
Cyber Reflections of Iran’s Attack on Israel
[Update] April 22, 2024: “Israeli Hackers Strike Back: Cyber Av3ngers Hacked”
[Update] April 17, 2024: “Ongoing Hacktivist Activities”
On Saturday and early Sunday, Iran launched a series of missile and drone attacks aimed at Israel. This retaliation came after a suspected Israeli strike on its consulate in Damascus last week, resulting in the deaths of 13 individuals.
The feud between Israel and Iran seems likely to continue unabated. However, this conflict did not start this year, nor did Iran’s attack appear suddenly. Activities started in the cyber world at the end of March, and one year has already passed since the conflict that began all the events.
On October 7, 2023, Amid the ongoing Israel-Palestine conflict, a noticeable increase in hacktivist groups occurred. These collectives have announced continuous digital attacks targeting various entities on both sides of the conflict.
This development was a direct response to the escalating conflict involving Palestinian militant groups, particularly Hamas, launching a large-scale offense from the Gaza Strip aimed at Israel.
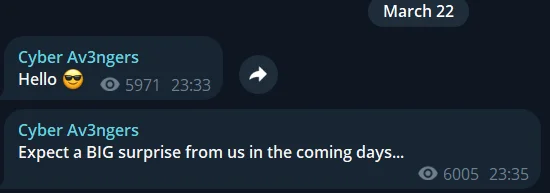
A Telegram post of IRGC-affiliated group on March 22, 2024, much earlier visible activity from the Iran’s drone attack
We followed the reflection of the Israel-Hamas conflict, which started last year, on the cyber world, and we followed its traces both before and during the conflict. This week, we see again that the sounds of cyber war were heard before the physical damage.
Israel Under Cyber Siege
The head of cyber defense of Israel, Gaby Portnoy, cautioned that the frequency of cyberattacks targeting Israel has tripled since the onset of the conflict with Hamas on October 7. This surge is attributed to increased involvement from Iran and its allies, including Hezbollah, in cyber hacking activities.
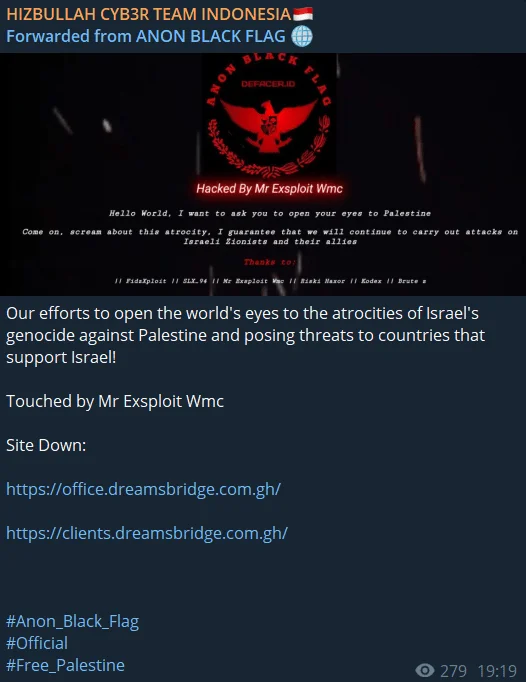
On Telegram channels, many self-claiming Hezbollah affiliated hacker groups also carry out various cyber attacks
These words gauged the intensity of attacks compared to the preceding years. However, it’s notable that such attacks were more pronounced in the initial months of the conflict, gradually diminishing over time. Nevertheless, certain days and events stood out, highlighting moments when the intensity of attacks surged significantly.
The activities of hacktivist groups followed by tags such as OpIsrael and FreePalestine have been accelerated in recent weeks.
Intensifying Threats on Celebrations: Jewish Holidays, Ramadan
On April 1, a threat message circulating on Telegram from the hacktivist groups was calling for coordinated cyber attacks against Israel on specific dates coinciding with Jewish holidays. The message claims that these dates hold significant symbolism for the Israeli government’s actions and urges hackers worldwide to unite in targeting Israeli assets.
