Critical DICOM Server Misconfigurations Lead to Exposure of 1.6M Medical Records
In a regular threat and vulnerability hunting activity, SOCRadar has discovered during their research that thousands of DICOM servers were exposed on the internet due to misconfigurations, resulting in the exposure of patient data for many countries. These identified data include patient names, surnames, birthdates, disease information, images, and similar details.
SOCRadar regularly monitors publicly accessible servers and identifies misconfigured servers, then alerts its customers. The exposure of servers poses a significant risk to companies since it allows access and use of the data by various threat actors. SOCRadar conducts scans on the Deep, Dark, and Clear Web to detect such leaks.
The healthcare sector is one of the industries heavily targeted by threat actors such as the Conti/Ryuk ransomware attack against Ireland’s Health Service Executive. Many companies in this sector are among the targets of complex threat groups such as Ransomware and APT (Advanced Persistent Threat) groups.
DICOM
DICOM is a standard used for the storage, viewing, and transmission of medical images. Images obtained from various imaging devices such as X-rays, ultrasound, computed tomography, and Magnetic Resonance Imaging (MRI), are stored in the DICOM form.
DICOM facilitates the more efficient and effective sharing of medical images and data, thereby contributing to the improvement of the quality of patient care.
DICOM Usage Areas and Purposes
DICOM’s main areas of use are as follows:
- Storage and Archiving of Medical Images: DICOM enables the secure and organized storage of medical images. This allows for easy accessibility and retrieval of images.
- Viewing and Analysis of Medical Images: DICOM facilitates the accurate and efficient viewing and analysis of medical images. This enables doctors and other healthcare professionals to diagnose diseases more quickly and accurately.
- Transfer of Medical Images for Remote Diagnosis and Treatment: DICOM allows for the remote transfer of medical images between different hospitals and clinics. This enables expert doctors to diagnose and treat patients without physically seeing them.
- Utilization for Education and Research Purposes: DICOM permits the use of medical images for educational and research purposes. This enables medical students and researchers to examine and analyze medical images more effectively.
Detection and Identification
SOCRadar Threat and Vulnerability Hunting Team have identified numerous publicly accessible unsecured DICOM servers during their research. Since search engines like Shodan and similar tools index these servers, they pose a security risk by potentially making them targets for security researchers or threat actors.
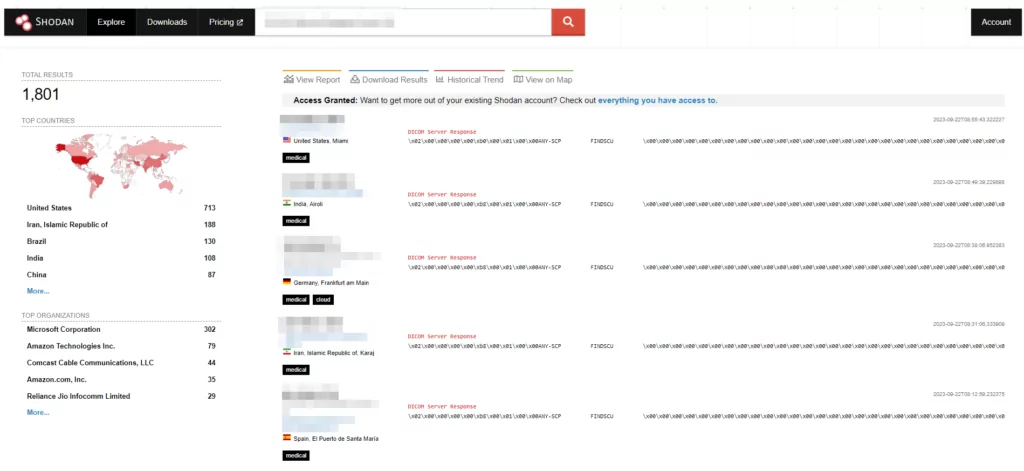
Based on the findings and analyses conducted by SOCRadar Threat and Vulnerability Hunting Team, it has been observed that the relevant data includes information such as patient name, patient ID, date of birth, description, modality, images, date, time, accession number, referring physician, and institution.
