
CISO’s Guide to Navigating Dark Web Risks – How to Protect Your Organization
As cyber threats grow increasingly sophisticated, Chief Information Security Officers (CISOs) are tasked with defending their organizations from dangers that are often hidden from plain sight. Among these threats, the Dark Web stands out as one of the most insidious, a concealed part of the internet where cybercriminals thrive, trading in stolen data, hacking tools, and other illicit goods.
For a CISO, understanding and mitigating the risks born from the Dark Web has become essential for protecting their organizations in an increasingly complex digital landscape.
What is the Dark Web for a CISO?
The Dark Web, a hidden realm inaccessible through standard search engines, requires specialized software like Tor or I2P for access. While not entirely illegal, this space is often exploited by threat actors to trade stolen data, develop cyberattack tools, and coordinate malicious activities.
For CISOs, the Dark Web represents a dynamic threat landscape that must be proactively monitored to protect sensitive assets.

“Chief Information Security Officer and Dark Web”, illustrated by DALL-E
Critical Dark Web Risks Every CISO Should Know About
The Dark Web poses significant risks to organizations, with threat actors exploiting this hidden part of the internet to buy, sell, and exchange malicious tools, stolen data, and other illicit services. As a Chief Information Security Officer, understanding these threats and how they can affect your organization’s security is vital.
Below are some of the most critical Dark Web risks you should be aware of.
Data Breaches and Data Theft
Sensitive data, from personal records to intellectual property, is frequently traded or auctioned on Dark Web marketplaces.
For example, data breach sets are compilations of breached data often sold or distributed by cybercriminals for malicious purposes like identity theft, financial fraud, or phishing. These sets contain information from multiple breaches, making them highly valuable.
For more, check out our blog post “Beyond Phishing: Top 10 Data Breach Sets”.
Cyber Attack Tool Market
Cybercriminals buy and sell malware, hacking kits, and zero-day exploits, making sophisticated attacks accessible even to less experienced actors.
SOC Tools built on the SOCRadar platform can be helpful in addressing these threats. These tools are designed to investigate common incidents like phishing, malware, and account breaches. By leveraging machine learning from big data and advanced behavioral analytics, the SOC Tools service enables faster detection and more effective response to emerging threats.
Targeted Phishing and Social Engineering
Phishing-as-a-Service kits on the Dark Web make it easier for attackers to launch highly customized, convincing phishing campaigns.
SOCRadar’s free tool, Phishing Radar, helps you detect domain spoofing and phishing attempts. This tool allows you to proactively protect your organization from social engineering attacks.
Phishing Radar, available under SOC Tools on SOCRadar LABS
Ransomware-as-a-Service (RaaS)
RaaS platforms allow individuals with minimal technical knowledge to launch devastating ransomware campaigns, sharing profits with the developers.
Ransomware-as-a-Service operates like a business, where developers provide tools to customers to carry out attacks. Curious about RaaS? Read more in our blog: What is Ransomware-as-a-Service?.
Credential Stuffing and Account Takeovers
Compromised credentials, often sold in bulk on Dark Web forums, fuel attacks that lead to unauthorized access to corporate systems. Credential stuffing attacks are especially dangerous for mobile and web applications. With stolen credentials, hackers can easily automate attacks, making them more efficient.
Check out our blog post, “The Age of Credential Stuffing & Account Takeover”, for more on how to defend against these attacks.
How to Fortify Your Organization Against Dark Web Risks
To effectively combat risks originating from the Dark Web, CISOs should adopt a multi-layered security strategy:
- Proactive Dark Web Monitoring: Utilize advanced tools like SOCRadar’s Dark Web Monitoring to identify compromised data and credentials early. SOCRadar helps detect potential risks in real time, allowing for swift mitigation and minimizing exposure.
