
Custom GPTs for Vulnerability Management: Harness the Power of AI in Cyber Defense
Artificial intelligence (AI) stands as a multifaceted force, shaping the future of both defense and offense in the cyber realm. As technology advances, threat actors adeptly leverage AI for malicious purposes, crafting sophisticated malware and phishing attacks that challenge traditional security measures. Illustrating this threat is the proof-of-concept AI malware, BlackMamba, signaling a new era where AI-generated threats encompass data theft, system manipulations, and unauthorized code execution. The evolving and adaptable nature of AI-generated malware presents a formidable challenge to conventional security software, making detection and removal increasingly elusive.
Beyond the ominous shadow cast by cyber criminals, there exists a parallel narrative where defenders harness AI to fortify their arsenals. In this paradigm, security researchers and blue team professionals leverage AI bots to enhance their operations and proactively address emerging threats. Microsoft’s Security Copilot, fueled by GPT-4, stands as a testament to AI’s prowess in cybersecurity. Tailored for incident response teams, Security Copilot rapidly detects and reacts to potential security threats by analyzing vast datasets.
While there are projects that exemplify AI’s impact, much like BlackMamba and Security Copilot, there is an even more convenient way to harness the power of AI in daily cybersecurity practices. Enter Custom GPTs, user-created AI language models finely tuned for specific needs – in our case, cybersecurity needs. The custom GPTs offer a streamlined and accessible approach to integrating AI into everyday security operations, providing a user-friendly solution to bolster defenses.
You can gain a better understanding of the cybersecurity battles in AI by reading our other blog post, titled “AI vs. AI: Future of the Cybersecurity Battles”; meanwhile, in this blog post, we will delve into how else AI, in the lead of custom GPTs, can be used in the field of cybersecurity, to actively fight the security threats.
AI’s Impact Across Cybersecurity Domains
As we delve into the intricate interplay between AI and cybersecurity, the narrative extends; AI can be a powerful ally in various domains of security, offering advanced capabilities to fortify defenses and proactively respond to emerging threats. Here’s a closer look at how AI can be leveraged across key cybersecurity efforts:
- Malware Detection:
AI algorithms analyze data to detect patterns indicative of cyber threats, enhancing the effectiveness of malware detection beyond traditional methods.
- Phishing Prevention:
AI-driven solutions analyze email content and user behavior to identify potential phishing attacks, surpassing the limitations of rules-based filtering.
- Log Analysis:
AI-based systems use machine learning algorithms to analyze large volumes of security log data in real-time, detecting patterns and anomalies indicative of potential security breaches.
- Network Security:
AI monitors networks for suspicious activity, identifying unusual traffic patterns and unauthorized devices through anomaly detection.
- Endpoint Security:
AI-based solutions enhance endpoint security by analyzing behavior, detecting potential threats, and adapting to evolving cyber threats.
- Likewise, AI unleashes its power in Vulnerability Management:
In addition to its prowess in the aforementioned domains, AI can be an invaluable asset in Vulnerability Management. Its capabilities can streamline the identification, prioritization, and mitigation of vulnerabilities, ensuring a proactive defense against potential cyber threats.
Key Steps in Vulnerability Management
Vulnerability Management, a continuous and proactive process, serves as the frontline defense against cyberattacks and data breaches. This comprehensive effort involves just a few key steps:
- Identifying vulnerabilities through regular scans and assessments.
- Prioritizing vulnerabilities based on risk and potential impact.
- Implementing patches and updates to address identified vulnerabilities.
- Monitoring and validating the effectiveness of mitigation measures.
Custom GPTs: Catalysts for Innovation in Vulnerability Management
Recently announced during OpenAI DevDay on November 6, 2023, the custom GPTs, or GPT agents, cater to users seeking tailored solutions for their unique needs. With this advancement, users can easily create these GPTs without the need for coding.
Custom GPTs can be made publicly accessible or kept private, providing businesses with the flexibility to leverage the power of AI in a manner that aligns with their specific requirements and data sensitivities. This allows them to prepare and utilize GPTs with their own domain’s data while keeping the process secure and private.

In the domain of Vulnerability Management, the role of Custom GPTs becomes increasingly pivotal. These user-created AI language models, finely tuned to comprehend vulnerability concepts, offer unparalleled accuracy and efficiency in automating the vulnerability management process.
Below are some of the top pieces of this AI evolution in vulnerability management, tailored to decipher the nuances of vulnerability identification, risk assessment, and proactive mitigation.