The exposure of patient data can pose various serious risks:
- Privacy Breach: The exposure of patient data means the leakage of individuals’ highly personal medical information. This seriously violates their personal privacy rights and is a major source of concern for data owners.
- Identity Theft: The exposure of patient data can present a significant opportunity for identity thieves. Personal information can be used for fraud and deception purposes, such as fraudulent health insurance claims or financial fraud. With the exposed data, attackers can receive healthcare services, obtain medications, or undergo medical procedures. This can also damage existing treatment plans and medical histories.
- Fraud: The exposure of patient data can lead to an increase in healthcare fraud, such as writing fake prescriptions or creating fake documents indicating receipt of healthcare services. This can place an additional financial burden on healthcare systems.
- Social Engineering Attacks: The leaked patient data enables attackers to conduct convincing social engineering attacks on targeted individuals. These types of attacks aim to deceive individuals into providing more information or money.
- Legal Liability: Healthcare institutions or providers bear legal responsibility for the protection and confidentiality of patient data. They may face serious legal consequences in cases of data exposure.
- Fake Medical Procedures: Medical procedures conducted with false identities can lead to mix-ups in patients’ medical records and result in incorrect treatments. This situation can cause serious harm to patients’ health.
- Medical Extortion: Exposed medical data can be used to extort patients. Since this data contains private and sensitive information, it can lead to personal and financial harm.
In conclusion, the exposure of patient data can lead to serious and legal issues. Therefore, the healthcare sector and other relevant organizations must invest significant effort in effectively safeguarding patient data and implementing strong security measures against cyber threats.
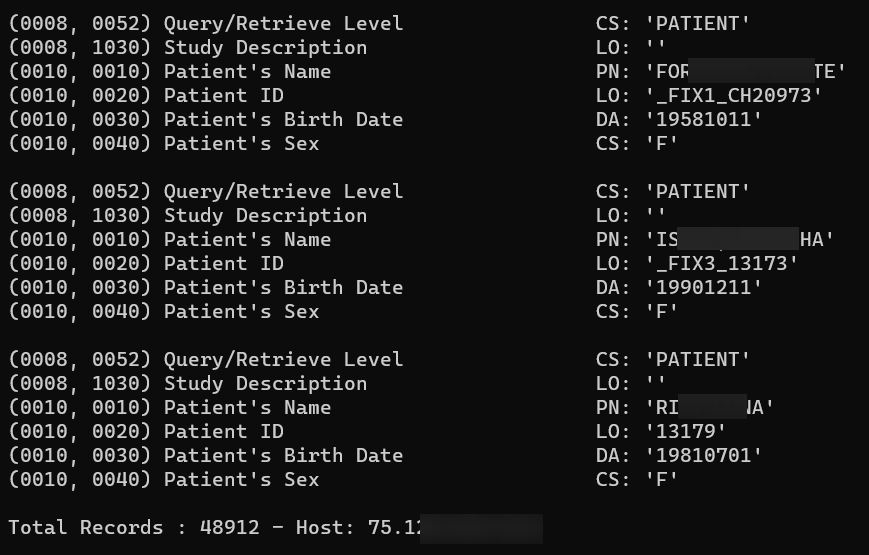
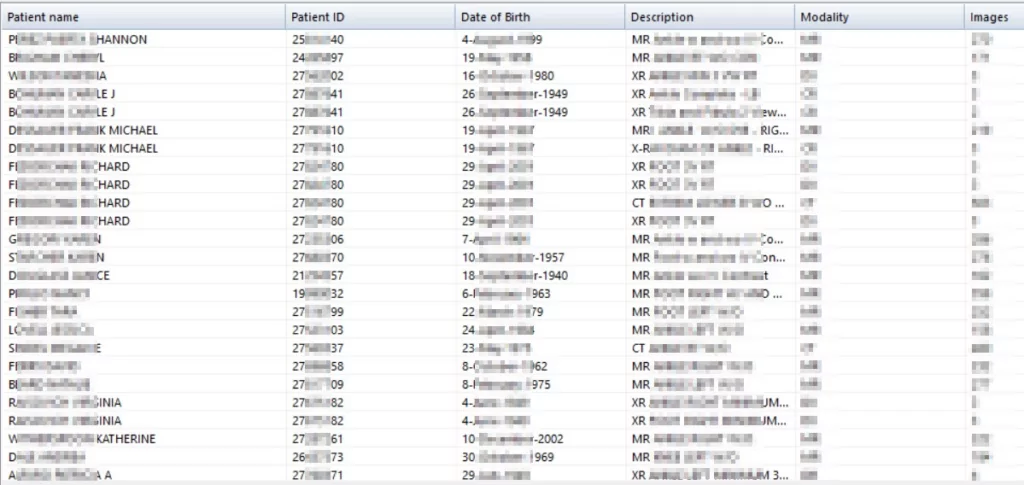
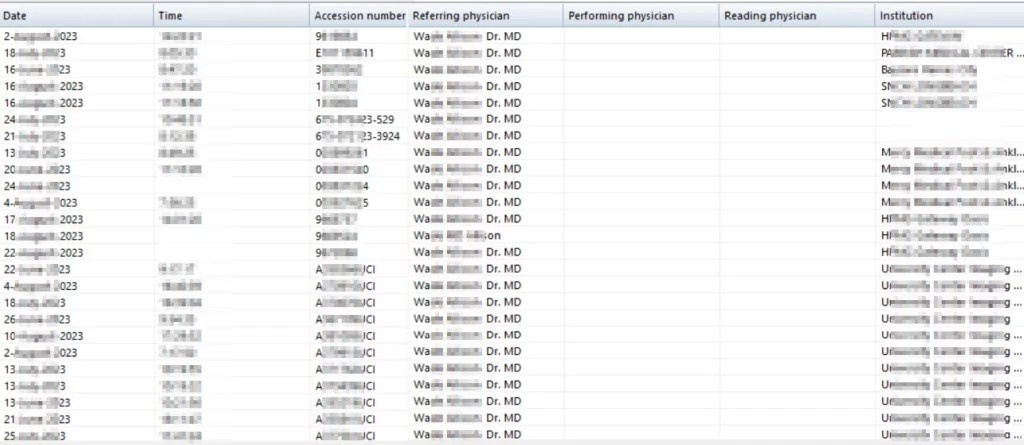
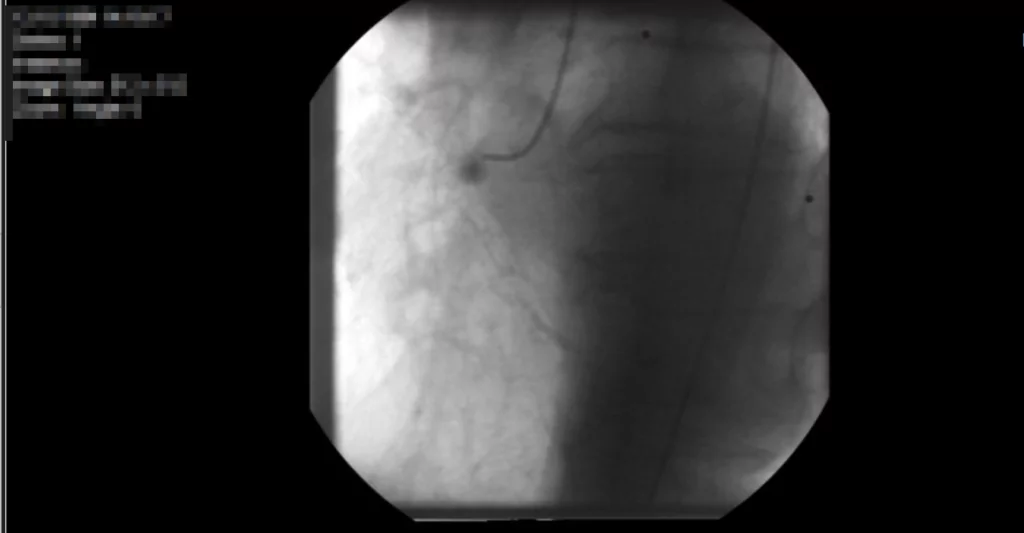
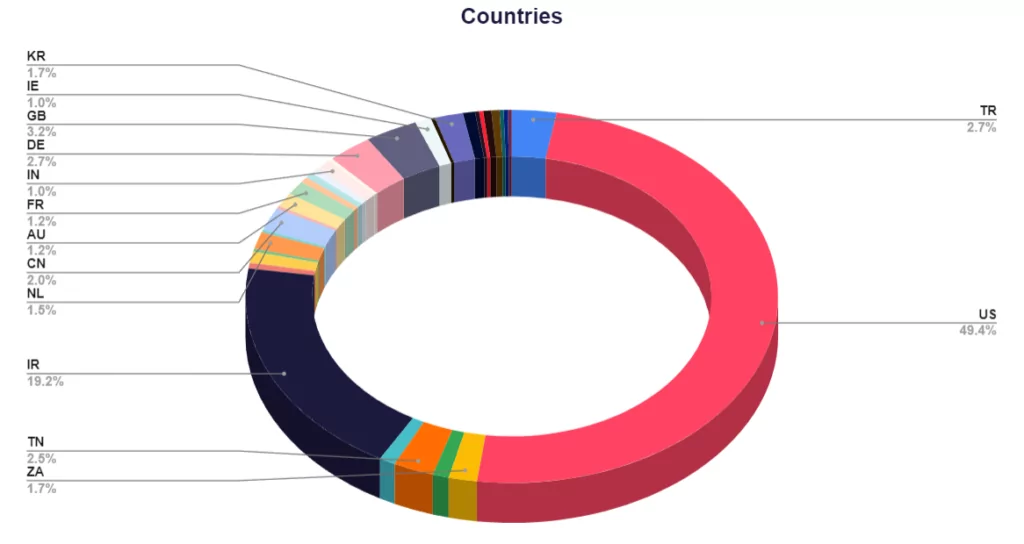
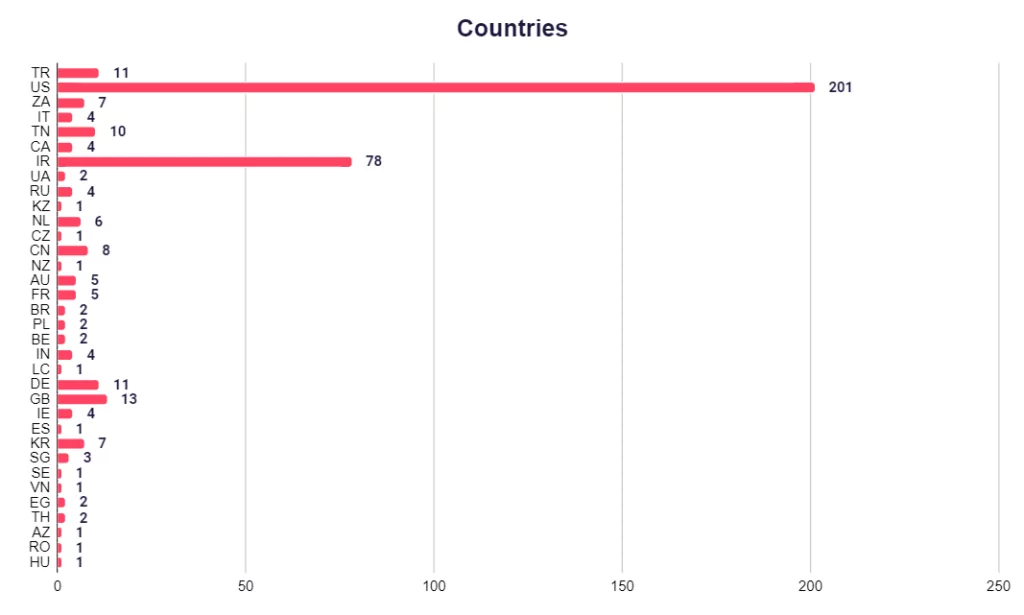
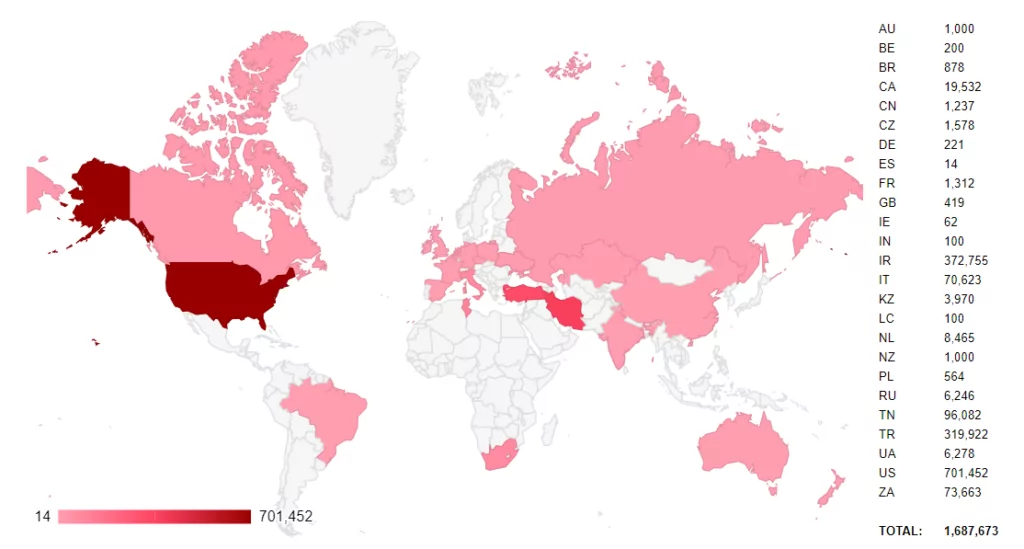
