
Atlassian CISO Announced: Improper Authorization Vulnerability Detected on Confluence Data Center and Server (CVE-2023-22518)
[Update] April 18, 2023: “Cerber Ransomware Exploits CVE-2023-22518 in Confluence Servers, Deploys Linux Variant”
[Update] November 8, 2023: CISA has included the CVE-2023-22158 vulnerability in Confluence Data Center and Server in its Known Exploited Vulnerabilities (KEV) catalog, setting the deadline for organizations to patch the vulnerability to November 28, 2023.
[Update] November 7, 2023: See the subheading: “Attackers Exploit CVE-2023-22518 to Deploy Cerber Ransomware in Confluence Data Center and Server.”
[Update] November 3, 2023: Atlassian has warned customers that a PoC exploit is available for the CVE-2023-22518 vulnerability affecting Confluence Data Center and Server.
In a recent discovery, Confluence Data Center and Server customers found themselves vulnerable to significant data loss due to an Improper Authorization Vulnerability, tracked as CVE-2023-22518. Luckily the issue has been discovered by Confluence Team and announced by the company’s CISO in a note with the details that there is no active exploitation observed so far.

What You Need To Know About CVE-2023-22518?
This critical issue has the potential to cause considerable harm to targeted organizations, with unauthenticated attackers able to exploit this vulnerability. While there are currently no reports of active exploitation, the urgency to mitigate this vulnerability is high. Although severity of the issue is high, there is not much information shared by the company; the thing that can be inferred from CVSS vectoral string assigned by Confluence is that, even after a successful exploitation, the vulnerability affects only availability and integrity of the server on which vulnerable software is installed.
Details of the Vulnerability
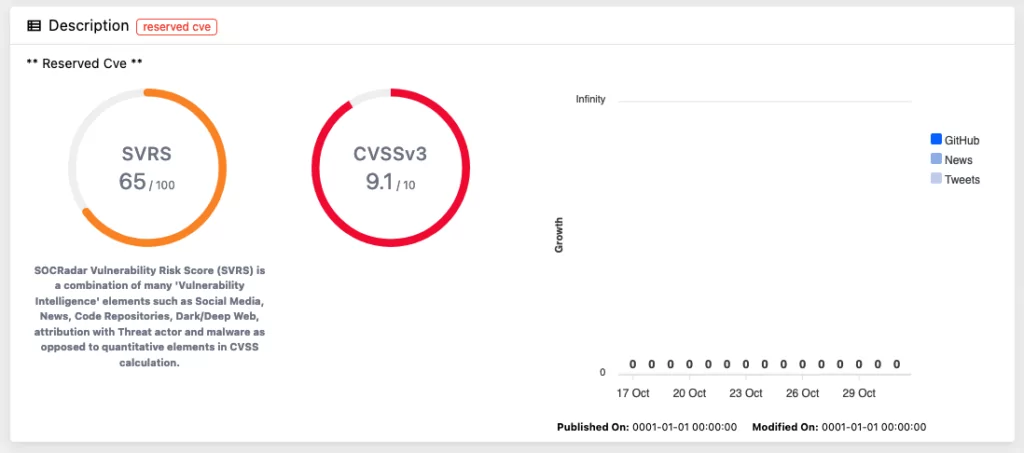
Confluence, developed by Atlassian, is a widely used platform for team collaboration and information sharing, with a diverse user base spanning various industries. The vulnerability in question, CVE-2023-22518, was identified and an advisory was issued on October 30, 2023, by Atlassian’s Chief Information Security Officer (CISO), Bala Sathiamurthy. The related Jira ticket for this issue is CONFSERVER-93142. This vulnerability affects all versions of Confluence Data Center and Server, with Atlassian’s Cloud sites being unaffected.
Which Versions of Confluence Data Center and Server Are Affected by CVE-2023-22518?
Users of Confluence Data Center and Server are at risk of significant data loss if this vulnerability is exploited. Previous investigations into similar vulnerabilities show that such flaws can provide attackers with unauthorized access to networks and systems. While there is no impact on confidentiality and attackers cannot exfiltrate any instance data, the potential risks of unauthorized system access and other harm are present. Atlassian has issued official statements urging immediate action to protect affected instances.
