Essential Addons for Elementor WordPress Plugin Allows Privilege Escalation (CVE-2023-32243)
A popular WordPress plugin called Essential Addons for Elementor has a security vulnerability, tracked as CVE-2023-32243, which could allow hackers to gain administrator privileges on affected websites.
The plugin, which has over one million active installations, enables administrators to improve their Elementor page-building experience with more than 90 creative elements and extensions.
How Does the CVE-2023-32243 Vulnerability Affect WordPress Sites?
PatchStack researchers discovered that the vulnerability, CVE-2023-32243 (CVSS score: 9.8, Critical), exists in the Essential Addons for Elementor plugin’s password reset functionality and could allow an unauthenticated attacker to perform privilege escalation.
Versions 5.4.0 to 5.7.1 are affected by CVE-2023-32243.
The CVE-2023-32243 vulnerability arises because the password reset function does not validate a password reset key. Instead, it directly changes the password of the given user. This means that any user can escalate their privileges to that of any user on the vulnerable WordPress site, without requiring authentication.
Exploitation of the CVE-2023-32243 Vulnerability
The code for resetting user passwords does not properly check if the password reset key is present and legitimate. This means that a remote attacker could exploit the issue to reset the password of any existing user on the system, as long as they know the user’s username.
To exploit the issue, the attacker would first need to set a random value in the $_POST[‘page_id’] and $_POST[‘widget_id’] variables. This is to prevent the code from displaying an error message.
The attacker would then need to set the $_POST[‘eael-resetpassword-nonce’] variable, which is used to verify the authenticity of the request.
Finally, the attacker would need to enter the same password in the $_POST[‘eael-pass1’] and $_POST[‘eael-pass2’] variables.
If all of the above conditions are met, the code will create a $rp_login variable from $_POST[‘rp_login’].
The code will then search for the username value that matches the $rp_login variable and construct a $user object using the get_user_by function.
The code will utilize the reset_password function to reset the user’s password if the $user object is present and there are no errors.
The nonce value of essential-addons-elementor can be obtained from the front-end page of the website because it is set in the $this->localize_objects variable by the load_common_asset function.
If this vulnerability is exploited, attackers can gain control of the website and use it for malicious purposes such as distributing malware or redirecting traffic.
Patch Available for CVE-2023-32243
The vendor has fixed the CVE-2023-32243 vulnerability in version 5.7.2 of the plugin, released on May 11, 2023. Users of Essential Addons for Elementor are advised to update to the latest version of the plugin as soon as possible to protect their WordPress websites from the security vulnerability.
How Can SOCRadar Help with Vulnerability Management?
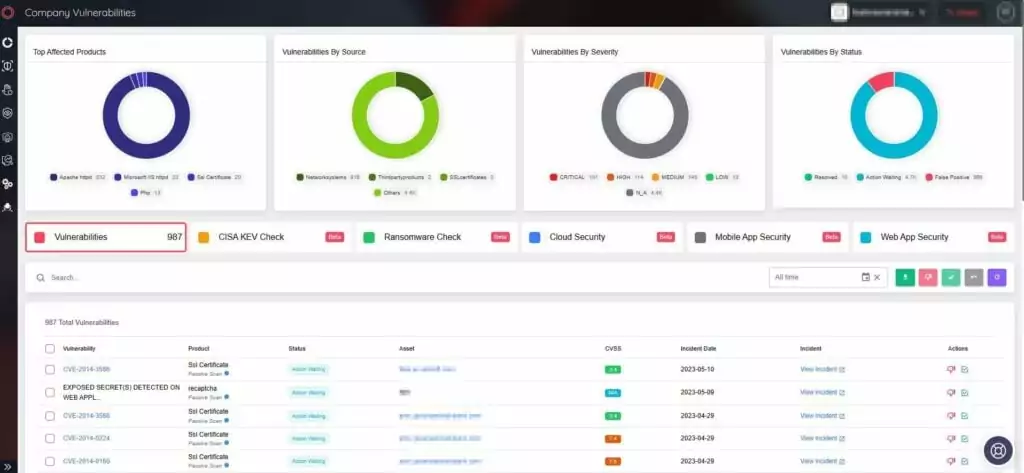
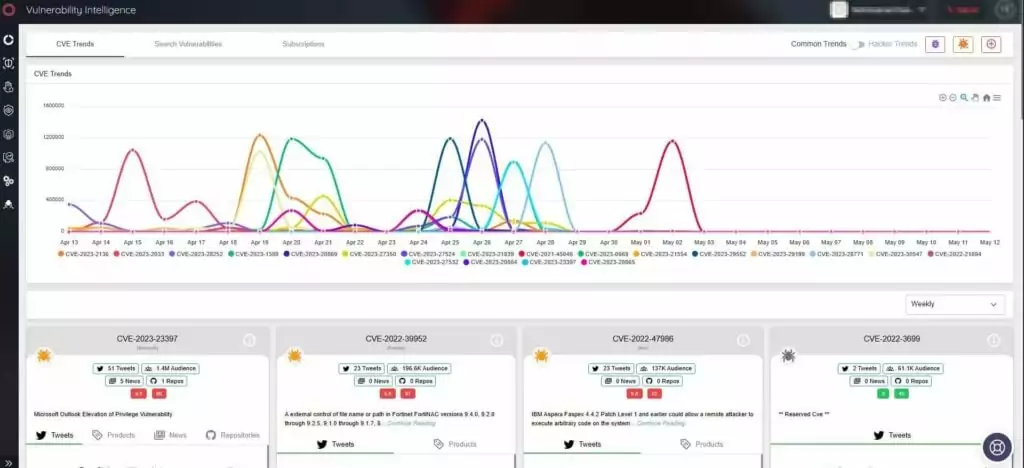
SOCRadar’s Vulnerability Intelligence tracks vulnerabilities and provides you with the actionable intelligence required to mitigate them. On the platform, you can look up a vulnerability’s CVE identifier and get detailed information about it, as well as see which vulnerabilities are popular among hackers.
The platform continuously monitors organizational assets for vulnerabilities and threats, assisting you in remediating them in your organization’s IT infrastructure. You can see vulnerabilities affecting your assets on the Company Vulnerabilities tab and take action on them quickly and easily. You can prioritize patches and protect your organization from vulnerability exploitation by using the information provided by SOCRadar.