Dark Web Profile: RA World
RA World is believed to be a rebranded iteration of the ransomware operation previously known as RA Group. This is because it employed the same extortion and encryption techniques, in addition to its name. A closer look at the victim lists shows that they were similar and in the same order, despite being distinct websites. Although it’s still unclear, it’s plausible that there are two distinct groups functioning under one roof. But most likely, RA World and RA Group are the same group.

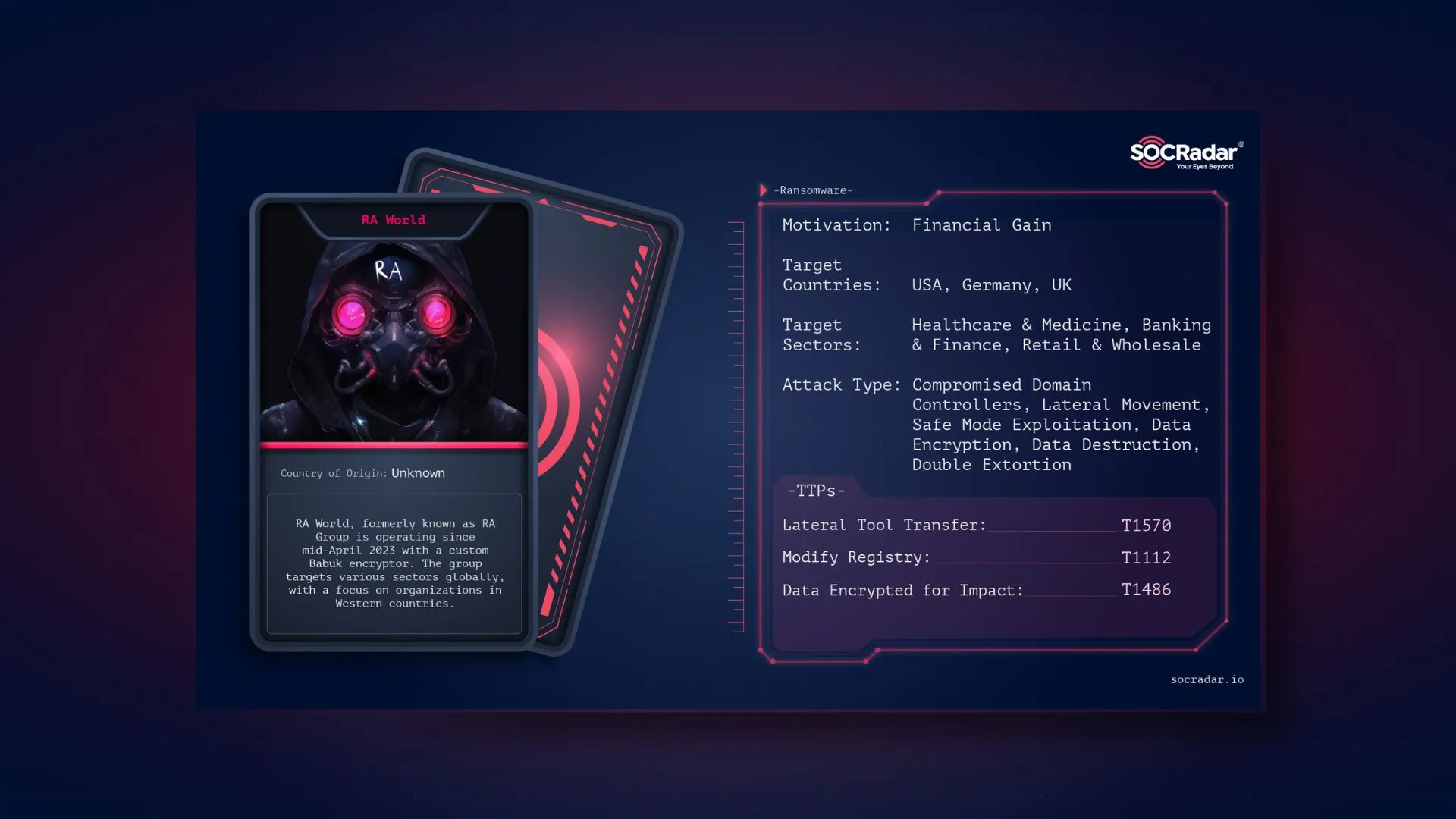
RA World threat actor card
In May 2023, RA World was reported for the first time. The claim was that RA started using a modified version of the Babuk encryptor that was disclosed in mid-April 2023. The encryption method is still the same, using Curve25519 to encrypt the key and the HC-128 eStream symmetrical cipher to encrypt files. Nonetheless, a few adjustments have been made. Both the title and the content of the ransom note are different, and the encrypted files have “.GAGUP” or “.RAWLD” extensions. Intermittent file encryption is a less evident but significant shift that is being used more and more to get around endpoint detection measures.