When addressing vulnerabilities, our initial concern revolves around Common Vulnerabilities and Exposures (CVEs) and the process of identifying them. This entails obtaining detailed information about CVEs and determining whether they pose a threat to our systems or components, including any digital assets within our attack surface. Here are some GPT agents specifically trained to excel in understanding and handling CVE-related knowledge:
NVD – CVE Research Assistant:

- Expert in CVEs and cybersecurity vulnerabilities.
- Provides precise information from the National Vulnerability Database.
- Developed by vulmon.com.
CVEs:

- Enables the lookup of Common Vulnerabilities and Exposures (CVEs).
- Developed by ai.moda.
CyberGPT:
- Delivers the latest CVE details.
- Developed by Edward Prentice.
Strobes Intel AI:
- A cybersecurity GPT providing insights into the latest CVEs and exploits.
- Developed by strobes.co.
Let’s test the capabilities of Custom GPTs by seeking information about a recent CVE:
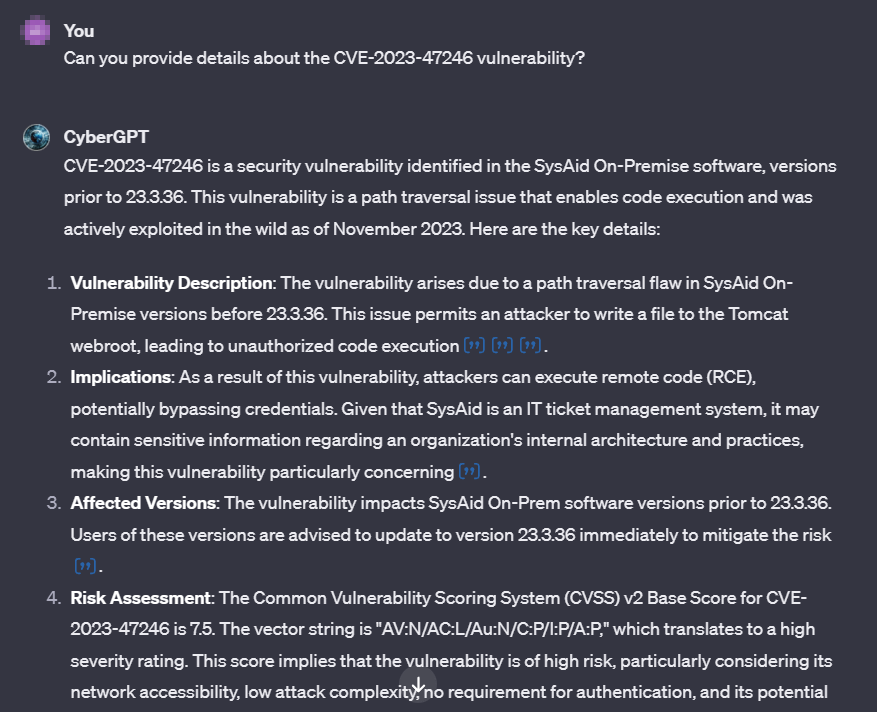
In the example above, CyberGPT delivers precise and up-to-date information regarding the SysAid vulnerability (CVE-2023-47246). While you can explore open information in detail and discuss it with GPTs, SOCRadar’s Vulnerability Intelligence offers a comprehensive summary, including the vulnerability timeline, exploits, and metrics when searching for the specific vulnerability card.
Moreover, SOCRadar’s Attack Surface Management (ASM) module complements specific vulnerability findings for a comprehensive identification and management approach. Cataloging external-facing assets like servers, domains, IPs, and applications, the ASM module allows cross-referencing with known vulnerabilities to identify potentially at-risk assets. It also ensures rapid identification of changes, such as new assets or modifications to existing ones. This proactive monitoring can alert you to vulnerabilities, like a server running a version of SysAid On-Premise software susceptible to CVE-2023-47246.
In the continuum of vulnerability management, the second crucial step involves prioritizing identified vulnerabilities. Attempting to address all vulnerabilities within the attack surface simultaneously is impractical, as it demands considerable resources and time. Allocating time to a vulnerability with a low likelihood of exploitation while a critical one persists poses a significant risk to assets vital to an organization, and is only a recipe for disaster. The strategic objective, therefore, is to concentrate resources on mitigating the most critical vulnerabilities first, thereby minimizing the risk of cyberattacks.
Typically, organizations can address a fraction of known vulnerabilities each month, ranging from 5% to 20%. Additionally, it is noteworthy that only a small subset (2%-7%) of published vulnerabilities is observed to be exploited in the wild.
The following GPT is designed for enhancing the prioritization process:
Vuln Prioritizer:

- Fetches EPSS scores for CVEs and provides prioritization summaries.