All versions of Confluence Data Center and Server prior to the following fixed versions are affected:
- 7.19.16 or later
- 8.3.4 or later
- 8.4.4 or later
- 8.5.3 or later
- 8.6.1 or later
Users are encouraged to apply these fixes as soon as possible and refer to the official advisory for patching instructions.
Is There a Proof-of-Concept (PoC) Exploit for CVE-2023-22518?
Atlassian has issued a warning about CVE-2023-22518 in its advisory. The company claims to have discovered critical information relating to the vulnerability, essentially a Proof-of-Concept (PoC) exploit, which has been made public.
There are currently no reports of this vulnerability being exploited in the wild or any attribution to specific threat actors.
As there are no reports of active exploitation, no additional incidents or data breaches have been reported as a result of this vulnerability.
Atlassian emphasizes the necessity for customers to take immediate action to safeguard their instances, as the discovery of the PoC exploit raises the risk of potential exploitation.
Attackers Exploit CVE-2023-22518 to Deploy Cerber Ransomware in Confluence Data Center and Server
Researchers have identified attempts to exploit the CVE-2023-22518 vulnerability, impacting both Windows and Linux systems. Their findings, dating back to November 5, reveal that some of these attempts involved ransomware deployment.
Researchers state that the process execution chain exhibits consistency across various environments, suggesting potential mass exploitation of vulnerable Confluence servers exposed to the internet. After successful exploitation of the vulnerability, it was observed that attackers downloaded payloads from remote servers, resulting in the deployment of the Cerber ransomware.
Cerber ransomware operates on the Ransomware-as-a-Service (RaaS) model, enabling affiliates to distribute the ransomware payload in exchange for a specified fee to its developer. In their research, Rapid7 has provided a list of indicators of compromise associated with CVE-2023-22518 exploitation activities involving the Cerber ransomware:
IP Addresses:
- 193.176.179[.]41
- 193.43.72[.]11
- 45.145.6[.]112
Domains:
- j3qxmk6g5sk3zw62i2yhjnwmhm55rfz47fdyfkhaithlpelfjdokdxad[.]onion
File Hashes:
- BAT file: /tmp/agttydcb.bat
- 81b760d4057c7c704f18c3f6b3e6b2c4 (MD5)
- ELF ransomware binary: /tmp/qnetd
- 4ed46b98d047f5ed26553c6f4fded7209933ca9632b998d265870e3557a5cdfe (SHA256)
Ransom Note:
- read-me3.txt
Cerber Ransomware Exploits CVE-2023-22518 in Confluence Servers, Deploys Linux Variant
Researchers recently uncovered a concerning development: Cerber ransomware is now leveraging the CVE-2023-22518 vulnerability to infiltrate Confluence servers, with its lesser-known Linux variant.
The attackers deploy Cerber by exploiting the CVE-2023-22518 vulnerability, which enables them to reset the Confluence application and create a new administrator account via an unprotected configuration restore endpoint used by the setup wizard.
This Linux variant of the ransomware family deploys three heavily obfuscated C++ payloads compiled as 64-bit ELF files, packed with the UPX packer, a favored tool among threat actors for evading detection by security software.
The main payload, like others, is UPX-packed. It orchestrates the environment setup and payload retrieval. Upon execution, it unpacks and attempts to create a file at /var/lock/0init-ld.lo, possibly as a lock file to prevent duplicate execution. However, existing lock files do not impede execution.
The main payload then connects to the now-defunct C2 server at 45[.]145[.]6[.]112, fetching the secondary payload known as ‘agttydck’. This is achieved through a simple GET /agttydcki64 request over HTTP, with the payload body written to /tmp/agttydck.bat.
Upon exploitation of CVE-2023-22518, attackers create an admin account to deploy the Effluence web shell plugin, granting them the ability to execute arbitrary commands on the vulnerable server. The primary Cerber payload is then downloaded and executed via the web shell.