SOCRadar Threat and Vulnerability Hunting Team analyzed all servers to reveal how many patient records were exposed through these servers. You can see an example of the analysis performed for a server in Figure 2. You can see the graph resulting from the analysis of all servers in Figure 7.
As a result of the analysis, a total of 1,687,673 patient records from 25 countries were identified.
Common Issues, Risks and Remediation
Numerous servers and services, including Elasticsearch, FTP, and MongoDB, among others, are accessible on the internet. If not configured correctly, these servers and services can result in data exposure. This has led to a surge in data breaches. The Adobe Creative Cloud incident serves as an illustrative example. The information exposed in these breaches is exploited by various malicious actors, thereby posing a significant threat and risk to both companies and users.
The main risks of misconfigured servers are as follows:
- Security Vulnerabilities: Can lead to attacks and data leakage.
- Performance Issues: Inefficient resource allocation or use of network traffic service outages and slowdowns can occur.
- Data Loss or Leakage: Increases the risk of sensitive data leakage.
- Service Disruptions: Due to resource allocation problems, network issues, or improper updates unexpected interruptions may occur.
- Backup Issues: Due to incomplete or outdated backups, improper storage, lack of version control, and encryption issues data recovery may become more difficult.
- Compliance Issues: Legal penalties, reputational damage, financial losses, security vulnerabilities, operational disruptions, and potential loss of market access can be the risks of non-compliance with standards.
- Cost Increase: Due to factors like over-provisioning, inefficient resource allocation, network congestion, and licensing discrepancies unnecessary resource consumption or additional costs may occur.
- Audit Challenges: Can complicate monitoring and threat detection by causing incomplete logging, erratic alerting, reduced visibility, delayed incident response, compromised access controls, and hindered vulnerability identification.
- Slow Response Time: Due to incomplete logging, delayed alerts, limited visibility, compromised access controls, and hindered audit trails responding quickly to threats may become more challenging.
To mitigate and prevent these risks, it is important to properly configure servers, adhere to security best practices, and regularly review them. Additionally, applying security patches and updates regularly is crucial.
