
Fact-Checking of Cyber Incidents and CTI as a Helper
Nowadays, every article on information security starts with “In today’s rapidly evolving digital landscape,” but this time it is a really appropriate usage.
In today’s rapidly evolving digital landscape, the intersection of global conflicts and cyberspace has given rise to a new and challenging phenomenon: hacktivism. This blend of hacking and activism has become particularly prominent in the context of major global events, such as the Israel-Hamas conflict.
Alongside the growth of hacktivism, the cyber world faces a parallel challenge: the proliferation of misinformation and disinformation. As digital platforms become the primary battleground for information warfare, distinguishing between genuine cyber threats and fabricated claims has never been more crucial.
Interpreting Current Events in Cyber Security
Hacktivism, a portmanteau of hacking and activism, represents the strategic use of cyber techniques to advocate for political or societal causes. Its evolution traces back to the 1980s, with milestones like the emergence of groups like Anonymous and events like the Arab Spring. Hacktivist methods range from website defacement and Distributed Denial-of-Service (DDoS) attacks to data leaks and online propaganda. This digital activism has become increasingly prominent in the context of global conflicts, notably during the Israel-Hamas and Ukraine-Russia conflicts and wars.
In the case of the Israel-Hamas conflict, the cyber realm mirrored the physical confrontation, seeing a surge in hacktivist activities from various groups. These groups, originating from different regions and driven by diverse motivations, engaged in various cyber-attacks. Some targeted Israeli organizations and their allies with relatively low-impact methods like DDoS attacks and website defacements, while others made more alarming claims. Particularly concerning were the assertions of infiltrating Israeli SCADA systems, which, if true, posed significant real-world threats due to the critical nature of these infrastructures.
However, the veracity of these claims often remained unverified, underscoring the challenges in distinguishing genuine threats from exaggerated or fabricated cyber incidents. Investigations into these claims did not provide clear evidence supporting the alleged compromises, though they did indicate an ongoing interest in Israel’s critical infrastructure sectors. This ambiguity highlights the necessity of rigorous fact-checking and the use of sophisticated tools in cybersecurity, ensuring that responses are based on accurate and reliable information.
Fact-Checking in Cyber Incidents
In cybersecurity, fact-checking is a crucial defense against misinformation and disinformation. The process involves evaluating claims and assertions related to cyber incidents. This is particularly important when dealing with alleged cyber attacks or breaches, where the authenticity of such claims can have significant real-world implications.
Fact-checking in cybersecurity encompasses verifying the source of information, cross-referencing claims with credible reports, and consulting expert analyses. Utilizing tools and platforms dedicated to fact-checking can aid in this process. These tools analyze data, verify the authenticity of digital content, and provide insights into the credibility of cyber threat claims. In an era where cyber incidents can be easily fabricated or exaggerated, fact-checking is indispensable in maintaining informational integrity and ensuring informed decision-making in cybersecurity contexts. Now that we understand the situation, let’s see what precautions we can take against it and how fact checking can be done.
Use Cases & Role of CTI in Fact Checking
Since the Intelligence comes from the processing of knowlodge, Cyber Threat Intelligence plays a critical role in countering misinformation in the cyber domain. CTI involves the collection and analysis of information about current and potential attacks that threaten the cybersecurity of an organization. This intelligence is crucial for understanding the cyber threat landscape, identifying potential security breaches, and formulating strategic responses.
Without further ado, let’s see some examples of how to do a fact check with CTI
Threat Hunting for Leaks
Many allegedly leaked data is shared in many Telegram groups, GitHub repositories and hacker forums. However, many of these shares appear as combining old data sets, scraping from open sources, or re-emerging of an old leak as if it were new.
For example, when I search in SOCRadar’s Threat Hunting for a row from the data set allegedly belonging to a bank’s customers, leaked on November 23, we can see that the same data appeared from another source on November 3. In this scenario, we were able to see where the leak occurred, and we could also understand that the hacktivist group’s hacking claim was not true.
