
Citrix RDP Access, Jenkins Exploit, and Major Database Leak of Union Bank of India
In the past week, the SOCRadar Dark Web Team has uncovered a series of alarming cyber threats involving unauthorized access sales, database leaks, and new phishing services. Among the most concerning incidents is the alleged sale of Citrix RDP access to an American company. Additionally, an exploit for a newly identified vulnerability in Jenkins, CVE-2024-43044, has been shared. Other incidents include the sale of employee data from the Union Bank of India, database leaks exposing sensitive information of millions of users, and the emergence of a new phishing service.
Receive a Free Dark Web Report for Your Organization:
Alleged Unauthorized Citrix RDP Access Sale is Detected for an American Company
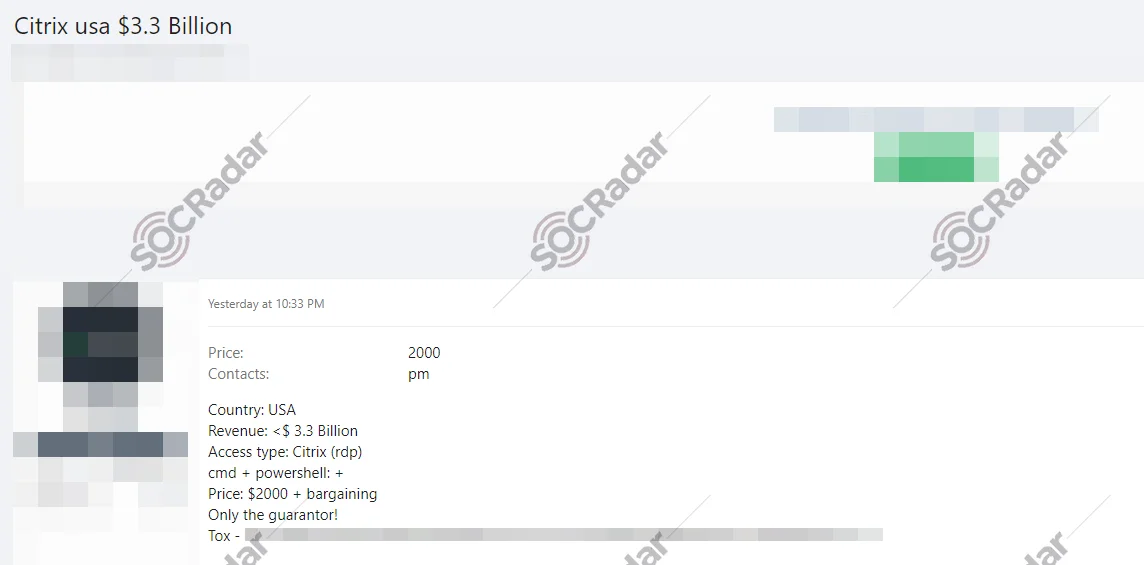
SOCRadar Dark Web Team detected a post on a hacker forum where an unauthorized sale of RDP Citrix access, allegedly belonging to a company operating in the United States, has been advertised. The threat actor claims that this access could provide significant entry into the company’s systems.
According to the threat actor’s claims, the company in question is based in the USA and has an annual revenue of less than $3.3 billion. The type of access being sold is Citrix (RDP), with command-line and PowerShell capabilities available. The starting price for this access is $2,000, with room for negotiation. The threat actor emphasizes that the sale is only available through a guarantor, and they provide contact details via Tox.