The victims of the gang come from a variety of backgrounds and places. Although there is no trend in the kinds of organizations attacked, the majority are situated in what are commonly referred to as “Western countries.” Notably, the Indo-Pacific area, which includes Taiwan, Thailand, South Korea, and India, is also home to a large number of attacks. Although there is no proof that these industries are explicitly targeted, a sizable portion work in the wholesale manufacturing and healthcare sectors.
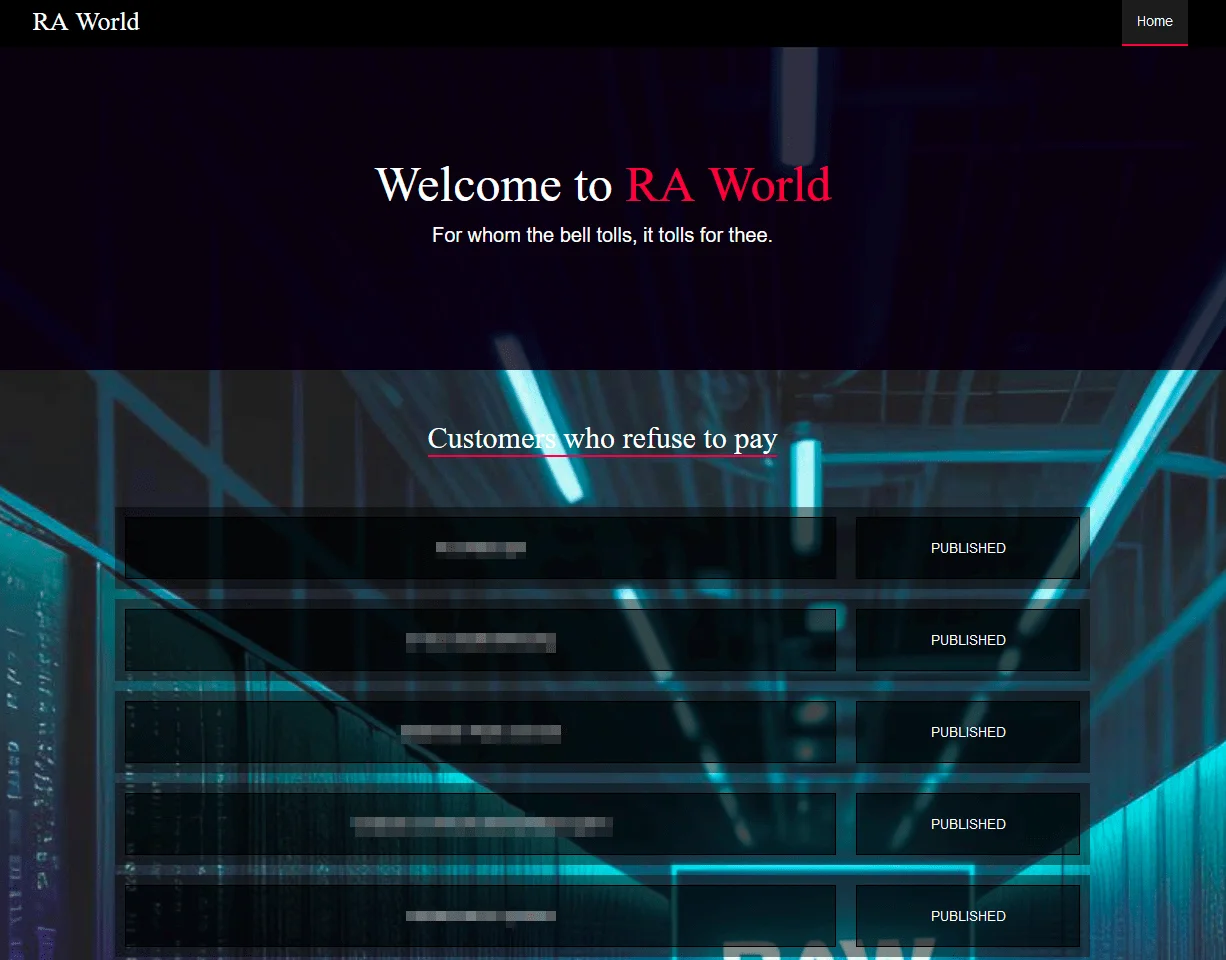
RA World’s TOR site showing its victims
Prior to delivering and running the ransomware for file encryption, the threat actor steals the data of the victims. In order to release stolen data from victims who do not cooperate with their requests, the gang runs websites which one of them is on the clearnet.
