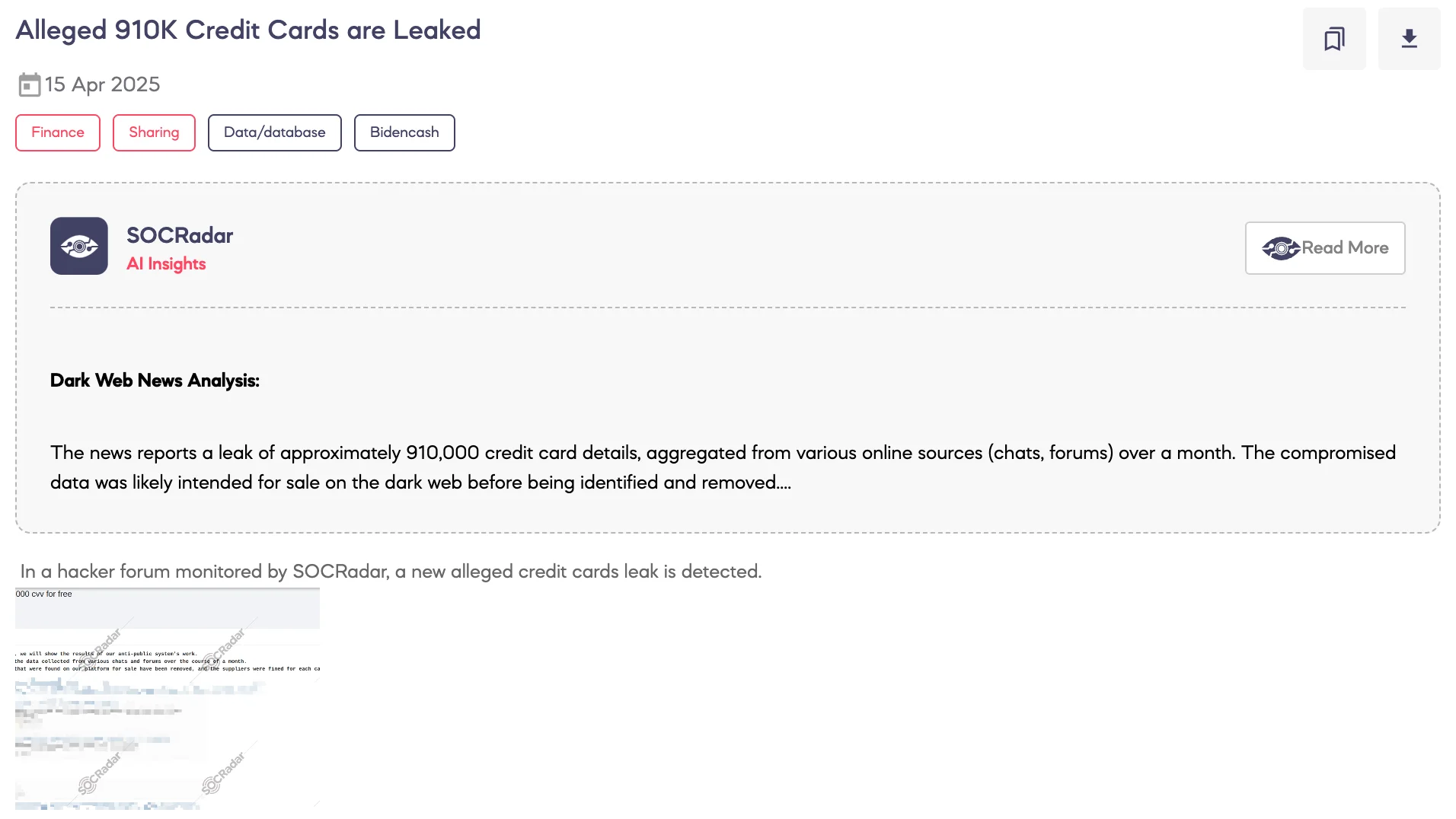
Alleged 910K Credit Cards are Leaked
SOCRadar Dark Web Team has identified a major leak posted on April 15, 2025, by the BidenCash Dark Web Marketplace, involving more than 910,000 credit card records. The dataset was shared openly through clearnet file-hosting platforms, increasing its accessibility and potential for abuse.
The leaked records include card numbers, expiration dates, and CVV codes, making the data highly actionable for cybercriminals engaged in carding and financial fraud.
The announcement appeared on XSS, a prominent Russian-speaking hacker forum where BidenCash routinely promotes its campaigns. The release was positioned as part of the marketplace’s so-called Anti-Public System—a mechanism claimed to ensure that only exclusive and non-public data is circulated. According to the platform’s operators, the dataset was compiled from underground chats and forums over the past month.
