
CHAVECLOAK: A Complex Cyber Threat to Brazil’s Financial Security
The Brazilian financial sector is facing a formidable cyber threat known as CHAVECLOAK, a banking trojan that has emerged as a significant menace. This sophisticated malware is designed to breach security measures and extract sensitive financial information from potential victims.

An AI illustration of the CHAVECLOAK campaign
The CHAVECLOAK banking trojan primarily affects Microsoft Windows platforms and targets it’s users, especially those residing in Brazil. It enables unauthorized control over the victim’s device and is designed to extract sensitive financial information. Given its capabilities and target demographic, the severity level of this threat is classified as high.
You can visit the CHAVECLOAK campaign page on SOCRadar
How Does CHAVECLOAK Initiate Its Attacks?
The trojan begins its infiltration by using a deceptive PDF file containing a hidden downloader link.
The PDF file used by CHAVECLOAK is designed to appear as if it contains contract-related documents with instructions in Portuguese, enticing victims to click a button to access and sign the documents.
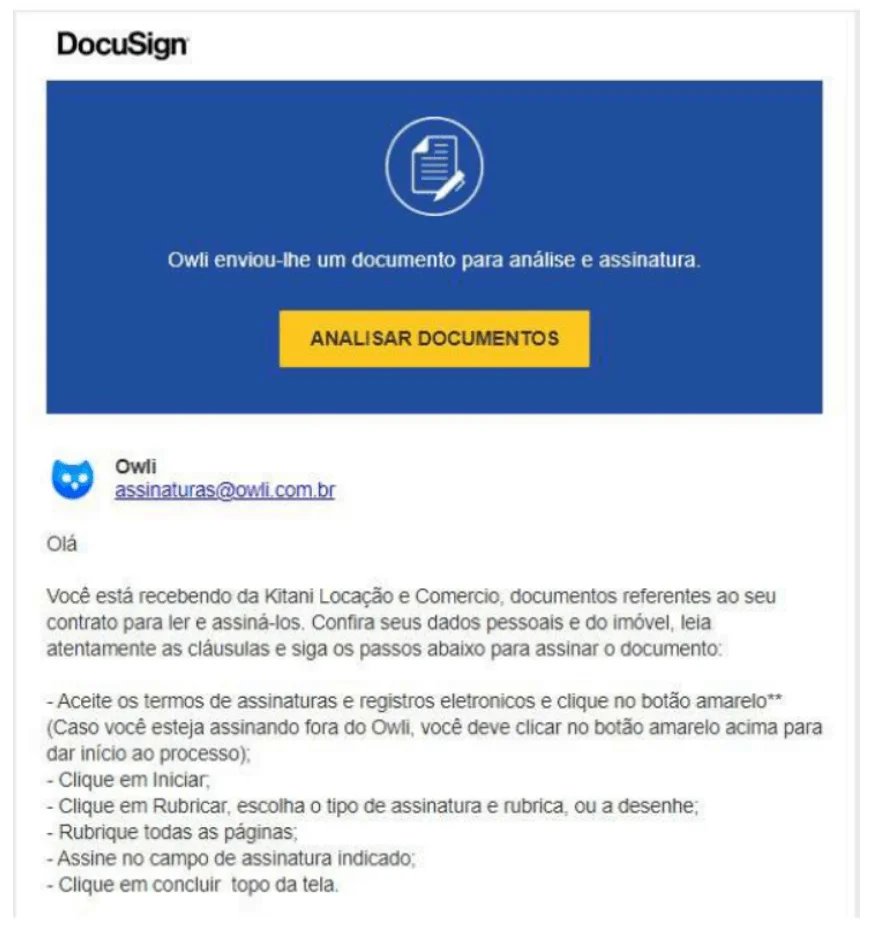
The malicious PDF file (Fortinet)
When the link is activated, it triggers the download of a ZIP file containing the trojan’s payload. The payload is then executed using DLL side-loading techniques, enabling the malware to integrate into the system without detection.