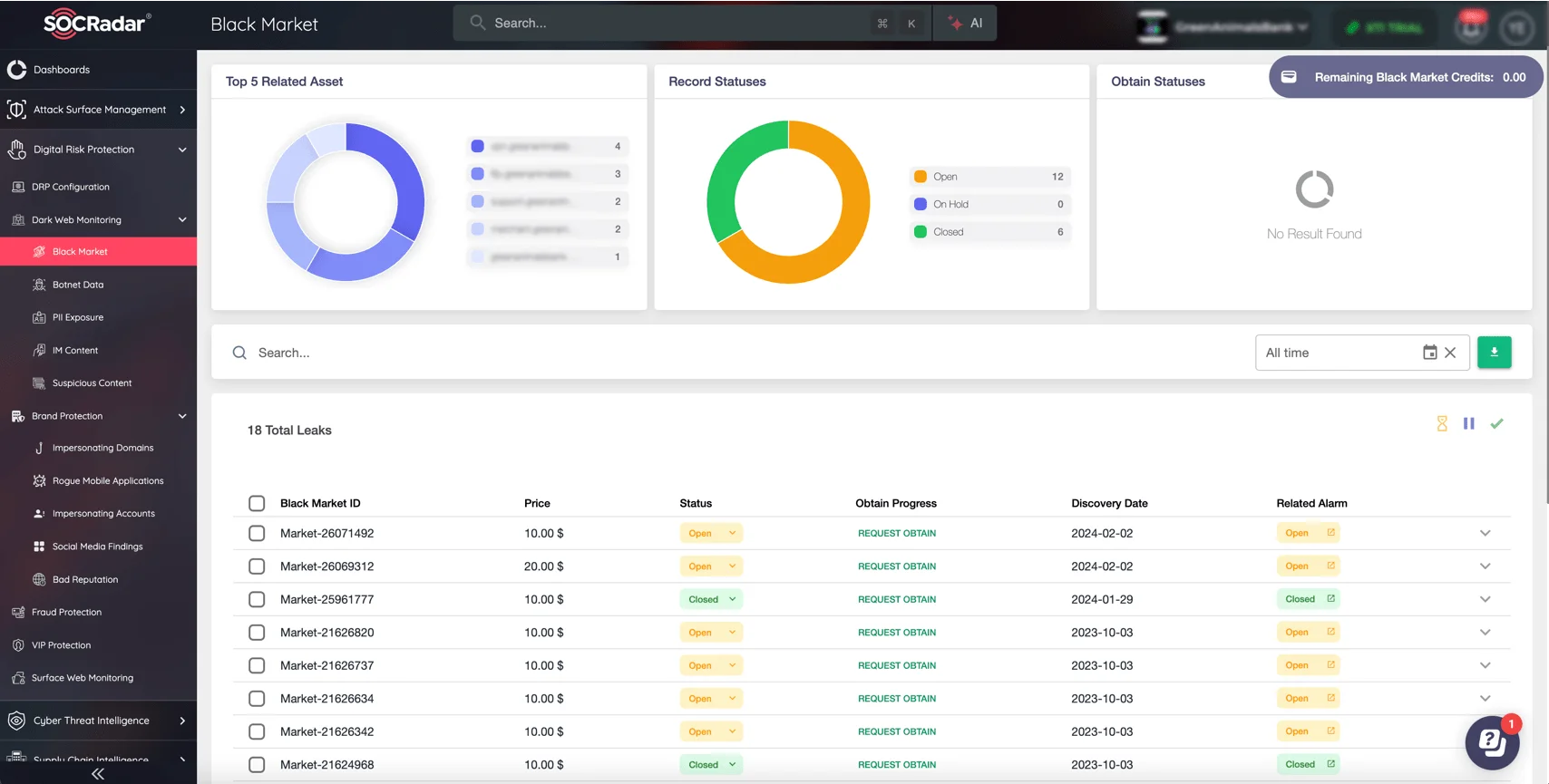
Monitor Black Markets, PII Exposure, Suspicious Content, and more with SOCRadar Dark Web Monitoring
- Strong Authentication and Access Controls: Enforce strong password policies and implement Multi-Factor Authentication (MFA) to reduce the chances of unauthorized access. These steps are essential in securing critical systems.
- Employee Awareness and Training: Regularly educate employees on recognizing phishing attempts and social engineering tactics. Simulated phishing exercises can improve awareness and reduce the likelihood of successful attacks.
- Swift Incident Response: Create a comprehensive incident response plan to address data breaches and leaks. A rapid response is key to minimizing damage and accelerating recovery.
- Threat Intelligence Integration: Leverage actionable threat intelligence feeds, like those from SOCRadar, to stay updated on emerging vulnerabilities and attack methods. Proactively addressing these threats helps strengthen your defense.
- Regular Vulnerability Assessments and Penetration Testing: Conduct routine testing to identify and fix security gaps before cybercriminals exploit them. Regular assessments ensure your security posture remains strong and up to date.
Find Out How Popular You Are on the Dark Web
With SOCRadar LABS’ Dark Web Report, you can quickly discover if your data has been exposed on Dark Web forums, black market sites, leak platforms, or Telegram channels.
Get your free Dark Web Report now.
