Dark Web Profile: NoName057(16)
By SOCRadar Research
[Update] July 11, 2023: NoName recently launched a cyber attack on Poland, targeting critical infrastructures such as the National Bank of Poland and the Polish Computer Security Incident Response Team (CSIRT GOV) website. Added the subheading: “Cyber Attack on National Bank of Poland.”
The Russia-Ukraine war continues to this day with huge consequences on the physical side. In parallel, the sides also wage cyber warfare against each other to have leverage against one another, such as using DDoS attacks against valuable infrastructures or conducting espionage activities that could harm the target country.
As this cyber warfare continues, many pro-Ukrainian and pro-Russian groups have emerged. There are lots of groups actively operating, such as GhostSec, Kelvin Security, and IT Army of Ukraine on the Ukraine side, while Killnet, Zarya, and Xaknet groups are operating against Ukraine.
Although the groups generally interact with each other, they usually have their Telegram and/or Twitter accounts where they share their activities.
Using social media, they continue seeking new volunteers to participate in this cyber warfare. One of the new groups running DDoS operations on a volunteer basis is NoName057(16).
Who is NoName057(16)

NoName057(16) is a pro-Russian hacktivist group first observed in March 2022 and operating since that date.
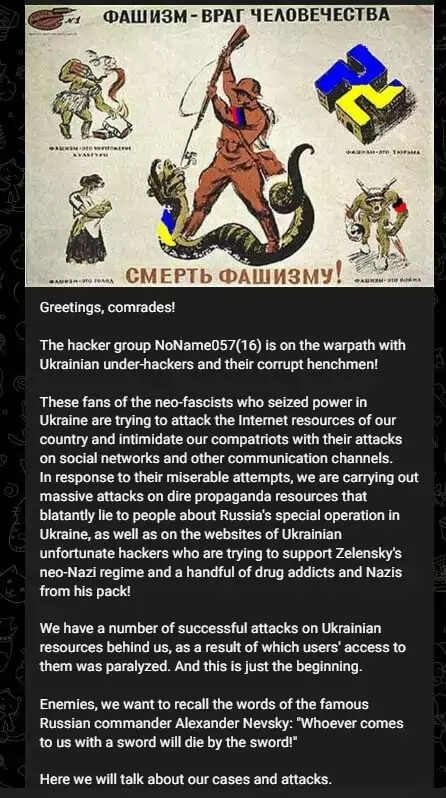
Even though the group has been operating since March 2022, it took until July 2022 for the group to publish its manifesto. According to the group’s manifesto, their actions are a response to those who have taken an openly hostile position toward Russia, and they have the strength and experience to restore justice. The group also notes that they do not work for financial gain and are willing to cooperate with like-minded groups. The manifesto emphasizes the importance of truth as a source of strength.
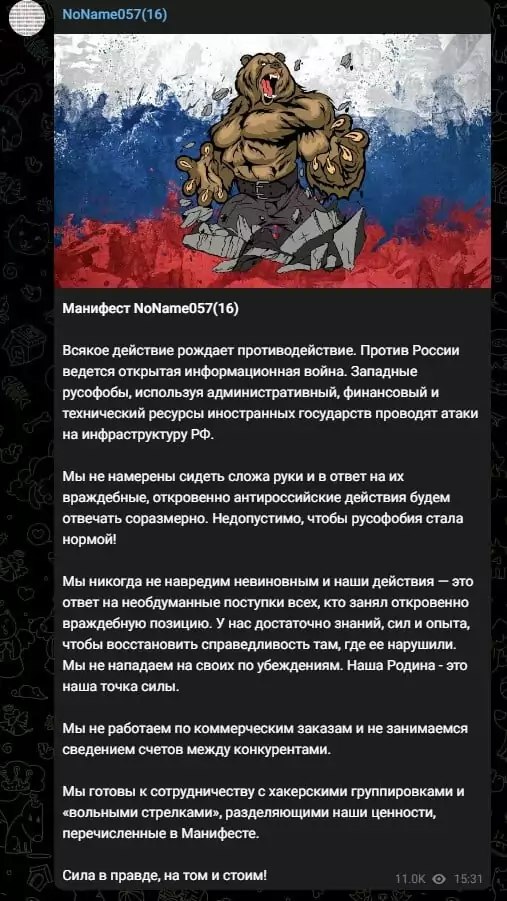
SOCRadar researchers observed that the group runs a total of 5 Telegram channels (and we did not observe that the group posted on any social media other than telegram):
- NoName057(16) is used for announcing their claims (mostly screenshots of their DDoS attacks) in the Russian language.
- NoName057(16) Eng has English translations of the same posts on their main Telegram channel.
