Critical WooCommerce Vulnerability Enables Admin Privileges on WordPress Sites (CVE-2023-28121)
Researchers have observed an active exploit campaign targeting a newly disclosed vulnerability, CVE-2023-28121, in WooCommerce Payments plugin. There are more than 600,000 WordPress websites that use the plugin.
Notably, this targeted exploit campaign distinguishes itself from typical large-scale campaigns that indiscriminately attack numerous websites. Wordfence, a web application firewall for WordPress sites, observed that this campaign focuses on a smaller subset of websites.
What Is the Vulnerability in WooCommerce Payments?
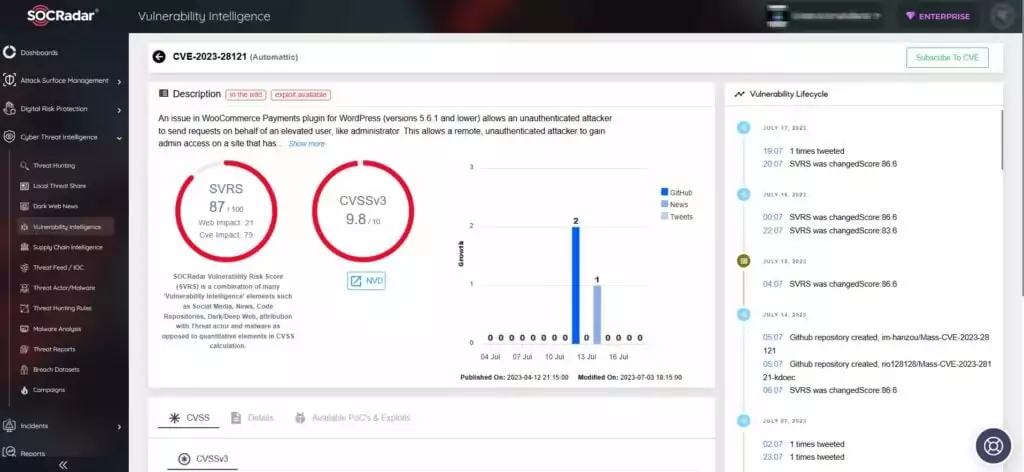
The critical vulnerability, identified as CVE-2023-28121, has a CVSS score of 9.8. Successful exploitation of CVE-2023-28121 allows unauthorized attackers to gain administrative privileges on vulnerable WordPress websites.
Affected Versions of WooCommerce Payments Plugin
Specifically, versions 4.8.0 to 5.6.1 of the WooCommerce Payments plugin are susceptible to exploitation.
Details of the WooCommerce Exploit Campaign
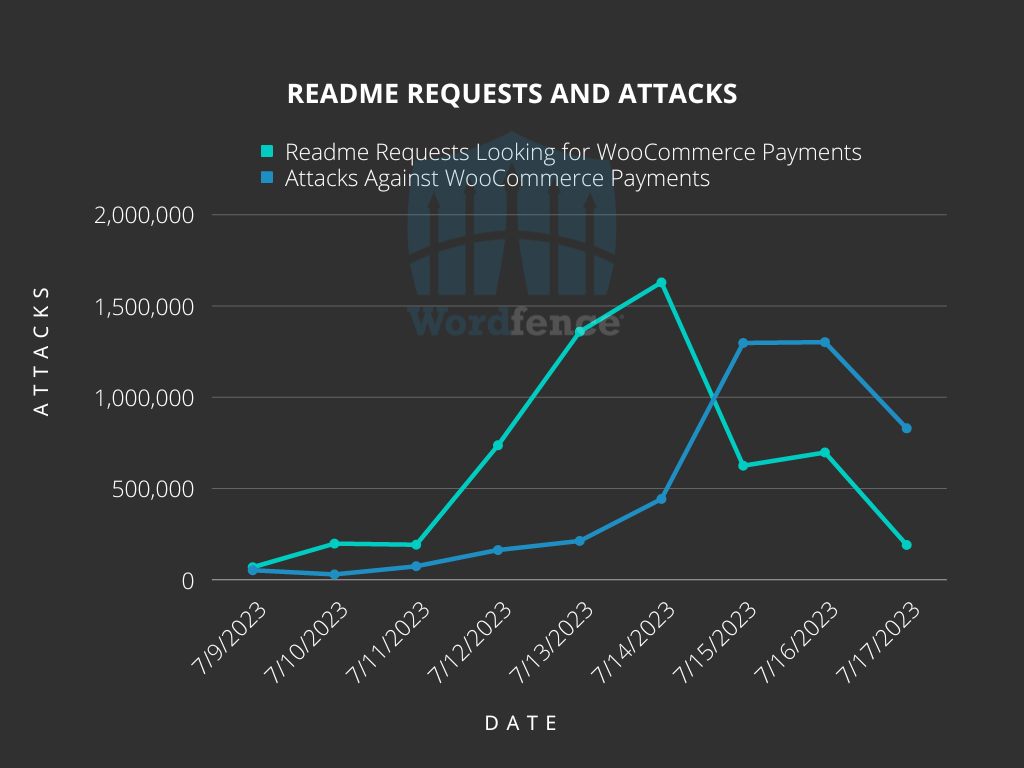
The campaign began on July 14, 2023, gained momentum, and peaked on July 16, with 1.3 million attacks targeting 157,000 websites.