- Developed by Dino Dunn.
In our recent exploration of the Exploit Prediction Scoring System (EPSS), we highlighted its functionality in predicting the likelihood of a software vulnerability being exploited by evaluating various factors. This model conducts assessments based on historical data and environmental factors, referencing the Common Vulnerabilities and Exposures (CVE) database. It assigns scores grounded in risk, facilitating the prioritization of response efforts.
EPSS operates with continuous updates, leveraging the latest data to guide organizations in effective patch management and security strategies. While utilizing the EPSS API endpoint is a viable option for assessing vulnerability exploitability, it may be possible to streamline and enhance this process further with the assistance of a GPT agent equipped with EPSS and has knowledge about it.
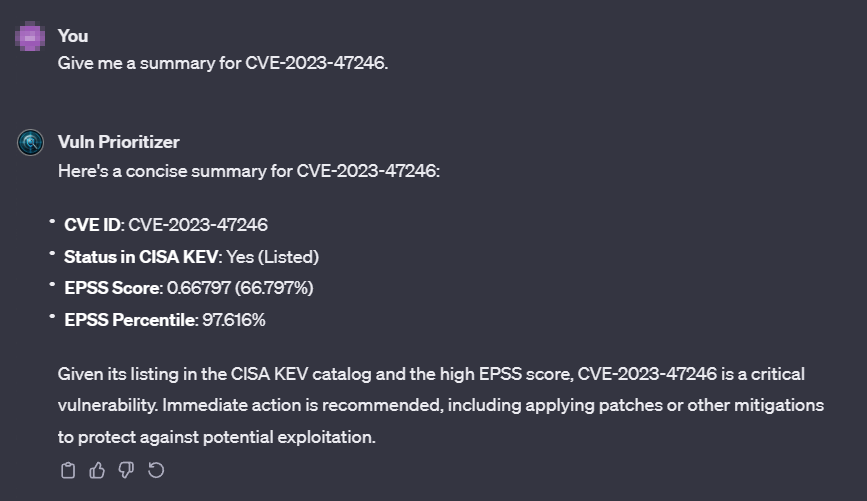
While EPSS is valuable in exploitation prediction, it is essential to recognize the evolving threat landscape, and its scope. To boost vulnerability prioritization accuracy, organizations can integrate SOCRadar Vulnerability Intelligence, featuring the SOCRadar Vulnerability Risk Score (SVRS).
SVRS gathers insights from diverse sources, like social media, news, and dark web, and vulnerability’s connection to threat actors and malware, offering a hacker’s perspective on a vulnerability’s popularity. Combining EPSS with SOCRadar Vulnerability Intelligence equips organizations to proactively address emerging threats, heightening the challenge for attackers to exploit vulnerabilities within the organization’s infrastructure.
Explore how SVRS enhances vulnerability management with EPSS in our related blog post:
The subsequent phase in vulnerability management involves the actual patching process: maintaining software and systems through updates, implementing patches, and addressing security vulnerabilities, particularly those prioritized earlier. Below are custom GPTs designed to facilitate this critical step.
Threat Model Companion:
- Assists in identifying and mitigating security threats.
- Developed by Matthew Johansen.
While it’s crucial to clarify that the model doesn’t autonomously implement patches, as that responsibility rests with us, it significantly aids in identifying and streamlining the mitigation process, serving as a guiding hand.