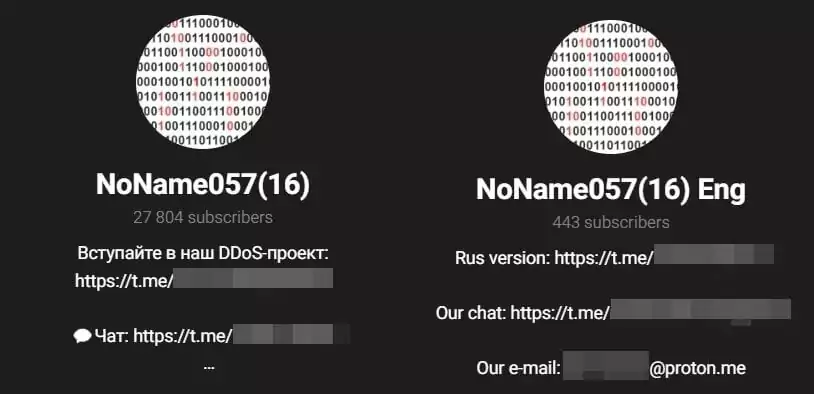
- NoName057(16) Chat is a chat channel members use to communicate.
- NoName057(16)_reserve is the group’s backup channel, as they say, and it is observed that this group was established on January 6, 2023.
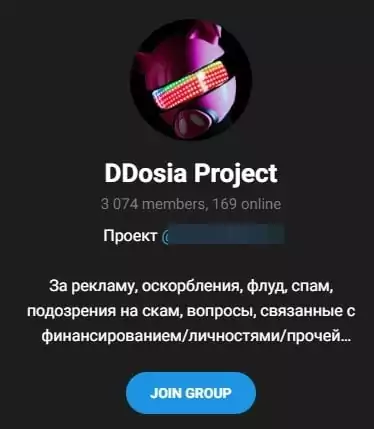
- And also, the group has a private Telegram channel called DDosia Project, the communication channel they created for the Dosia tool they use.
In addition, the group has observed using NoName05716, 05716nnm, and Nnm05716 names.
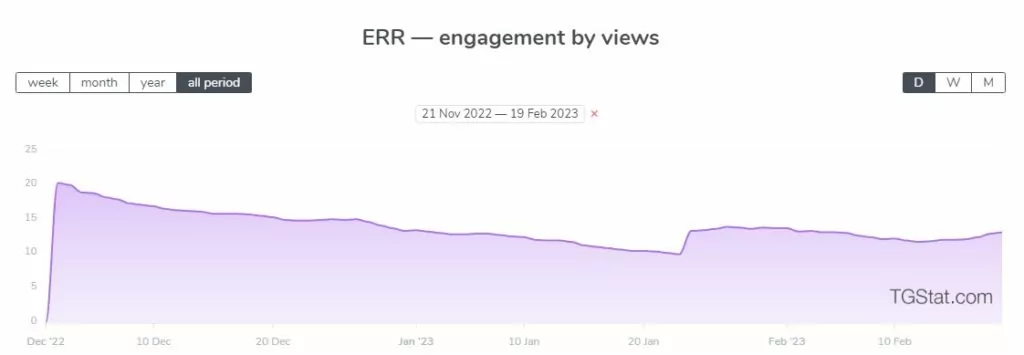
According to statistics gathered from TGStat.ru, although the group lost some traction towards January, its engagement rate by reach (ERR) is rising again, indicating that people are interested in the group again.
The group not only posts about its attacks but also informs its followers with posts about issues such as VPN, password security, etc.
DDoSia Evolves
The latest version of DDoSia has been equipped with an advanced protection method that effectively conceals the list of targets. This list is securely relayed from the command-and-control (C2) server to the users by leveraging AES-GCM encryption. This encryption method is complex, involving a key, an initialization vector (IV), and a tag, with the key being determined using a token value and the IV and tag derived from the encrypted text.
This sophisticated concealment through encryption poses challenges for cybersecurity experts in analyzing and mitigating the attacks.
From May 8 to June 26, 2023, the enhanced DDoSia tool was deployed in a series of attacks aimed at numerous countries, including Lithuania, Ukraine, Poland, Italy, the Czech Republic, Denmark, Latvia, France, the UK, and Switzerland. These attacks have left a profound mark on a total of 486 unique websites.
Bearing Down on Finance
In recent attacks, NoName057(16) has targeted the financial sector, mainly Ukrainian and Polish financial institutions.