The malware adds the “.RAWLD” extension to the encrypted data after encrypting the victim’s files. The compromised systems are left with a ransom note, which describes the demands of the attackers and how they operate.
According to the note, victims can use Telegram or Tox to get in touch with the perpetrators. It warns that if communication is not established within three days, stolen files may be partially made public. The attackers escalate by distributing the stolen files in batches if no communication is received within seven days. By using deadlines and a multi-layered data-leak method, the group aims to maximize psychological strain on victims.
Explore SOCRadar’s Ransomware Intelligence module and gain comprehensive insights with detailed group profiles, MITRE Visualizer, and actionable IOCs. These insights will empower you to stay ahead of evolving threats and enhance your cybersecurity strategy.
SOCRadar’s Ransomware Intelligence module
Workings of RA World
1. Initial Access
- Method: According to TrendMicro, RA World obtains access by compromising domain controllers.
- Payload Delivery: In the Windows system, the malicious components are sent to the SYSVOL share path, which is commonly used for Group Policy Objects (GPOs). This enables the malware to use GPO to spread across numerous machines.
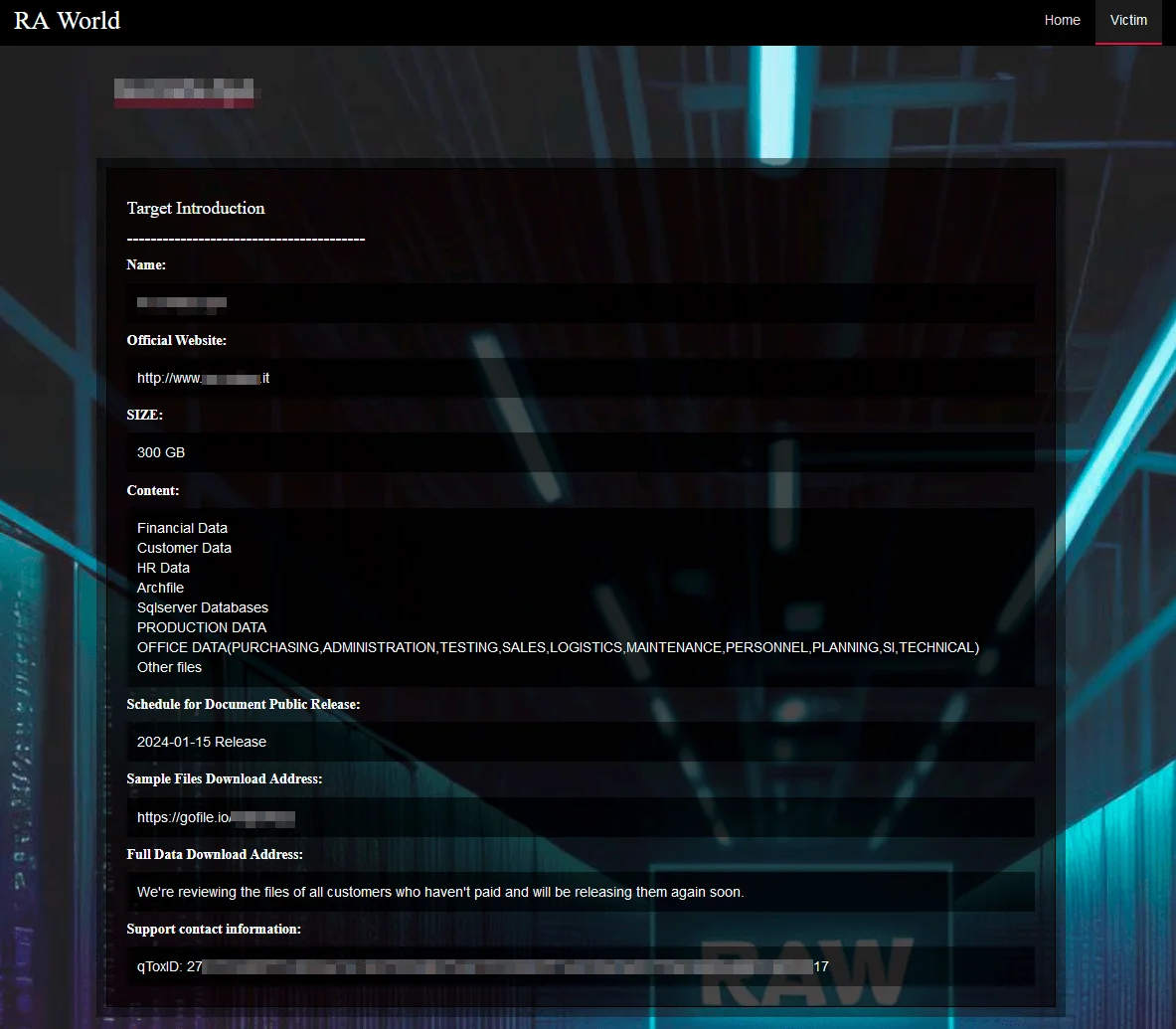
RA World victims page
2. Privilege Escalation
- Execution of Stage1.exe: PowerShell is used to run Stage1.exe. This implies that Group Policy settings might have been changed to permit the execution of PowerShell scripts.
