
Dark Web Profile: Red Ransomware
On April 3, 2024, a newly discovered ransomware group surfaced as Senior Threat Analyst Rakesh Krishnan shed light. Known as Red CryptoApp, this group began its operations between February and March, coinciding with the dismantling or retreat of Lockbit and ALPHV.
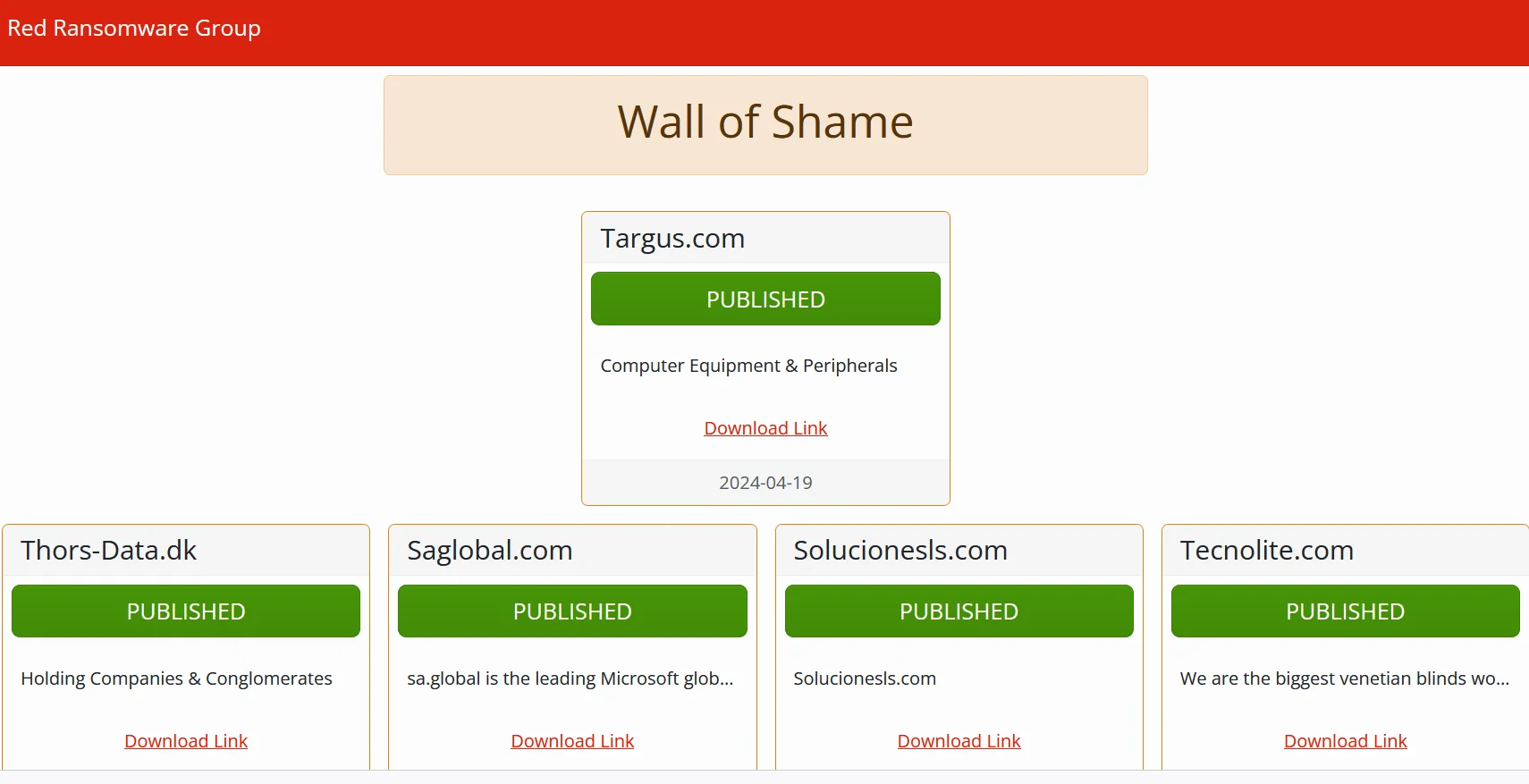
Red Ransomware Group’s Wall of Shame
Who is Red Ransomware
Red Ransomware or Red CryptoApp, a fresh ransomware group, surfaced in March 2024 and promptly revealed the data of 11 victims on its Data Leak Site (DLS), along with announcing an additional victim.
Their DLS debuted on March 29, 2024, titled “Wall of Shame.” Interestingly, the group chose to release the data of all 11 victims simultaneously on March 5, 2024, indicating a strategic delay in publishing the information. This tactic hints that Red CryptoApp probably have initiated their activities earlier and deliberately held off on disclosing the data for a greater effect.
Victimology
The victimology report for Red Ransomware reveals a narrow range of targets across a few sectors and countries. The majority of victims, mainly in the United States, represent industries such as Information Technology, Legal, Hospitality, Transportation, Manufacturing, Education, Electronics, and Retail.
This narrow targeting could indicate Red Ransomware’s focused approach, possibly because of lack of wide capabilities. The overview also notes a recent victim in the Retail sector from the United States, indicating that the group’s activities extend beyond its initial incident on March 5, 2024, showcasing ongoing threats posed by Red Ransomware.
