
The Landscape of Hacktivism in the Context of Current Events
Hacktivism, may be defined in the dictionary as a mixture of the words “hacking” and “activism,” encompasses the strategic application of hacking techniques in pursuit of political or societal objectives. This unconventional form of civil dissent harnesses digital tools’ power to voice grievances and directly influence change.
At its core, hacktivism is driven by hacktivists who advocate for causes encompassing freedom of expression, human rights, and information ethics. The arsenal of hacktivism may contain tactics such as altering website appearances (which is known as defacement) or orchestrating Denial-of-Service (DoS) attacks to convey messages or disrupt the activities of the entities they oppose. The ethical implications surrounding hacktivism remain a subject of intense debate, underscoring how it serves as a cutting-edge domain within the realm of activism, vividly illustrating the profound impact of digital technologies on contemporary society.
Nonetheless, this narrow definition is not always adequate to encapsulate the complex nature of hacktivism. The relative nature of the notions of right and wrong, and even the definitions of legality and illegality, can vary depending on one’s geographical location. While unauthorized access to an organization’s resources is inherently considered a criminal act, regardless of intent, the presence of nation-sponsored actors and their activities also exist, so things may not always align with the ideal scenario. In this context, it becomes apparent that the aforementioned definition may fall short of comprehensiveness.
Furthermore, questions regarding whether specific entities oversee and control the individuals and groups involved in hacktivist movements, or if they merely serve as public faces, can be quite dubious. For instance, in the context of the Russia-Ukraine conflict, Ukrainian authorities asserted that so-called Russian-speaking “hacktivist” groups may serve as cover for APT (Advanced Persistent Threat) groups, potentially serving as a diversion while APT groups pursue their ultimate objectives.
While discussing the definition of this phenomenon and the discussions on its definition, we drew a vague picture. Still, we can talk about one fact: hacktivism is not a situation that only concerns states because many organizations are evaluated and attacked based on the country they are based in, even if they are independent in their stance. As we’ve observed, particularly in the context of the ongoing Israeli-Palestinian conflict, numerous civilian entities, independent businesses, and institutions dedicated to the overall betterment of humanity, such as those in the education and healthcare sectors, have become targets of cyberattacks. This is why the Red Cross proposed guidelines for cyber warfare engagement, but many hacktivist communities showed little concern for them.
How Did Hacktivism Evolve?
Hacktivism’s history reveals a narrative that stretches back to the 1980s. During this era, the seeds of digital activism were sown, marked by the emergence of a subculture known as “phreaking.” This early hacking involved manipulating telephone networks to secure free calls, providing a glimpse into the potential of using technology for unconventional purposes. Still, there is an infamous hacker magazine, Phrack, which resembles these days.
The term Hacktivism did not enter the dictionary until 1996 when Omega, a member of the hacking collective Cult of the Dead Cow, started it. This milestone marked the inception of a movement that would soon transcend mere digital mischief, becoming a potent force for change.
Hacktivism flourished as the 1990s unfolded, coinciding with the widespread adoption of personal computers and the burgeoning internet. Pioneers in this realm started harnessing the power of the digital domain to voice their dissent against a multitude of issues.
One of the earliest documented instances of hacktivism occurred in 1994 when a group known as the Zippies orchestrated an attack against the UK government. Their motivation was a protest against a proposed law aimed at curbing open-air rave parties.
The 2000s marked a significant turning point in the hacktivist landscape. During this decade, the movement diversified and grew more sophisticated with the emergence of groups like Anonymous and LulzSec. These collectives executed a series of high-profile cyberattacks, often directing their digital arsenals against corporations, governments, and any entities they perceived as oppressive or unethical in their ideological beliefs. Notably, it was during this time that WikiLeaks, led by Julian Assange, played a significant role in hacktivist activities by publishing classified government documents, further galvanizing the movement.
The 2010s started a new era of hacktivism, characterized by the resistance to censorship and surveillance. A notable moment was the Arab Spring, where hacktivism was pivotal in enabling communication and coordinating protests. During this turbulent period, hacktivists used their digital prowess to disrupt and amplify the voices of those seeking change, or maybe they sometimes lead the crowds with disinformation.
Thus, the world has witnessed the influential role of social media and digital space in mass movements in the Arab Spring. A critical factor is that, in cyberspace, the cost of launching an attack can be meager, while the potential impact remains disproportionately high. Consequently, communities that may face physical suppression during events often opt for cyberattacks as a means of action.

