
Dark Web Highlights: Xiaomi Data Exposed, eToro Leak, and Crypto.com Access Sale
SOCRadar’s Dark Web Team uncovered alarming activity on hacker forums, including a powerful new Mirai botnet service for massive DDoS attacks. Further findings include leaked databases from eToro and Xiaomi, raising concerns about internal operations and customer security, as well as unauthorized Crypto.com access for sale. A partnership-seeking post also emerged, targeting individuals experienced in crypto-related operations, including password cracking and deepfake manipulation for Binance displays.
Receive a Free Dark Web Report for Your Organization:
New Mirai Botnet Service is Detected
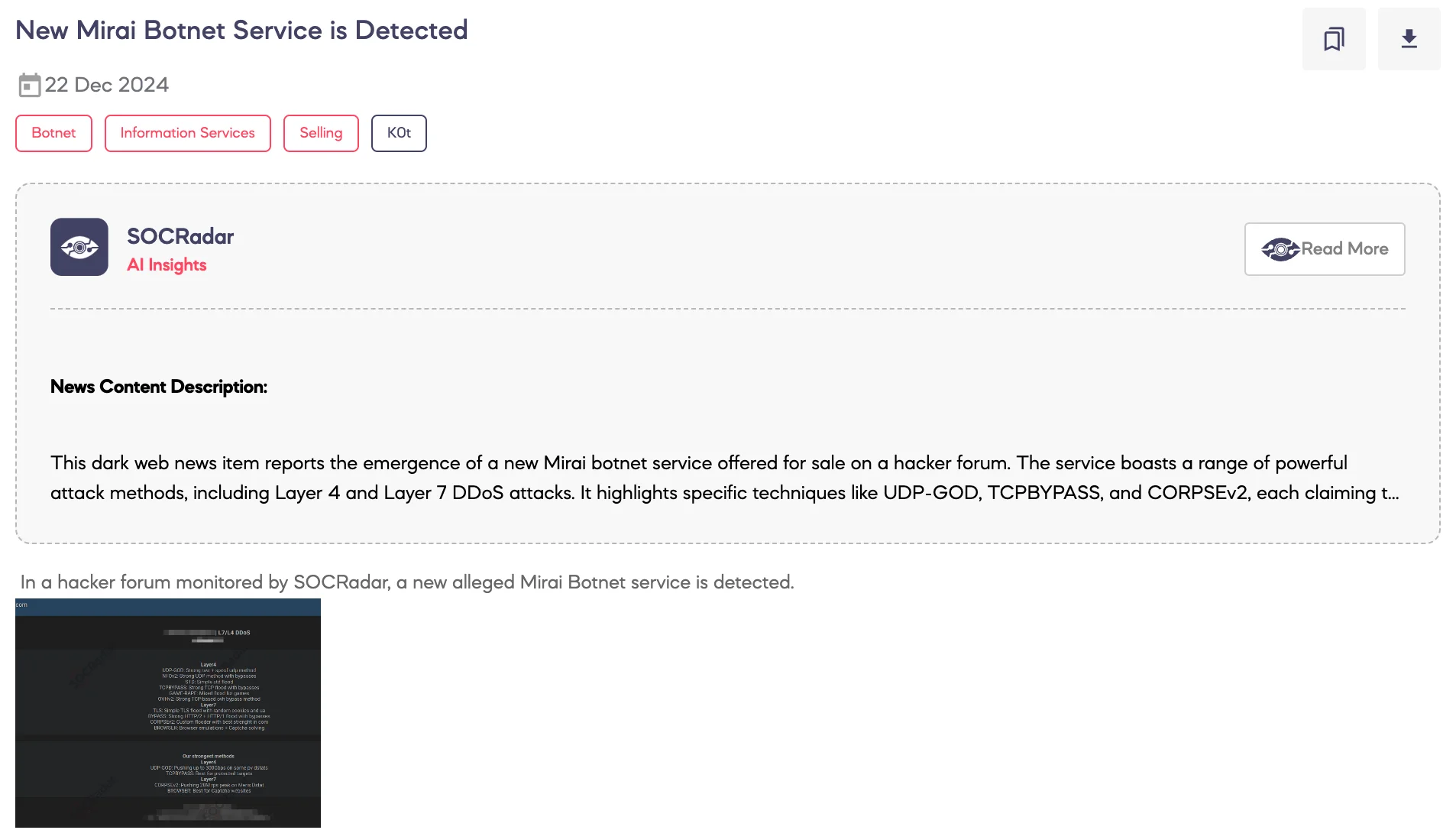
SOCRadar Dark Web Team detected a post advertising a new alleged Mirai botnet service on a hacker forum.
