
Magecart Skimmer Attack Targets WooCommerce and Authorize.net Payment Gateway Plugin
Online transactions ease our daily lives but also pose a serious risk to both businesses and their customers. Magecart attacks are one of them. Magecart is a type of malware that can steal credit card information from eCommerce websites. This threat has now extended to WordPress environments, particularly those using WooCommerce.
WooCommerce is a popular, open-source eCommerce plugin for WordPress.
Recently, a client of Sucuri received a warning from their bank that their website may have been compromised. Unknown individuals fraudulently used their legitimate cards on their website over the holidays.
Upon investigation, researchers found that the compromise occurred through modifying files related to the client’s payment gateway, Authorize.net.
Authorize.net, which Visa owns, is a payment gateway that allows vendors to handle digital transactions.
How Did the Magecart Attack Take Place?
The attackers tampered with the primary file of the plugin (./wp-content/plugins/woocommerce-gateway-authorize-net-cim/class-wc-authorize-net-cim.php) and injected malicious code that steals payment information from users.
The code checks for user payment information and generates a random password to encrypt the payment details. The encrypted data is then dumped into an image file (.jpg) and made easily accessible.
Storing stolen credit card information in an image file is not a new technique, but usually, the information is saved in either plain text format or encoded as basic base64 data in most instances. So, cybersecurity researchers have seen this as a new trend.
What is concerning about this attack is that the attackers took additional steps to encrypt the data with a public key in PEM format and a randomly generated string, making it more difficult for fraud prevention officers or law enforcement to investigate the theft.
The Magecart skimmer also modified a Javascript file (/assets/js/frontend/wc-authorize-net-cim.min.js) to inject code into a section named dispatch_payment. The code carried two functions to get data from form elements on the page and to send data with specific attributes such as “billing” to WordPress. This way, attackers could intercept additional billing information besides credit card details, increasing the value of stolen credit card information.
Attackers Use Heartbeat API for Stealth
The attacker appears to have imitated the Heartbeat API to avoid detection while sniffing the billing information. Heartbeat is originally a WordPress API that provides real-time communication with the server. The attacker used an Ajax request within Heartbeat API in one of the functions in injected Javascript file to send data, which helped them bypass detection.
This skimmer malware attack shows that attackers can modify secure software to exploit a website. Continuous monitoring of file integrity could prevent such attacks.
Magecart Attack Employs Hunter Obfuscator
Threat actors often attempt to bypass security measures. In the Authorize.net attack, they used several techniques and the Heartbeat API for stealth.
Malwarebytes recently reported on a Magecart skimmer attack that used Hunter, a PHP Javascript obfuscator, to achieve stealth.
A code injection initiates the attacks by calling out to a remote URL, which loads the skimmer in payment checkout. The function(h,u,n,t,e,r) and a subsequent string are processed dynamically to return some instructions in the code’s “eval” section.
Decoding the obfuscated string yields a single line of Javascript with additional obfuscated code. This is the skimmer code, which includes HTML forms for credit card information fields. The fields are added to the original payment form on the site; however, the additional fields are in English, as opposed to the original language on the site, which is Spanish.
Recommendations
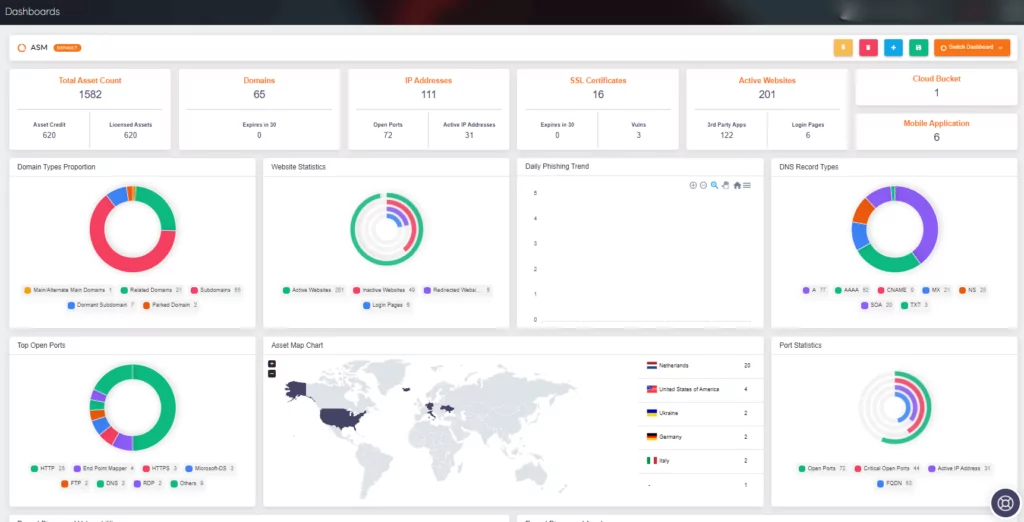
SOCRadar enables the detection of unauthorized and potentially harmful code injections by constantly monitoring automatically discovered client-side web assets, login pages, and forms. You can use SOCRadar alongside the following measures:
- Use Content-Security-Policy (CSP) with the use of nonces to whitelist JS and CSS files. This way, if there is even a slight change in the file, the injected JS file will not run and the attackers will not be able to achieve their objectives.
- Use Subresource Integrity (SRI) mechanism to take a hash of a secure file and whitelist it. This will prevent the file from running if any malicious change is made.
- Regularly check payment gateways and related files for any unauthorized changes or modifications.
- Keep payment gateway plugins and other software up-to-date with the latest security patches and updates.




