Ukrainian financial institutions include
- Joint Stock Company “Bank Credit Dnepr,”
- State Savings Bank of Ukraine “Oshchadbank,”
- Joint Stock Company TASCOMBANK,
- Bank JSC “UNIVERSAL BANK,”
- Pravex-Bank,
- MTB Bank,
- Piraeus Bank,
- Bank JSB “CLEARING HOUSE,”
- IndustrialBank,
- Ukrsibbank BNP Paribas Group,
- Credit Agricole Bank.
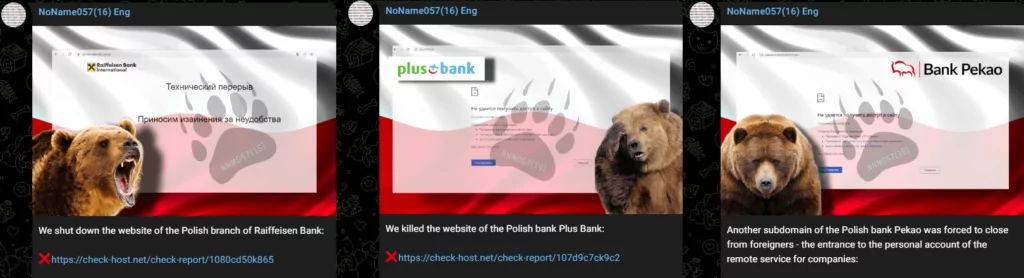
In Poland,
- PKO Bank Polski,
- Bank Pekao,
- Plus Bank,
- Raiffeisen Bank,
- Polish Development Fund (PFR) Ventures, and another Polish Development Fund Group, PFR Towarzystwo Funduszy Inwestycyjnychhas been targeted by NoName057(16).
Cyber Attack on National Bank of Poland
NoName recently launched a cyber attack on Poland, targeting critical infrastructures such as the National Bank of Poland and the Polish Computer Security Incident Response Team (CSIRT GOV) website.
The bank was unable to defend against the Distributed Denial-of-Service (DDoS) attack. Several threat intelligence services confirmed that the bank’s website was inactive for a period of time but became active again later. This attack is the latest in a series of DDoS attacks conducted by NoName against various Polish organizations.
How Does NoName057(16) Group Attack?
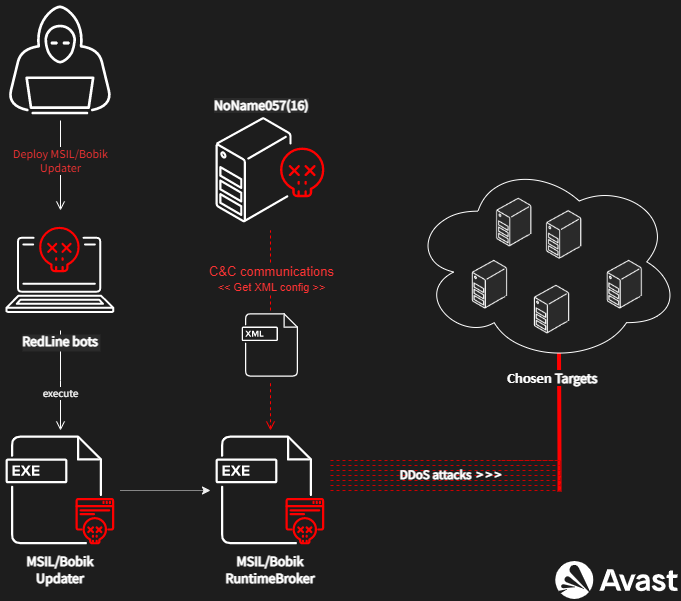
Distributed Denial of Service (DDoS) is the group’s primary attack method. To carry out a DDoS attack, botnets are needed. The group has been using the Redline Stealer botnet Bobik, a Remote Access Trojan (RAT), to operate its DDoS attacks. Below is the attack pattern of the NoName057(16) group when the group was using Bobik:
In September, they released their DDoS service, Project DDoSia, and continue to spread the tool through Telegram groups. Most of their posts include an invitation to participate in Project DDoSia.
