
CISA Adds Apache OFBiz, Microsoft .NET, and Paessler PRTG Vulnerabilities to the KEV Catalog
The Cybersecurity and Infrastructure Security Agency (CISA) has recently updated its Known Exploited Vulnerabilities (KEV) Catalog, adding four new vulnerabilities due to evidence of active exploitation. These vulnerabilities affect Apache OFBiz, Microsoft .NET Framework, and Paessler PRTG Network Monitor, posing significant risks to federal enterprises and organizations relying on them.
Newly Added Vulnerabilities
Below are the latest vulnerabilities added to the CISA KEV Catalog as of February 4, 2025:
- CVE-2024-45195 – Apache OFBiz Forced Browsing Vulnerability
- CVE-2024-29059 – Microsoft .NET Framework Information Disclosure Vulnerability
- CVE-2018-9276 – Paessler PRTG Network Monitor OS Command Injection Vulnerability
- CVE-2018-19410 – Paessler PRTG Network Monitor Local File Inclusion Vulnerability
Each of these vulnerabilities presents a significant security risk and has been actively exploited. Below, we break down the details of each vulnerability.
CVE-2024-45195 (CVSS 7.5) – Apache OFBiz Forced Browsing Vulnerability
Apache OFBiz, an open-source enterprise resource planning system, is vulnerable to forced browsing, a security flaw that permits attackers to directly access unauthorized resources by circumventing authentication controls (CVE-2024-45195). This vulnerability could allow malicious actors to retrieve sensitive data or manipulate restricted functionalities within the system.
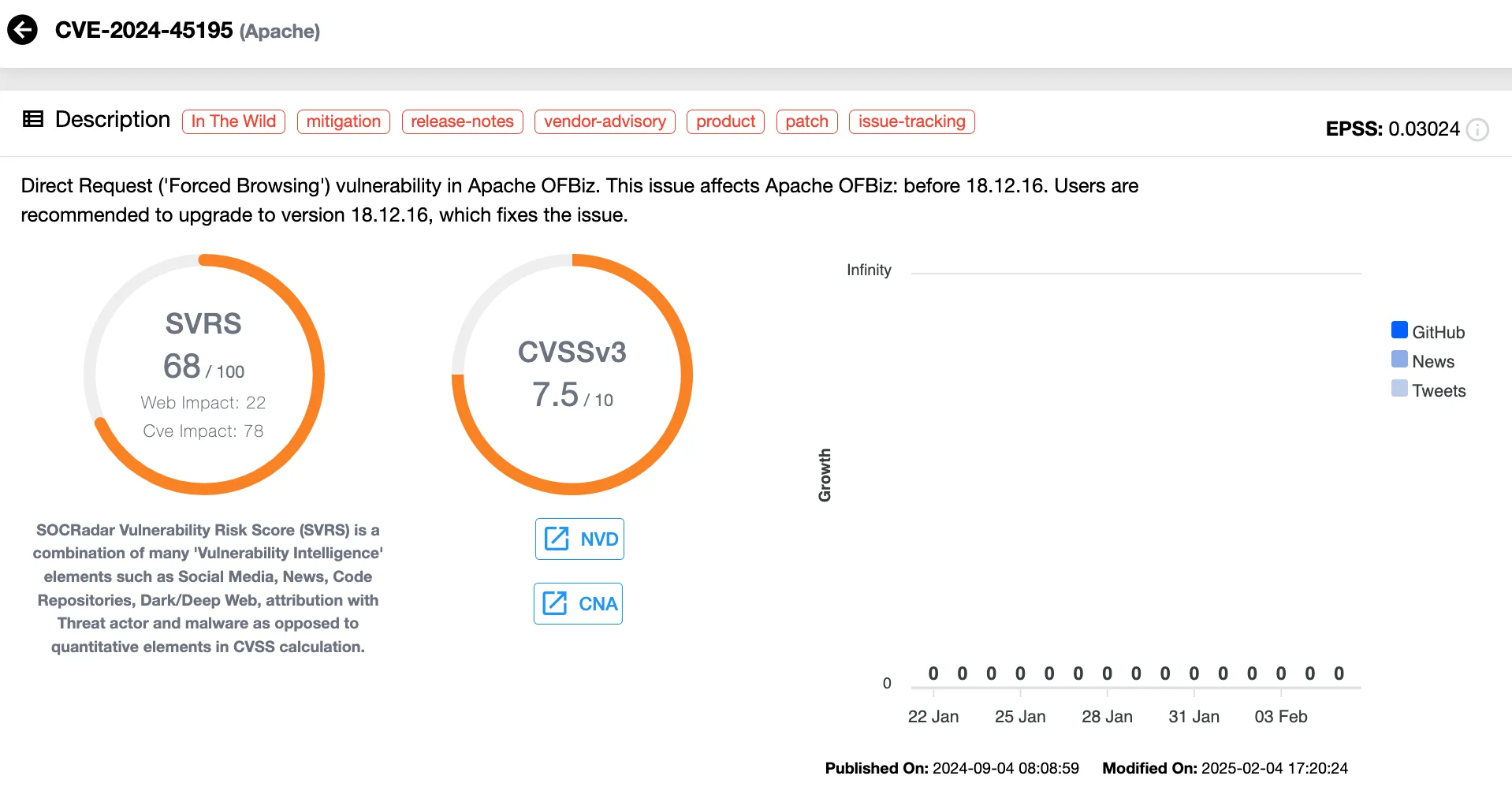
Vulnerability card of CVE-2024-45195 (SOCRadar’s Vulnerability Intelligence)
