Dark Web Profile: Just Evil
[Update] October 23, 2024: “Founder of Just Evil and KillNet Allegedly Killed in Drone Attack”
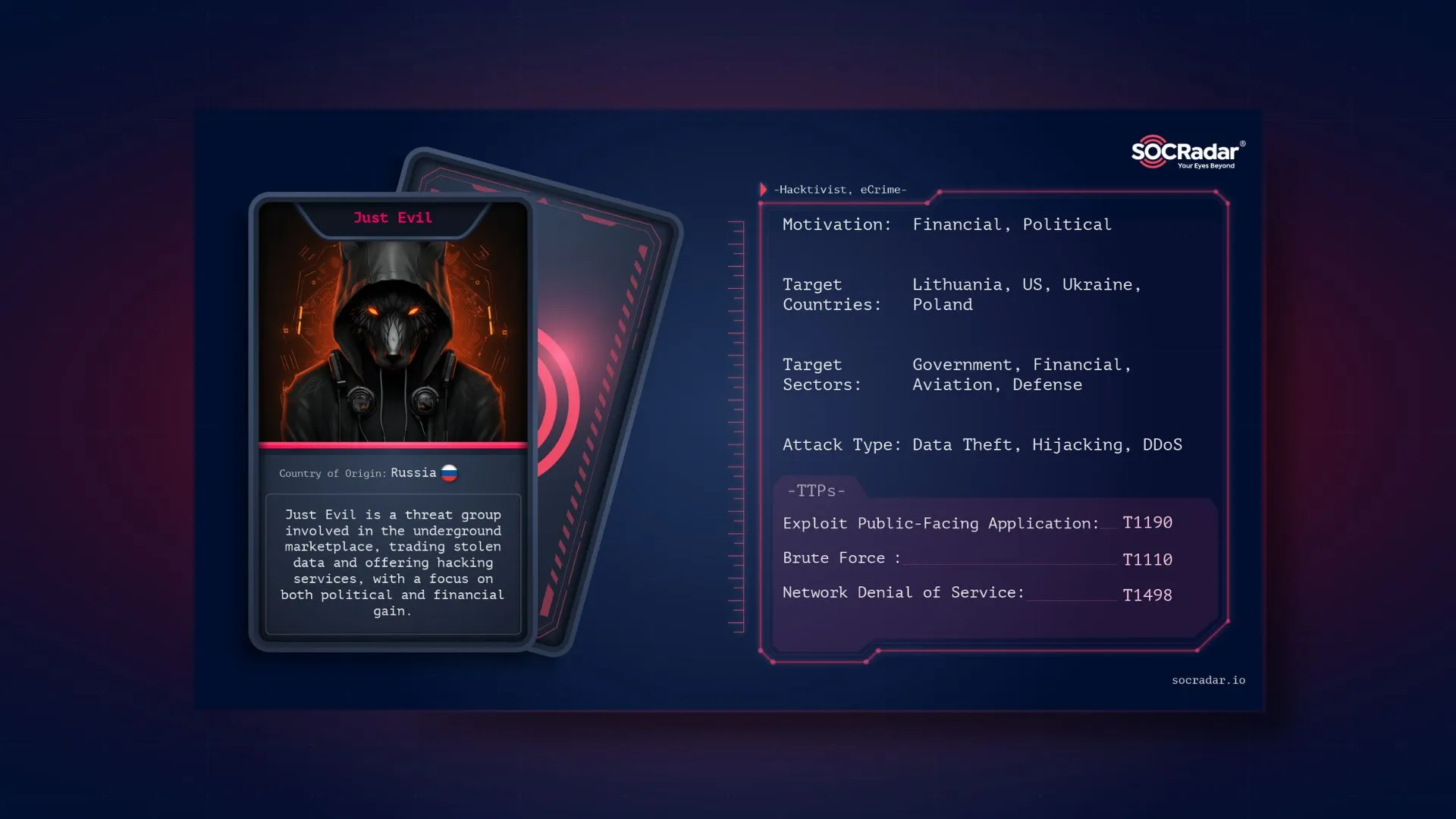
Just Evil is a pro-Russian cyber threat group formed in January 2024 by KillMilk. This group emerged following internal changes within KillNet, particularly regarding its sale to another owner and shift towards commercial motivations under the leadership of Deanon Club. Just Evil, like KillNet 2.0, is focused on maintaining an ideological mission, distancing itself from financial(!) motives to retain influence in the pro-Russian hacktivist landscape.