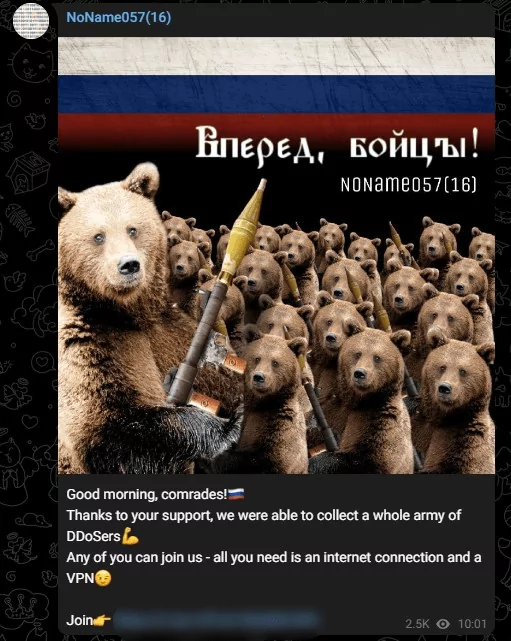
DDoSia is a volunteer-fueled DDoS program that seems to be a system that can expand its impact with increased volunteers. The group invites volunteers to the DDoSia Project Telegram group, and according to research, successful operations are rewarded in the form of cryptocurrency, which seems to be a move to increase the number of volunteers.
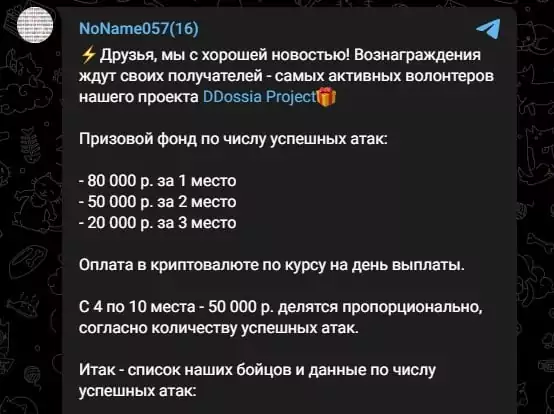
As seen from the group’s Telegram post on January 2023, the 1st most active volunteer will be awarded 80000 rubles, 2nd 50000, 3rd 20000, and the rest of the volunteers will be rewarded according to the number of successful attacks they have made.
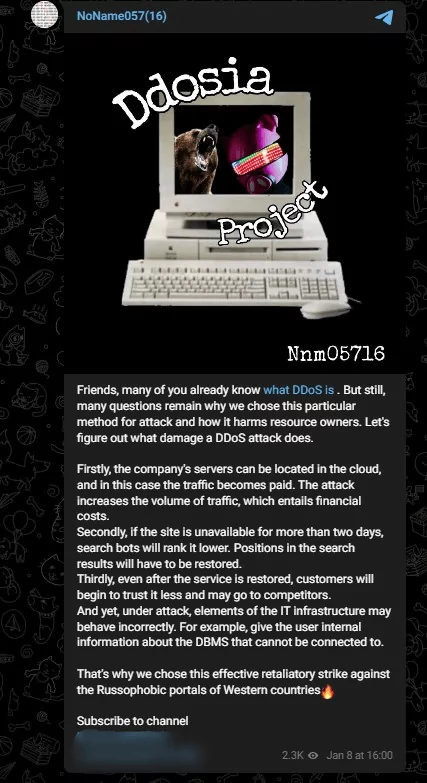
In January 2023, as seen in the screenshot above, the group shared updates on its Telegram channel and explained why they were using DDosia. It can be seen from these posts that they are targeting Western countries.
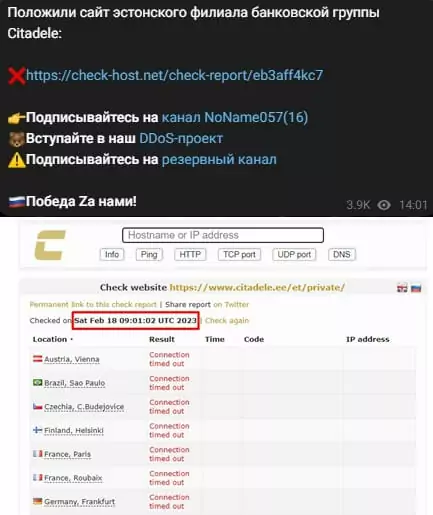
When NoName057(16) makes a successful attack, it posts a screenshot of the attacked domain with the country’s flag in the background and a log of the time of attack gathered from check-host.net.
Without joining the group, we found a sample of DDoSia with hash “1dfc6f6c35e76239a35bfaf0b5a9ec65f8f50522,” and when we tried to use it, we got the error: “Не удалось прочитать client id, запросите у бота новый клиент.” This error told us it needed a new client to run. This could indicate that the group’s DDoS tool is constantly updated, and they are trying to keep communication within the group alive.

Which Countries Did NoName057(16) Target?
The group is targeting Ukraine and the NATO countries. Also, we can predict that the group will target the countries which support Ukraine during the war between Ukraine and Russia.
