
Dark Peep #3: Gone Phishing, We’ll Be Back!
It is clear that the world of the dark web will never be still, but the shape and size of the waves can change, and sometimes, there are still areas in this vast sea of cybercrime.
So, what happened this time, let’s take a look at what caught the attention of the SOCRadar team among the interesting events of the dark web!
Welcome to Dark Peep #3:

Ransomed’s New Forum Blossoms on the Dark Web
Evil Rabbit Inc. and other actors couldn’t leave RansomForums in peace, and finally, Ransomed crew opened a new forum called “Ransomed”, apparently opening a new page on the Dark Web.
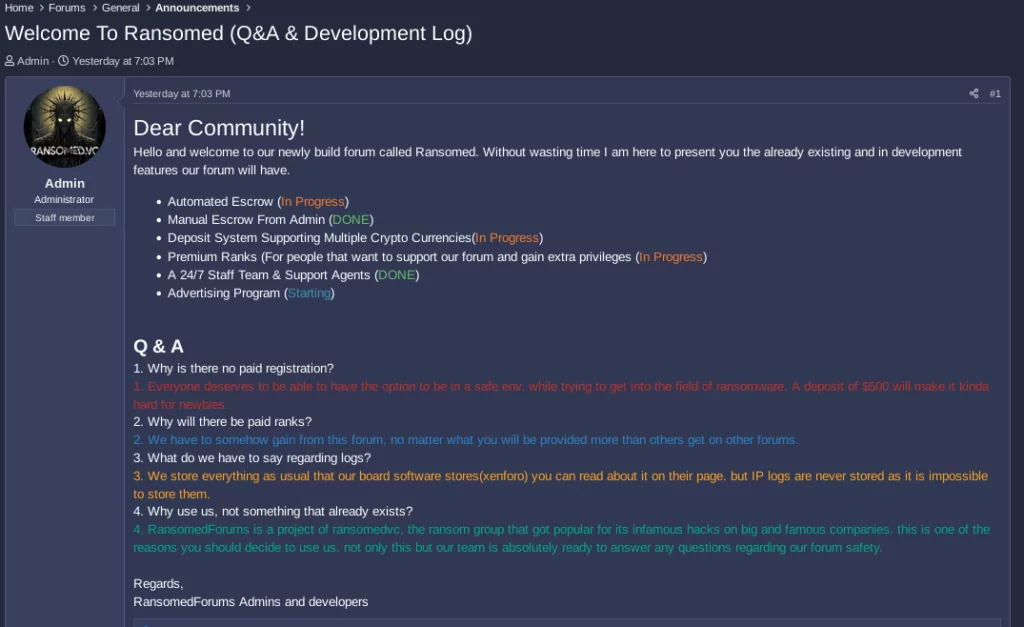
We wish the Ransomed crew, who extort their victims by using GDPR as a weapon, who recognize the employees of some cyber security companies as “threat actors” as if they themselves are not threat actors, good luck in their new forums, and we want them to know that we will continue to monitor them(!)
Every Day Brings New Ransomware, Here is qBit:
A new flower has bloomed in the world of ransomware. Meet qBit ransomware (or let’s meet together, shall we?)