Just Evil’s Telegram logo
Who is Just Evil?
Short answer is KillMilk, ex-leader of KillNet. The original KillNet, widely known for its hacktivist operations, sold its primary Telegram channel to Deanon Club. This transaction marked a significant turning point, as Deanon Club shifted the group toward more commercial activities.

Threat actor card for Just Evil
Dissociating from this commercialization, KillMilk established Just Evil to maintain an ideological stance in the pro-Russian cyber community. At the same time, KillNet 2.0 another pro-Russian group was formed as a decentralized collective focused on non-commercialized, ideological missions, further fragmenting the pro-Russian cyber landscape.
Announcement post of Just Evil in January 31, 2024
However, the above description may lead to just another question.
Who is KillMilk?
KillMilk is a key figure in the pro-Russian cyber landscape, best known for leading the hacktivist group KillNet. Initially, he was seen as the driving force behind the group’s operations, which were heavily focused on supporting Russian geopolitical interests, particularly during the Russia-Ukraine war. Under his leadership, KillNet launched a series of high-profile DDoS attacks against Western entities, positioning itself as a prominent pro-Russian hacktivist group.
However, by early 2024, cracks begin to show in KillMilk’s leadership. Internal tensions arose, with several members of KillNet publicly accusing him of unethical actions and a lack of technical expertise, which they felt undermined the group’s credibility. These criticisms were further amplified when Russian news outlet Gazeta.ru identified KillMilk as being linked to Nikolai Nikolaevich Serafimov, a controversial figure with a questionable background, adding to the group’s internal discord.
Amidst this growing dissent, KillMilk decided to step down from his leadership role, handing control of KillNet over to Deanon Club. This transition marked a turning point for KillNet, as Deanon Club began steering the group away from its original hacktivist, patriotic mission toward a more financially motivated agenda. Before his departure, KillMilk had overseen some of KillNet’s largest-scale operations, including DDoS attacks on major targets such as Microsoft’s Azure, Outlook, and OneDrive.
For further information about Deanon Club and KillNet check out our relevant blog post: Beyond Hacktivism: Deanon Club, KillNet, and the Russian Dark Web Market Wars
Furthermore, in addition to these attacks, KillNet also attempted to expand its influence by forming a subsidiary group called KillNet Palestine during the Israel-Hamas conflict. However, due to the internal struggles within KillNet, the group was probably unable to play a significant role in the conflict. Despite this, one of KillNet’s close allies, Anonymous Sudan, remained active and continued to collaborate with pro-Russian cyber actors for some time. However now Anonymous Sudan is also defunct.
Following KillMilk’s exit, the fate of KillNet shifted dramatically. While the group retained its name, Deanon Club emerged as the primary force behind its activities. So, were these splits and changes in names and groups just about motivations?
What is Just Market?
We just discussed their intention to distance themselves from financial motives, but, as always, human nature finds it hard to resist greed.
Just Evil’s launch of Just Market raises questions about their ideological stance, which claims to distance itself from financial motivations. Despite positioning themselves as a group with decentralized, anti-commercial goals, their first market post directly contradicts this claim. Offering services like GMail access, cryptocurrency laundering, document forgery, and security auditing, Just Market appears to cater to cybercrime for profit.
Just Market launched in April of 2024
While Just Evil emphasizes that they don’t operate destructively within Russia, this limitation does little to align with their proclaimed ideological mission. Instead, it suggests a pragmatic approach to avoiding local repercussions while still engaging in illegal activities globally.
How Does Just Evil Operate?
Just Evil employs a variety of tactics and techniques that align with its mission of supporting Russian geopolitical interests. The group’s operations are specifically designed to target nations and organizations considered adversaries to Russia, with a strong emphasis on Western countries, NATO members, and Ukraine.
One of the primary tactics used by Just Evil is Distributed Denial of Service (DDoS) attacks. These attacks overwhelm target systems with a flood of internet traffic, causing significant disruptions to online services and operations in the targeted nations. This method of attack is intended to cripple the digital infrastructure of countries seen as enemies.
