Critical RCE Vulnerability (CVE-2023-33308) in FortiOS and FortiProxy: Immediate Security Update Required
Fortinet has recently addressed a critical Remote Code Execution (RCE) vulnerability that affects FortiOS and FortiProxy. This vulnerability, tracked as CVE-2023-33308 and rated with a CVSSv3 score of 9.8, could be exploited by remote attackers to execute unauthorized code or commands on vulnerable systems. It is crucial for users and administrators to promptly apply the necessary security updates to protect their environments.
About CVE-2023-33308: A Stack-Based Buffer Overflow Vulnerability
The vulnerability arises from a stack-based buffer overflow in FortiOS and FortiProxy. It can be exploited through crafted packets reaching proxy policies or firewall policies with proxy mode alongside SSL/TLS deep packet inspection. The severity of this vulnerability has been rated as critical.
Affected Versions
The following versions of FortiOS and FortiProxy are impacted by the CVE-2023-33308 vulnerability:
FortiOS:
- Versions 7.2.0 to 7.2.3
- Versions 7.0.0 to 7.0.10
FortiProxy:
- Versions 7.2.0 to 7.2.2
- Versions 7.0.0 to 7.0.9
According to the Fortinet advisory, it has been clarified that the CVE-2023-33308 vulnerability does not affect FortiOS versions 6.0, 6.2, 6.4, and FortiProxy versions 2.x, and 1.x.
Security Updates and Fixes for the CVE-2023-33308
Fortinet has provided security updates and fixes for the CVE-2023-33308 vulnerability. Users are advised to upgrade to the following versions:
FortiOS:
- Version 7.4.0 or above
- Version 7.2.4 or above
- Version 7.0.11 or above
FortiProxy:
- Version 7.2.3 or above
- Version 7.0.10 or above
CISA has also issued an alert regarding the vulnerability, advising affected organizations to promptly apply the available security update.
Workaround for the CVE-2023-33308
As a temporary workaround, users can disable HTTP/2 support on SSL/TLS inspection profiles used by proxy policies or firewall policies with proxy mode. Detailed instructions can be found in the Fortinet security release FG-IR-23-183.
The CVE-2023-33308 vulnerability poses a significant threat to systems running FortiOS and FortiProxy. It is crucial for users and administrators to promptly update their software to the recommended versions or apply the provided security fixes. By doing so, organizations can mitigate the risk of unauthorized code execution and ensure the security of their networks.
Enhancing Vulnerability Management with SOCRadar’s Vulnerability Intelligence Module
SOCRadar’s Vulnerability Intelligence Module is an invaluable tool for addressing the risks associated with vulnerabilities like CVE-2023-33308. This comprehensive solution ensures that your organization can effectively address vulnerabilities and minimize potential risks.
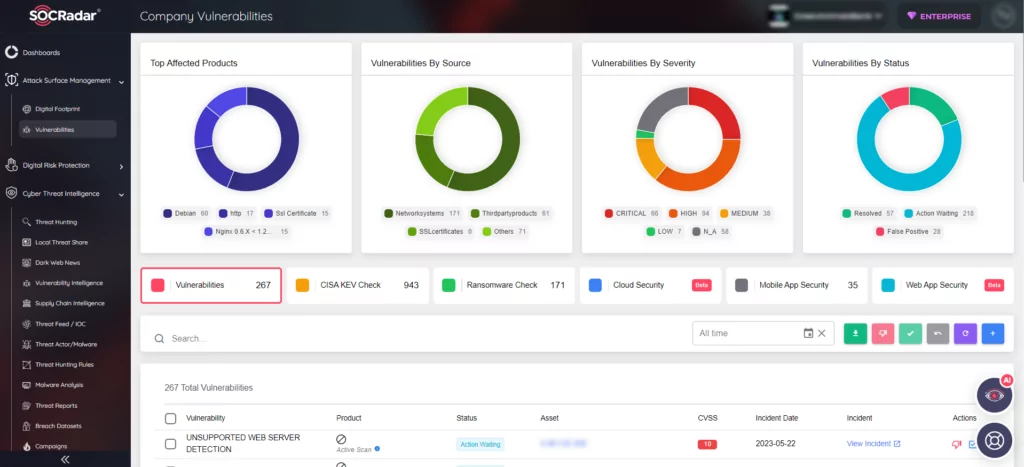
With SOCRadar’s Attack Surface Management, you gain the ability to continuously monitor vulnerabilities in the products detected within your organization’s digital footprint in real-time.
This empowers you to stay informed about the vulnerabilities that are targeted by threat actors, enabling you to gain actionable insights and contextual information for faster assessment and verification processes.