For a deeper breakdown of the incident, see our full analysis: BidenCash Dark Web Market Leaks Nearly One Million Credit Cards
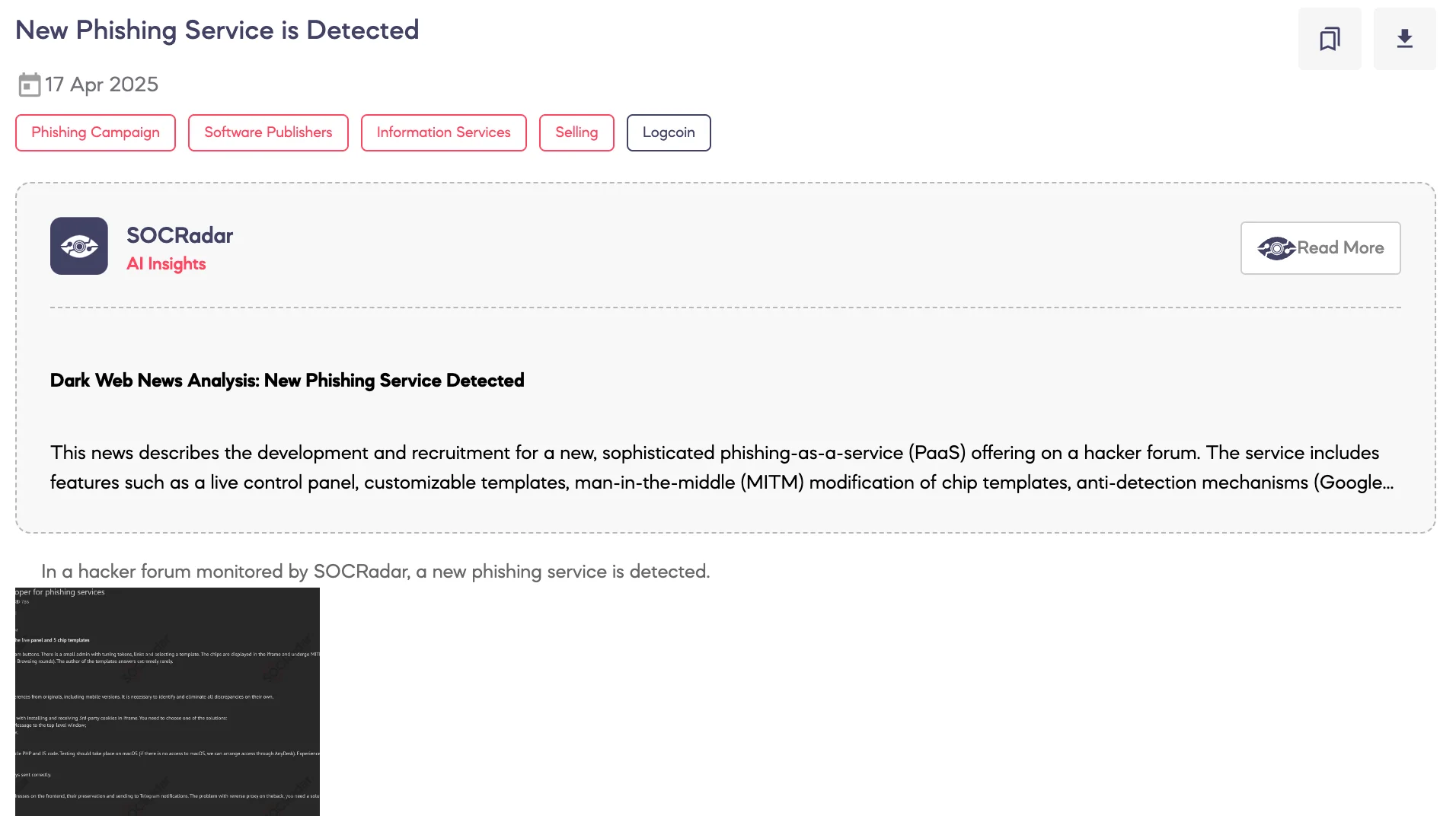
New Phishing Service is Detected
SOCRadar Dark Web Team has identified a Phishing-as-a-Service offering on a dark web forum, featuring man-in-the-middle injection, iframe-based templates, Telegram integration, and a custom admin panel.
The service includes tools for cookie handling in Safari, form debugging, IP logging, and automated domain failover. The threat actor seeks developers familiar with PHP, JS, and Telegram API. Payment is offered via cryptocurrency.
