
CrowdStrike Update Causing Blue Screen of Death and Microsoft 365/Azure Outage
[Update] August 7, 2024: “New Root Cause Analysis”
[Update] July 19, 2024: “Official Statement from the CrowdStrike CEO and the Possible Phishing Scenarios”
The tech world is now experiencing significant turbulence due to two major outages. The first involves CrowdStrike, whose latest update may have resulted in critical issues for many Windows users. The second pertains to a substantial outage affecting Microsoft 365 and Azure services in the Central US region. Here’s a detailed look at both events.
CrowdStrike Update Causes BSOD on Windows
CrowdStrike’s latest update has caused unexpected and severe problems for many Windows users. Comments indicate that the update has led to the dreaded Blue Screen of Death (BSOD), rendering many systems unusable.
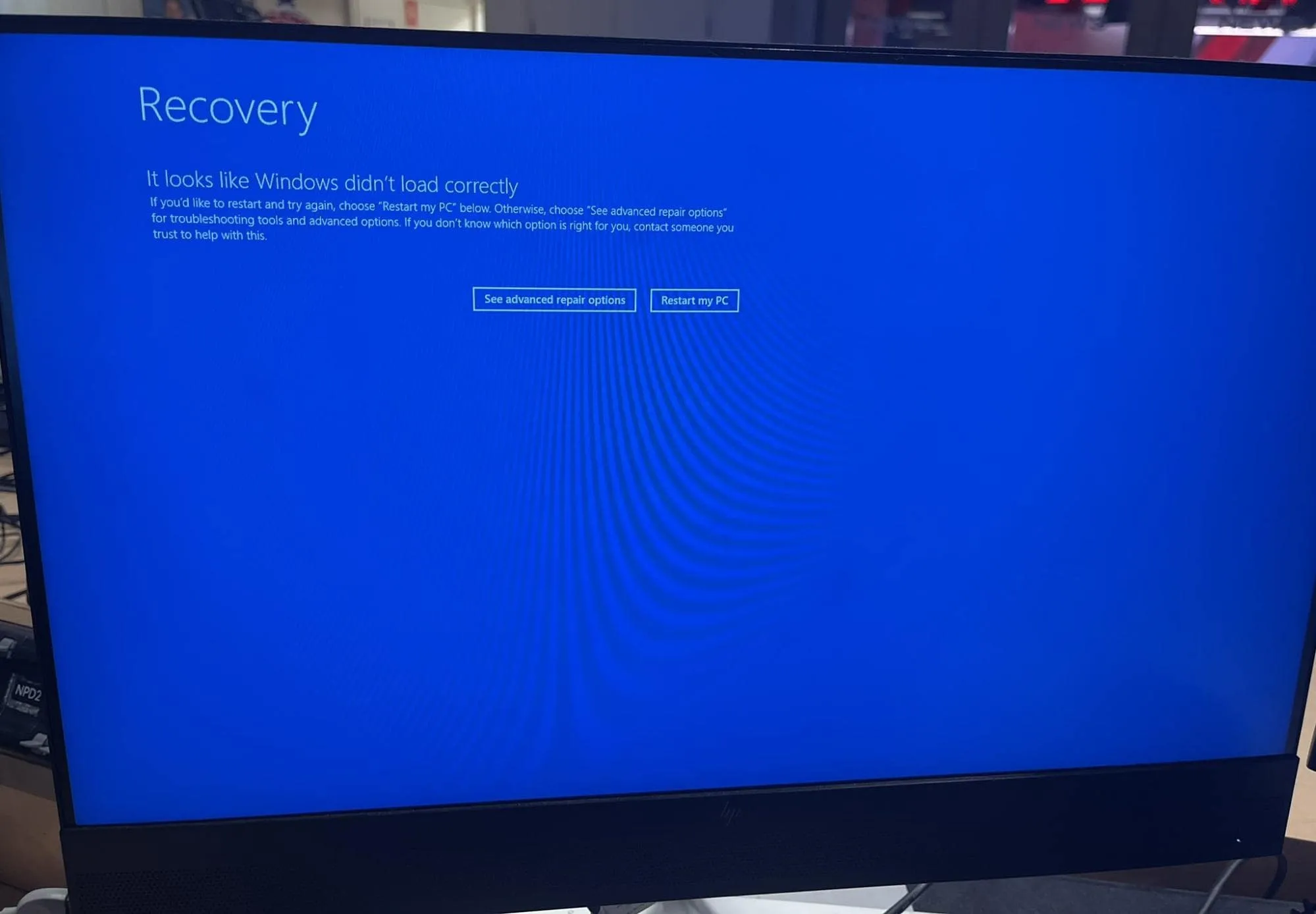
BSOD probably caused by CrowdStrike agent, (Troy Hunt’s post on X)
This issue began to surface shortly after users installed the update, causing widespread frustration and operational disruptions.