According to the threat actor, the botnet is designed to execute high-capacity Layer 4 (L4) and Layer 7 (L7) Distributed Denial-of-Service (DDoS) attacks. The advertised methods include:
- Layer 4: Techniques such as UDP-GOD, NFOv2, STD, TCPBYPASS, GAME-RAPE, and OVHv2, claimed to deliver powerful UDP and TCP floods, targeting both unprotected and protected systems. Some methods are alleged to achieve up to 300 Gbps in attack volume.
- Layer 7: Methods include TLS floods, HTTP/2 and HTTP/1 bypasses, CORPSEv2 (described as a highly effective custom flooder), and BROWSER (which includes browser emulations and CAPTCHA-solving capabilities). The CORPSEv2 method is claimed to peak at 28 million Requests Per Second (RPS).
The post emphasizes the botnet‘s strength in bypassing advanced security measures, demonstrating an ongoing enhancement of DDoS attack tools in cybercrime ecosystems.
Alleged Investor Database of eToro is Leaked
SOCRadar Dark Web Team detected a post on a hacker forum claiming an alleged leak of the investor database belonging to eToro, a global trading platform specializing in cryptocurrency, stocks, and other financial investments.
According to the threat actor, the database contains information on cryptocurrency investors worldwide. The actor states that the data has been made available for download and hints at releasing additional parts of the database for free if the post generates significant interest.
Alleged Database of Xiaomi is Leaked
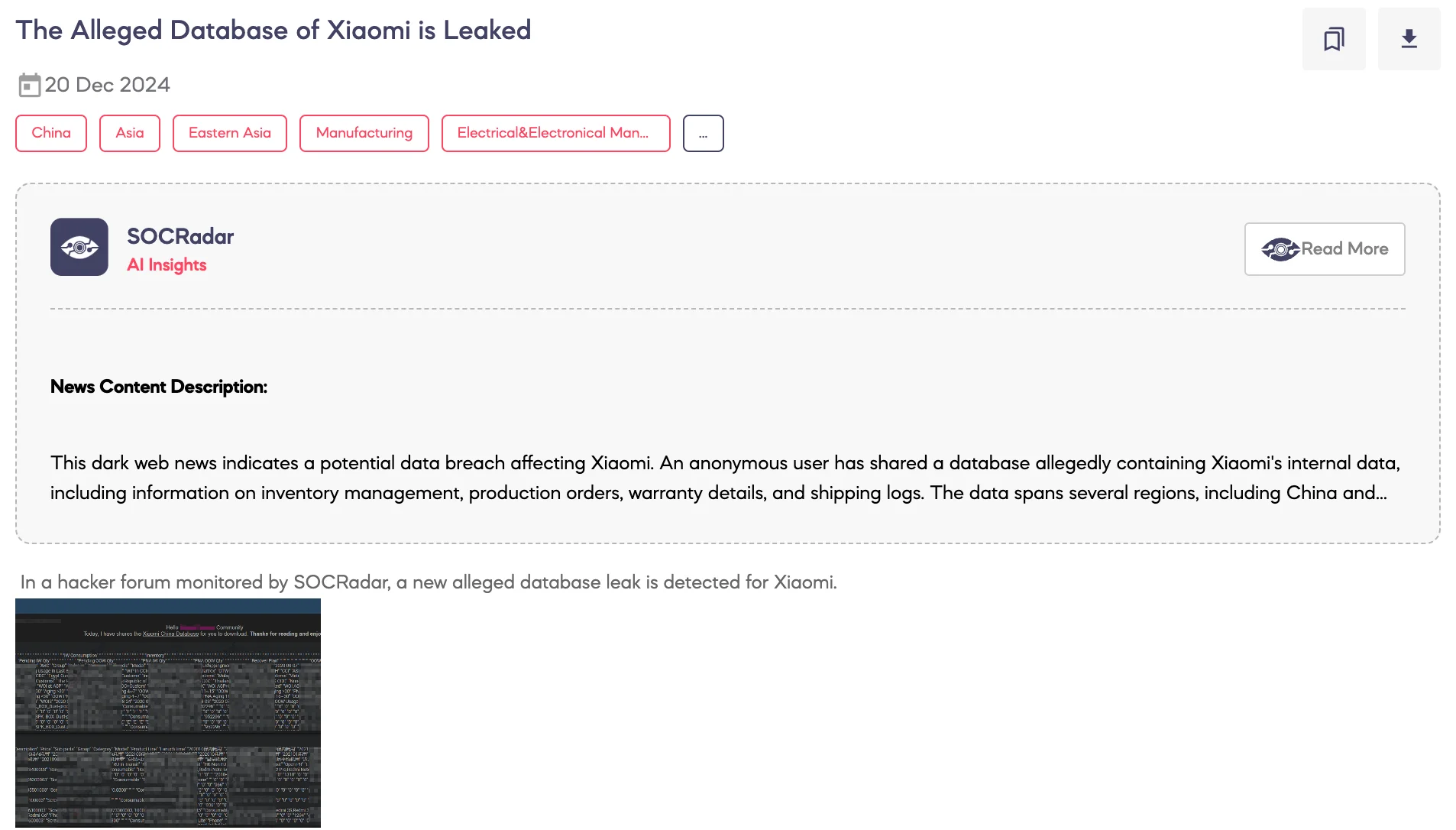
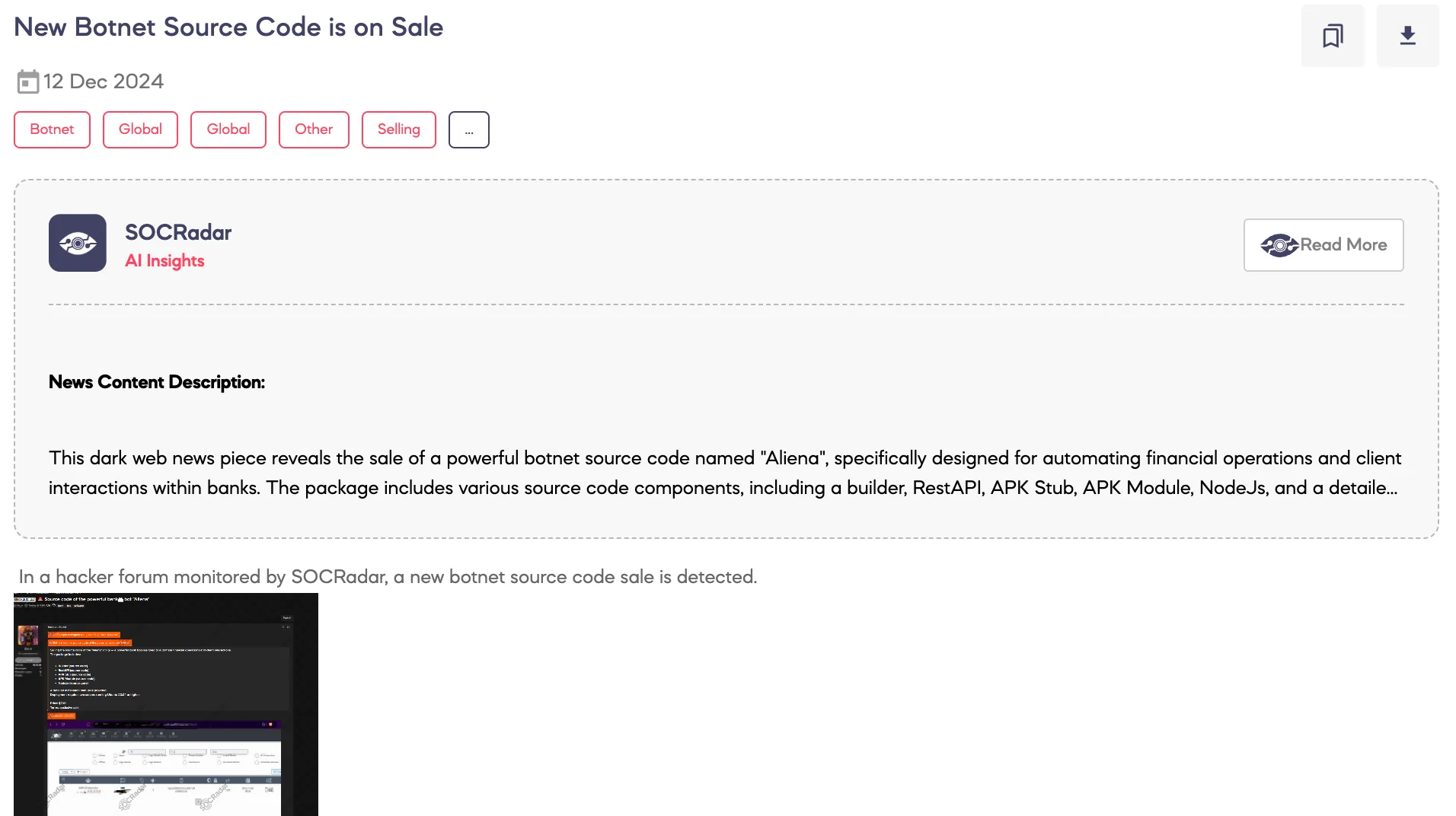
SOCRadar Dark Web Team detected a post on a hacker forum claiming an alleged database leak involving Xiaomi.
The threat actor claims to have shared a wide range of files purportedly from Xiaomi’s systems. The leaked data is said to include CSV files containing service orders, warranty lists, parts returns, parts management, and warehouse maps specific to China.
Excel files reportedly include shipping invoices and warehouse data, while log files detail email communications, ERP synchronization, and shipping activities. Additionally, SQL files are claimed to contain database dumps for inventory and ERP synchronization, and ZIP files are said to archive various other data, including usage statistics for Xiaomi mobile phones overseas.
According to the threat actor, the data is categorized by topics such as warranty, parts, warehousing, and system integration, with significant portions tied to Xiaomi’s operations in Chinese regions and overseas markets.