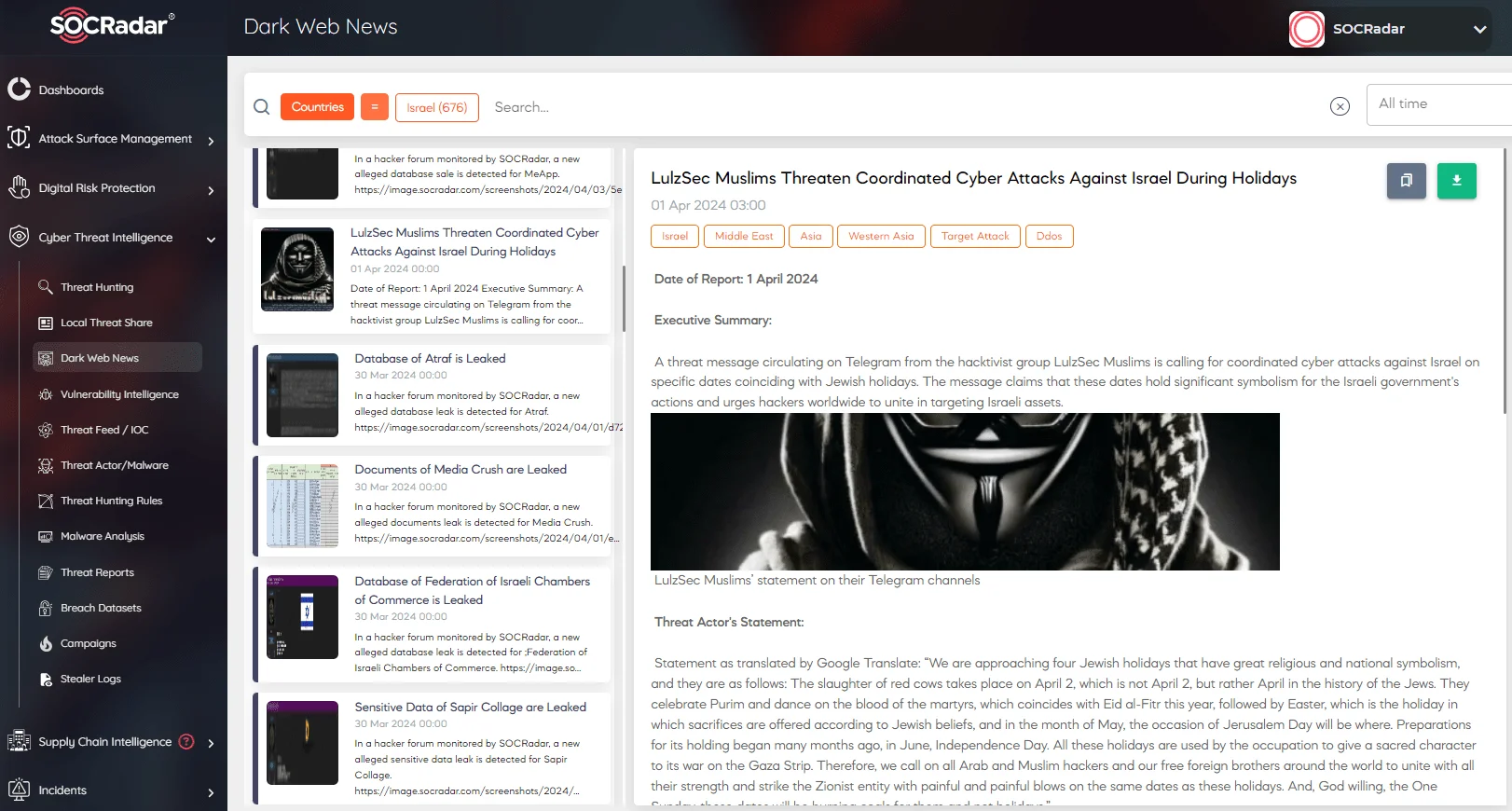
An early alert has been sent by SOCRadar to our users
During the same period, there were many groups targeting Israel, and time intervals such as holidays and important dates in the conflict became excuses for hacker groups to gather.
