Dark Web Profile: GlorySec
GlorySec is a hacktivist group that has quickly gained notoriety for targeting governments and institutions it deems corrupt, particularly in Russia and Venezuela at the time of writing. Their attacks are often publicized on their Telegram channel, where they blend anti-authoritarian rhetoric with reports of their cyber activities.
Who Is GlorySec?
GlorySec is still a relatively new but rapidly growing hacktivist group that aligns itself with, as in their statements, Anarcho-Capitalist ideals. By the definition of these ideas, the group possibly advocates for minimal government intervention, promoting individual freedoms through the non-aggression principle—a core tenet of their ideology. As in their actions, GlorySec claims to support Western political values, positioning themselves against what they view as authoritarian regimes and corrupt institutions, with a particular focus on countries like Russia, China, and their allies.

Their logos on GlorySec Telegram channel
How Do They Operate?
Their operations are primarily conducted and publicized through Telegram, where they frequently share details about their cyberattacks, including data breaches and distributed Denial-of-Service (DDoS) attacks. GlorySec once collaborated with other hacktivist groups, such as ThreatSec and KromSec, to amplify their impact. The group’s rhetoric is allegedly deeply anti-authoritarian, framing their cyberattacks as a form of digital resistance against oppression and corruption. They have openly declared their mission to expose and dismantle corrupt systems, often encouraging others to join their cause or continue their efforts under the GlorySec banner, as in their sayings.
Again, similar to many hacktivist organizations, in addition to data leaks, there are also attack shares such as DDoS, Doxxing, Defacement, and access share in the main Telegram channels and backup channels where they share data leaks.
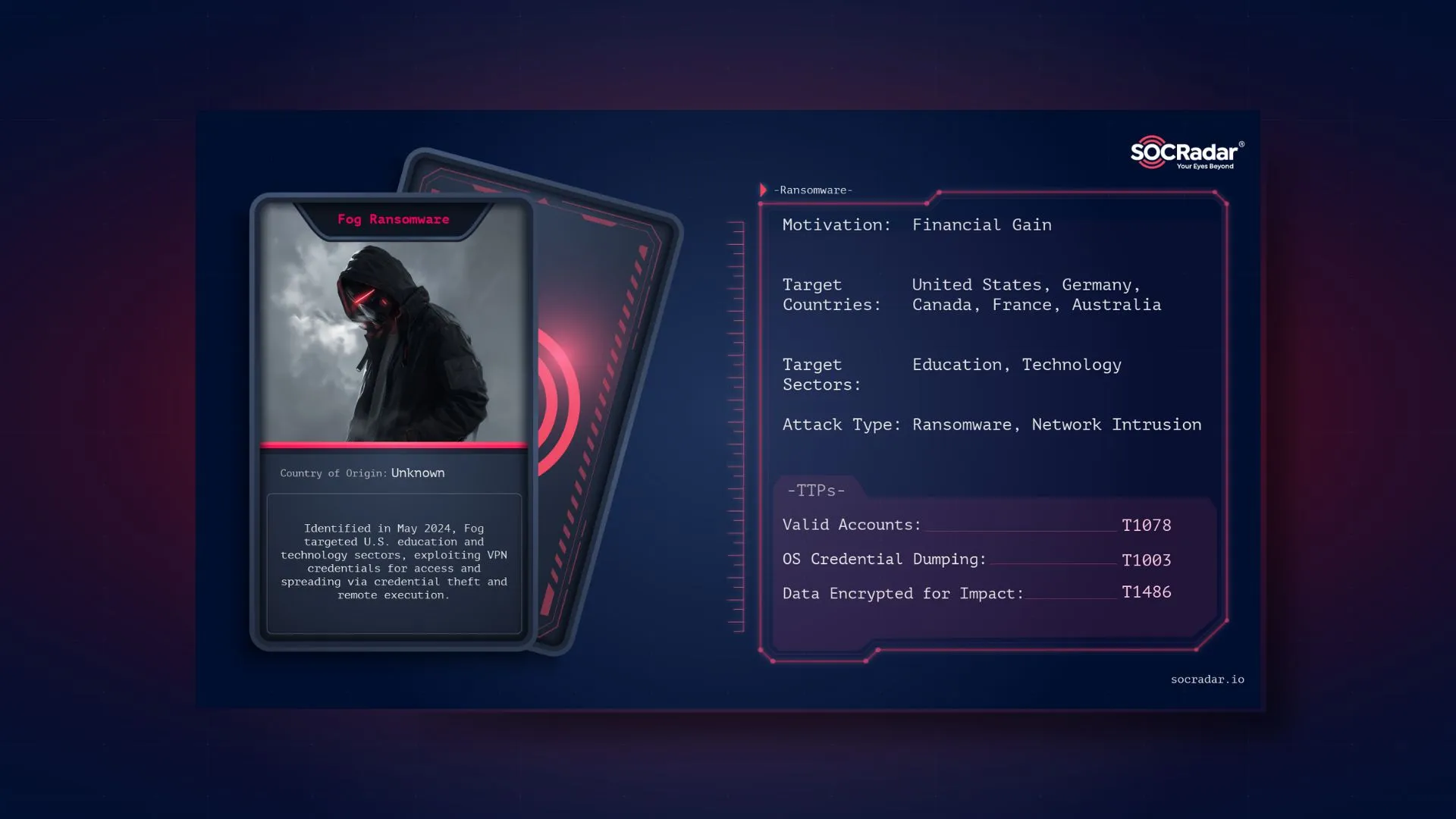
One of the group’s most interesting aspects is choosing their leaders through “democratic” voting for the supposed leadership role.