Alleged Unauthorized Support Access Sale is Detected for Crypto.com
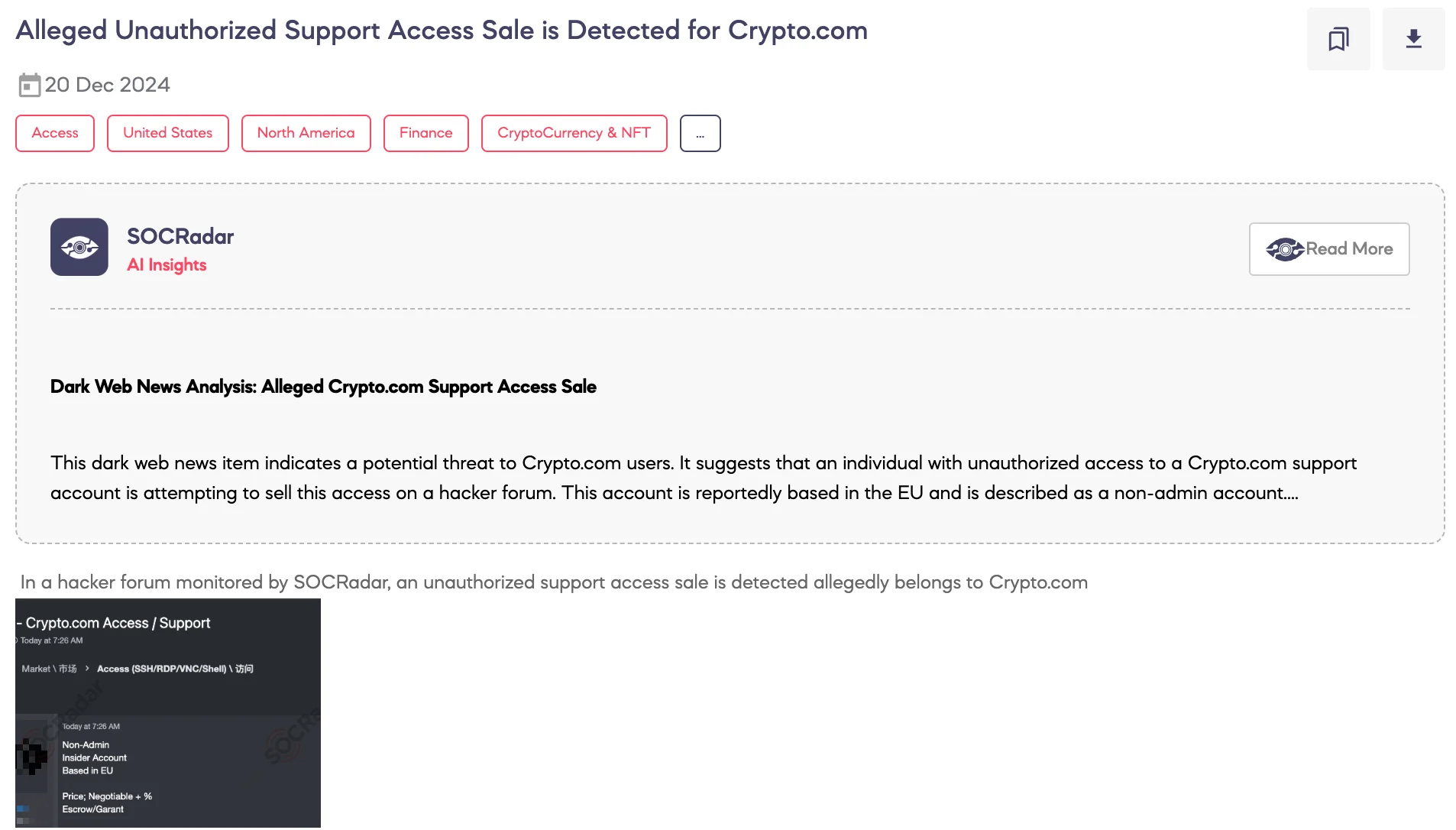
SOCRadar Dark Web Team Detected a post on a hacker forum advertising the sale of alleged unauthorized support access associated with Crypto.com, a cryptocurrency trading and payment platform.
The threat actor claims to offer a non-administrative insider account based in the European Union. The post states that the pricing is negotiable and includes a percentage-based fee. The threat actor also mentions the use of escrow or guarantee services for the transaction. This sale, if valid, could pose risks to Crypto.com’s internal operations and customer security.