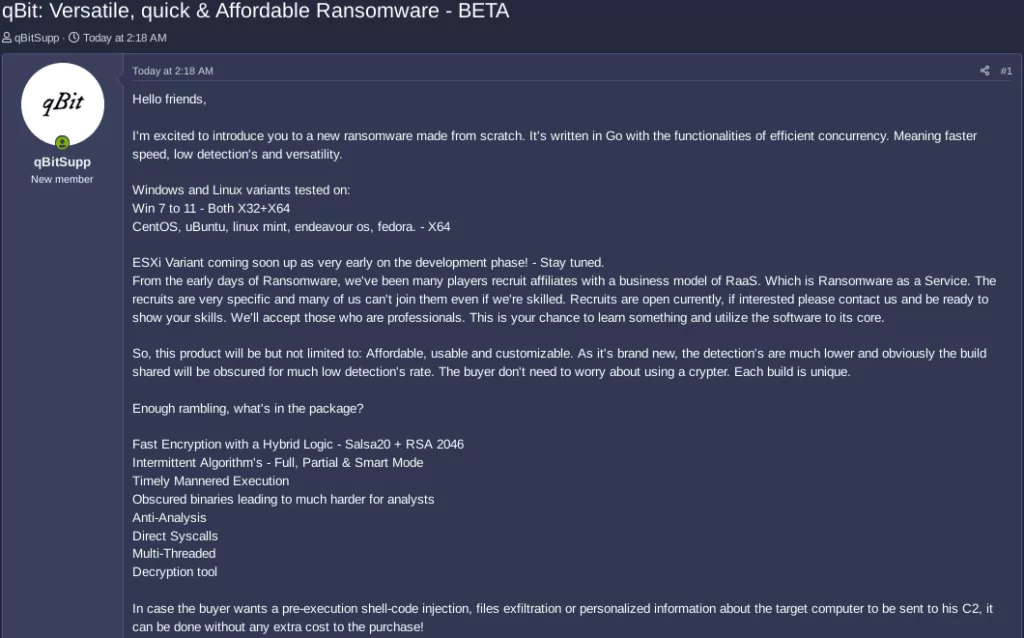
This new strain of ransomware promises speed, low detection rates, and versatility. This brand-new threat, developed from scratch, promises unparalleled speed and efficiency, thanks to its programming in Go. Notably, it’s designed to operate seamlessly across both Windows and Linux platforms, including versions from Windows 7 to 11 and Linux distributions like CentOS, Ubuntu, and Fedora. With plans to launch an ESXi variant, qBit hints at ambitions to target virtual environments. Following the Ransomware as a Service (RaaS) model, qBit is currently recruiting skilled affiliates, emphasizing its unique and customizable nature. The ransomware boasts features like rapid encryption using a hybrid of Salsa20 and RSA 2046, multiple algorithm modes, and obfuscated binaries, making it a potential stealthy menace.
Movie Recommendations From a Cybercriminal, Don’t Miss It!
Seems the extortion team Snatch is not just ‘byte’-ing into data but also digging into some cinematic bytes! If you’re in watching movies about “hack”, snatch’s list might just ‘decrypt’ your weekend plans. Stay safe both online and on the couch!
P.S.: Ghost in the Shell caught our attention in the list, if possible, watch its ’95 anime movie, you won’t regret it!
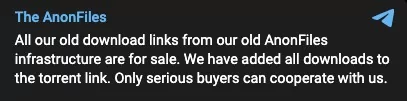
The AnonFiles: We’re Closing, Big Sale!
It looks like AnonFiles has put all of its download links up for sale, so those who think they might be worth something might want to consider taking advantage of the discount.
Hunters International: Successor of the Ransomware Group Hive?
After the Trigona takedown, another actor who has caught our attention is on our radar: Hunters International.
According to cybersecurity researchers, the Hunters International group, whose source code is more than 60% similar to the Hive ransomware, has started its first activities.
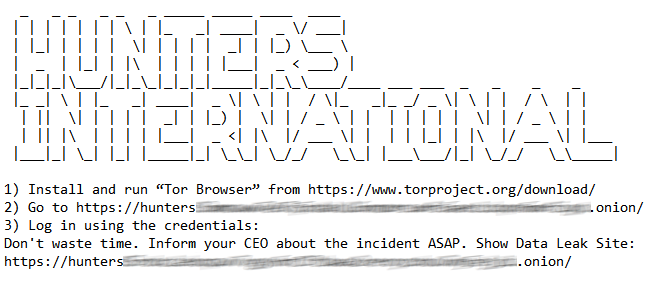
Hunters International, which we assume works with the double-extortion method, soon broke its silence and made a statement on this issue.
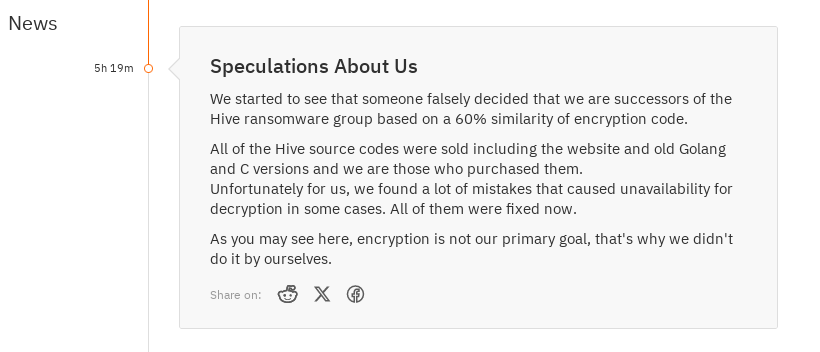
The group addressed rumors suggesting they are successors of the Hive ransomware group due to a 60% similarity in encryption code. They clarified that they purchased the Hive source codes, including the website and old Golang and C versions. They encountered errors in the codes, which hindered decryption in certain instances, but those issues have since been resolved. Contrary to speculation, their main objective isn’t encryption.