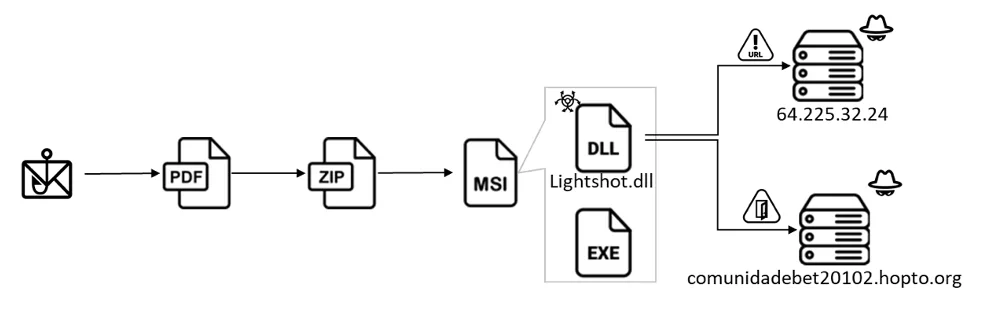
The detailed infection flow (Fortinet)
The attack unfolds in multiple stages, showcasing the trojan’s complexity. It starts by collecting information about the file system and establishing persistence within the system through registry modifications. This ensures that the trojan activates with each user login, maintaining a constant presence on the infected device.
The trojan’s geo-targeting feature confirms the victim’s location within Brazil before proceeding, indicating a campaign specifically tailored to the Brazilian financial sector.
CHAVECLOAK operates under the radar, continually monitoring the windows active on the system for banking-related activities. It employs APIs to detect when a user accesses a financial platform, then springs into action, establishing communication with its Command and Control (C2) server.
The trojan’s capabilities are extensive, allowing it to block the victim’s screen, log keystrokes, and display deceptive pop-up windows designed to harvest credentials. The trojan targets not only traditional banking platforms but also extends its reach to cryptocurrency exchanges, reflecting its adaptability to the evolving financial landscape.
Credential Harvesting and Persistence Mechanisms of CHAVECLOAK
In detail, the hidden link in the deceptive PDF file directs to a shortened URL via “Goo.su.” This shortened link then redirects users to a site for downloading a ZIP file. Unpacking this ZIP file reveals an MSI file named “NotafiscalGFGJKHKHGUURTURTF345.msi,” which triggers the next phase.
Upon decompressing the MSI installer, various TXT files, a legitimate executable, and the suspicious DLL “Lightshot.dll” emerge. The MSI installer, primarily configured in Portuguese, launches the “Lightshot.exe” file, extracting files to the directory “%AppData%Skillbrainslightshot5.5.0.7.”
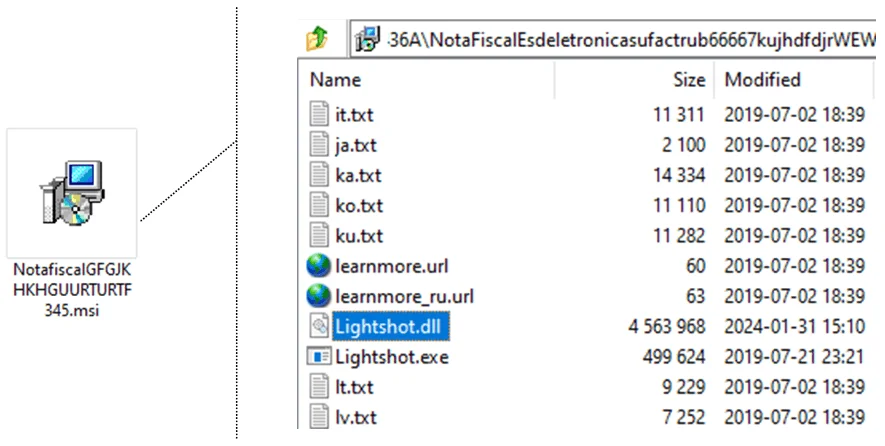
Contents of the MSI Installer (Fortinet)
Lightshot.dll commences operation by obtaining file system specifics and creating a log file, establishing persistence through a registry entry. Subsequently, an HTTP request is dispatched to hxxp://64[.]225[.]32[.]24/shn/inspecionando.php, recording data if the victim is in Brazil.