Many companies were experiencing downtime (@RMXD on X)
The BSOD typically occurs during the system boot, preventing affected computers from starting correctly. CrowdStrike has acknowledged the problem and is diligently working on a fix to resolve the issue. Meanwhile, users are advised to avoid installing the latest update until a resolution is available.
CrowdStrike has provided steps to mitigate the impact for those already affected, including booting into safe mode and uninstalling the problematic update.
There are also emerging manual solutions to address this boot problem, but please exercise caution if you’re unsure of what you’re doing.
Update: A semi-official workaround has been shared in a post on X by a director at CrowdStrike, as follows;
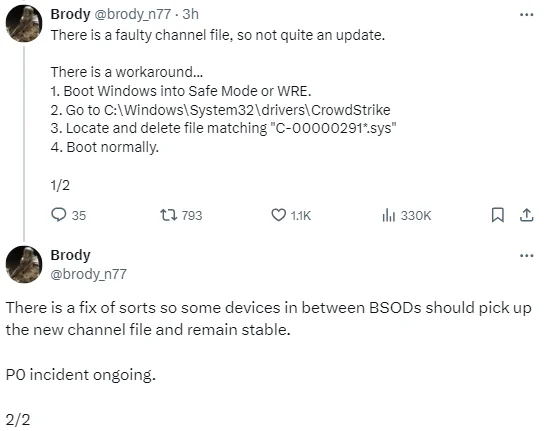
Director of OverWatch at CrowdStrike – Post on X (formerly Twitter)
- Boot Windows into Safe Mode or WRE.
- Go to C:WindowsSystem32driversCrowdStrike
- Locate and delete file matching “C-00000291*.sys”
- Boot normally.
Official Statement from the CrowdStrike CEO and the Possible Phishing Scenarios
In response to the recent issues, CrowdStrike CEO has provided a statement to address customer concerns:
“CrowdStrike is actively working with customers impacted by a defect found in a single content update for Windows hosts. Mac and Linux hosts are not impacted. This is not a security incident or cyberattack. The issue has been identified, isolated and a fix has been deployed. We refer customers to the support portal for the latest updates and will continue to provide complete and continuous updates on our website. We further recommend organizations ensure they’re communicating with CrowdStrike representatives through official channels. Our team is fully mobilized to ensure the security and stability of CrowdStrike customers.”
Apart from the statements, there may have been possible phishing scenarios related to the outage.
Beware of Phishing Scenarios
While malicious actors have no trustworthy interest in the subject for now, such social engineering attacks may occur. It is crucial to be especially vigilant against phishing attacks. Cybercriminals may exploit this situation by sending emails or messages that appear to be from CrowdStrike or other trusted sources. These phishing attempts can trick users into revealing sensitive information or downloading malicious software. Always verify the authenticity of communications by contacting CrowdStrike representatives through official channels.
Workarounds and Potential Issues
Several workarounds like the above one have been shared to address the Blue Screen of Death issue, but these only apply when booting Windows into safe mode. However, there are significant challenges:
- Lack of Admin Access: End users typically do not have administrative access, which is required to boot Windows into safe mode. This limitation makes it difficult to remotely restore functionality for hundreds of staff computers.
- BitLocker Complications: For organizations using BitLocker, resolving the issue may involve reading admin or BitLocker keys over the phone, adding another layer of complexity.