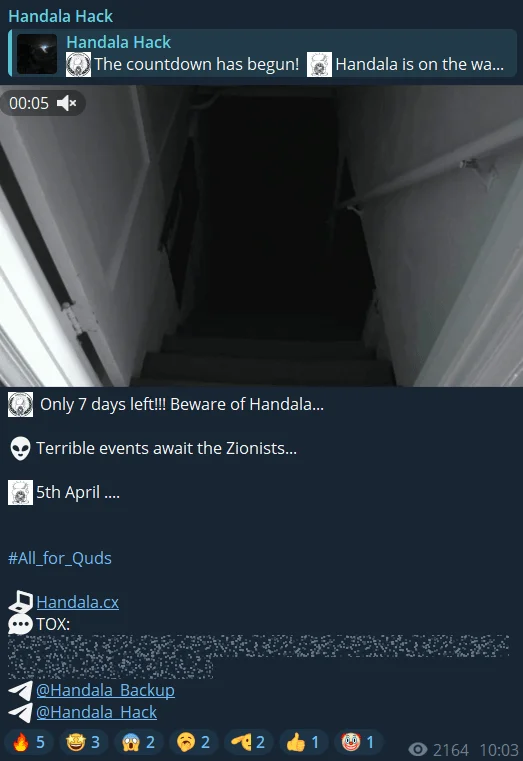
A group named Handala signaled an attack in similar dates
Early Signs of Attack: Resurrected Groups from Iran
Many hacktivists or hacktivist-looking groups can be the pioneers and harbingers of many events, willingly or unintentionally, and are often used to conceal more malicious attacks. During the Israel-Hamas conflict, hundreds of groups from both sides carried out cyber actions and carried out operations for the causes they believed in. Thus, some groups could have a much more significant and tangible impact; These were IRGC-related groups, Hezbollah-backed hacker groups, Iranian APTs, and even Houthi-backed groups.
On April 7, 2024, Wake up call of Cyber Toufan Al-Aqsa
Allegedly a state-sponsored group, named Cyber Toufan or Cyber Toufan Al-Aqsa was one of the groups that carried out many large operations, and their biggest impact was that they were able to direct many other groups to similar targets on similar dates. After a very long gap, their activity was observed again in early April.

Threat Actor card of Cyber Toufan Al-aqsa
Members of the IRGC related group called Cyber Av3ngers, who made much more noise in the world news with their attacks on OT systems, were exposed by the security forces and put their names on the sanction lists, thus they were silent for a while, but at the end of March, they shared a message that something big would happen soon and they responded to Iran’s attack. They simultaneously claimed responsibility for a massive cyber attack.
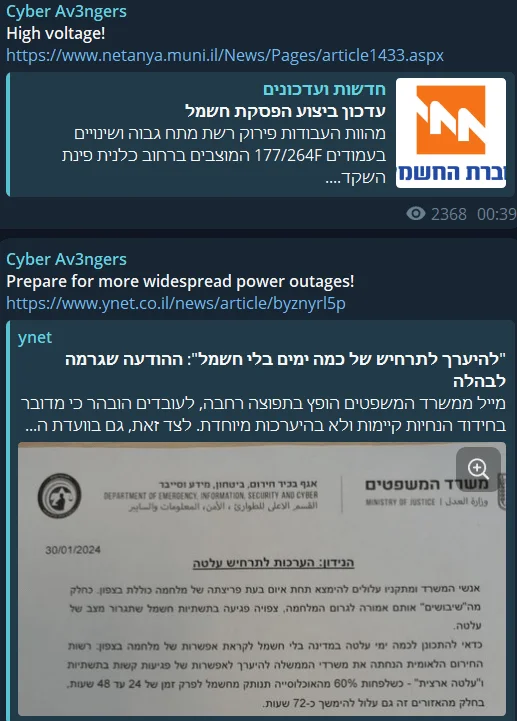
Cyber Av3ngers’ alleged attack on industrial systems
Cyber Av3ngers declared in a statement that it was responsible for cutting off electricity in various parts of the occupied territories. The group emphasized that it carried out this cyber attack from south to north in response to the Zionist regime’s actions in Gaza.
These were the recent actions of the big groups that were visible, but an increase in the activities of many other Iranian groups had also been observed since the beginning of this year.
Hacktivist Tide
As we mentioned, hacktivist waves can either trail or spearhead significant groups and events. The Israel-Hamas conflict sparked one of the largest hacktivist waves on record last year.
Now again, Throughout April, numerous groups launched cyber attacks targeting Israel and nations they deemed as its allies, notably India, the US, the UK, EU countries, and Saudi Arabia due to their abysmal relations with Yemen.
Even with a simple hashtag search on Telegram, we can see that many groups are claiming attacks
Iron Dome was one of the popular and logical targets for the conflict before it even started, and hacker groups are targeting Iron Dome again.