The setup reflects a growing trend of modular, evasive phishing platforms with full infrastructure control. Such offerings lower the technical barrier for aspiring cybercriminals and enable more persistent, scalable phishing operations across global targets.
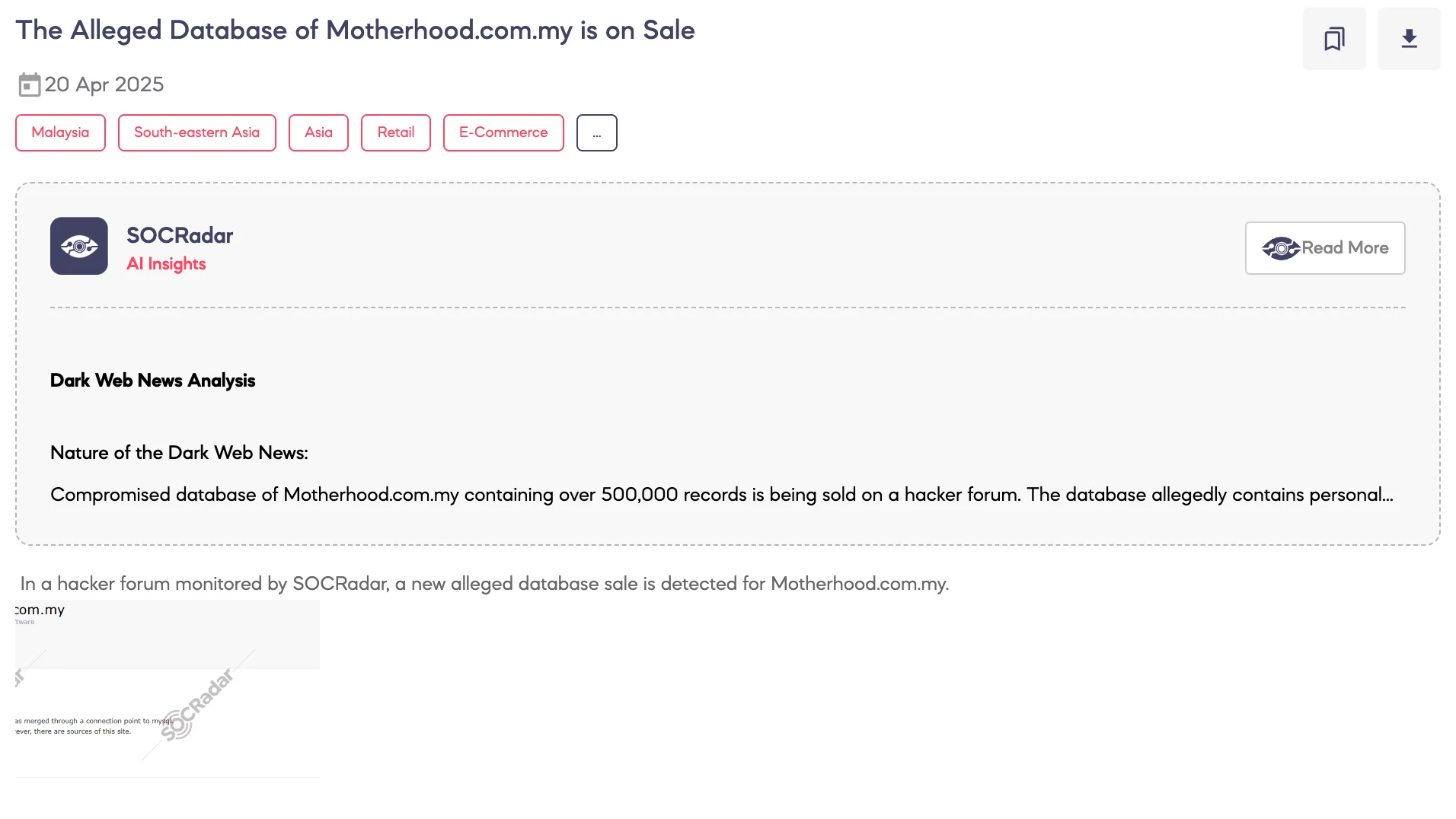
Alleged Database of Motherhood.com.my is on Sale
SOCRadar Dark Web Team has identified a new dark web forum post in which a threat actor claims to be selling a database allegedly stolen from Motherhood.com.my, a Malaysian e-commerce platform that offers products and services for parents and children.
According to the threat actor, the dataset contains over 500,000 personal records of users in Malaysia. The compromised data was reportedly extracted through a MySQL access point and includes sensitive fields such as identification card numbers.