CVE-2024-29059 (CVSS 7.5) – Microsoft .NET Framework Information Disclosure Vulnerability
This vulnerability affects the Microsoft .NET Framework, where improper handling of ObjRef URIs exposes sensitive information. An attacker could leverage this flaw to obtain privileged information, which may ultimately lead to Remote Code Execution (RCE) under certain conditions.
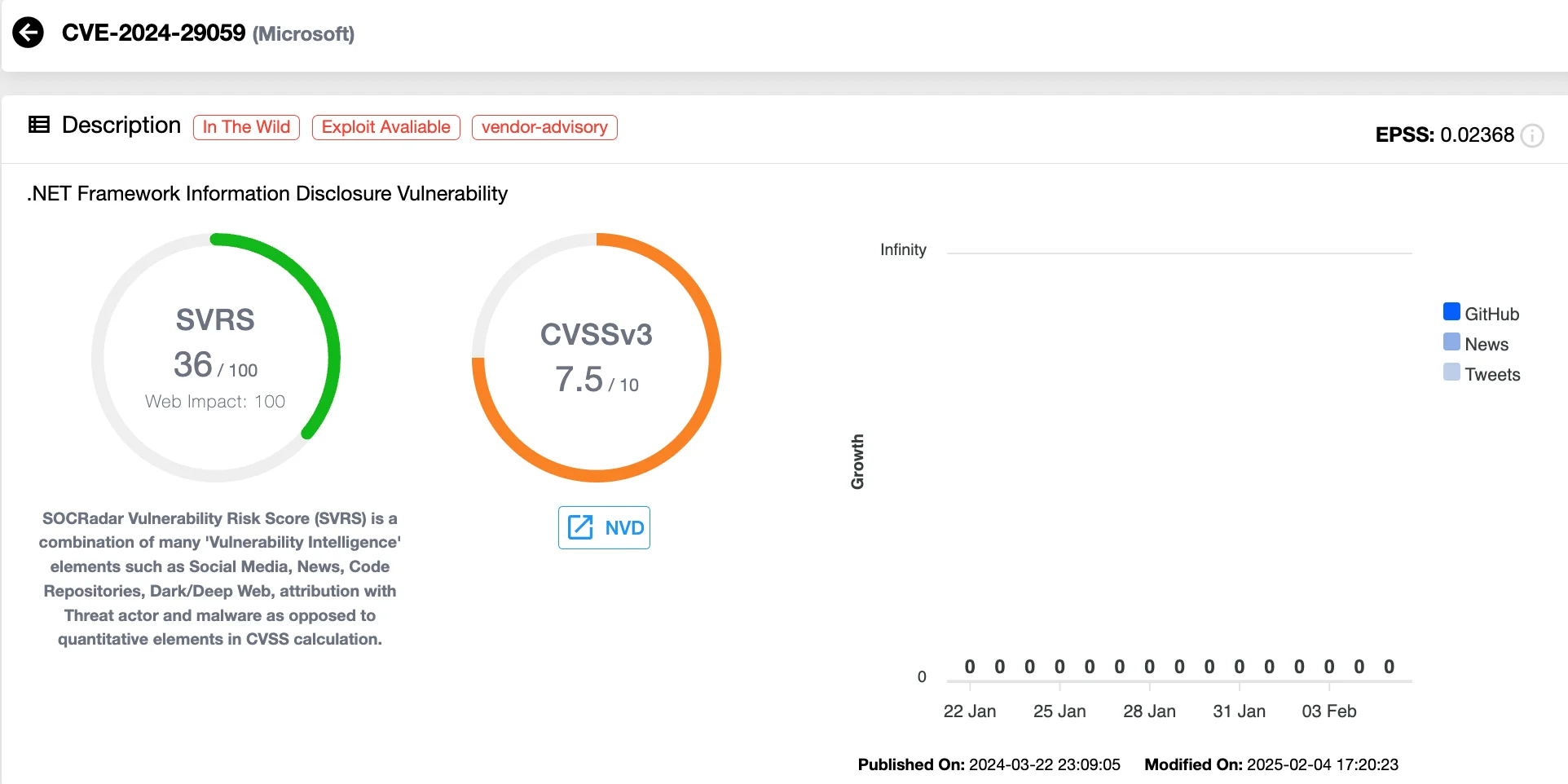
Vulnerability card of CVE-2024-29059 (SOCRadar’s Vulnerability Intelligence)
CVE-2018-9276 (CVSS 7.2) – Paessler PRTG Network Monitor OS Command Injection Vulnerability
Paessler PRTG Network Monitor, a network monitoring software, contains an OS command injection vulnerability. This flaw allows an attacker with administrative access to inject and execute arbitrary system commands through the PRTG System Administrator web console.
