
CVE-2023-22515: The Confluence Data Center and Server Vulnerability
[Update] November 13, 2023: New ‘Effluence’ Backdoor Targets Confluence Data Center and Server Upon Exploiting CVE-2023-22515 and CVE-2023-22518
[Update] October 12, 2023: See subheadings: “Storm-0062 APT Exploits Confluence Vulnerability (CVE-2023-22515)” & “Nuclei Template for CVE-2023-22515 is Available on Github.”
[Update] October 10, 2023: Read under “PoC and Root Cause Analysis Available for CVE-2023-22515 Vulnerability in Confluence.”
Recently, a security concern has caught the attention of the cybersecurity world – a privilege escalation vulnerability within the Confluence Data Center and Server. This flaw allows external attackers to exploit some Confluence instances, creating unauthorized administrator accounts and thereby gaining unrestricted access to the Confluence platform.
It is worth noting that Atlassian Cloud sites remain unaffected by this vulnerability. If you access your Confluence site through an atlassian.net domain, rest assured, it is hosted by Atlassian and remains invulnerable to this particular flaw.
Severity: Why the Confluence Vulnerability Is Critical
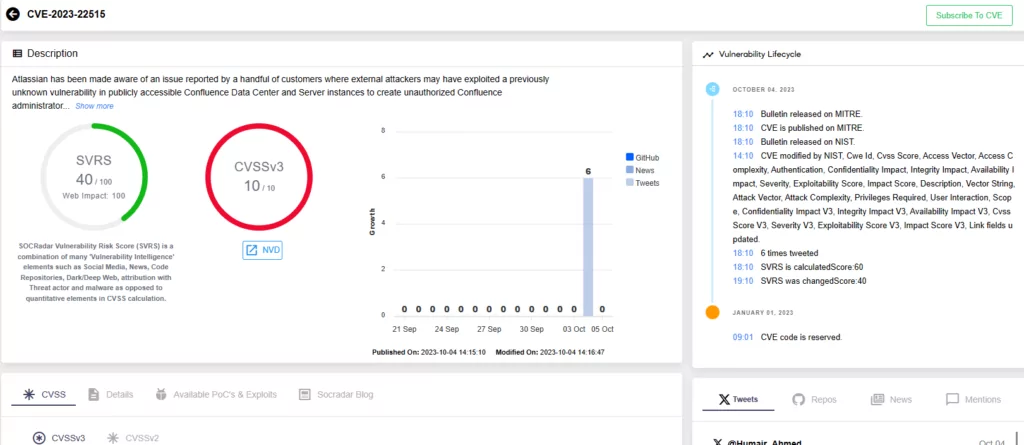
While NVD hasn’t assigned a score to this vulnerability as of yet, Atlassian rates it as ‘critical’. It’s a 10.0 on the CVSS scale, which is the highest possible score, indicating the severity and potential impact. The vulnerability is remotely exploitable, aligning more with an authentication bypass or remote code execution than a typical privilege escalation issue. For businesses and IT teams, understanding the severity is paramount in determining how urgently they need to respond.
Are You Affected by the Confluence Vulnerability?
Versions before 8.0.0 remain unaffected by this vulnerability. Furthermore, Atlassian Cloud sites remain immune to this issue. If your Confluence site is accessed through an atlassian.net domain, it is hosted by Atlassian and remains safe from this vulnerability. However, the subsequent versions of Confluence Server and Data Center are at risk:
- 8.0.0
- 8.0.1
- 8.0.2
- 8.0.3
- 8.0.4
- 8.1.0
- 8.1.1
- 8.1.3
- 8.1.4
- 8.2.0
- 8.2.1
- 8.2.2
- 8.2.3
- 8.3.0
- 8.3.1
- 8.3.2
- 8.4.0
- 8.4.1
- 8.4.2
- 8.5.0
- 8.5.1
Instances on the public internet are at an elevated risk, given the exploitability of this vulnerability even without authentication.
PoC and Root Cause Analysis Available for CVE-2023-22515 Vulnerability in Confluence
Researchers at PT Swarm have successfully reproduced the CVE-2023-22515 vulnerability in Confluence, demonstrating its urgency through a video they shared on Twitter, which essentially serves as a Proof-of-Concept (PoC) exploit.
Furthermore, Rapid7 researchers have outlined the vulnerability’s root cause in a recent analysis. They identified significant modifications to the class SafeParametersInterceptor through patch diffing, and suggest that classifying CVE-2023-22515 as an “Improper Input Validation” may be more appropriate than “Broken Access Control”, as the core issue appears to be a lack of proper filtering in the mentioned class.