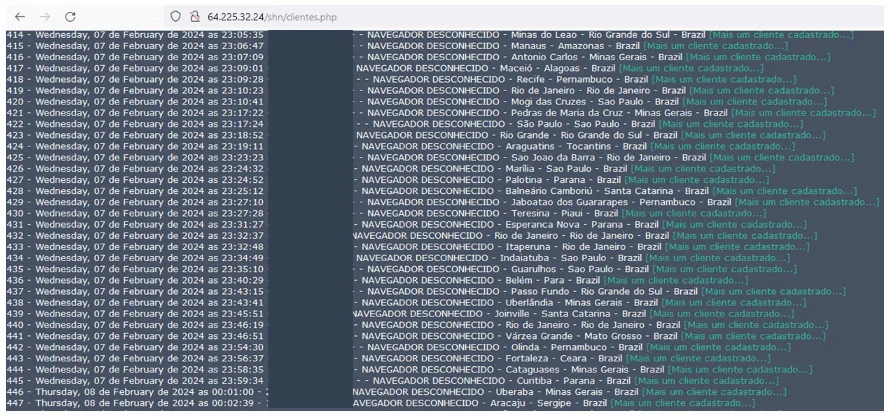
The check-in victim list (Fortinet)
Regular window checks through “GetForegroundWindow” and “GetWindowTextW” APIs enable the trojan to intercept bank-related activities, harvesting credentials by freezing screens, capturing keystrokes, and presenting misleading pop-ups. It meticulously monitors interactions with financial websites, targeting both traditional banks and cryptocurrency exchanges such as Mercado Bitcoin.
Once the malware captures the login information entered by the user, it establishes a connection with its C2 server located at hxxp://comunidadebet20102[.]hopto[.]org.
Based on which bank’s data has been compromised, the stolen information is then uploaded to specific directories, such as “04/M/” for transactions related to Mercado Bitcoin.
Evolution of the Threat
An older variant of CHAVECLOAK provides a glimpse into the trojan’s development. This variant differs in its delivery mechanism, using a Delphi executable file to embed the final payload.
This version is distinguishable as being more archaic, with the initial check-in dates of victims tracing back to 2023.
Its procedure initiates by collecting system specifics to create a novel directory, storing the payload at “C:Program Files (x86)Editor-GH-[HEX ID]Editor-[HEX ID].exe.” In tandem, it generates a log file, secures its persistence in the system, and applies a PowerShell command to remove the payload path from being scanned by Windows Defender.
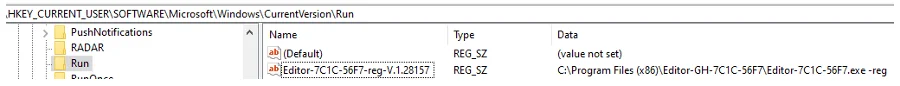
Payload directory
Following these steps, it proceeds to make a check-in communication to hxxp://64[.]225[.]32[.]24/desktop/inspecionando.php.
Furthermore, it diligently monitors user interactions, records the text of active windows, and collects sensitive personal information from targeted banking and Bitcoin login screens, such as user names, passwords, and keystroke data. Following this, it sends the acquired data to its C2 server located at hxxp://mariashow[.]ddns[.]net/dtp/cnx.php.
How to Protect Against Banking Trojans Like CHAVECLOAK?
Protecting yourself from banking trojans like CHAVECLOAK involves a combination of vigilance and proactive security measures. Here are some key steps you can take:
- Be Cautious with Emails and SMS: Avoid clicking on links or downloading attachments from unknown or suspicious sources. Phishing attempts often use these methods to spread trojans.
- Verify Website Legitimacy: Before entering any sensitive information, ensure that the website is legitimate and secure. Look for “https://” in the URL and a padlock symbol in the address bar.
- Enable Two-Factor Authentication (2FA): Use 2FA wherever possible, especially for online banking and other financial services. This adds an extra layer of security beyond just a password.
- Use Strong Passwords: Create complex passwords that are difficult to guess and use a different password for each account. Consider using a password manager to keep track of them.
- Regularly Update Your Systems: Keep your operating system, web browser, and security software up to date to protect against known vulnerabilities.
- Install and Maintain Security Software: Use reputable antivirus and anti-malware software, and ensure it’s set to update automatically and run regular scans.
By following these steps you can significantly reduce the risk of becoming a victim of banking trojans and other types of malware.
Additionally, SOCRadar can assist in protecting against banking trojans like CHAVECLOAK through its comprehensive capabilities. Here’s how:
- Threat Hunting: SOCRadar provides a proactive approach by actively searching for potential threats and vulnerabilities that could impact your organization, helping to identify and mitigate risks before they can be exploited by trojans.
- Dark Web Monitoring: With the ability to monitor the dark web, SOCRadar can alert you to any leaked information or discussions related to banking trojans, ensuring you are aware of threats as they emerge.