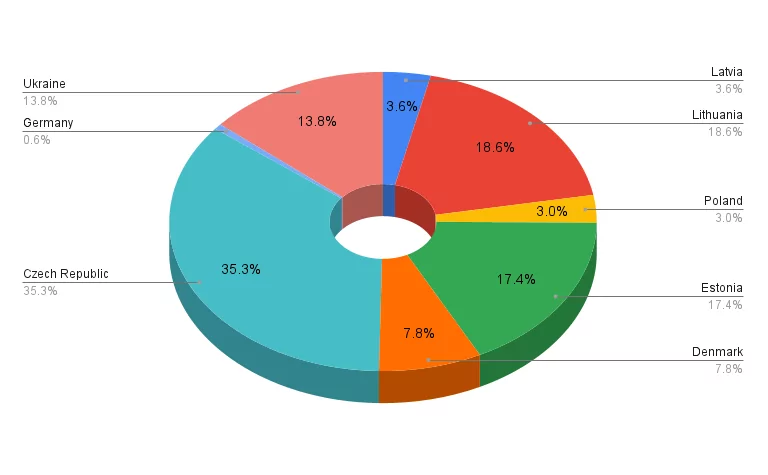
Looking at NoName057(16) ‘s claims in January, we can see that more than a quarter of the attacks targeted the Czech Republic. The group offers no reason for these attacks other than “Russophobia.”
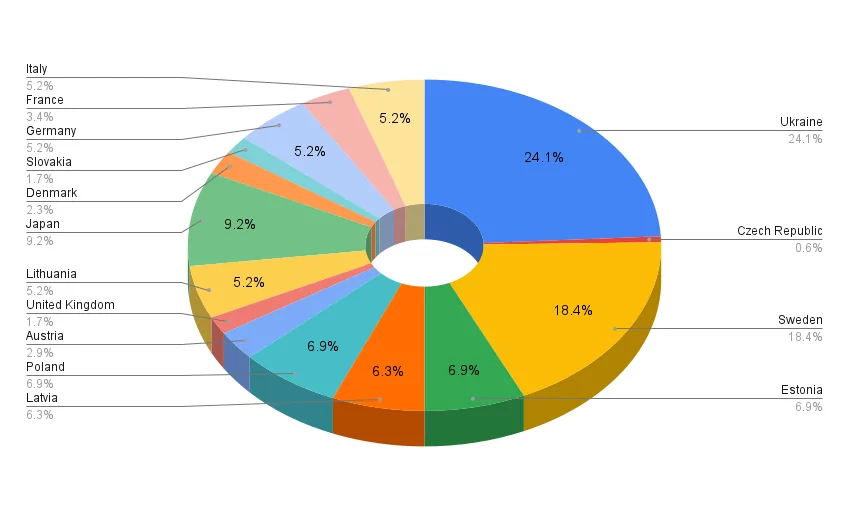
Looking at NoName057(16) ‘s claims in February, close to half (42.5%) of the group’s attacks target Ukraine and Sweden.
In addition, the group mostly targets a few sectors of their targeted countries, as listed below:
- Public Administration
- Transportation and Warehousing
- Finance and Insurance
- National Security and International Affairs
- Telecommunications
- Couriers and Express Delivery Services
- Utilities
- Commercial Banking
Latest Attacks of the NoName057(16)
According to the SOCRadar research team’s observations, the group makes approximately about 8 claims per day on its Telegram channels and attacks targeting 2 or 3 countries daily. In recent days, DDos attacks targeting Germany, Sweden, Poland, and Estonia have been the majority; however, Ukraine seems to be their main target because, in some of their attacks, they post messages about their current targeted country’s support for Ukraine as the reason for the attack.
Looking at the group’s attacks in recent days, it seems that the group targeted the domains of the Swedish postal and telecommunication services.