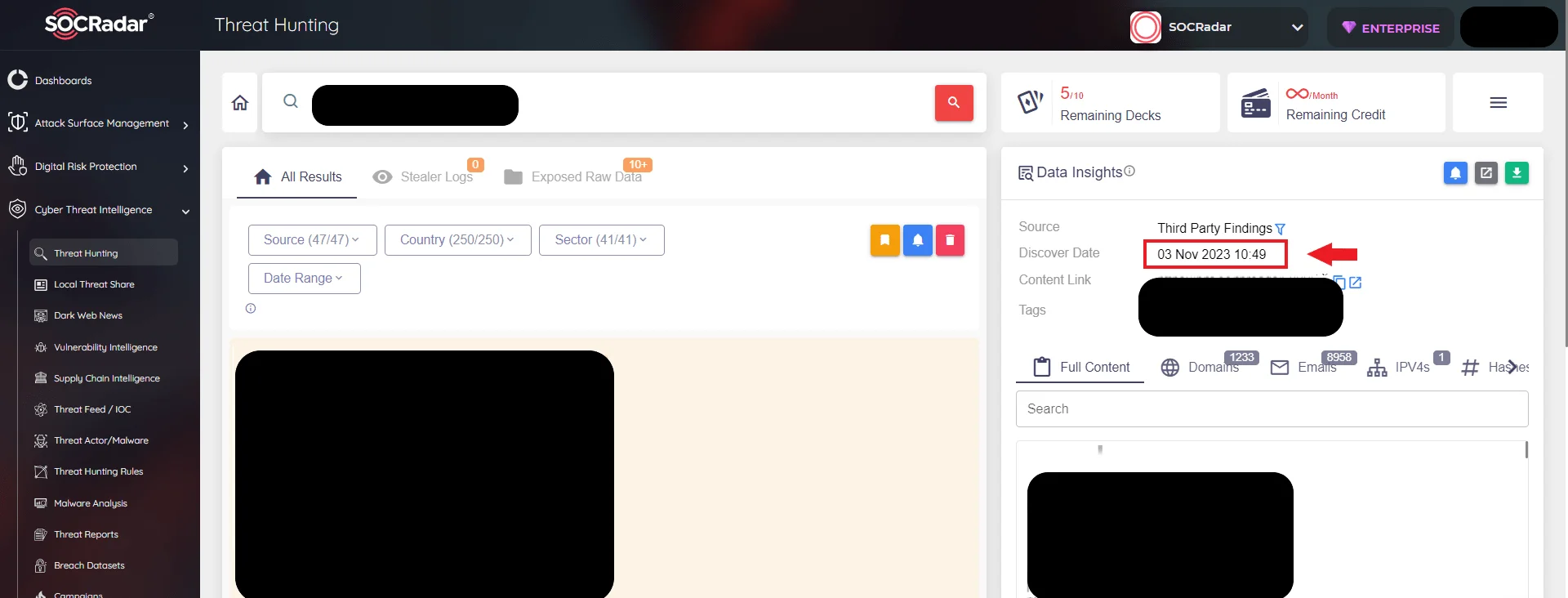
SOCRadar Threat Hunting
Although conducting such research from open sources is possible, traditional methods may not work if the data source is the Dark Web. However, our suggestion for searching outside the Dark Web is to learn the Google search functions to make specific searches such as file type, and certain date ranges.
Breach Datasets and Stealer Logs
As mentioned above, many datasets can be exfiltrated in various attacks and sometimes exposed to the public due to misconfiguration. In such cases, threat actors waste no time in using them. Such data can be offered for sale, phishing attacks can be prepared with the PII obtained, and sometimes unauthorized access can be obtained by leaking credentials.