Operating under the “confluence” user privilege, the ransomware encrypts files limited to the Confluence application’s datastore. However, if granted higher privilege, the scope of encrypted files would significantly broaden.
Additionally, the malware performs various malicious actions, including logging activity, searching for encryptable directories, dropping ransom notes, and encrypting files with a “.L0CK3D” extension. To conceal its presence, the malware ultimately deletes itself from the disk.
While Cerber poses a significant threat to compromised systems, the effectiveness of its ransom demands may be limited, particularly in well-configured systems with adequate backups.
Indicators of Compromise (IOCs)
The following are identified by Cado as indicators of compromise connected to the exploitation of CVE-2023-22518.
Hashes (SHA256):
- 4ed46b98d047f5ed26553c6f4fded7209933ca9632b998d265870e3557a5cdfe (cerber_primary)
- 1849bc76e4f9f09fc6c88d5de1a7cb304f9bc9d338f5a823b7431694457345bd (agttydcb)
- ce51278578b1a24c0fc5f8a739265e88f6f8b32632cf31bf7c142571eb22e243 (agttydck)
C2 IP Address:
- 45[.]145[.]6[.]112 (Defunct)
What Should Users Do to Safeguard Their Confluence Data Center and Server?
Atlassian strongly advises patching affected installations to one of the fixed versions mentioned earlier. If patching is not immediately possible, temporary mitigations include backing up the instance and removing the instance from the internet until it can be patched. It is crucial for administrators to secure their systems and apply necessary updates to prevent exploitation.
How SOCRadar Can Help Securing System Against Vulnerabilities?
SOCRadar is a comprehensive cybersecurity solution that can greatly assist organizations in addressing recently discovered vulnerabilities through its Vulnerability Intelligence, Attack Surface Management, and Supply Chain Intelligence modules.
In the realm of Vulnerability Intelligence, SOCRadar keeps your organization informed and vigilant. It continuously monitors the evolving landscape of vulnerabilities and alerts you in real-time when critical vulnerabilities or exploits emerge for the specific product components and technologies associated with your digital footprint. This proactive approach allows you to stay one step ahead of threat actors and expedite the assessment and verification processes by providing actionable insights and contextual information.
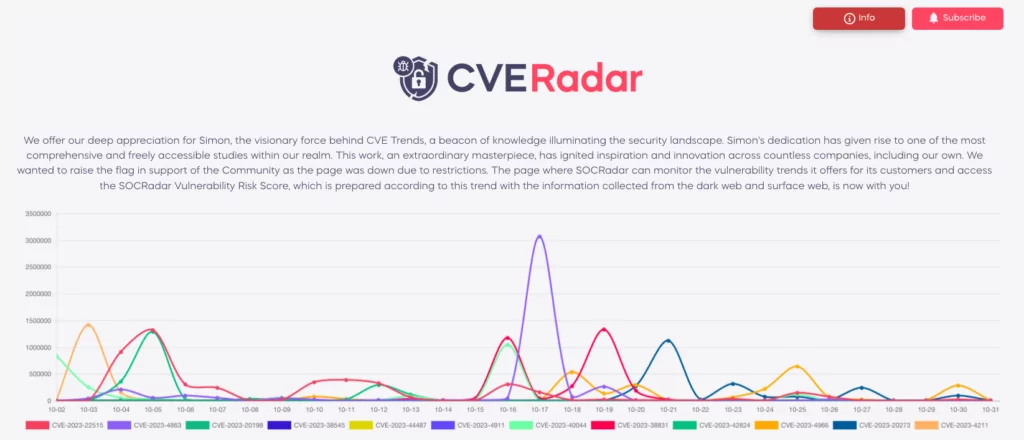
Access vulnerability trends and the SOCRadar Vulnerability Risk Score, which is calculated based on these trends using data collected from both the dark web and surface web. This valuable resource is readily available to you. Additionally, SOCRadar offers the CVE Radar service at no cost, aiding security professionals and system administrators in keeping abreast of the most recent vulnerabilities.



