Researchers report that they detected signs of impending attacks several days in advance through an increase in plugin enumeration requests. These requests searched for a specific file, readme.txt, within the wp-content/plugins/woocommerce-payments/ directory on millions of sites.
Although not all scans targeting readme.txt files are malicious, the surge in searches for a particular plugin slug typically indicates heightened interest from threat actors.
The majority of actual attacks originate from specific IP addresses, which have targeted a significant number of websites. Here are the IP addresses and the corresponding number of sites attacked:
| IP Address | Number of Sites Attacked |
| 194.169.175[.]93 | 213,212 |
| 2a10:cc45:100::5474:5a49:bfd6:2007 | 90,157 |
| 103.102.153[.]17 | 27,346 |
| 79.137.202[.]106 | 14,799 |
| 193.169.194[.]63 | 14,619 |
| 79.137.207[.]224 | 14,509 |
| 193.169.195[.]64 | 13,491 |
On the other hand, readme.txt requests were spread across multiple IP addresses. While nearly 5,000 IP addresses were responsible for both readme.txt requests and actual attacks, those IP addresses that solely sent readme.txt requests had attacked only a few or no sites. Therefore, these IP addresses are less valuable for defenders.
All attacks targeting the WooCommerce Payments vulnerability share a common header, which tricks vulnerable sites into treating additional payloads as if they were from an administrative user. This header is: X-Wcpay-Platform-Checkout-User: 1
Most requests using this header attempt to exploit their newly gained administrative privileges by installing the WP Console plugin. This plugin allows attackers to execute code on a site. Once the WP Console plugin is installed, malicious code is executed, and a file uploader is added to establish persistence.
Attackers have also been observed creating malicious administrator users with randomly generated alphanumeric usernames like ‘ac9edbbe’.
These attacks demonstrate a higher level of sophistication compared to previous similar attacks. They involve reconnaissance and utilize multiple methods to maintain persistence using functionalities available to administrators.
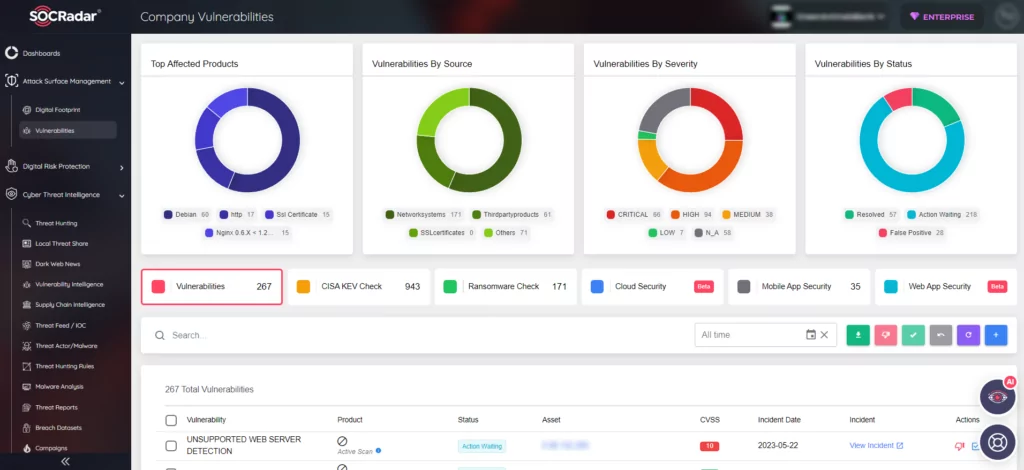
Stay Safe with SOCRadar
SOCRadar provides a valuable solution for keeping up with the most recent vulnerabilities and risks. Its Vulnerability Intelligence feature enables you to effectively handle vulnerability concerns and prioritize patching. You have the ability to search for and access comprehensive details about vulnerabilities directly on the platform.
Additionally, SOCRadar’s External Attack Surface Management (EASM) helps identify your digital assets and promptly notifies you of any emerging issues.