The post about their first leadership elections
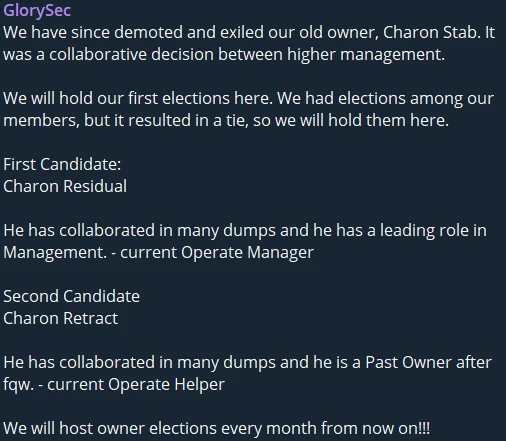
While their methods of selecting a leader and openly participating in target selection reflect a democratic approach for the hacktivist group, the abrupt decisions to end operations on Telegram, the consistency of their attacks, and their reflective actions make it hard to take the group’s “threat” level seriously, despite fitting the hacktivist label.
Project could have been canceled, GlorySec’s Telegram channel
What are Their Targets?
GlorySec, while generally targeting entities in the Eastern Hemisphere, tends to follow a Western-aligned agenda, though not consistently. The table below ranks the downloadable leaks from the channel labeled GlorySec Storage.

Leak post numbers in their Telegram channel
In addition to leak posts, as we mentioned above, there are also DDoS, Defacement, and Doxxing attacks and targets such as Burkina Faso and Armenia.
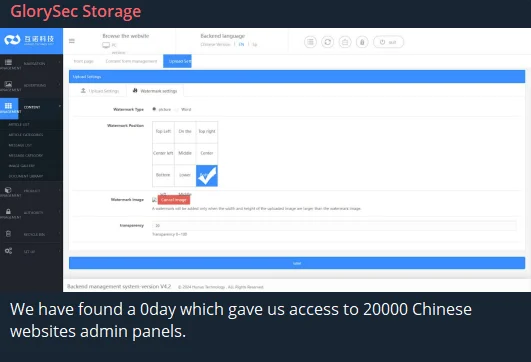
Alleged 0day access for 20.000 Chinese websites
It should be noted that even if they make more assertive claims, such as zero-day exploits, their accuracy is not sure. The group, which has recently shifted its primary focus to Venezuela, continues to launch various attacks, with a particular emphasis on defacement.
In Summary
GlorySec has quickly gained attention with its anti-authoritarian campaigns, particularly targeting governments and institutions in Russia and Venezuela. While their attacks are frequently publicized and backed by hacktivist ideals, the group’s erratic actions and inconsistent agenda raise questions about their long-term threat. Nevertheless, staying vigilant and monitoring their movements through platforms like SOCRadar can provide crucial threat intelligence and help mitigate potential risks.
How SOCRadar’s Operational Intelligence Helps You?
SOCRadar’s Operational Intelligence, Threat Actors Intelligence tab can provide valuable insights into hacktivist groups like GlorySec by monitoring their online activities, especially on platforms like Telegram where they announce their operations. With real-time alerts, organizations can stay informed about emerging threats, leaked data, and ongoing campaigns. The module’s comprehensive tracking of ransomware, DDoS, and other cyberattacks ensures a proactive defense by enabling timely response measures.
SOCRadar Operational Intelligence, Threat Actors Intelligence
Tactics and Techniques Table
| Tactic | Technique |
| Initial Access | T1190 Exploit Public-Facing Application |
| Impact | T1491 Defacement |
| Impact | T1499.002 DDoS: Network Flood |
| Collection | T1589.002 Gather Victim Identity Information: Email Addresses |
| Exfiltration | T1530 Data from Cloud Storage Object |
| Credential Access | T1078.003 Valid Accounts: Local Accounts |