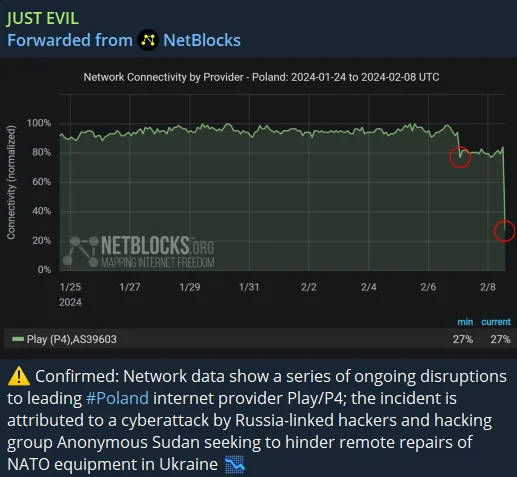
Attack on Polish internet provider
Another notable tactic is website defacement. Just Evil frequently defaces websites to publicly shame and spread propaganda against Western governments and organizations. This approach not only damages the reputation of the targets but also serves to disseminate anti-Western messages and propaganda.
Data breaches are also a key component of Just Evil’s strategy. By infiltrating and stealing sensitive information, the group aims to make this data public or use it strategically. This can involve blackmail, espionage, or other forms of strategic manipulation, further destabilizing the security and operational integrity of their adversaries.
While KillMilk led the KillNet group, most threats involved DDoS attacks. However, as Just Evil under KillMilk’s leadership and with the new(?) team, their tactics have shifted toward more destructive methods, including leaking classified data and gaining initial access to critical industries.
In terms of leadership, Just Evil is spearheaded by KillMilk, a prominent figure from the original KillNet operations. His leadership continues to guide the group’s activities and strategic objectives, ensuring that their operations remain focused on their ideological goals.
The motivation behind Just Evil’s actions is deeply rooted in pro-Russian geopolitical objectives. The group’s primary aim is to disrupt and undermine Western governments and institutions, thereby aligning its operations with broader Russian interests.
What are Their Targets?
The Just Evil team, led by KillMilk, has consistently targeted NATO and its allied nations, though Ukraine has not been a significant focus since the Just Evil launch. Lithuania is their most frequent target. The graphic below illustrates the unique posts aimed at specific countries and their organizations, though some numbers may reflect the same attack with varied outcomes or follow-ups.
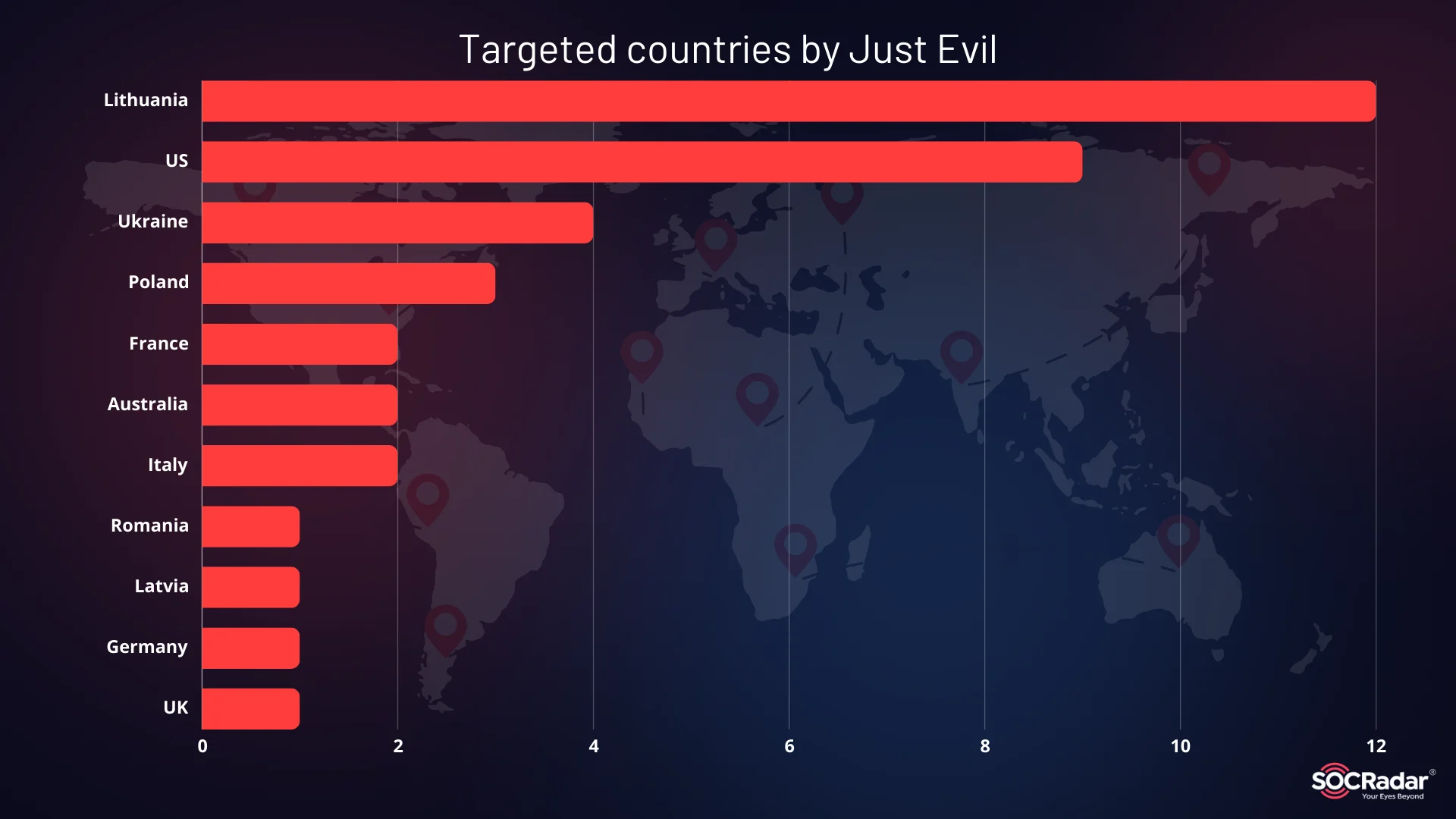
Targets specified in their Telegram channel
Once again, the US is a key target, along with countries that closely align with Lithuania. The rest of the list indicates that their actions align with Russia’s strategic interests.
In Summary