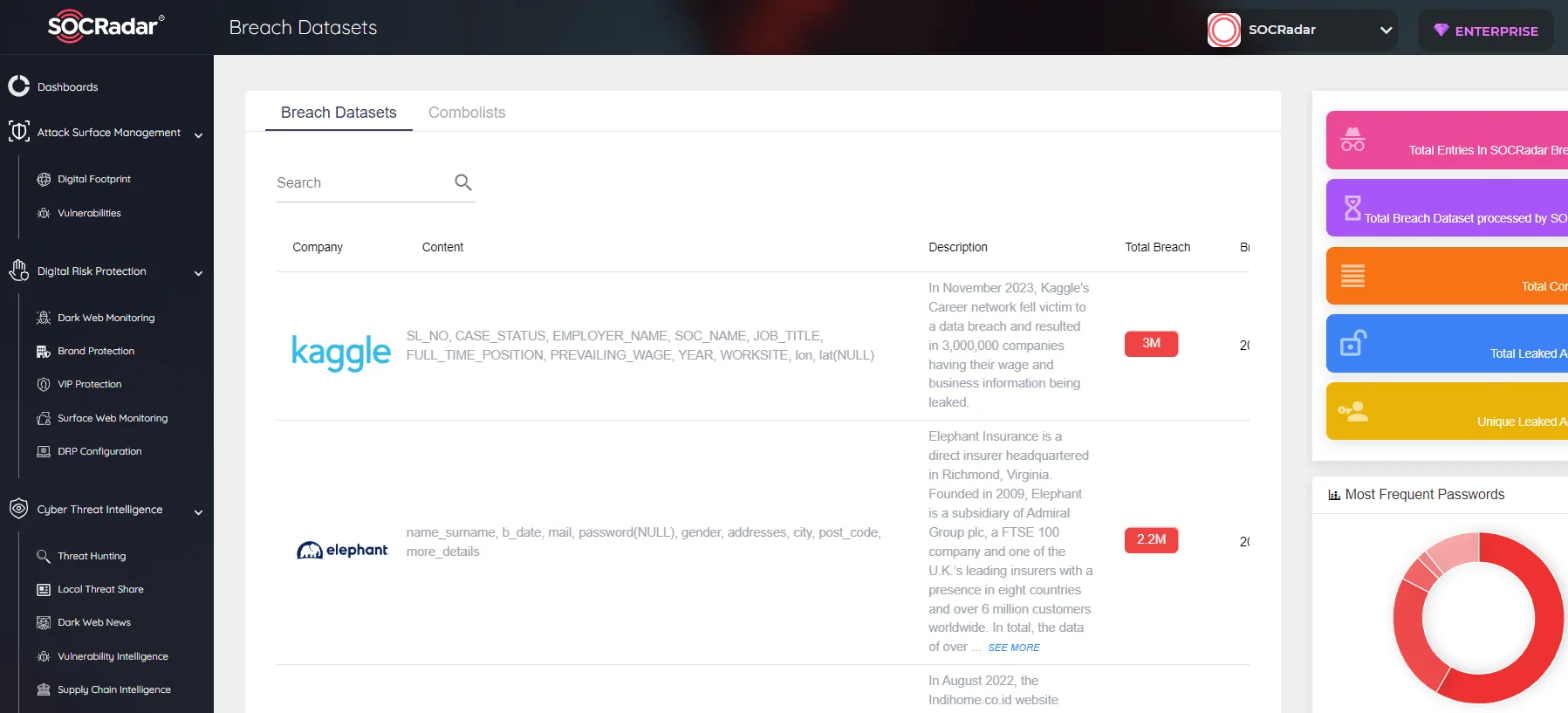
SOCRadar Breach Datasets
Of course, these leaks or lists scraped within the leaks can be offered for sale as new data, and in this case, it may cause institutions and people who experienced a leak to think that they have experienced a leak again. Of course, control is necessary to be on the safe side, but with the help of CTI, you can find out whether there is a new leak and what information the leaks contain. For example, SOCRadar can help you cross-check by recording the information in these datasets, such as their date and size.
Attack Methodology
Another fact-checking methodology is to become aware of the groups’ capacities or TTP. Although every system can ultimately be hacked, it should be compared with the capacity of the group claiming parallel with the reach of the claim. When news of significant breaches and infiltration comes from APT groups and Ransomware groups, it resonates relatively close to the truth. But a hacktivist group that carries out cheap defacement attacks every day and claims to have hacked a critical infrastructure should initially be approached with great skepticism.
For example, if we go through a group, let’s check a leak claim by SiegedSec, a member of the Five Families hacker collective.
