
Critical Vulnerabilities in Exim Email Server Allow RCE
Two critical vulnerabilities discovered in the open source email server Exim threaten over 500,000 email servers. One of the vulnerabilities allows RCE.
POCs Published
The critical vulnerability, code CVE-2022-37452, allows threat actors to execute commands on the email server with root privileges. The “buffer overflow” flaw allows attackers to view, modify, and delete data when exploited. It allows attackers to install programs and create new privileged accounts. The PoC can be found on GitHub.
The second vulnerability is CVE-2022-37451, caused by the “invalid free” in pam_converse (auths/call_pam.c). Because store_free is not used after store_malloc. The PoC for this vulnerability can also be found here.
Which Exim Versions Affected by the Vulnerabilities?
Cybersecurity researchers underline that these vulnerabilities can significantly affect government and commercial organizations. CVE-2022-37452 affects Exim versions before 4.95, and CVE-2022-37451 affects versions before 4.96.
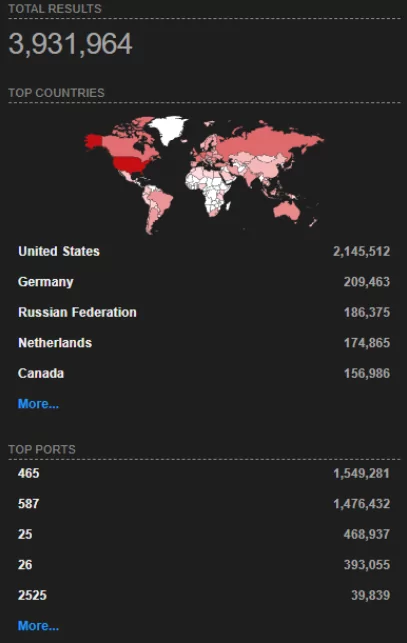
Exim is one of the most popular email servers used on Unix-like systems. According to Shodan, it has close to 4 million users, mainly in the US.
How to Fix the Vulnerability?
Experts recommend applying Exim’s updates to fix the vulnerabilities. In addition, organizations must renew their vulnerability management procedures for their digital assets.
Some mitigation methods are:
- Implement restrictions -such as adding a software allowlist- to ensure that only authorized software is run or accessed.
- Only allow specific files (.dll, .ocx, .so, etc.) to load and make sure to block unknown scripts.
- Establish a vulnerability management process for corporate digital assets.
- Use automatic patch management to perform monthly or regular application updates on digital assets.
- Prefer solutions that will automatically scan internal company assets for vulnerabilities.





