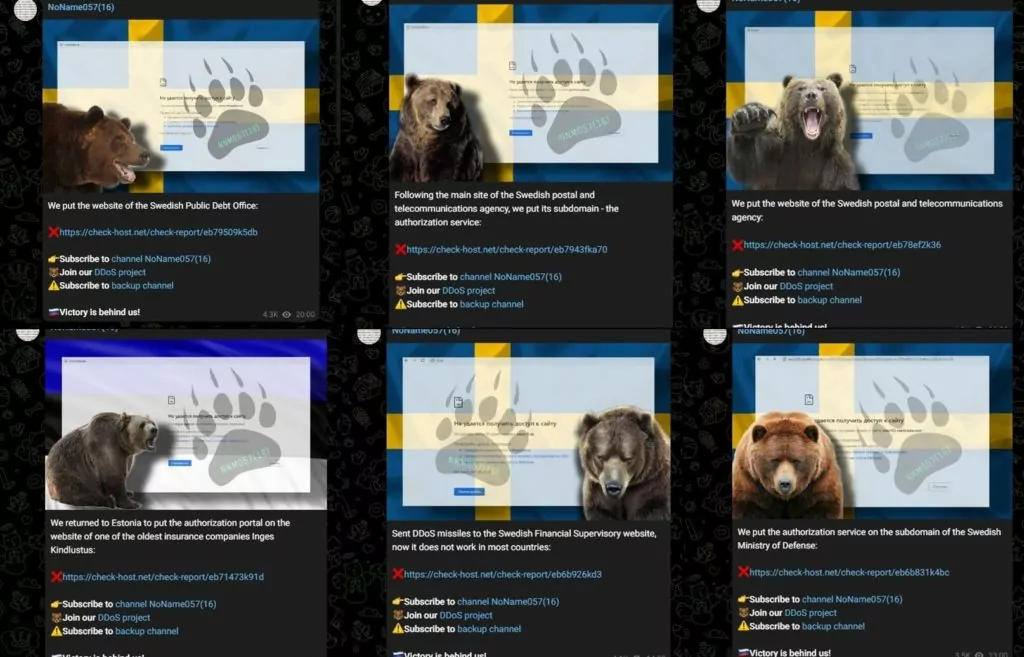
The following day of these activities, by choosing a completely different target, the group targeted German domains such as the Federal Ministry of Transport and Digital Infrastructure of Germany’s website, the German airport Weeze, etc.
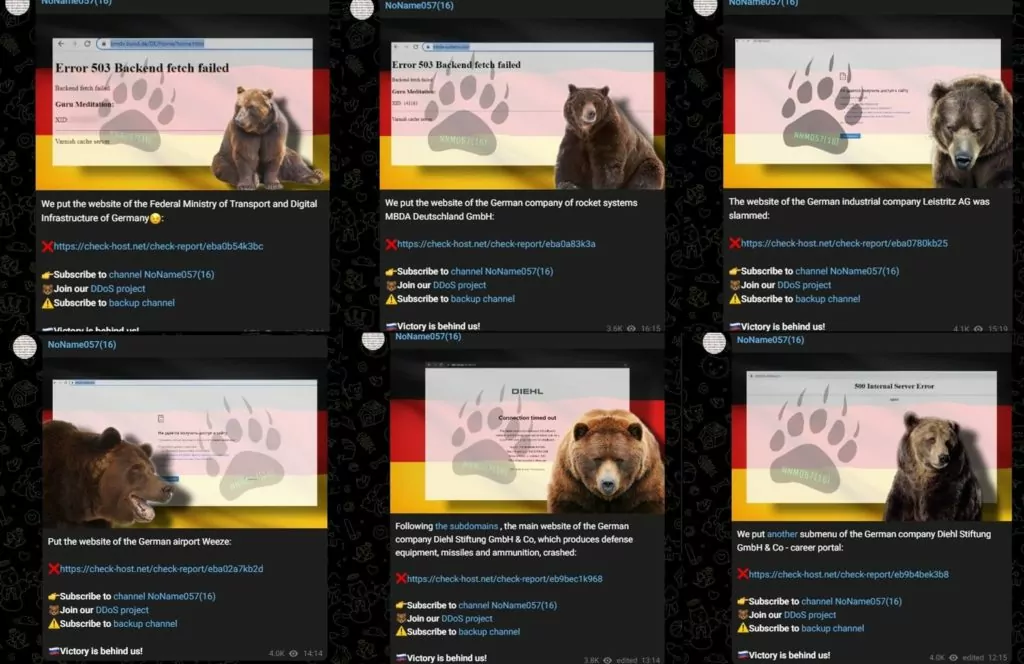
This means the group can choose a different target daily and often post claims independent of past activities.