Exploitation of this vulnerability could lead to system compromise, potentially allowing attackers to manipulate network infrastructure and exfiltrate sensitive data.
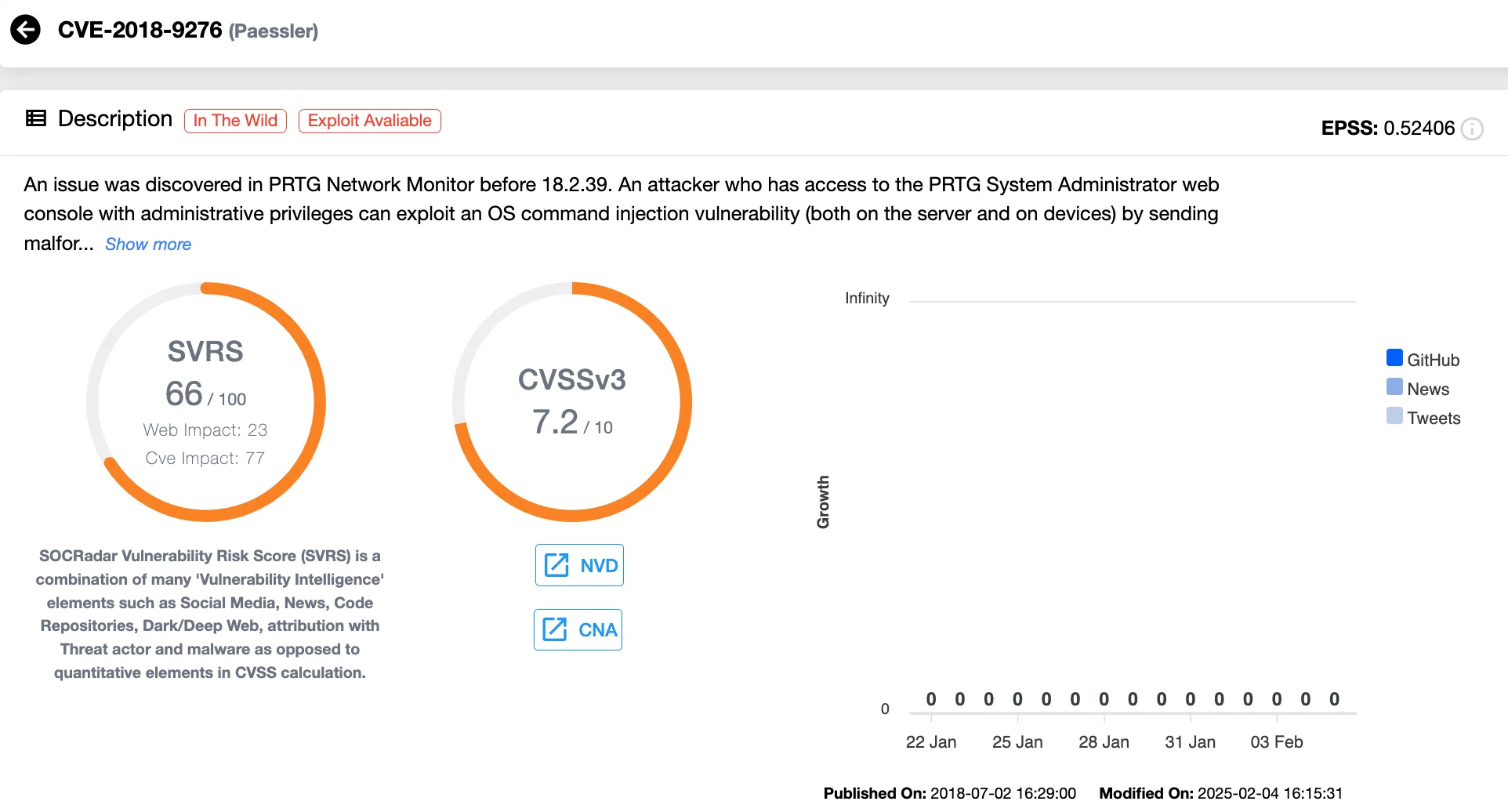
Vulnerability card of CVE-2018-9276 (SOCRadar’s Vulnerability Intelligence)
CVE-2018-19410 (CVSS 9.8) – Paessler PRTG Network Monitor Local File Inclusion Vulnerability
An additional vulnerability in Paessler PRTG Network Monitor enables remote, unauthenticated attackers to take advantage of Local File Inclusion (LFI) vulnerabilities. If exploitation of this critical-severity flaw is successful, an attacker may be able to create users with read-write rights, including administrative access, which would compromise the entire system.
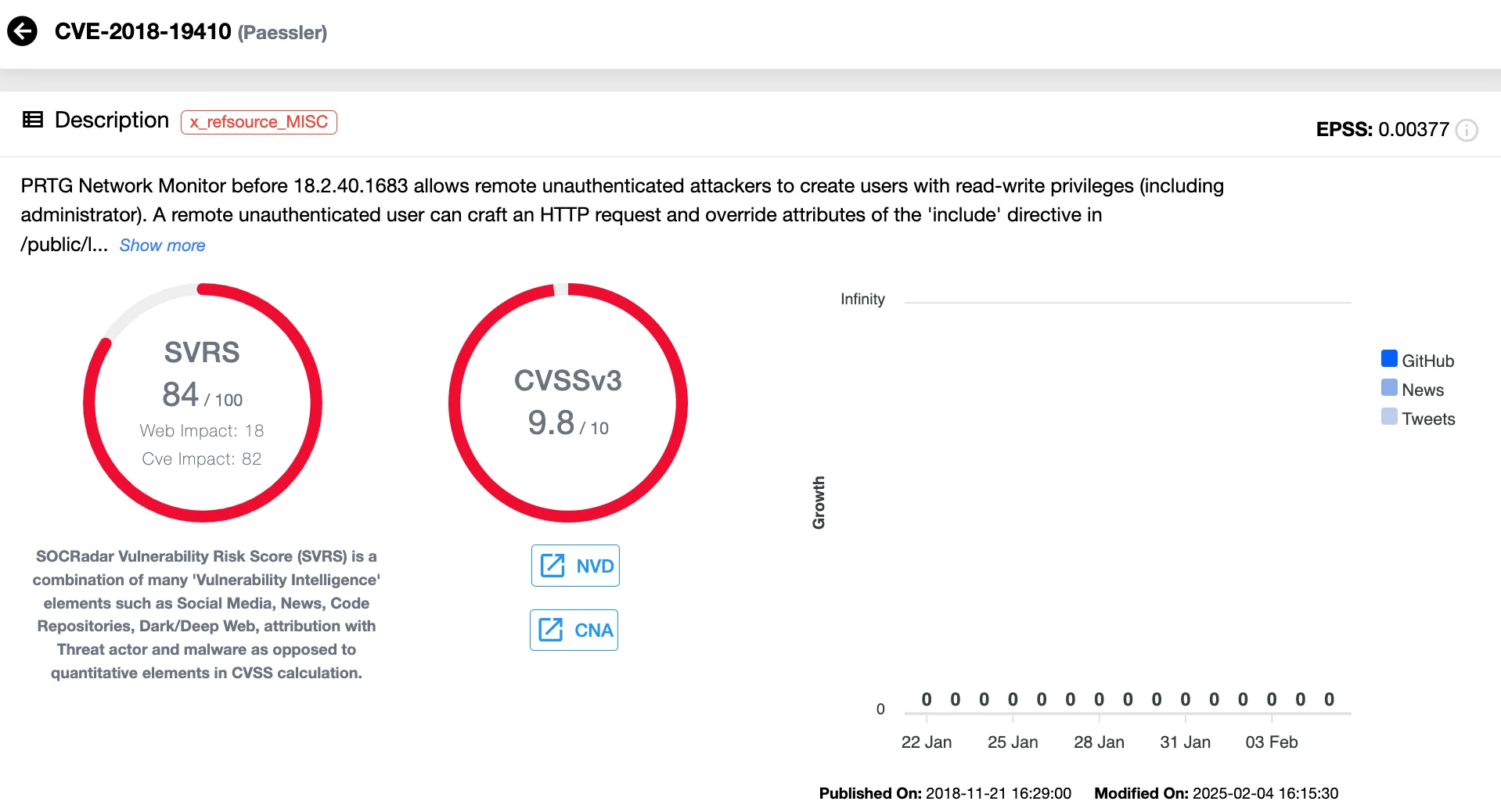
Vulnerability card of CVE-2018-19410 (SOCRadar’s Vulnerability Intelligence)