- Manipulation of GPO: The attackers most likely changed Group Policy configurations or scripts to incorporate the malicious payload, which is subsequently run on the computers they have targeted as part of the GPO processing.
3. Lateral Movement
- Domain Controller Discovery: Stage1.exe verifies the domain name and locates each domain controller inside the domain.
- Checks for Prior Compromise: In the %WINDIR%Help directory, it looks for Finish.exe, which indicates a previous compromise, and Exclude.exe, which indicates the machine is protected from future infection.
- Copying Stage2.exe: It copies pay.txt and Stage2.exe from the hacked SYSVOL path to the local machine and runs Stage2.exe if Stage2.exe cannot be located. The ransomware payload is delivered by Stage2.exe.
4. Persistence
- Persistence Mechanism:
- Stage2.exe determines whether the machine is in safe mode. If not, Stage2.exe is set up to run as a service in Safe Mode with Networking and a service called MSOfficeRunOncelsls is created.
5. Defense Evasion
- Boot Configuration Data (BCD) Manipulation: Stage2.exe adjusts the system’s boot configuration to enable Safe Mode with Networking.
- Checking for Exclusions: The malware verifies that Exclude.exe and Finish.exe are not present, ensuring that the machine hasn’t been excluded from the attack.
6. Ransomware Payload Deployment
- Decryption of pay.txt: Stage2.exe decrypts pay.txt using Base64 and AES encryption, passing its contents to Stage3.exe, which is the actual ransomware payload.
- Cleanup and Registry Key Creation: After execution, the malware remnants are cleaned and registry keys are created.