About the alleged hack of Iron Dome
In addition to critical systems, military systems are also popular targets. Israeli air defense systems are the most targeted systems in this regard. It is said that Iran costs Israel billion dollars with its cheap drones, but cyber attacks on such systems are likely to cause more than financial damage, even with cheap drones.
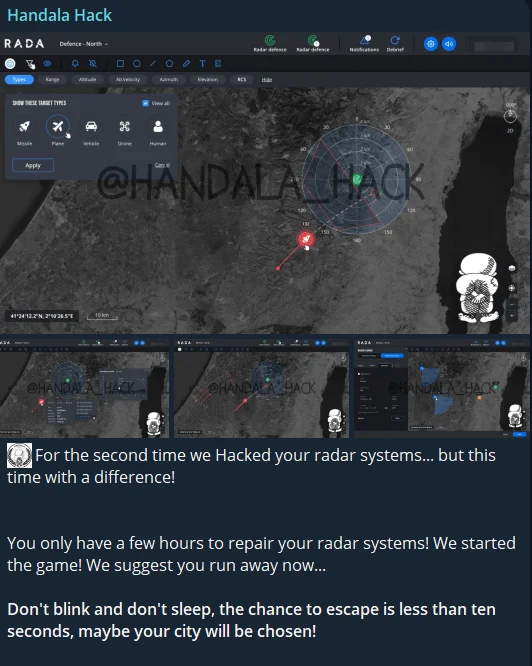
Handala’s alleged hack of Israeli radar systems
Targets other than Israel can also be interpreted as overflow waves. Apart from more popular secondary targets such as the US, many groups are also targeting Saudi Arabia due to the recent coalition against the Houthis and subsequent events.
One of the claims and annoucements about Saudi organization hacks
Ongoing Hacktivist Activities
While events continue in the political arena, hacktivist groups continue their accelerated operations that started at the beginning of April. Although there were no incidents as significant as the attacks carried out by Cyber Av3ngers and Handala Hack.
At the time there is a lot of noise. To help you guide these false claims, check out our relevant article to get accurate information in such a noisy arena.
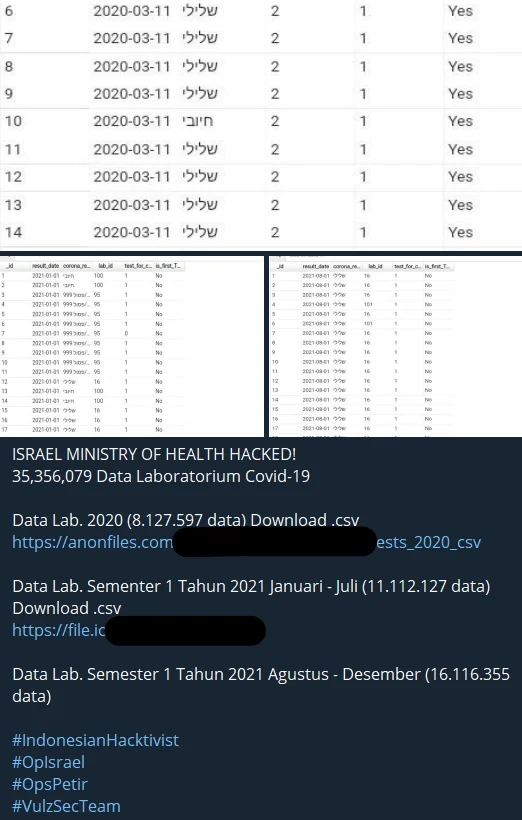
Claims of Israel Ministry of Health breach
Various data sets are shared, especially regarding many Israeli entities, critical institutions, and organizations. However, most of the data is previously shared or scraped. Thus, even if some of it is nonsense, sensitive data may float around.

Telegram post of a pro-Palestine group
Many groups have been targeting Israel for a long time, but the last actions are to show their support to Iran in any way they can.
Alleged DDoS attack to a Saudi Arabian organization
Saudi Arabia, Jordan and India are popular targets these days, along with Israel. The vast majority of attacks targeting these countries are small-scale DDoS attacks.