Conclusion
It is crucial to recognize that security is an ongoing endeavor, necessitating continual monitoring, testing, and upkeep to guarantee systems are properly configured and safeguarded. The emphasis on automated tools and process management aims to reduce human error. Even the most seasoned security experts may occasionally overlook a minor detail that could have significant repercussions.
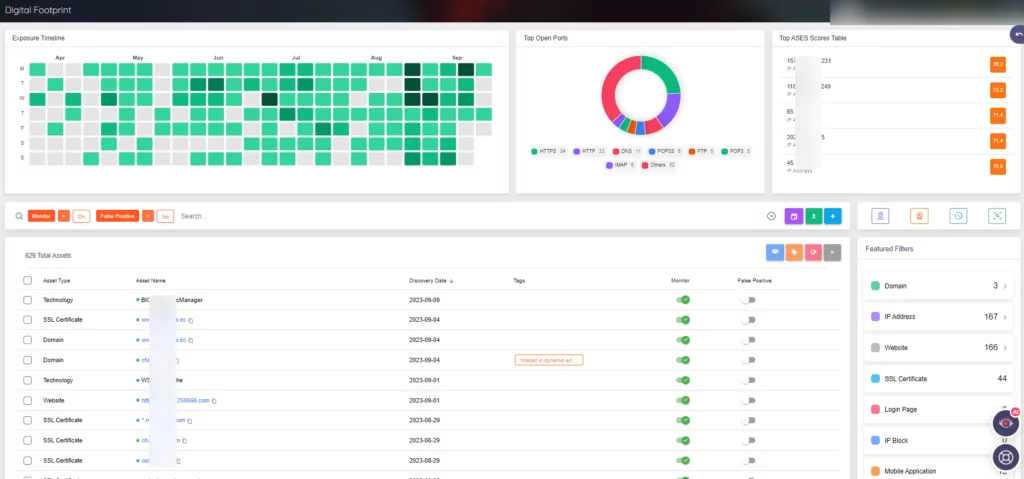
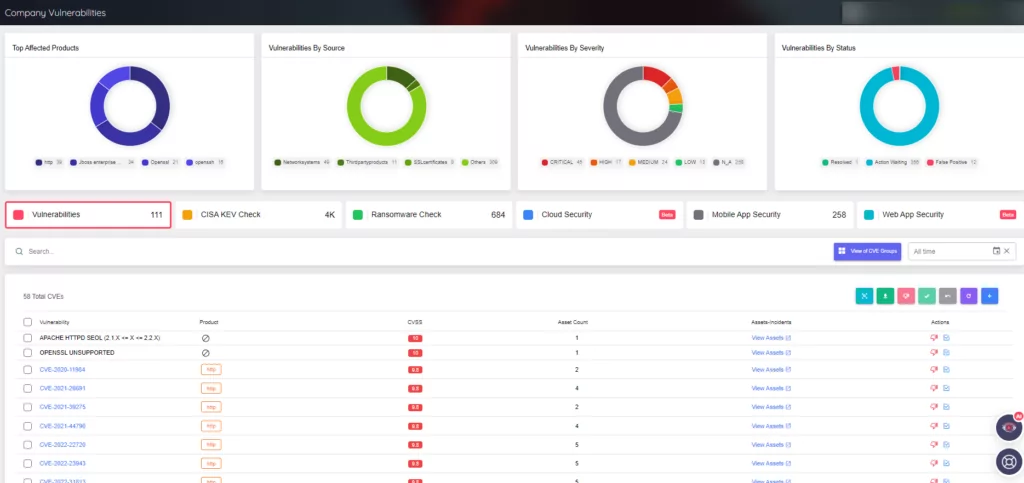
By harnessing timely, pertinent, and actionable threat intelligence via SOCRadar’s External Attack Surface Management (EASM), organizations can address misconfiguration challenges. This is achieved through a comprehensive assessment of assets, involving the ingestion, deduplication, and correlation of data from IT and security solutions. Moreover, Brand Protection acts as a shield for digital assets and leverages Cyber Threat Intelligence (CTI) monitoring to spotlight specific security vulnerabilities.