Just Evil represents an evolution in the pro-Russian cyber landscape, emerging as a key player with ideological roots, though not completely immune to financial motivations, as seen with the launch of Just Market. While the group seeks to distance itself from the commercial activities that defined KillNet’s later phase under Deanon Club, its actions suggest a blend of hacktivism and pragmatic cybercrime.
Just Evil’s operations, including DDoS attacks, website defacements, and data breaches, are primarily aimed at Western nations and NATO members, aligning with Russia’s geopolitical goals. However, the contradictions in their actions and stated motivations leave room for speculation about the true nature of the group’s objectives.
How SOCRadar Can Help
SOCRadar’s advanced threat intelligence capabilities can provide critical insights into groups like Just Evil by monitoring dark web channels and forums, where Just Evil operates and promotes illegal services. SOCRadar’s Dark Web Monitoring can track discussions, data leaks, and market activities associated with Just Evil, allowing organizations to stay ahead of potential threats. Moreover, Attack Surface Management features offer proactive vulnerability assessments, while Threat Actor Intelligence service helps defend against the exact tactics employed by Just Evil. SOCRadar provides a comprehensive suite of tools to mitigate risks from this evolving threat actor, ensuring organizations can safeguard their assets and operations effectively.
SOCRadar’s Threat Actor Intelligence
MITRE ATT&CK Tactics and Techniques
| Tactic | Technique | MITRE ID |
| Initial Access | Exploit Public-Facing Application | T1190 |
| Credential Access | Brute Force | T1110 |
| Command and Control | Application Layer Protocol | T1071 |
| Impact | Network Denial of Service (DDoS) | T1498 |
| Defacement | T1491 |
Mitigation Tactics
To defend against Just Evil’s diverse range of tactics, it’s crucial to adopt a multi-layered approach that encompasses both proactive and reactive measures. Here’s how organizations can mitigate their attacks:
- DDoS Mitigation
- Recommended Defense: Deploy robust Distributed Denial of Service (DDoS) protection mechanisms. Solutions such as cloud-based DDoS protection (e.g., AWS Shield, Akamai Kona) can help absorb and mitigate traffic spikes. Additionally, load balancing and redundancy across geographically distributed servers can ensure continuous availability.
