
Critical RCE Vulnerability in Microsoft RPC Could Be a Big Issue
The critical RCE vulnerability in the Microsoft RPC (Remote Procedure Call) communication protocol raises concerns among cybersecurity experts. A patch was released on April Patch Tuesday for the vulnerability with CVE-2022-26809 and a CVSS score of 9.8.
Cybersecurity researchers point out that any command with the same privilege level as the RPC server can be executed and allow full admin access when the vulnerability is exploited.
The vulnerability provides ideal conditions for threat actors to perform the lateral movement on the network. This supports the view that ransomware gangs will frequently exploit it in the future.
How Does the Vulnerability Affect?
Microsoft Remote Procedure Call (RPC) allows processes to communicate with each other even if they are running on another device. It uses ports 445 and 135 of the RPC hosts to accomplish this. This makes it easier for threat actors to spread through the system once they reach the RPC server.
Cybersecurity researchers are almost sure that this vulnerability will be exploited widely. They think that something similar to the Blaster worm in 2003 and the Wannacry attacks in 2017 could happen.
Who is Vulnerable?
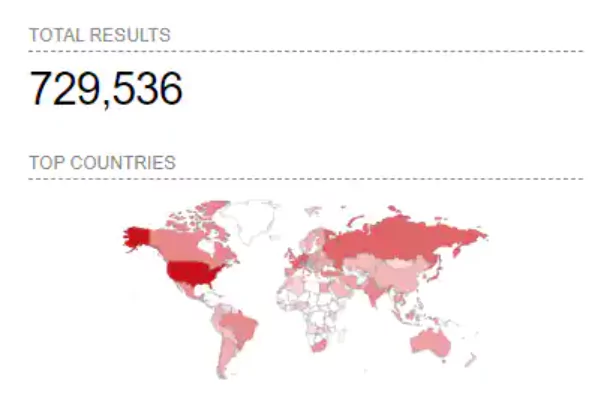
All unpatched Windows machines with port 445 open to the internet are currently vulnerable. According to Shodan, over 700,000 Windows machines expose to the internet with this port.
Antoni Cocomazzi of Sentinel One explained that the vulnerability was successfully exploited on a private RPC server.
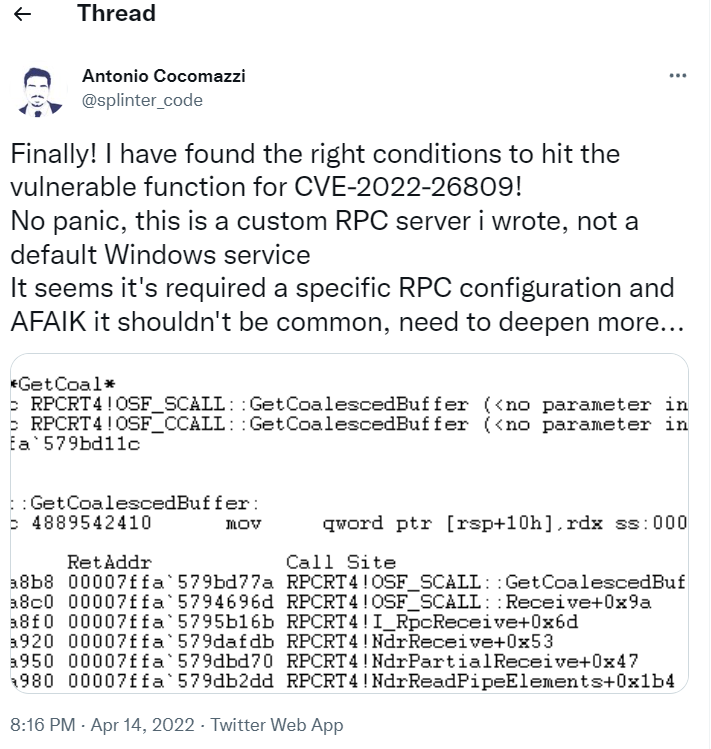
It is still unclear what conditions must meet for the vulnerability to be exploited. The researchers continue the analysis process.
Third-Party Apps May Also Be Affected
The fact that the vulnerable “rpcrt4.dll” is used not only by Microsoft services but also by many other applications suggests that the vulnerability may also affect third-party applications. Even if Windows ports are closed, backup services, antivirus programs, and endpoint software may be vulnerable.
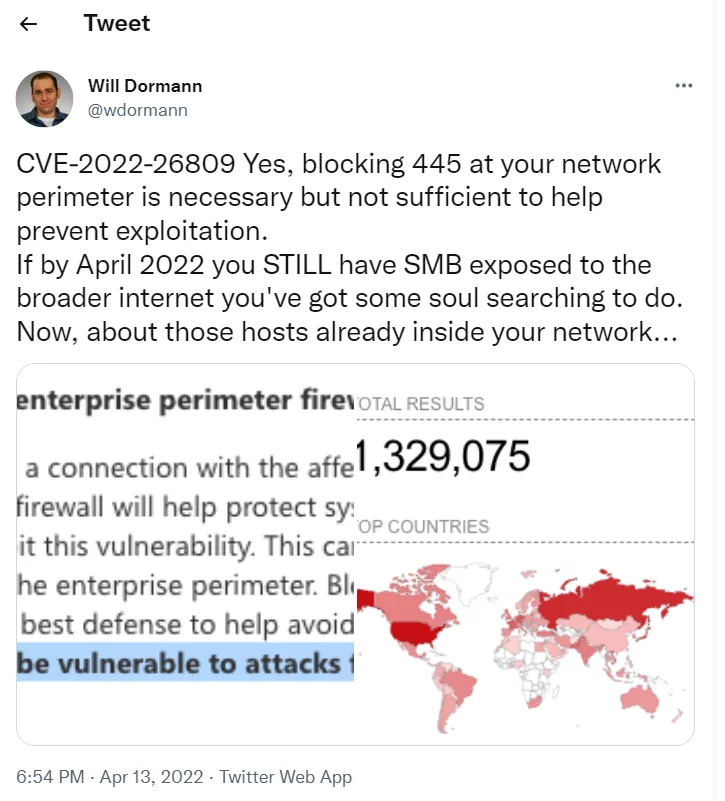
Microsoft’s security updates are strongly advised to be applied urgently for this and other vulnerabilities.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.


