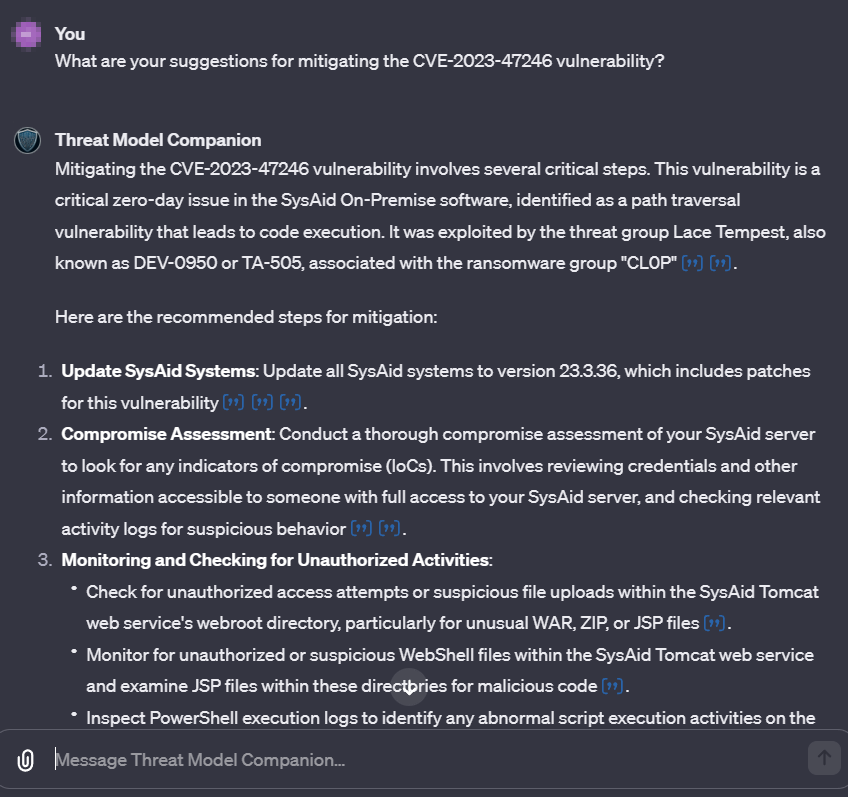
As demonstrated, the GPT provides vulnerability mitigation recommendations, including updates, assessment guides, and monitoring for unauthorized activities and indicators of compromise. It also provides additional recommendations on securing your environment against similar issues.
Fortunately, with the SOCRadar XTI platform, you can go beyond merely identifying vulnerabilities across your assets – you can receive real-time alerts and insights for any security issues or suspicious activities, staying informed about your organization’s security posture.
In the event of a detected vulnerability or breach, SOCRadar will immediately send out an alarm summarizing the incident. The alarms can seamlessly integrate with incident response protocols, providing essential information to initiate containment and remediation efforts.
Below is another custom GPT designed to offer valuable assistance in the domain of mitigation strategies:
Amelia: Cybersecurity Analyst:

- Specializes in threat identification, risk assessment, and security protocol development.
- Excels in fortifying networks and systems against cyber threats.
- Developed by microgpt.ai.
Amelia serves as a cybersecurity assistant, specializing in threat identification, risk assessment, and the development of security protocols. This GPT excels in the crucial task of fortifying networks and systems against cyber threats, providing yet another guiding hand in the ongoing efforts to enhance cybersecurity measures.
Here is another GPT to remind you the best practices in cybersecurity:
Systems Security Analyst:

- An expert in cybersecurity advice and best practices.
- Developed by Randy Blasik.
Yet, a GPT is not required to emphasize a foundational principle in cybersecurity: Always monitor your attack surface, encompassing everything digitally available and related to your organization, from devices and systems to software and accounts.