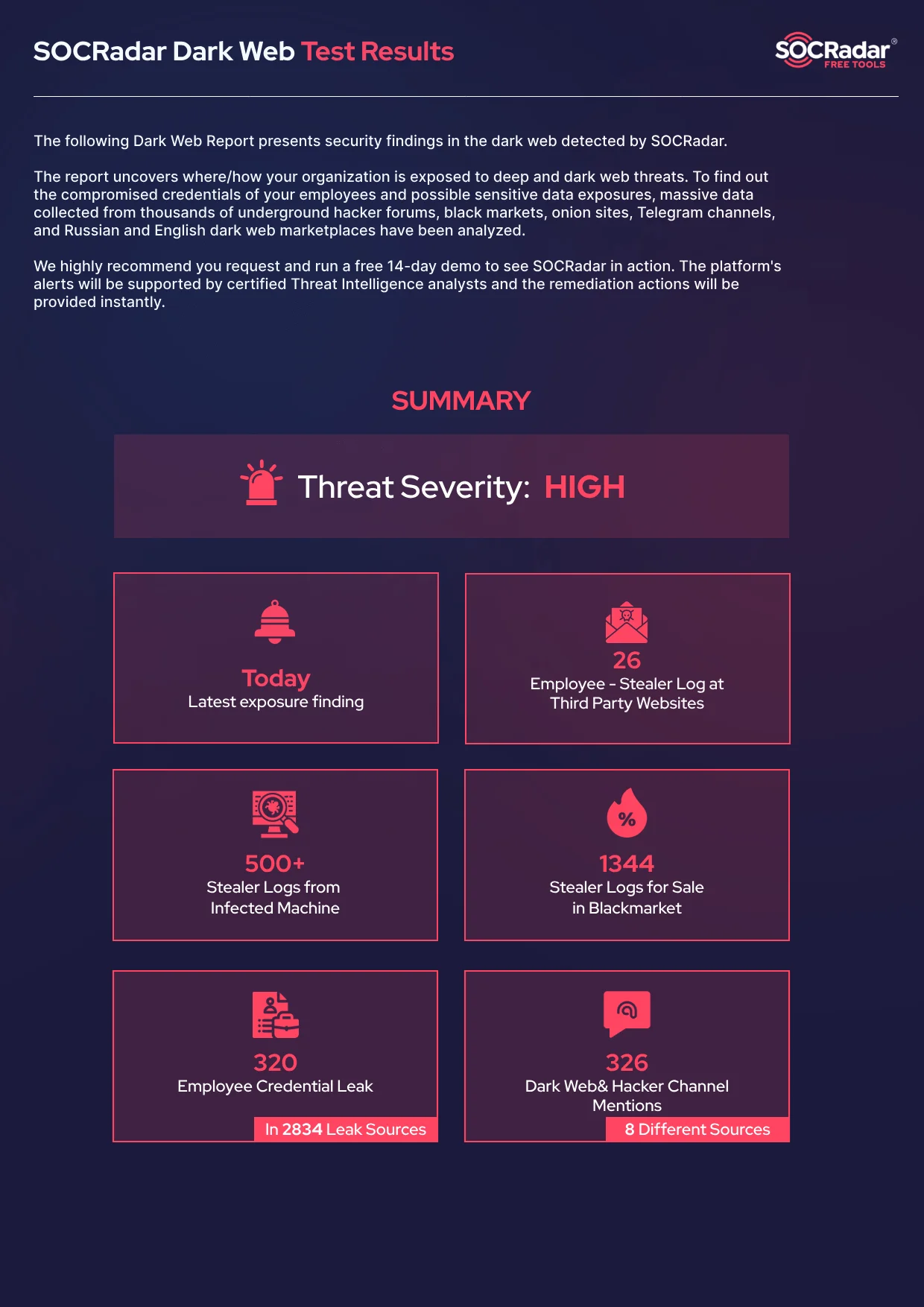
Example summary from SOCRadar’s free Dark Web Report
Why SOCRadar is a CISO’s Ally
In addition to our free Dark Web Report, SOCRadar provides CISOs with a full suite of threat intelligence tools designed to mitigate Dark Web risks. Key benefits include:
- Early Threat Detection: Monitor Dark Web marketplaces in real time for leaked data and credentials.
- Actionable Insights: Access detailed reports and analytics to inform your security strategy.
- Automated Security Workflows: Simplify threat detection and response through automated alerts and workflows.
- Enhanced Resilience: Stay ahead of emerging threats with the latest intelligence from trusted sources.
- Track Threat Actors’ Footprints: Gain valuable insights into threat actors’ operations, tactics, techniques, and procedures (TTPs) with SOCRadar’s Threat Actor Intelligence.