CVE-2024-43044 Exploit is Shared for Jenkins
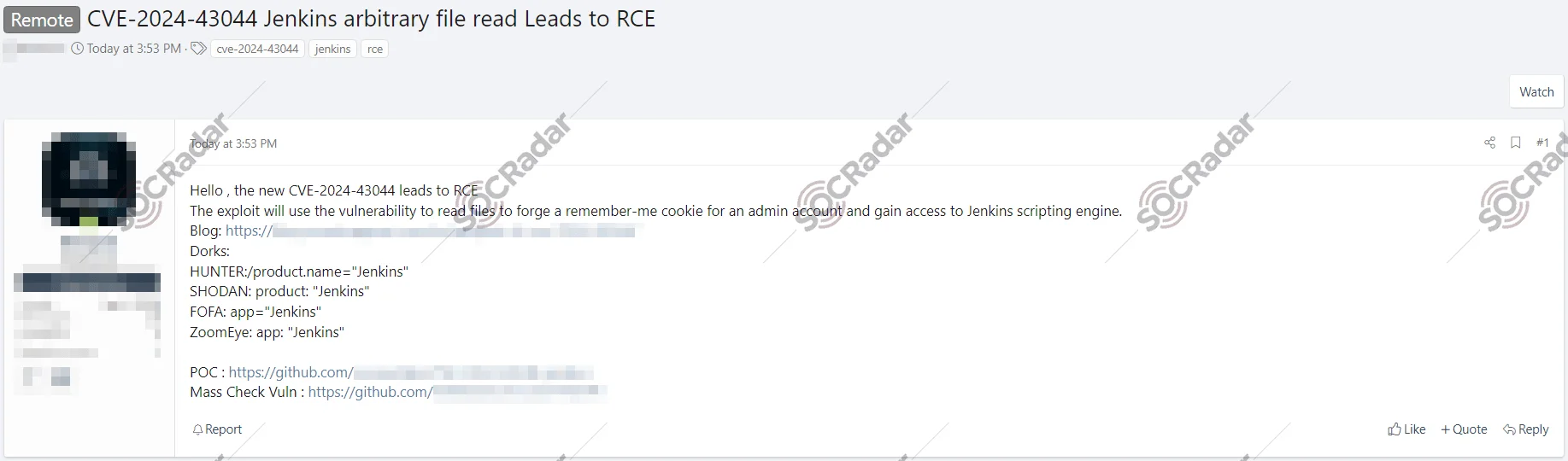
SOCRadar Dark Web Team detected a post on a hacker forum where an exploit for the newly identified vulnerability CVE-2024-43044 in Jenkins has been shared. The threat actor claims that this exploit can lead to Remote Code Execution (RCE), posing a significant risk to Jenkins installations.
According to the threat actor’s claims, the exploit leverages the CVE-2024-43044 vulnerability to read files and forge a “remember-me” cookie for an admin account, ultimately granting access to Jenkins’ scripting engine. The threat actor also claims to have provided a Proof of Concept (POC) link and a mass vulnerability checking tool on GitHub, which, if true, could make it easier for malicious actors to identify and exploit this vulnerability.
Alleged Employee Database of Union Bank of India is Leaked
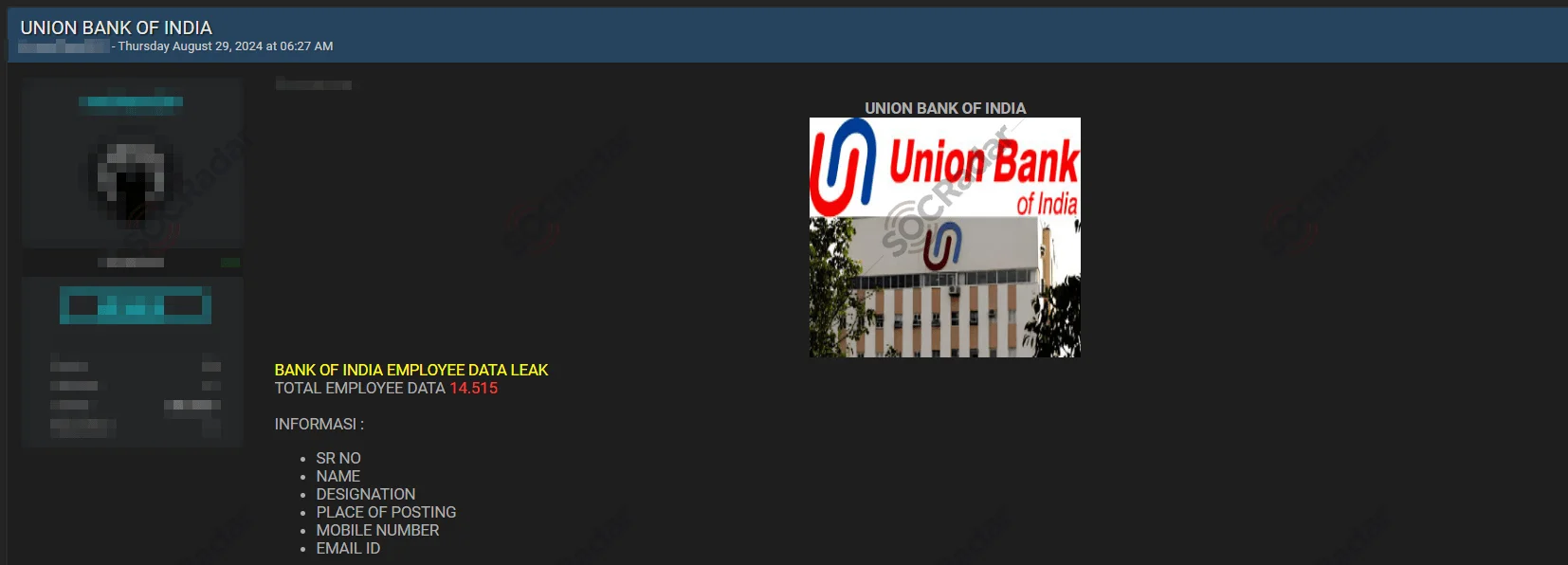
SOCRadar Dark Web Team detected a post on a hacker forum where an alleged employee database leak for the Union Bank of India has been reported. The threat actor claims to possess sensitive information belonging to thousands of employees.
According to the threat actor’s claims, the database contains details on 14,515 employees of the Union Bank of India. The leaked information allegedly includes serial numbers, names, designations, places of posting, mobile numbers, and emails.
Alleged Database of Rappi Pay is Leaked
SOCRadar Dark Web Team detected a new alleged database leak related to Rappi Pay, a digital payment service. The threat actor responsible for the leak claims to have uploaded the database, which reportedly contains sensitive information on approximately 46,000 users.
According to the threat actor’s post, the breach occurred in July 2024 and involved a significant amount of personal data, including full names, gender, addresses, geographical zones, phone numbers, email addresses, and financial details such as contract numbers and PAN (Primary Account Numbers).
Alleged Database of Rappi is Leaked

SOCRadar Dark Web Team detected a new alleged database leak for the popular delivery service, Rappi. A threat actor has claimed responsibility for breaching and leaking the database, which they assert contains the personal information of over 32 million users.
According to the threat actor’s claims, the leaked data includes a wide range of sensitive information such as full names, CPF numbers, email addresses, phone numbers, addresses, and detailed financial records related to Rappi’s services. The breach, which allegedly occurred in July 2024, has been shared on the dark web, and the threat actor encourages the community to download and explore the database.
The compromised data includes fields like generation date, contract ID, and various financial details, such as credit limits, balances, interest rates, and payment histories, all tied to individual users. This extensive leak poses a significant risk to the affected users, potentially exposing them to various forms of cybercrime and identity theft.