For robust monitoring, leverage SOCRadar’s Attack Surface Management (ASM) module. The Digital Footprint feature within ASM provides insights into the overall posture of your digital presence, while also offering detailed asset information and incident-related data.
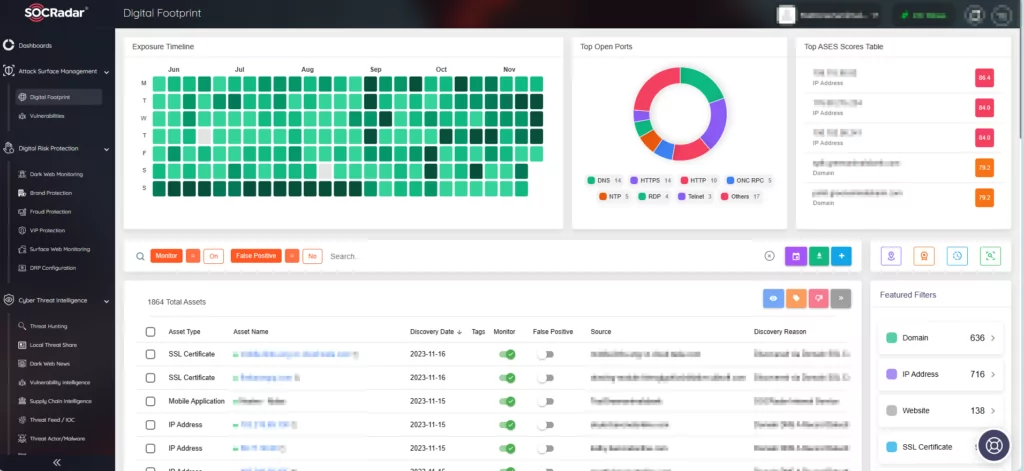
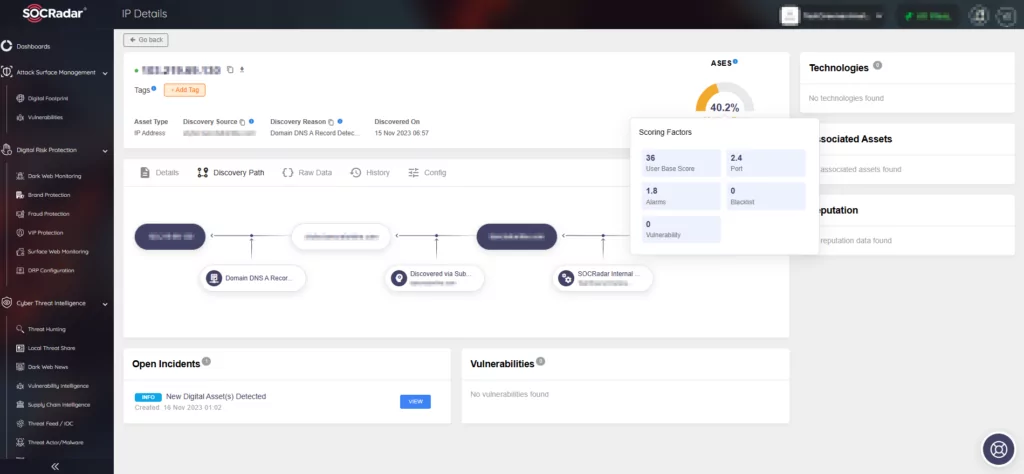
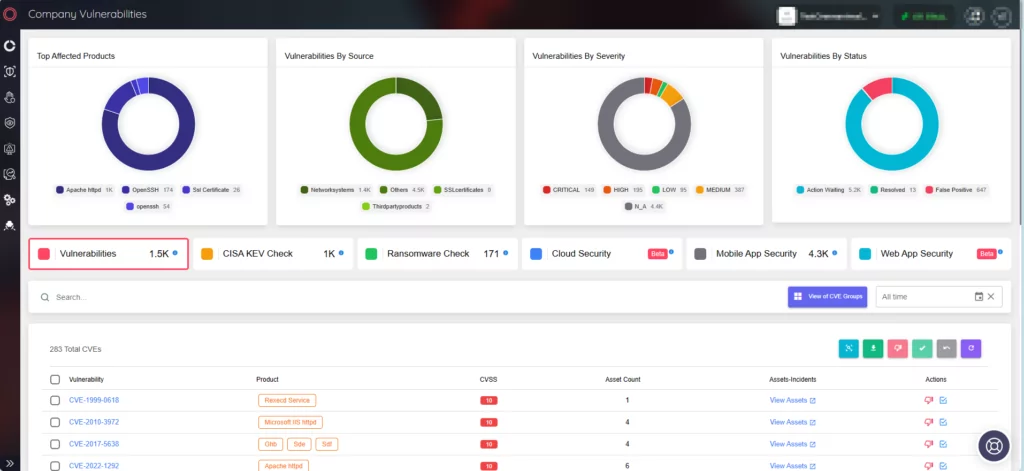
The Company Vulnerabilities page delivers crucial insights into vulnerabilities affecting your assets. Integrating SOCRadar into your security strategy ensures a comprehensive approach, enhancing defense mechanisms and proactive addressing of emerging threats with real-time alerts.
Conclusion – Role of Custom GPTs in Vulnerability Management
In summary, the interplay between Artificial Intelligence (AI) and cybersecurity signifies a dynamic force in the ongoing battle against cyber threats. Custom GPTs, born from user innovation, stand poised to revolutionize how vulnerabilities are identified, prioritized, and addressed, and offer a practical means to integrate AI into daily cybersecurity practices.
In Vulnerability Management, Custom GPTs could play a pivotal role, streamlining the identification, prioritization, and mitigation of vulnerabilities. Certain projects showcase AI’s capabilities in decoding vulnerability intricacies, while some can even facilitate the strategic prioritization of vulnerabilities, aligning with industry best practices, and help you in optimizing resource allocation and reducing the risk of cyberattacks.
As the vulnerability management journey progresses, Custom GPTs equipped with knowledge about various tools and resources, such as the EPSS model, could greatly improve efficiency in assessing vulnerability exploitability, and serve as guiding hands in fortifying systems.
In embracing Custom GPTs for Vulnerability Management, the integration of user-created AI models and cybersecurity promises a future where defenses against emerging threats become increasingly seamless and effective. The journey to harness the power of AI in cyber defense is not only underway; it is evolving, adapting, and fortifying the digital frontier.



