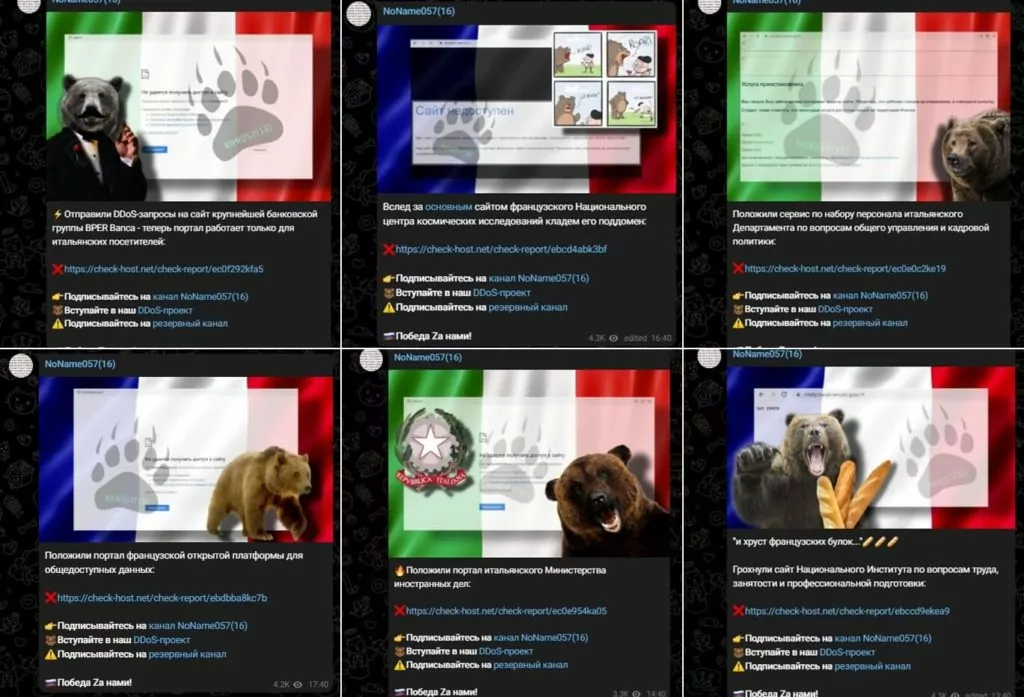
In recent attacks, the group has also started targeting Italy and France, and it can be inferred that NoName057(16) is expanding its attack surface.
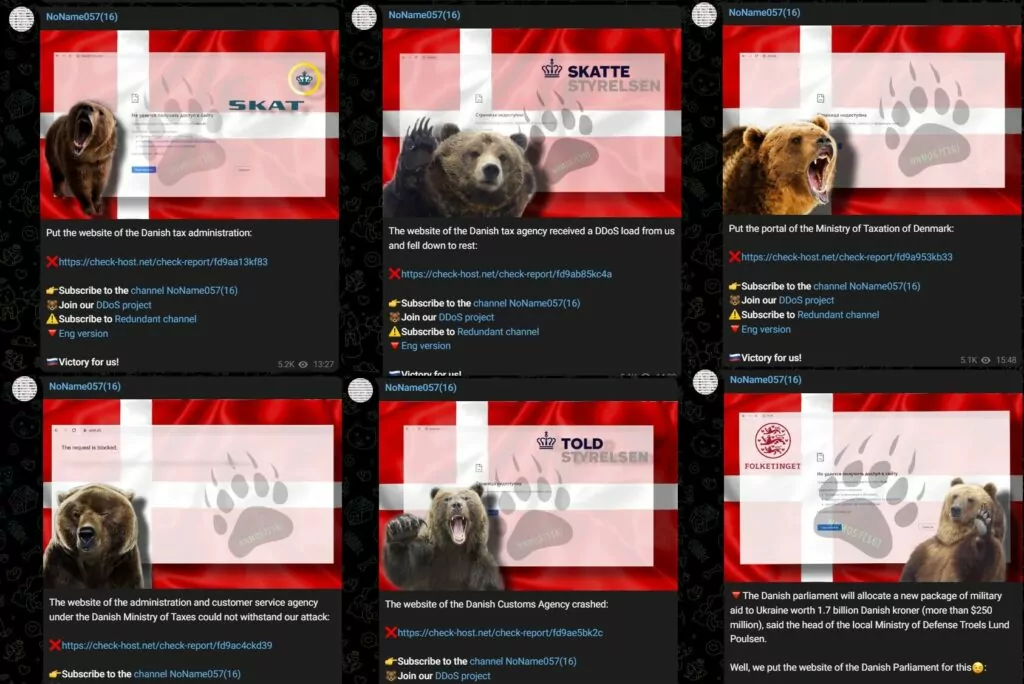
In May 2023, the group has been carrying out cyberattacks on Denmark. They seem to be retaliating against Denmark’s decision to send 80 Leopard 1 tanks to Ukraine along with Germany. The group has targeted a number of Danish government websites, including the website of the Danish parliament.
MITRE ATT&CK TTPs
|
Tactics |
Technique |
Technique ID |
|
Discovery |
System Network Connections Discovery |
T1049 |
|
Discovery |
System Network Connections Discovery |
T1016 |
|
Command and Control |
Application Layer Protocol |
T1071 |
|
Impact |
Network Denial of Service |
T1498 |
|
Impact |
Endpoint Denial of Service |
T1499 |
|
Persistence |
Boot or Logon Autostart Execution |
T1547 |
Conclusion
NoName057(16) only conducts DDoS attacks and so far has not been observed using any other type of attack. However, as they state in their manifesto, they look for companies and organizations that support Ukraine or are “anti-Russian” as their new targets.