SOCRadar’s Vulnerability Intelligence module provides continuous tracking and analysis of vulnerabilities, ensuring you can prioritize and address them before they’re exploited. Gain insights into active threats, risk levels, and patching needs to reduce your attack surface with capabilities like:
- Real-time CVE tracking
- Risk assessment and exploitability insights
- Integration with threat intelligence
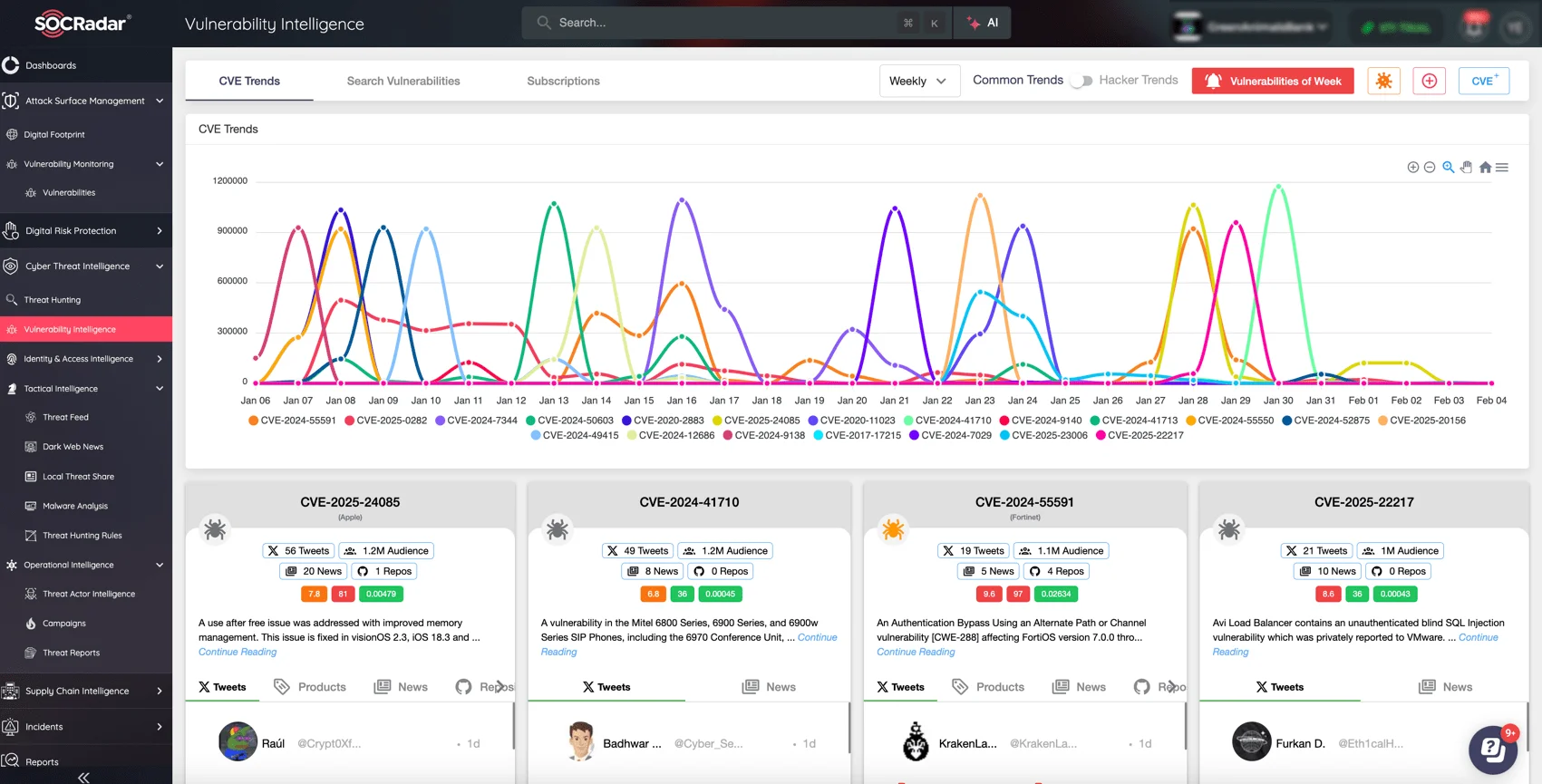
Secure your assets with SOCRadar’s Vulnerability Intelligence today.
Act Now: Patch These Vulnerabilities Before the Deadline
Organizations must take immediate action to patch these vulnerabilities and implement additional security controls to minimize risk exposure. According to CISA, federal agencies are required to remediate these vulnerabilities by February 25, 2025. For further details, refer to the official CISA alert.
Strengthening Your Security Posture with SOCRadar’s ASM
With the daily rise of new CVEs and emerging threats, organizations often struggle to stay ahead of potential risks. To stay secure, it’s essential to have a proactive solution in place that not only detects these vulnerabilities but also helps prioritize remediation efforts and reduce the attack surface.
This is where SOCRadar’s Attack Surface Management (ASM) module comes in. Designed to help organizations identify, prioritize, and mitigate vulnerabilities in real-time, ASM enables continuous monitoring of your digital assets and vulnerabilities. With its CISA KEV Check feature, the module helps you stay on top of vulnerabilities that are actively exploited, ensuring your systems remain aligned with the latest security protocols.