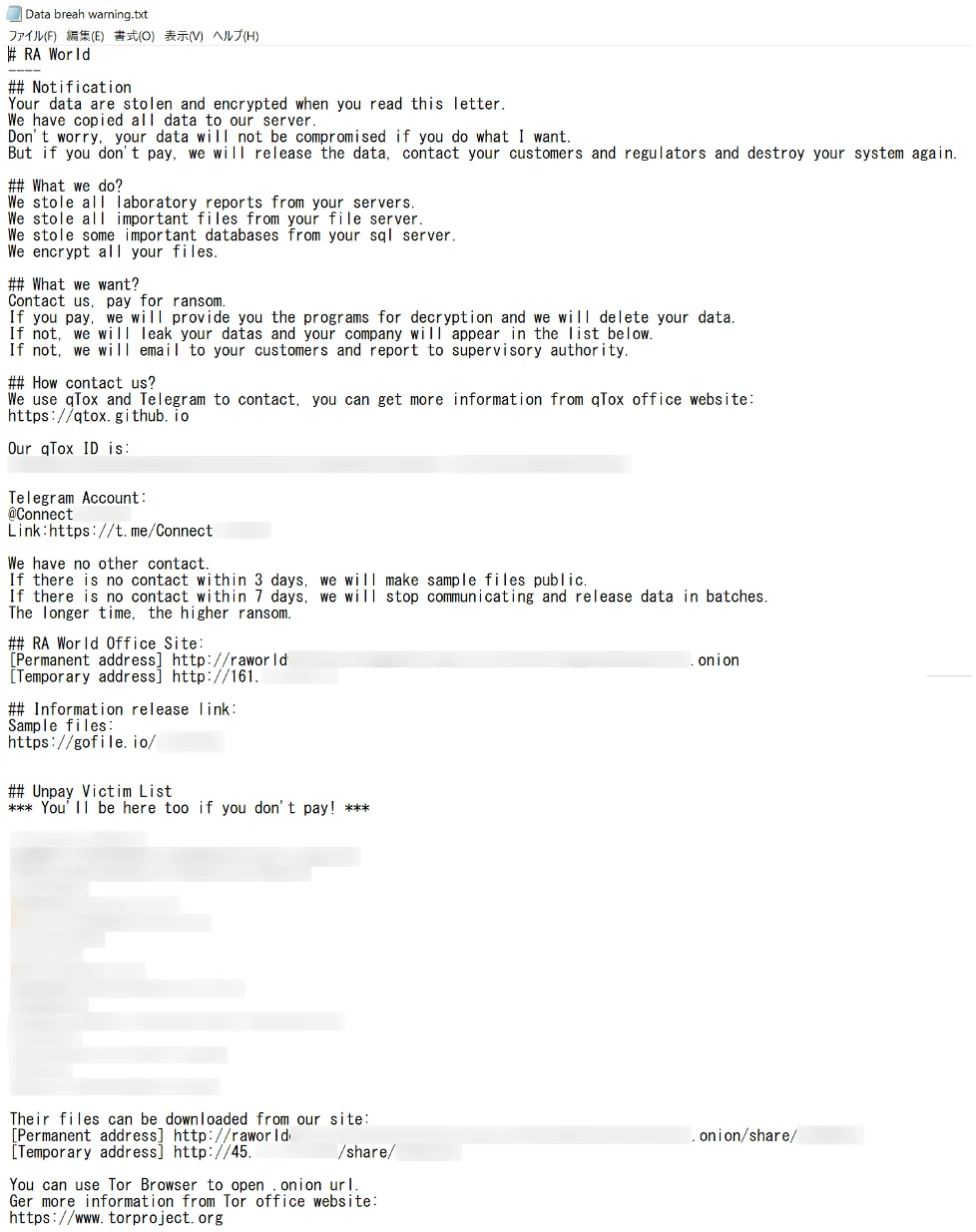
RA World ransom note, Source
7. Impact
- Ransomware Activation: Stage3.exe is deployed as the final ransomware payload.
- Final Payload Behavior: The ransomware uses code from the leaked Babuk ransomware.
- It drops a file Finish.exe, which contains the string “Hello, World.”
- It creates a mutex named “For whom the bell tolls, it tolls for thee,” which is associated with the Babuk ransomware.
Who are RA World’s Targets?