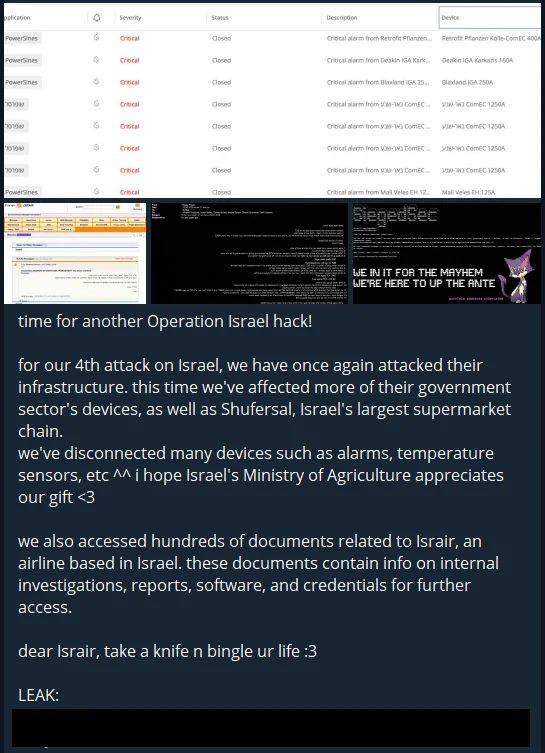
SiegedSec’s Telegram post, an alleged leak file is attached
When we look at SOCRadar’s SiegedSec profile article, we can see Exfiltration Over Web Service (T1567) and confirm that they can exfiltrate data from the organizations they infiltrate, strengthening the claim one step further.
Again, when it is possible to obtain outputs about the capacity and purpose of the group from the sections in the article such as “How Do They Attack, What Are Their Recent Activities, and Their Targets”, we can understand that this type of attack is suitable for common attack methodologies.
DDoS Claims
DDoS attacks appear to be the primary attack method, especially for hacktivists. Various groups share news of dozens of DDoS attacks and successful service downs every day. However, in order to understand their impact, it is necessary to learn how long these attacks last and whether they disrupt the functioning of the system.
For this reason, threat actors use the check-host website as evidence to prove the veracity of their claims. You can check whether the servers are down or not through similar websites and observe how big the outage is.
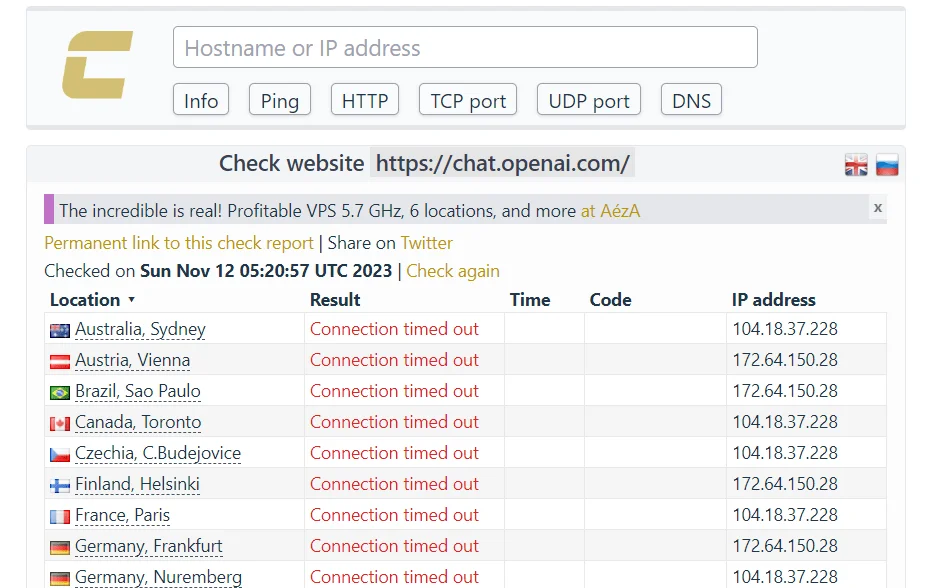
Anonymous Sudan’s proof for taking down OpenAI
Defacement Attacks
In defacements, which is also a popular attack method, it is not difficult to check the accuracy of the claim. We can verify these by taking screenshots and seeing that the website is still in that state when accessed, or by seeing its old state with sites such as Wayback Machine.