Given these challenges, knowing about potential vishing (voice phishing) attacks is essential. Cybercriminals might exploit the situation by pretending to be IT support staff or other trusted figures, attempting to extract sensitive information over the phone.
New Root Cause Analysis
CrowdStrike has released a detailed root cause analysis of the technical mishap behind the software update crash. The analysis reveals that the Falcon EDR sensor crash was caused by a combination of security vulnerabilities and process gaps:
- A mismatch between validated inputs and those provided to the Content Interpreter.
- An out-of-bounds read issue in the Content Interpreter.
- The absence of a specific test.
The crash occurred due to an out-of-bounds memory read when the Content Interpreter attempted to access more values than expected. The company has vowed to work with Microsoft on improving secure and reliable access to the Windows kernel. Future updates will leverage new support for security functions in user space to reduce reliance on kernel drivers.
CrowdStrike has also engaged two independent third-party software security vendors for an extensive review of the Falcon sensor code and the end-to-end quality process.
Microsoft 365 and Azure Outage in Central US
In another significant disruption, Microsoft 365 and Azure services experienced a considerable outage affecting users in the Central US region. This outage has led to widespread service interruptions, impacting businesses and individuals who rely on Microsoft’s cloud services for their daily operations.
The outage began on July 18, 2024, affecting many services, including email, cloud storage, and various enterprise applications. Microsoft has been actively investigating the cause of the outage and working to restore services as quickly as possible.
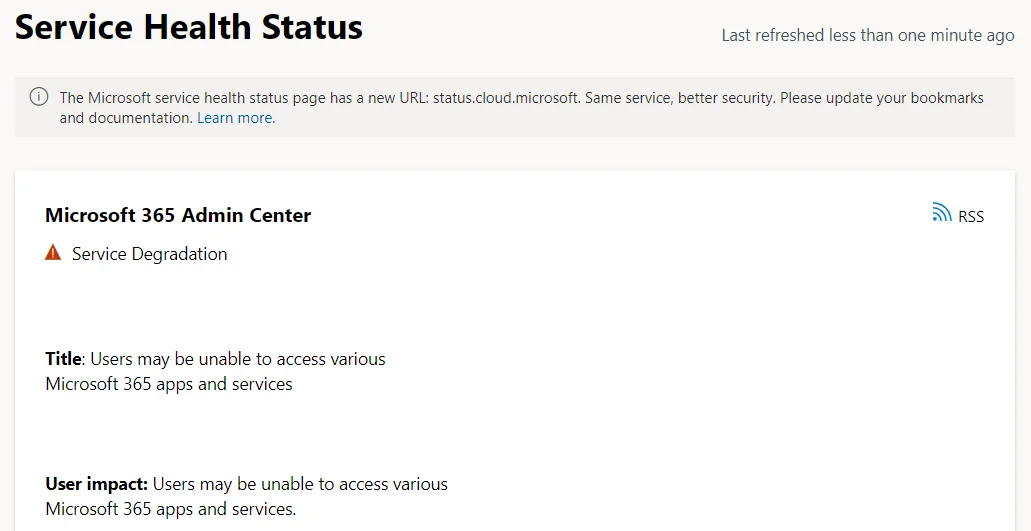
Central US is operational again, but issues with Office apps persist by the time of writing (Microsoft)
Preliminary reports suggest that the issue may be related to network configuration changes, but a detailed root cause analysis is still pending. Users are advised to monitor Microsoft’s official channels for updates on service restoration and any potential workaround solutions.
As availability is as important as confidentiality and integrity, these outages are also threats to cyber safety. Thus, the CrowdStrike update and the Microsoft 365/Azure outage highlight the challenges and vulnerabilities in the cyber world.
Protect your digital assets with SOCRadar’s Vulnerability Intelligence. Get instant alerts and actionable insights to safeguard against potential threats.
Organizations and users alike must stay informed about these outages, follow recommended mitigation steps, and prepare for potential disruptions by having robust contingency plans. As both companies work towards resolving these issues, it is essential to stay updated through official communications and support channels.


