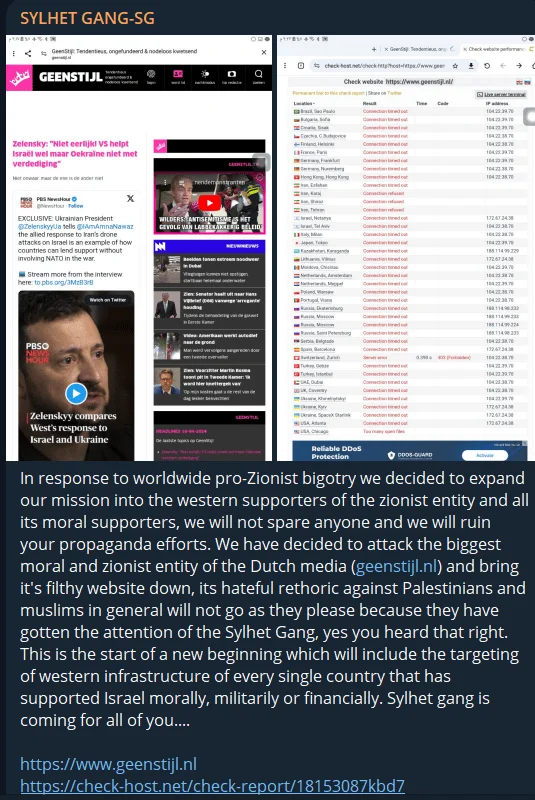
DDoS attack to a Dutch media agency
Certainly, it’s no surprise that attacks are also directed at numerous EU nations, particularly focusing on critical targets, logistical regions, and news agencies, with DDoS attacks being especially prominent.
Israeli Hackers Strike Back: Cyber Av3ngers Hacked
The digital battlefield continues to intensify as recent developments unveil significant retaliatory actions and exposed identities within the cyber conflict between Israel and Iran.
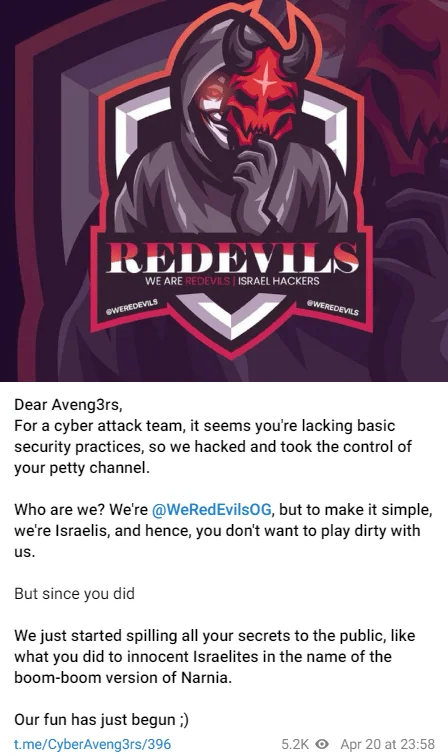
Telegram post of WeRedEvils in CyberAveng3rs’ channel
Israeli hacker group “@WeRedEvilsOG” has struck at the heart of the Iranian cyber front by compromising the notorious “Cyber Av3ngers” channel. They claim to have seized control and are now exposing sensitive information publicly. This includes the identity of the Cyber Av3ngers’ owner, Mahdi Lashgarian, along with detailed personal data such as date of birth, nationality, passport details, phone numbers, and residential address in Tehran, Iran.
Anonymous Israel’s Iranian government officials information list
Hacker group identified as AnonymousIsrael has released a list containing names and contact information of Iranian government officials. This release suggests a potential data breach or intrusion into sensitive government systems, adding another layer of concern to the ongoing cyber tensions.
Later they also escalated threats by targeting AlQuds newspaper, claiming access to their SMTP server and threatening to expose emails related to recent events. This action is accompanied by warnings of potential harm to businesses connected with Bashar al Masri.
These recent developments underscore the volatile nature of cyber warfare in the Middle East, where hacktivist groups on both sides are actively engaging in retaliatory measures and exposing sensitive information. The stakes continue to rise as digital assets and government systems become prime targets for disruption and espionage.
Stay tuned for further updates as the cyber conflict unfolds, revealing new tactics and escalating tensions in the realm of digital warfare.
Tracking Every Surface of the Web with SOCRadar
With SOCRadar’s Cyber Threat Intelligence and Digital Risk Protection modules, you can effortlessly maintain constant vigilance on threat actor activities across all corners of the web, including Telegram channels.
The Digital Risk Protection module from SOCRadar simplifies the monitoring of threat actor actions. Its Dark Web Monitoring tab automatically delivers relevant insights about products and technologies found within your digital assets. Additionally, Dark Web News provides timely updates from deep and dark web forums, social media platforms, and communication channels like Telegram, complete with screenshots and textual content.
