curl Update Available for CVE-2023-38545 and CVE-2023-38546: High-Severity Vulnerability Could Lead to RCE
[Update] November 15, 2023: See the subheading “curl and libcurl Vulnerabilities Have Been Fixed in Fortigate; CISA Issues Alert”
curl recently received an update that addressed two critical vulnerabilities in the curl data transfer library, identified as CVE-2023-38545 and CVE-2023-38546. Successful exploitation of these vulnerabilities could enable code execution and cookie injection.
Details of curl Vulnerabilities
CVE-2023-38545 (CVSS score: 7.5, High severity):
CVE-2023-38545, a heap-based buffer overflow vulnerability in SOCKS5, can potentially result in Remote Code Execution (RCE). It impacts both the curl command-line tool and libcurl.
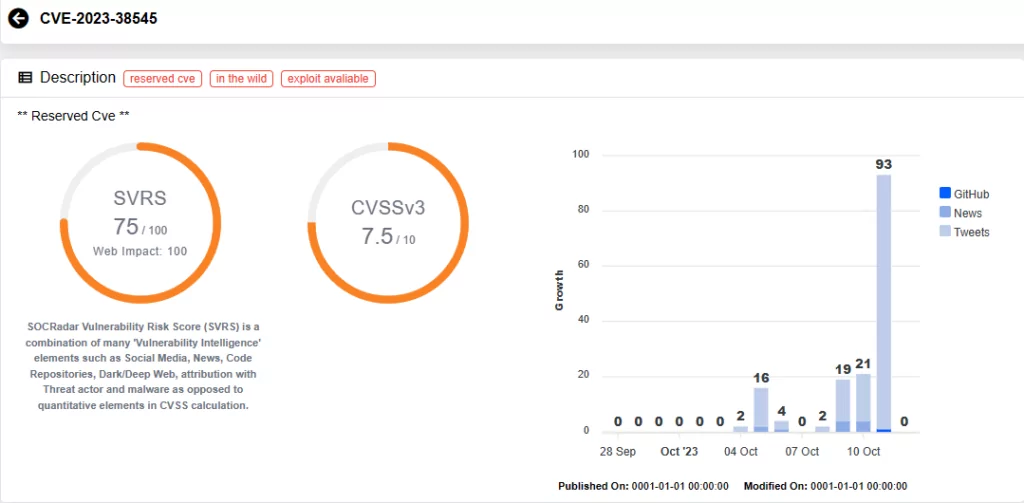
Researchers reported that curl version 7.69.0 introduced CVE-2023-38545 while attempting to convert a blocking function into a non-blocking state machine. The vulnerability essentially arises from a logic issue in the state machine, which represents a fallback mechanism when it handles excessively long host names in SOCKS5 proxy connections.
This vulnerability occurs when curl exceeds the 255-byte limit for the hostname during the SOCKS5 proxy handshake. Instead of properly passing on the resolved address to the proxy, CVE-2023-38545 may cause curl to copy the overly long hostname to the target buffer.
Numerous exploit codes are available on GitHub, proving how the vulnerability can be exploited in a Denial-of-Service (DoS) attack.
According to curl, exploitation is possible, even without a DoS attack, and a malicious HTTPS server redirecting to a specially crafted URL can trigger an overflow. Even so, researchers believe that the conditions required for a system to be vulnerable are more restrictive than initially thought, meaning most users are unlikely to be affected by the issue.
CVE-2023-38546 (CVSS score: 5.0, Medium severity):
In the advisory, the vulnerability is characterized as a cookie injection issue with none file. It enables an attacker to inject cookies into a running program using libcurl, provided that the specific series of conditions is met.
Which Versions of curl are Affected?
Below are the affected versions of libcurl for each vulnerability:
CVE-2023-38545: libcurl versions 7.69.0 to and including 8.3.0
Apply the Patches for curl
Version 8.4.0 of curl is available, providing patches for the CVE-2023-38545 and CVE-2023-38546 vulnerabilities.
This update, released on October 11, 2023, effectively mitigates the vulnerabilities, eliminating the behavior of curl switching to local resolve mode when a hostname exceeds the allowed length. It is strongly recommended to apply the update promptly to prevent the exploitation of these high-risk vulnerabilities.
See the release note here.
curl and libcurl Vulnerabilities Have Been Fixed in Fortigate; CISA Issues Alert
Fortinet has released several advisories for vulnerabilities in FortiClient and FortiGate, which include the curl and libcurl CVE-2023-38545 and CVE-2023-38546 vulnerabilities.
CISA has shared these advisories in an alert, highlighting the potential exploitation by threat actors to take control of affected systems. Users and administrators are urged to review Fortinet security advisories and apply patches.
The Fortinet advisory for CVE-2023-38545 and CVE-2023-38546 explains how these vulnerabilities work, emphasizing their significance, and lists affected Fortigate versions. These vulnerabilities exclusively impact the FGT_VM64_KVM model of Fortigate, requiring authentication for exploitation. The impacted versions are as follows:
- FGT_VM64_KVM version 7.4.0 through 7.4.1
- FGT_VM64_KVM version 7.2.0 through 7.2.6
- FGT_VM64_KVM version 7.0.1 through 7.0.13
Fortinet has addressed these vulnerabilities in various branches of its affected product. Users are advised to upgrade to FGT_VM64_KVM versions 7.4.2 or above, or versions 7.2.7 or above.
How Can SOCRadar Help?
SOCRadar continuously monitors security vulnerabilities, providing the timely intelligence necessary to safeguard organizational assets. Using Vulnerability Intelligence, you can search for vulnerabilities, obtain comprehensive details about them, and monitor related activities, including hacker trends.
Moreover, through the Attack Surface Management module, you can access critical information regarding vulnerabilities that impact your assets.