There Can Be Doubts About Whether to Conduct a Survey or Not
The ACEH was having an indecision about the nickname and wanted to clarify it with a poll. But they soon decided that they preferred their own decisions over the community’s, so they removed the poll, interesting…
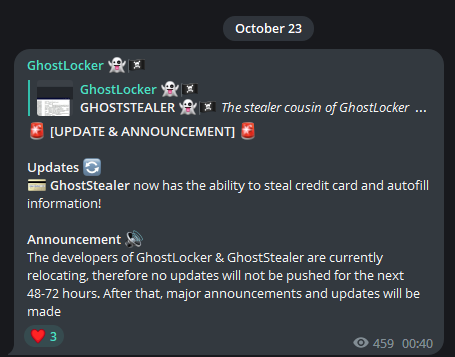
The Ghost Will Be Missing for 72 Hours.
GhostLocker announced in its latest post that it has added new features, including the ability to steal credit card details. In addition, the team announced that they will not post for a period of 48 to 72 hours, indicating that new developments are on the way.
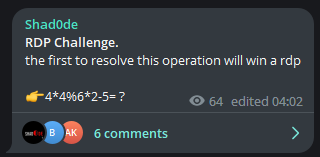
You Have to Use Your Brain to Get RDP Access!
Shad0de, which we have been closely following, continues to add new spice to the RDP giveaways. This time, our actor will give RDP access to the first correct answer to an ultra-complex(!) math question, so get your calculators ready!
Our One-eyed Knight Continues to Grow Stronger
Knight ransomware team, which changed its name from Cyclops to Knight, announced version 3.0 on the Ransomed forum
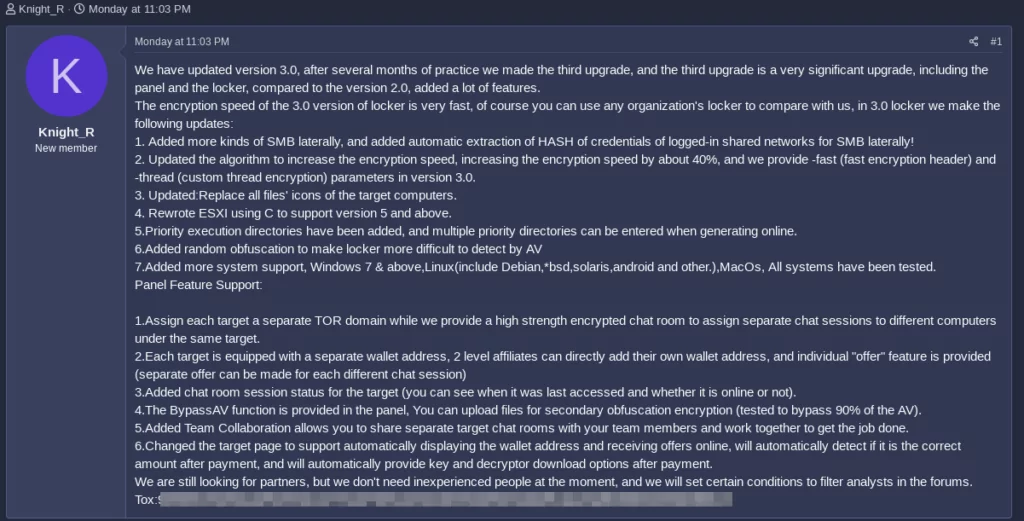
This update offers faster encryption speeds, increased lateral movement in SMB networks, and improved evasion techniques. The software now supports ESXI version 5+, various operating systems, and features a user panel that assigns unique TOR domains and encrypted chat rooms for each target. Each compromised system is also linked to a distinct cryptocurrency wallet.
Bears on YouTube
The NoName057(16) group, famous for their DDoS activities against Russophobia, seems to have decided to become an influencer to continue its fame on YouTube, don’t forget to subscribe and turn on notifications!
The Dark Web is not at rest and we don’t expect it to become slower. You can use Dark Web News in SOCRadar XTI’s Cyber Threat Intelligence module to keep up to date with developments on the Dark Web:




