Although noble ideas like the free world are often sympathetic, the digital world is, unfortunately, one of the places most open to disinformation, and the discussion of actions taken for these purposes should always remain open. Especially in more recent times, we have witnessed the reflection of major global events such as the Russia-Ukraine war and the Israel-Palestine war in the cyber world, and many innocent organizations have been targeted for various reasons.
Hacktivism as an Oriental Concept
When we talk about hacktivism today, the first thing that comes to mind is Russian Hacktivists. Although there seems to be a paradigm shift in this case, the involvement of Russian hacktivist groups’ involvement in the Israel-Palestine war still causes us to continue the same narrative. Although activist culture remains at its most vibrant in Western countries, such as the recent Yellow Vest protests in France, we see that the Eastern hemisphere dominates the hacktivist arena.
We recommend you read our article Reflections of the Israel-Palestine Conflict on the Cyber World to see the cyber reflection of the Israel-Palestine events and understand hacktivism’s popularity, especially in South Asia. Under this heading, we will take a look at Russian hacktivism.
Since the Russian invasion of Ukraine, there has been a surge in Russian hacktivism. Groups like KillNet and NoName057 conduct DDoS attacks against organizations in Ukraine and the West.
The groups usually finance their actions through cryptocurrency donations, selling of leaked data, or cyber theft. They mainly communicate and publish their activities on Telegram channels. It was during this period that Telegram became a platform associated with cybercrime.
For example, hacktivist channels such as KillNet, which reach thousands of followers, continue to exist on Telegram. These groups have administrators who run botnets used for attacks. They recruit volunteers from online forums, dividing them into squads and assigning targets.

Targets appear to be selected based on understanding who Russia perceives as its adversaries, including NATO countries. Although no definitive evidence connects these groups to the Russian government, cooperation among hacktivist groups is evident, not only within Russia. For instance, the Russian hacktivist group KillNet engages in joint operations with hacktivist groups from other regions. Anonymous Sudan, for example, has established a longstanding partnership with KillNet, and Russian hacktivists collaborate with pro-Palestinian groups concerning Israel.
These hacktivist groups also recruit hackers who can commit cyber breaches, they work with ransomware groups, buy initial accesses, and seek insiders. This makes the blurred lines between hacktivism and crime a more critical problem.
How Do Hacktivist Groups Conduct Attacks?
Hacktivist groups employ various strategies and techniques in their cyber campaigns and may use every possible attack vector. Thus, their methods often share common characteristics. Here’s an overview of how hacktivist groups typically conduct their attacks:
- Distributed Denial-of-Service (DDoS) Attacks: DDoS attacks involve overwhelming a target’s online infrastructure with a flood of traffic, rendering it temporarily inaccessible. Hacktivist groups use botnets, networks of compromised devices, to orchestrate large-scale DDoS attacks. These attacks are intended to disrupt the target’s services and make a statement.
- Web Defacement: In web defacement attacks, hacktivists gain unauthorized access to a target’s website and replace its content with their messages or graphics. This is a visible way to convey their message and disrupt the online presence of their chosen target.
- Data Leaks: Hacktivist groups may infiltrate a target’s systems to access and release sensitive information or documents. They often publish these materials on public platforms, exposing potentially damaging information and creating public relations challenges for the affected organization.
- Social Engineering: Some hacktivists may use social engineering techniques, such as phishing, to deceive individuals into revealing sensitive information, which can be used in attacks or for data leaks.
- Online Propaganda: Beyond direct attacks, hacktivist groups often engage in online propaganda campaigns. This involves disseminating their message through social media, forums, and websites to influence public opinion and gain support for their cause.
Even though these are the most common vectors, it can be observed that they also attack with many other attack vectors and techniques, sometimes with very superficial but in some scenarios with intricate methods. An excellent example is the modular stealer/ransomware called GhostLocker, produced by GhostSec, a member of The Five Families, a hacktivist collective.
How To Secure Your Organization?
Here are the key steps to enhance the security of your organization against hacktivist attacks:
- DDoS Mitigation: First, check your organization’s DoS/DDoS Resiliency for free via SOCRadar Labs. According to the results, you may have to implement DDoS mitigation solutions and strategies to handle sudden traffic surges. These can include load balancing, traffic filtering, and content delivery networks to ensure your online services remain accessible during attacks.