A New Partnership Searching Post is Detected
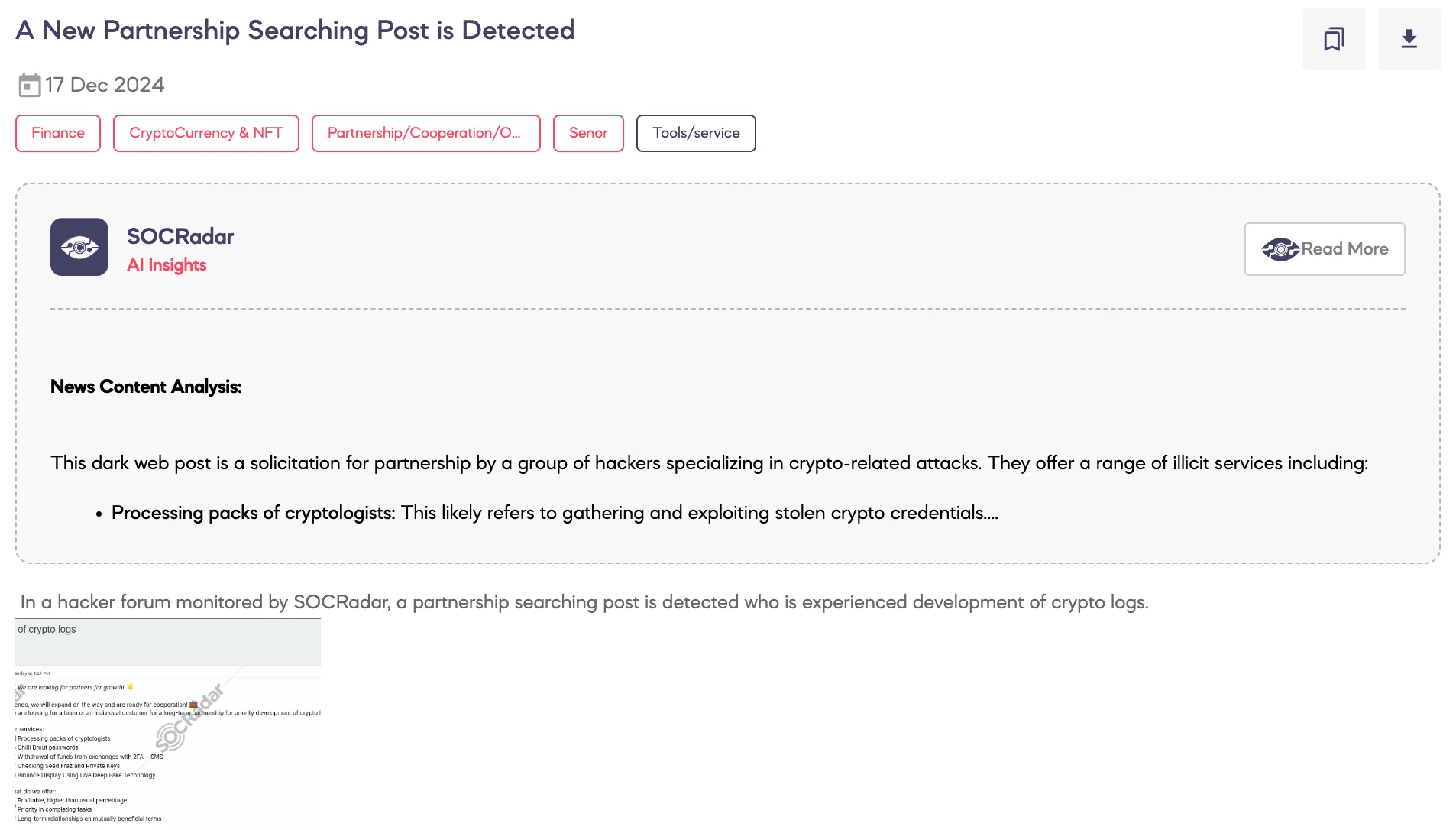
SOCRadar Dark Web Team detected a post on a hacker forum seeking partnerships for crypto-related operations.
The threat actor expressed interest in forming long-term partnerships, targeting individuals or teams experienced in crypto log development. Their advertised services include processing cryptographic data, cracking passwords, bypassing two-factor authentication (2FA) and SMS verification for fund withdrawals, verifying seed phrases and private keys, and utilizing live deepfake technology to manipulate Binance displays.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