In the analysis, it is explained that the vulnerability allows attackers to execute complex getter/setter chains on the Action object for unauthenticated endpoints, enabling them to modify critical properties. By modifying a related variable, attackers can exploit the setup functionality to create a new administrator user, as also shown in the PoC video.
Researchers warn that the vulnerability is not confined to specific endpoints, and there may be additional exploitation avenues beyond targeting /server-info.action.
For more comprehensive information, refer to the full patch diff and analysis here.
Storm-0062 APT Exploits Confluence Vulnerability (CVE-2023-22515)
Microsoft recently detected exploitation activity linked to the Confluence vulnerability (CVE-2023-22515), with attribution to an APT threat actor named Storm-0062.
Storm-0062, a nation-state threat actor associated with China’s Ministry of State Security, is also recognized by DarkShadow and Oro0lxy. Of note, DarkShadow and Oro0lxy are aliases of Chinese state hackers Li Xiaoyu and Dong Jiazhi, who are active since at least 2009 and were accused by US authorities in 2020 for probing vulnerabilities affecting companies involved in COVID-19 treatments.
The group is distinguished for its intelligence-gathering operations. Storm-0062 targets companies in a wide range of sectors, including software, medical research, government, and technology across various regions.
Microsoft disclosed that this threat actor has been actively exploiting CVE-2023-22515 in real-world scenarios since September 14, 2023.
In addition, Microsoft shared on Twitter (X) that it had observed exploit traffic related to CVE-2023-22515 originating from specific IP addresses:
- 192.69.90[.]31
- 104.128.89[.]92
- 23.105.208[.]154
- 199.193.127[.]231
Nuclei Template for CVE-2023-22515 is Available on Github
Nuclei template for the Confluence vulnerability is now accessible, allowing users to employ it with the Nuclei engine for the purpose of identifying the security vulnerability. You can find it on GitHub.
New ‘Effluence’ Backdoor Targets Confluence Data Center and Server Upon Exploiting CVE-2023-22515 and CVE-2023-22518
Researchers have discovered a stealthy backdoor, named Effluence, deployed after successfully exploiting vulnerabilities in Atlassian Confluence Data Center and Server. Threat actors can potentially exploit CVE-2023-22515 and CVE-2023-22518 to create unauthorized administrator accounts, subsequently initiating the malware attack.
The attack chain begins with the exploitation of CVE-2023-22515, permitting the creation of unauthorized Confluence admin accounts. This attack distinguishes itself with the innovative use of a web shell, which enables attackers to remotely access the backdoor without authenticating to Confluence with a valid account.
Triggered by a specific parameter, the web shell becomes active and enables various malicious actions, from creating admin accounts to gathering information, erasing files and logs, and executing arbitrary commands.
Researchers identified a loader component acting as a Confluence plugin, responsible for decrypting and launching the malware payload.
The Effluence backdoor reportedly persists even after patching for CVE-2023-22515 and CVE-2023-22518, allowing lateral movement and data exfiltration.
Interestingly, this malware’s plugin and loader, applicable to other Atlassian products, depend on common Atlassian APIs, offering flexibility for potential use in JIRA, Bitbucket, or similar environments. This highlights the potential for similar attacks across other Atlassian software.
For a detailed technical overview, refer to Aon’s blog on the Effluence backdoor.
Recommended Actions
For those running affected versions:
- Immediate Upgrade: Atlassian suggests upgrading to one of the following fixed versions:
- 8.3.3 or later
- 8.4.3 or later
- 8.5.2 (Long Term Support release) or later
- Mitigation: If upgrading is not feasible immediately, restricting external network access to the affected instance is recommended. Furthermore, known attack vectors can be mitigated by blocking access to the /setup/* endpoints on Confluence instances. Specific directions on doing this have been provided by Atlassian.
- Threat Detection: Engage your security team to check for indicators of compromise, such as unexpected members in the confluence-administrator group or unusual user account creations.
Conclusion
This vulnerability shows the significance of timely patch management and a proactive cybersecurity approach. We, at SOCRadar, consistently monitor such vulnerabilities to alert and guide organizations in making informed security decisions.
Stay vigilant and ensure your systems are regularly updated and checked for potential vulnerabilities.




