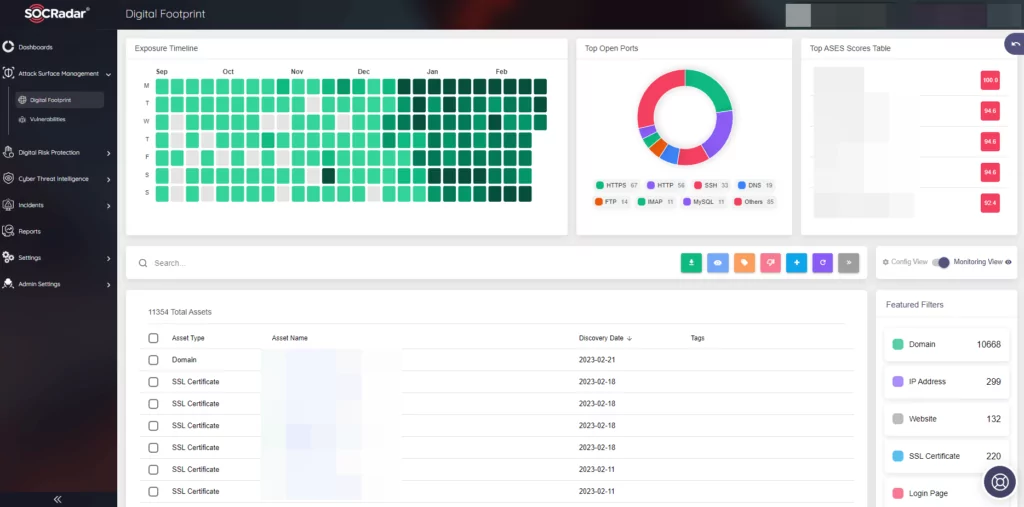
Attack Surface Management: Regularly update and secure your assets, especially your website, as it is a common target for web defacement and DDoS attacks. Employ strong authentication measures and monitor your internet-facing assets for unauthorized access or alterations.
- Data Protection: Safeguard sensitive information and data through encryption, access controls, and regular security audits. Monitor for unusual data access patterns and promptly respond to any breach.
- Security Awareness Training: Train your staff to recognize social engineering tactics like phishing attempts. Create a culture of cybersecurity awareness to reduce the risk of falling victim to such attacks.
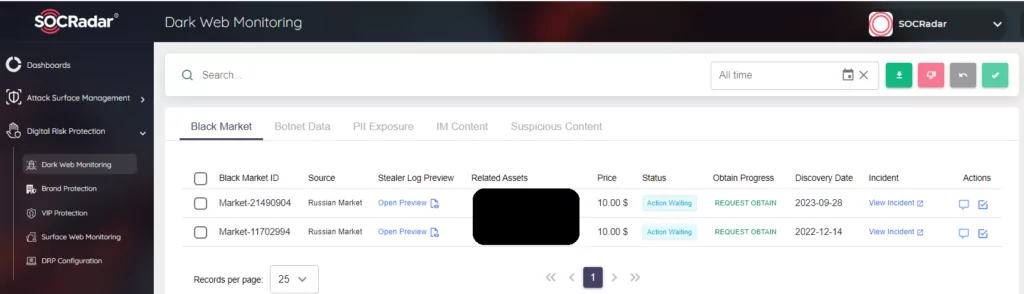
Dark Web Monitoring: Monitor your organization’s online presence on every web surface, most importantly the Dark Web. Be aware of any leaks about your organizational data, employee credentials, and initial access sales.
- Security Audits: Conduct regular security audits, vulnerability assessments, and penetration testing to identify and address potential weaknesses in your systems and networks. Have a vulnerability intelligence service and again, patch regularly.
- Collaboration with Cybersecurity Experts: Turn to resources that provide effective solutions against the ever-changing world of cybercrime. Engage with cybersecurity experts who can provide proactive threat intelligence and assist in fortifying your organization’s defenses against emerging threats.
Conclusion
In conclusion, hacktivism is a dynamic and evolving force that harnesses digital weapons to advocate for varying causes. As it continues to shape the digital landscape, the ethical boundaries of hacktivism remain a subject of debate, and its impact extends beyond state-level concerns to affect a wide range of organizations. Malicious actors are densely populated in this part of the cyber world, and it reminds us that it is an issue that needs to be taken precautions.
Proactive measures are necessary to secure your organization in this evolving landscape. SOCRadar is a platform developed to meet your needs in this regard. It enables you to monitor the entire internet, including Telegram and the Dark Web, while providing Vulnerability Intelligence, offering Attack Surface Management services, and much more.




