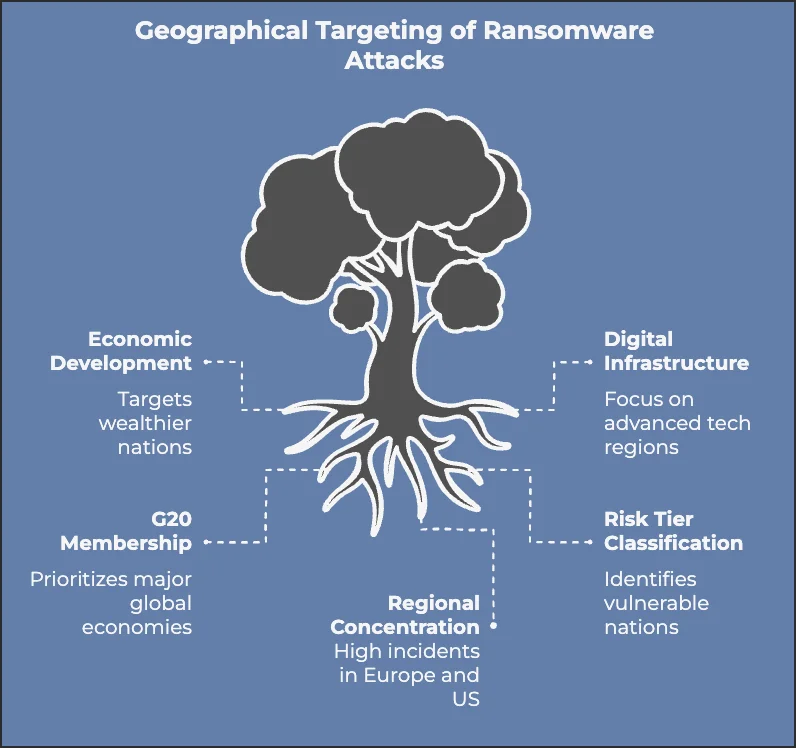
Summary of RA World’s targets
When we look at the diagram, we can state that these attacks are strategically focused on regions and organizations that offer the highest potential impact and financial return.
The targeting pattern is influenced by four key factors: economic development level (focusing on wealthier nations with greater capacity to pay ransoms), G20 membership (prioritizing major global economies), digital infrastructure sophistication (particularly in technologically advanced regions), and regional concentration (with a notable focus on Europe and the US).
The concentration of attacks in Europe and the US suggests these regions present an optimal combination of technological sophistication, economic capacity, and potential vulnerability that makes them particularly attractive targets.
Country Analysis of RA World’s Targets
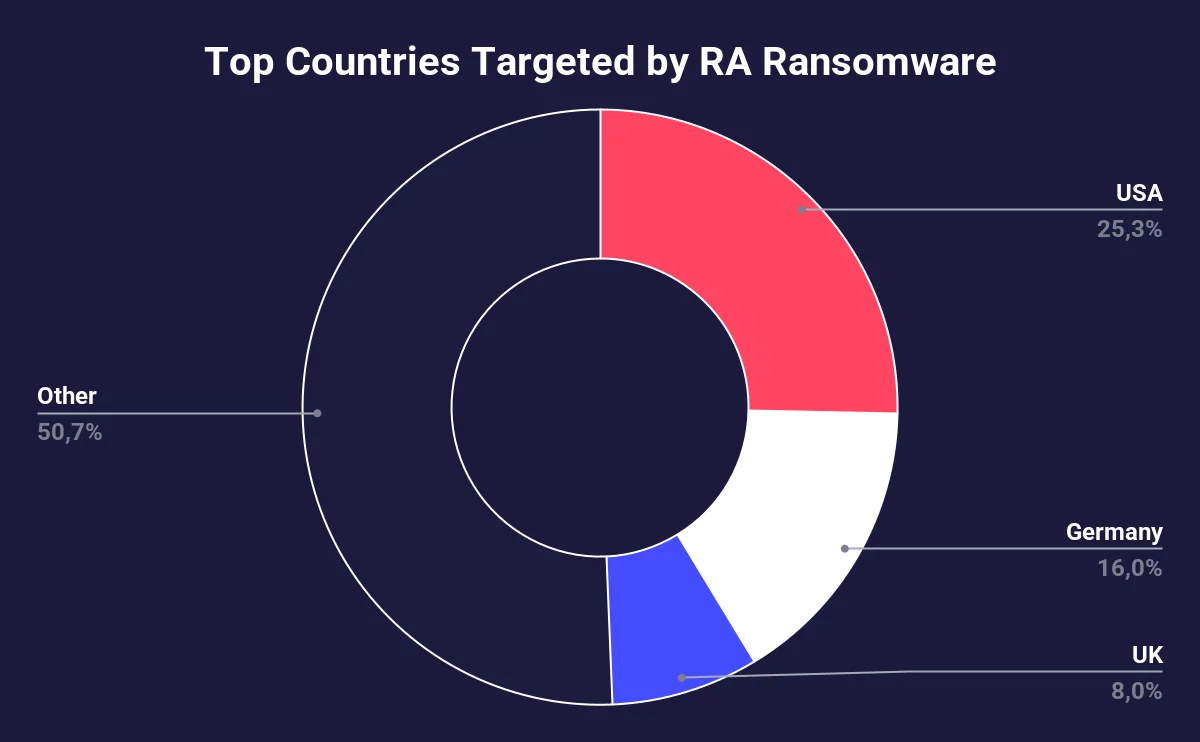
Most targeted countries by RA World
The analysis of RA World incidents highlights a pronounced geographical targeting pattern, underscoring strategic preferences towards economically developed nations.