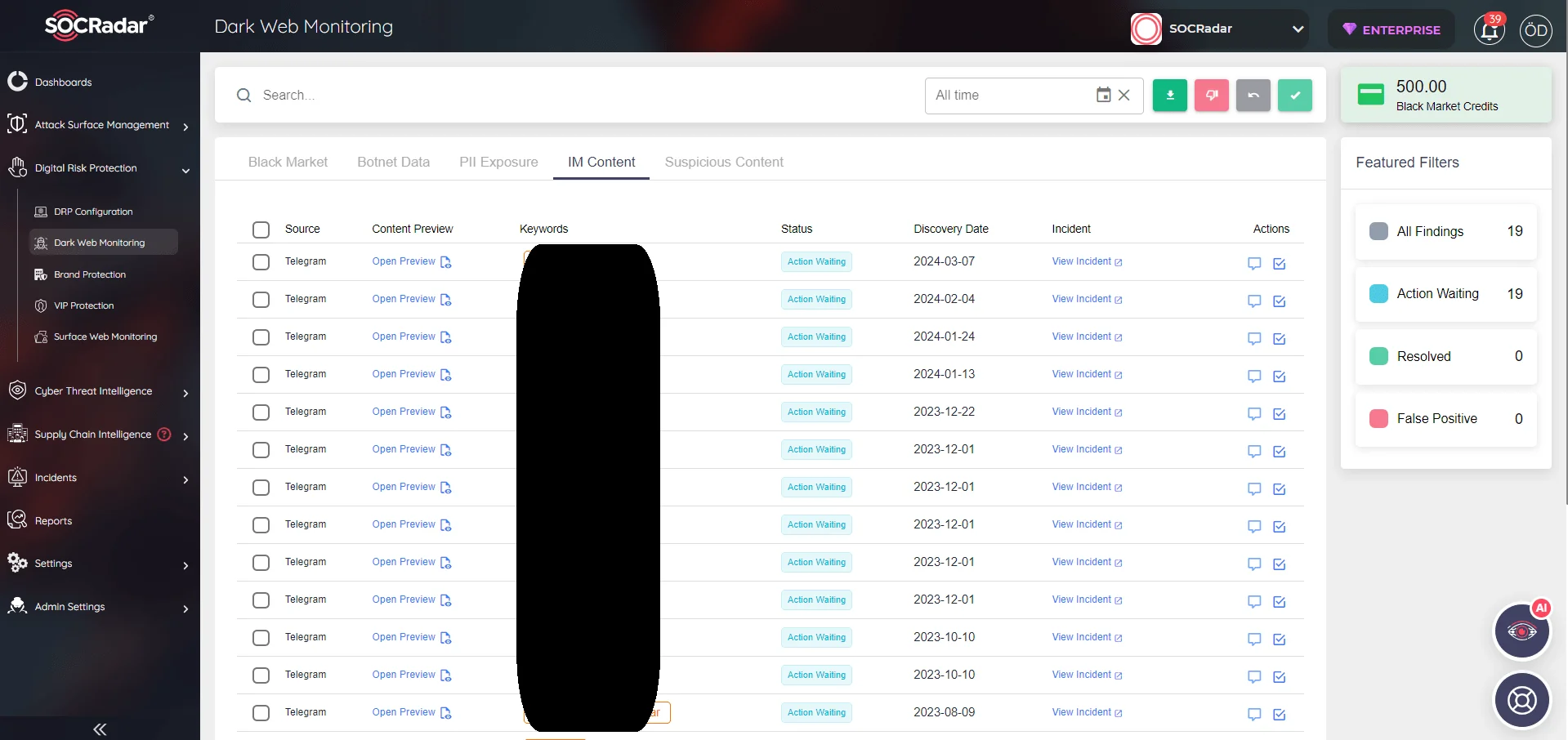
SOCRadar Dark Web Monitoring
Identify potential risks to your data from threat actors and take proactive measures to mitigate these risks within your digital assets. SOCRadar conducts regular internet scans to detect new Telegram groups where your company’s leaked data may be exposed. Furthermore, it promptly notifies you of any information pertaining to your organization.



