The post also alleges that while the original vulnerabilities have been patched, source files from the site remain exposed. The threat actor stated that the company declined to pay to secure or recover the data. The asking price for the full database is $5,500.
If authentic, the dataset could expose Malaysian users to significant privacy risks, including identity theft and targeted fraud.
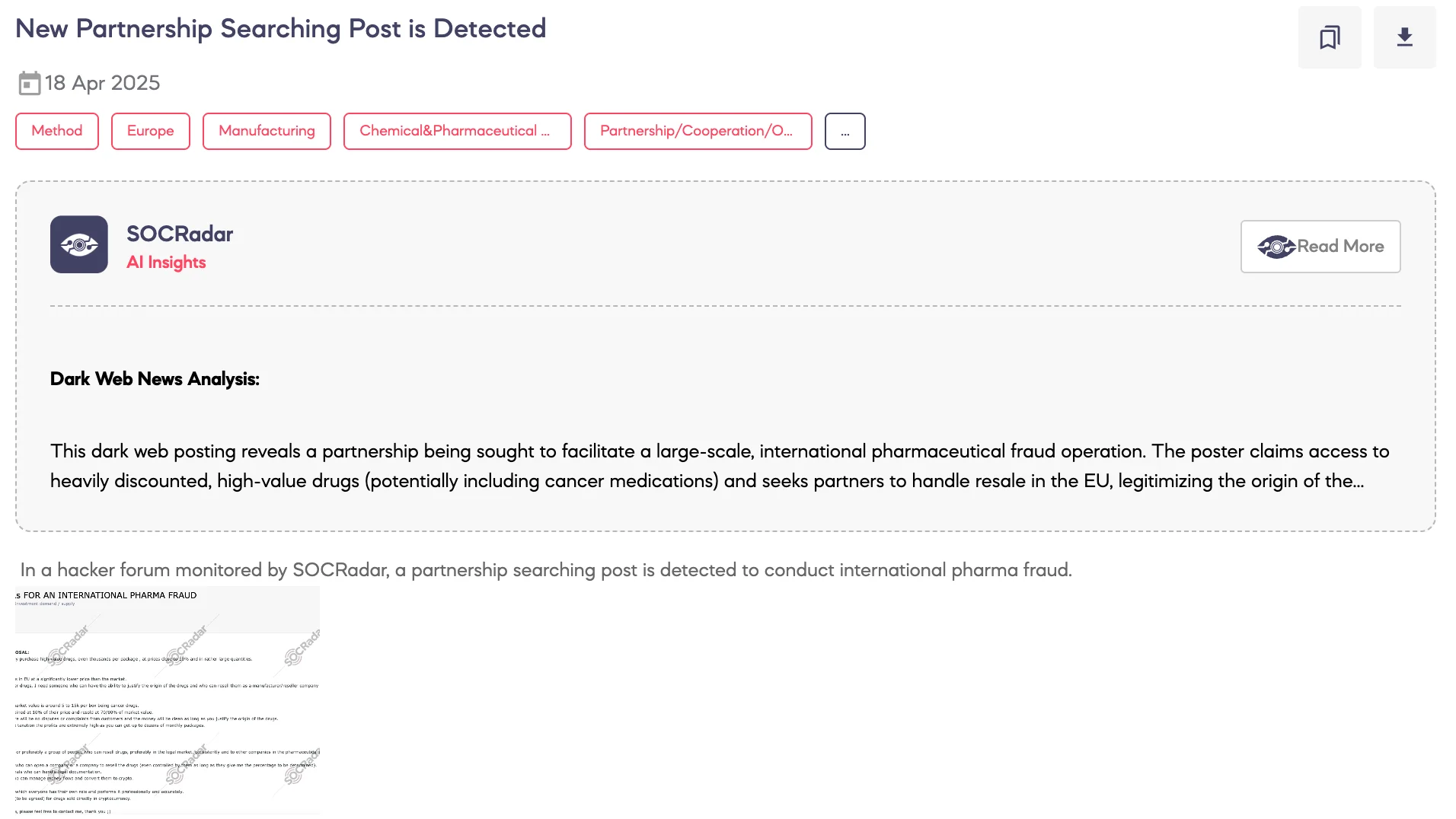
New Partnership Searching Post is Detected
SOCRadar Dark Web Team has identified a post in which a threat actor solicits partners for a pharmaceutical fraud operation targeting the European market. The actor claims access to large volumes of original high-value cancer drugs acquired at 10% of market price, with the aim of reselling them at up to 80% through front companies.
Roles sought include resellers, investors, legal experts, and money handlers to form a structured group. The scheme promises high profits while attempting to appear low-risk due to the use of authentic products.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.