New Phishing Service is Detected
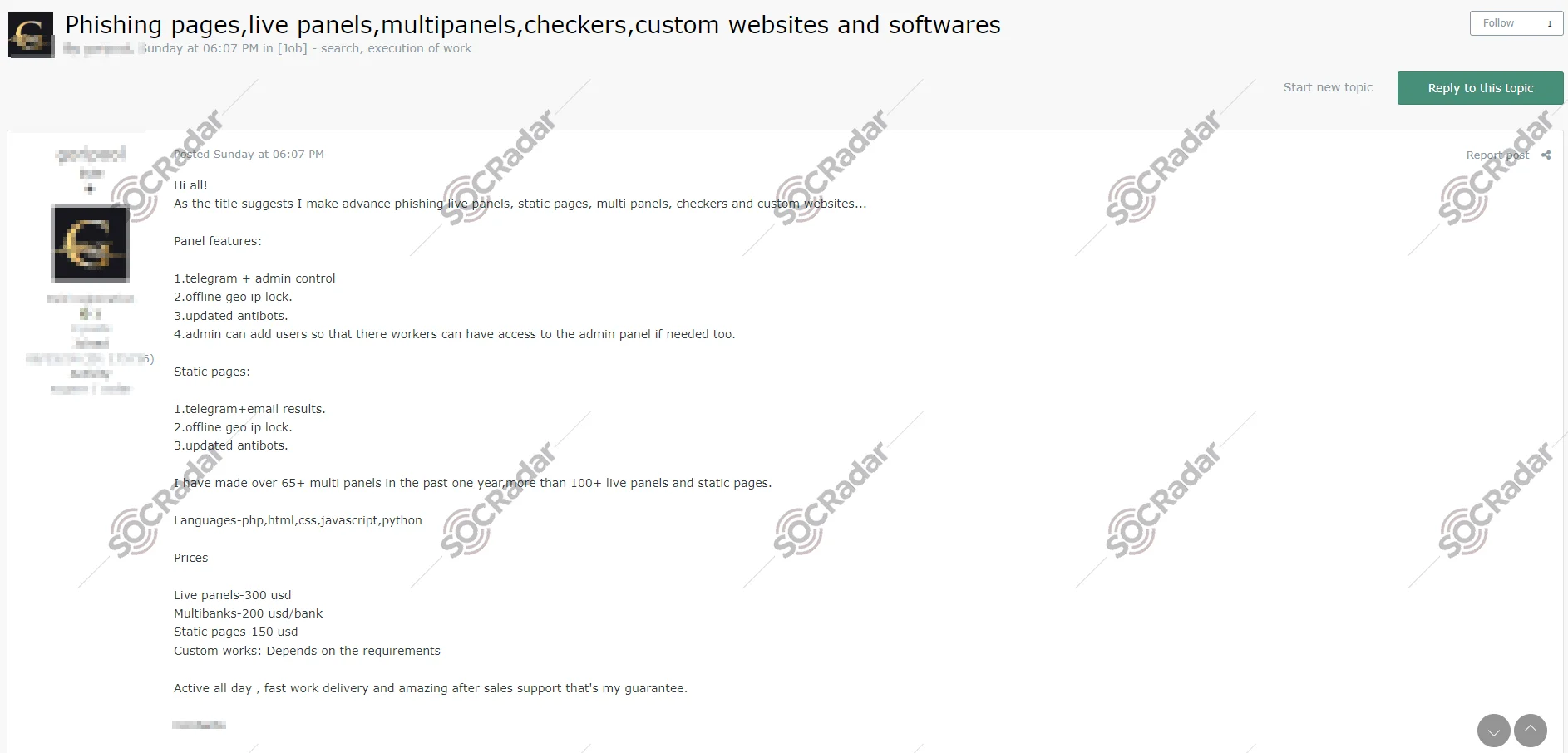
SOCRadar Dark Web Team detected a post on a hacker forum advertising a new phishing service that offers a range of customizable options for cybercriminals. The threat actor claims to provide advanced phishing live panels, static pages, multi panels, checkers, and custom websites, tailored to meet specific needs.
According to the threat actor’s claims, the phishing panels come equipped with several features, including Telegram integration for control, offline geo IP lock, updated antibot mechanisms, and the ability for administrators to add users who may require access to the admin panel. For static phishing pages, similar features are offered, such as Telegram and email result integration, offline geo IP lock, and updated antibot protection.
The threat actor also boasts of having created over 65 multi panels, more than 100 live panels, and numerous static pages in the past year. They work with various programming languages, including PHP, HTML, CSS, JavaScript, and Python. The pricing for these services starts at $300 for live panels, $200 per bank for multi-bank panels, and $150 for static pages. Custom projects are priced based on specific requirements.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