- How SOCRadar Helps: SOCRadar’s Attack Surface Management (ASM) continuously monitors your organization’s external assets, identifying exposed services and vulnerabilities that could be targeted in DDoS attacks. SOCRadar’s Threat Intelligence also provides real-time alerts on imminent DDoS campaigns, allowing proactive action before an attack escalates.
Additionally, organizations can also check their domain’s DoS Resilience for free in SOCRadar Labs.
- Website Defacement Prevention
- Recommended Defense: Secure web applications with Web Application Firewalls (WAF) and enforce strong access control measures. Regularly patch web-facing applications and use vulnerability scanning tools to identify and address security gaps. Employ Content Delivery Networks (CDNs) to help prevent unauthorized access.
- How SOCRadar Helps: SOCRadar’s Digital Risk Protection (DRP) monitors deep, dark, and surface web forums and channels to identify early indicators of planned defacement attacks targeting your organization. Paired with its Vulnerability Intelligence, SOCRadar enables real-time detection of web application flaws and supports rapid patching.
- Data Breach Prevention
- Recommended Defense: Use strong encryption for sensitive data, both at rest and in transit. Implement Multi-Factor Authentication (MFA) for all critical systems, and ensure strict access control policies. Regularly conduct phishing awareness training and enforce least-privilege access for employees.
- How SOCRadar Helps: SOCRadar’s Identity & Access Intelligence monitors the dark web for stolen credentials, providing alerts if your organization’s credentials appear in underground marketplaces. SOCRadar’s Phishing Domain Detection may also help mitigate phishing attacks, often precursors to data breaches.
- Exploitation of Public-Facing Applications
- Recommended Defense: Conduct regular vulnerability assessments and apply patches promptly, especially for high-risk internet-facing systems. Implement network segmentation to limit access to sensitive areas of the infrastructure.
- How SOCRadar Helps: SOCRadar’s Vulnerability Intelligence continuously scans your digital footprint for exploitable vulnerabilities and misconfigurations, ensuring that critical patches are applied before adversaries can exploit them. SOCRadar’s External Attack Surface Management (EASM) further identifies all exposed digital assets that could serve as potential entry points.
- Credential Compromise & Brute Force Protection
- Recommended Defense: Implement MFA for all logins and enforce strong password policies, using password managers to avoid weak or reused credentials. Utilize account lockout mechanisms after multiple failed login attempts to defend against brute force attacks.
- How SOCRadar Helps: SOCRadar’s Threat Hunting Module identifies brute force attempts targeting your infrastructure and provides insights into attack patterns. SOCRadar’s Dark Web Monitoring also proactively detects compromised credentials being sold or shared across underground forums.
Founder of Just Evil and KillNet Allegedly Killed in Drone Attack
A recent message shared on the Just Evil channel claims that KillMilk, the founder of KillNet and Just Evil, has reportedly died in a Ukrainian UAV attack. The message, forwarded from the Russian group UserSec, describes the circumstances of the attack, suggesting a fuel explosion caused by the drone strike. While this raises speculation about an information operation, it follows KillMilk’s recent threats against the US government and a prominent cybersecurity researcher. Additionally, Just Evil’s channel has been renamed to “DEAD.” However, there is no concrete evidence to support the claim, and the image shared below appears to be an old photo.
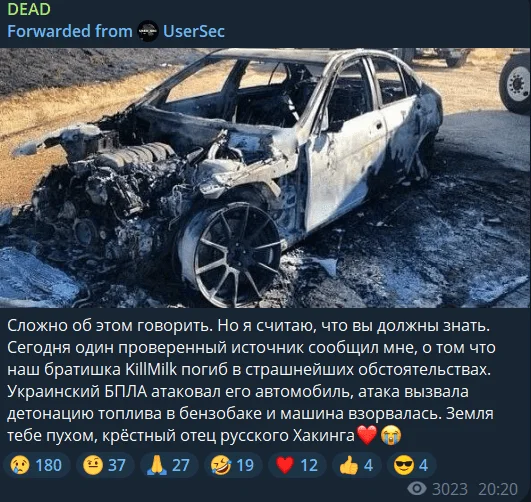
The Telegram post from the Just Evil group, now renamed to “DEAD,” shared a message claiming that KillMilk has died following a UAV attack.






