The United States remains the primary target, accounting for 22.58% of attacks, while Europe collectively bears the highest burden, with 48.39% of incidents concentrated in this region. Germany (19.35%) and the United Kingdom (12.90%) are the most impacted European nations, reflecting a focus on G20 members with advanced digital infrastructures. East Asia also features prominently, comprising 22.58% of the total attacks, with Taiwan identified as a significant target (9.68%).
The data classifies affected nations into three distinct risk tiers:
- High-risk nations with over 10% of attacks (US, Germany, UK),
- Moderate-risk countries experiencing 5-10% of incidents (Taiwan, South Korea, India, France)
- Emerging targets with less than 5% each (Thailand, Poland, Netherlands, Mexico, Italy).
This distribution underscores the attackers’ calculated focus on regions with substantial economic and digital assets.
Industry Analysis of RA World’s Targets

Most targeted industries by RA World
Analyzing the distribution of RA World’s targets highlights a strategic focus on critical sectors, with Healthcare & Medicine emerging as the most targeted, accounting for 22.58% of all attacks. The financial sector follows closely, with Banking & Finance at 16.13% of incidents, further underscoring a deliberate targeting of industries handling sensitive and high-value data.
Supply chain-related sectors also face significant risks, collectively comprising 22.58% of attacks. This includes Retail & Wholesale (9.68%), Manufacturing (6.45%), and Distribution & Logistics (6.45%), reflecting the ransomware operators’ interest in disrupting interconnected systems.
The data classifies industries into three distinct risk tiers:
- High-risk sectors, with over 10% of incidents (Healthcare & Medicine, Banking & Finance);
- Moderate-risk sectors, experiencing 5–10% of attacks (Retail & Wholesale, Manufacturing, Insurance, Distribution & Logistics, Automotive);
- Emerging targets, each representing less than 5% of incidents (Real Estate & Housing, Professional Services, Maritime, IT, Government, Forestry & Lumber, Construction & Architecture, and Chemical).
This pattern emphasizes a calculated approach by threat actors, prioritizing industries critical to societal and economic stability.
SOCRadar’s Advanced Dark Web Monitoring equips organizations with vital insights into hidden threats targeting key industries such as finance, insurance, and information technology, which have faced significant risks over the past year. By providing real-time monitoring of underground chatter and sensitive data exposure, SOCRadar empowers proactive defenses against Dark Web threats.
SOCRadar’s Advanced Dark Web Monitoring
Conclusion
Combined with the rise of ransomware-as-a-service (RaaS), ransomware leaks significantly lower the technical barrier for cybercriminals, enabling even those with limited skills to create and deploy ransomware. One of the examples is RA World. Although the Babuk gang “retired” in 2021, the leak of their source code allowed multiple new threat groups, such as the RA World ransomware operators, to enter the ransomware landscape.
To reduce the risk of falling victim to ransomware attacks, organizations should follow these best practices:
- Grant administrative rights and access only when necessary.
- Keep security tools updated and perform regular scans.
- Protect critical data with routine backups to mitigate potential loss.
- Be cautious with emails and websites, avoiding suspicious attachments, links, and programs.
- Encourage users to report suspicious emails or files to security teams promptly.
- Provide regular training on social engineering risks and warning signs.
MITRE ATT&CK TTP Table
| Tactic | Technique | ID |
| Privilege Escalation | Group Policy Modification | T1484.001 |
| Lateral Movement | Lateral Tool Transfer | T1570 |
| Defense Evasion | Impair Defenses – Safe Mode Boot | T1562.009 |
| Indicator Removal | T1070 | |
| Indicator Removal – File Deletion | T1070.004 | |
| Modify Registry | T1112 | |
| Persistence | Create or Modify System Process – Windows Service | T1543.003 |
| Impact | Data Encrypted for Impact | T1486 |
| System Shutdown/Reboot | T1529 | |
| Data Destruction | T1485 |




