- Incident Response: SOCRadar can help improve your incident response procedures by helping you understand the latest trends in threats, enabling you to respond effectively to incidents involving banking trojans.
- Indicator of Compromise (IoCs): SOCRadar can provide IoCs related to the latest banking trojan threats, which can be used to enhance your security systems and prevent potential breaches.
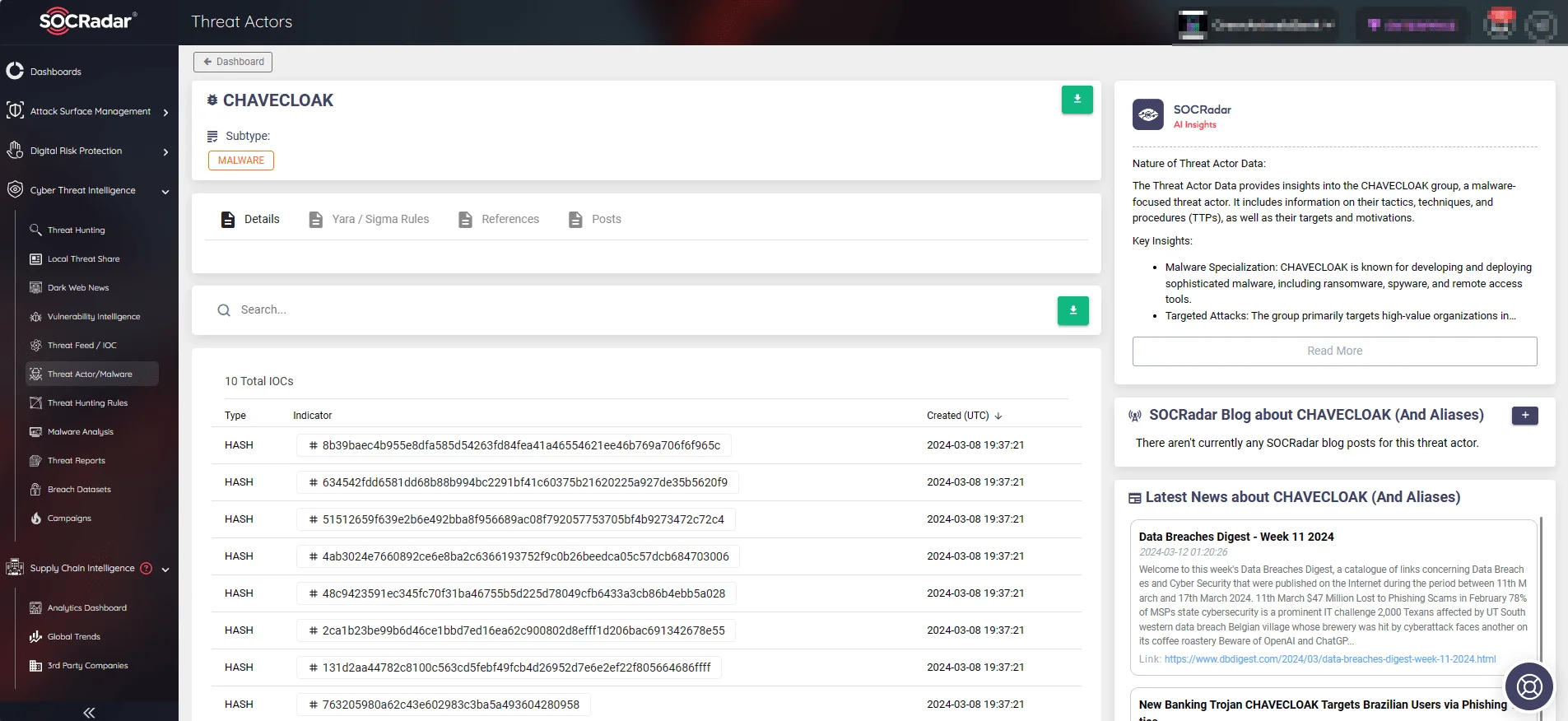
SOCRadar Threat Actors/Malware page, CHAVECLOAK
By utilizing SOCRadar’s services, you can strengthen your cybersecurity posture and better protect your financial information from advanced threats like CHAVECLOAK.




