It would be an important precaution against this group for companies located in NATO members or countries supporting Ukraine and doing business in the sectors mentioned above to receive DDoS protection services.
Among the industries listed above, manufacturing, energy, finance, insurance industries, and government domains are heavily targeted.
In addition, the following actions can work as a precaution against DDoS:
- Restrict the number of connections per IP address.
- Set limits on connections per second or lower the threshold.
- Control the number of downloads from a single IP address.
- Block requests with non-standard User-Agent headers that could be made by automatized tools.
- Implement captcha systems in public forms without authentication.
- Monitor and detect heavy requests to the databases.
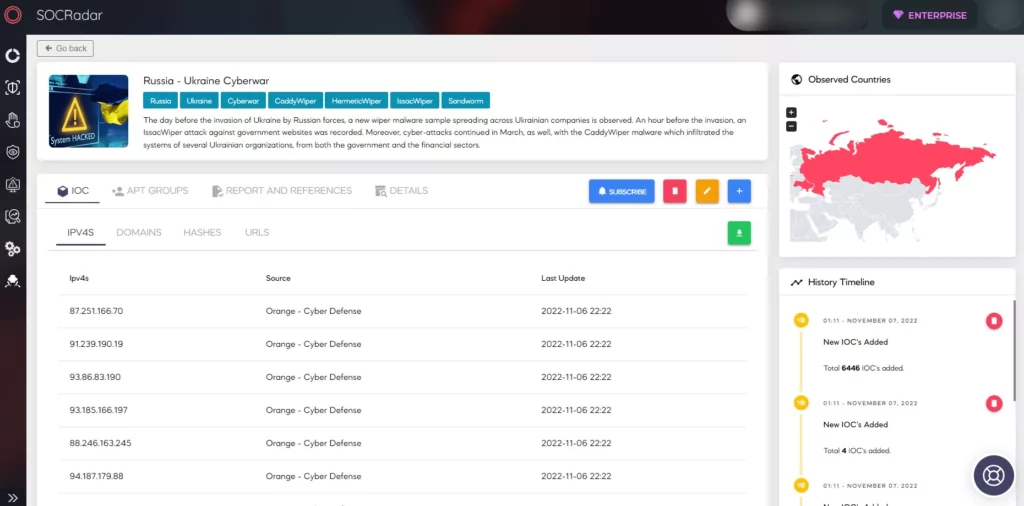
SOCRadar researchers continuously monitor threat actors and update new findings on the Threat Actor page on SOCRadar’s CTI platform. New IoCs found by NoName057(16) threat actors can be tracked on this page.
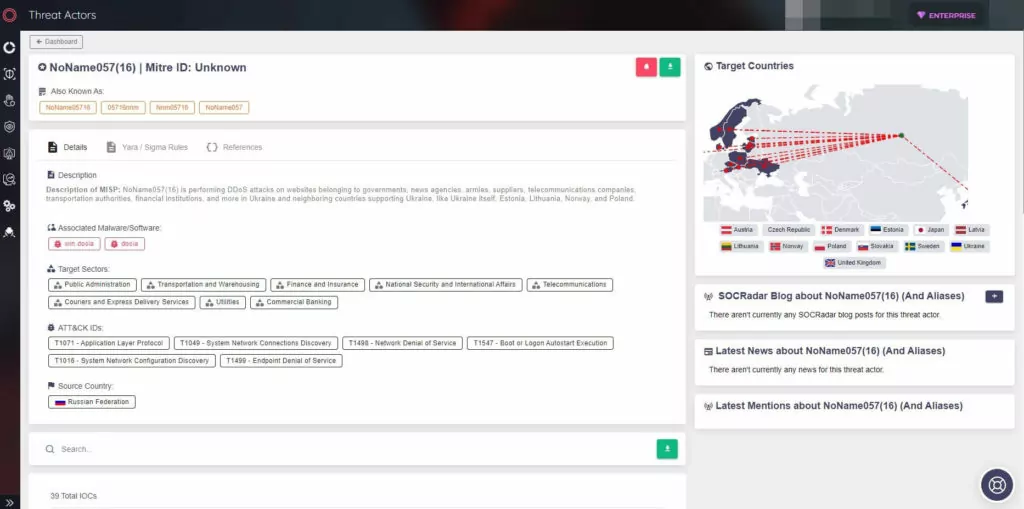
In addition, you can follow updates on the Russia-Ukraine cyber warfare on SOCRadar’s Campaigns panel.