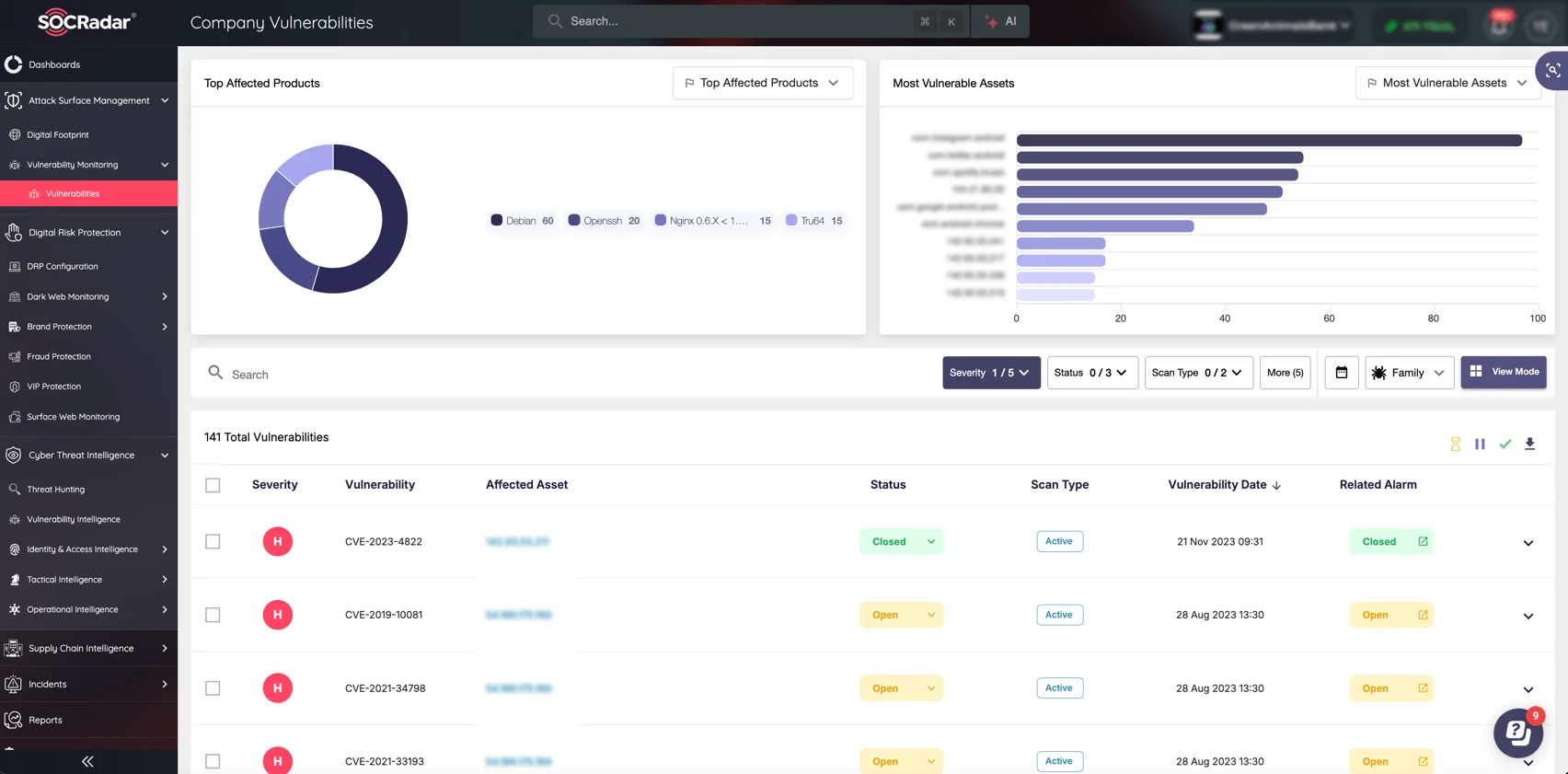
SOCRadar’s Attack Surface Management (ASM) module
With real-time threat intelligence, automated remediation insights, and continuous monitoring, SOCRadar’s ASM module offers extensive protection for your organization, strengthening your defenses and helping you combat threat actors and exploitation risks.


