However, the point to be considered here is different. For example, during the Israel-Hamas conflict, you may have come across news such as many of us hacked 50-100-200 Indian websites. Most of the time, even if their claims are technically true, this number includes subdomains of the same domain, unused domains, and amateur websites. So, what needs to be taken into consideration here is to examine what kind of websites are attacked rather than the size of the number.
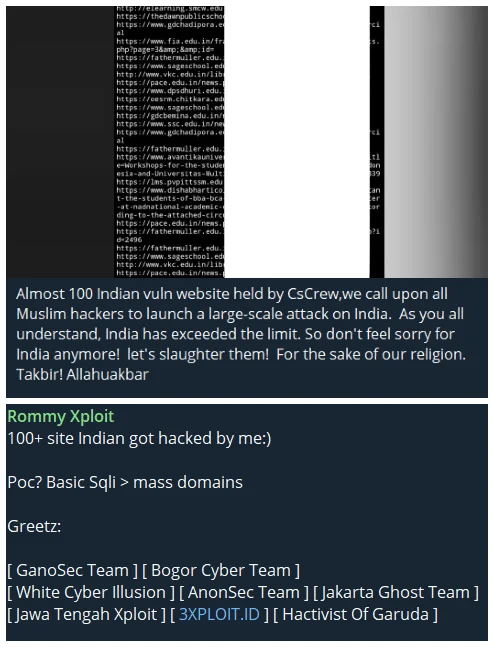
Some Telegram posts from hacktivist groups, why is it always 100?
Critical Allegations
Critical claims are generally the cyber incidents that are most difficult to verify. It is often not possible to reach a definitive conclusion without an investigation, especially in events that may have a major impact, such as hacking of SCADA systems, military systems, and emergency alarming systems. Especially recently, many SCADA hacking allegations have emerged during the Israel-Hamas conflict. We have recently identified scenarios where severe cyber threats target such systems and are truly successful and sent the news and precautions to the necessary countries as an alert e-mail.
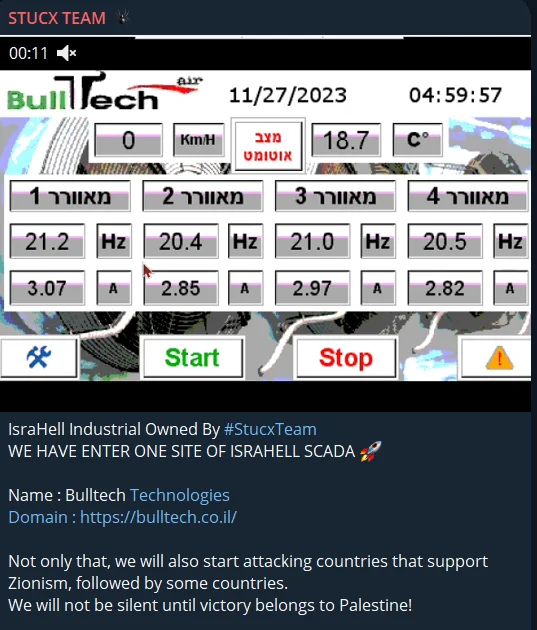
Hacked SCADA allegation
However, such claims were not approved by the authorities; only a tiny part of them were. Especially the simple interfaces of these industrial control systems seem to be the target of many fake claims because they are easy to imitate. In other words, we can say that a final decision cannot be reached without an official statement or investigation against such allegations.
A critical insight that should be added is that due to the nature of these SCADA systems, patch management is difficult and SCADAs produced by the same company may have similar vulnerabilities. In a scenario where one system is hacked, many other critical infrastructures may also be hacked.
Conclusion
In conclusion, the dynamic interplay between hacktivism, cyber incidents, and misinformation underscores the complexity of today’s digital security landscape. The Israel-Hamas conflict serves as a prime example of how global events can precipitate a surge in cyber activities, necessitating robust fact-checking and intelligence analysis. CTI and platforms like SOCRadar are pivotal in distinguishing real threats from misinformation, thereby safeguarding organizations from undue harm. As we navigate through this digital transformation era, accurate information, critical analysis, and sophisticated cyber intelligence tools remain paramount in ensuring cybersecurity in a world increasingly dependent on digital infrastructure.



