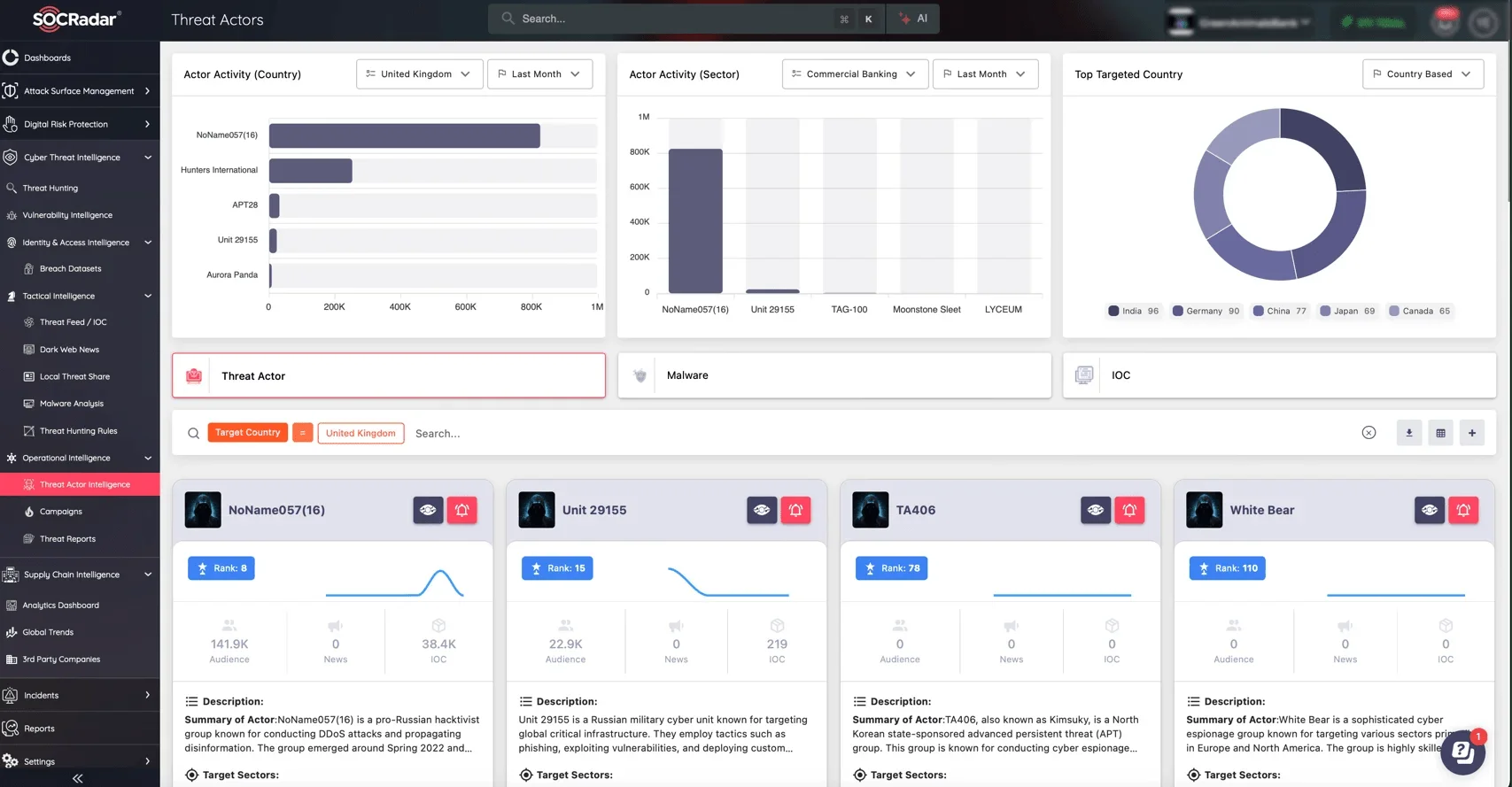
Easily track threat actors’ footprints; gain insights into their operations and TTPs via SOCRadar’s Threat Actor Intelligence
Moreover, a free threat actor database is now available on SOCRadar LABS, showcasing some of the features of the SOCRadar XTI platform’s Threat Actor Intelligence module.
Conclusion
The Dark Web continues to pose a dynamic and persistent threat, but with the right strategies and tools, CISOs can effectively defend their organizations. SOCRadar’s Extended Threat Intelligence (XTI) platform allows businesses to proactively identify, assess, and mitigate Dark Web threats.
Take action today to secure your organization. Discover how SOCRadar can help – request a demo and take the first step toward securing your critical assets.



