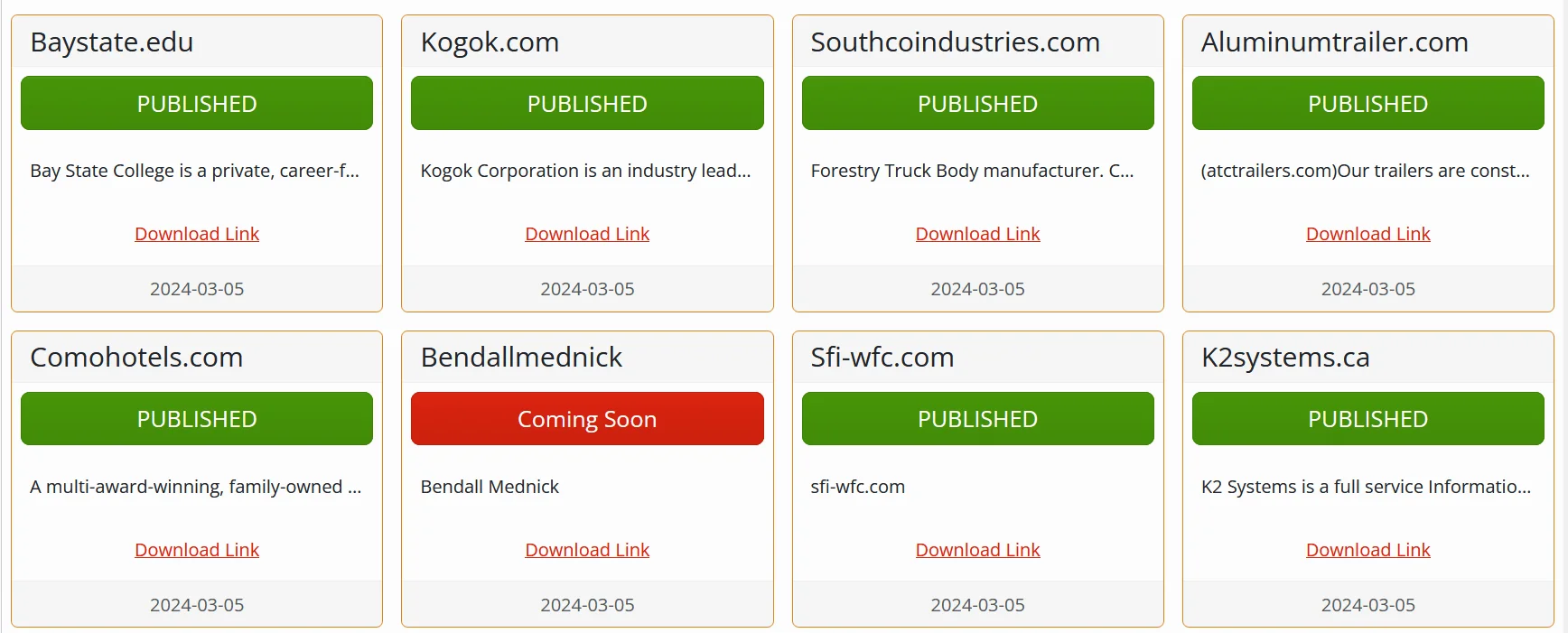
Wall of Shame – 2
The inclusion of victims from Canada, Singapore, Mexico, Spain, Italy, India and Denmark shows the narrow international reach of the Red Ransomware group. Most Western affiliated countries and heavy targeting US, also show a classical ransomware approach.
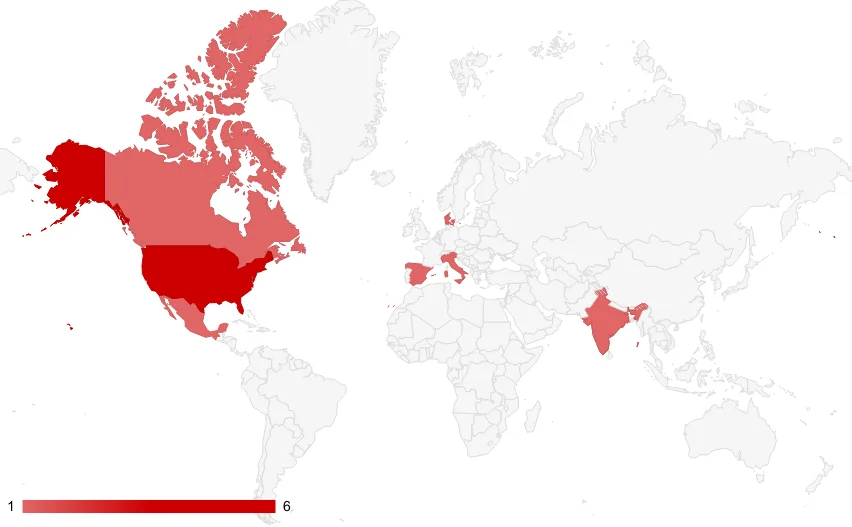
Targeted countries, most targets were US based
Modus Operandi
There isn’t detailed incident analysis for public research other than Rakesh Krishnan at Netenrich shared. The known facts are detailed below:
Infection Method:
Red Ransomware infects systems by exploiting vulnerabilities or using phishing emails with malicious attachments. Once a system is compromised, all files are modified with the .REDCryptoApp extension, rendering them inaccessible.
Target Selection:
- The group targets a wide range of industries, including Information Technology, Legal, Hospitality, Transportation, Manufacturing, Education, Electronics, and Retail. This broad targeting approach aims to maximize impact and financial gain.
- Timeline of Operations:
- Mid-February 2024: Initiation of targeting efforts, as indicated by the ransom note’s date of February 18, 2024.
- Early 2024: Intensification of operations, leading to the leakage of victim data in March 2024.
- April 19, 2024: Ongoing activities evidenced by a new victim in the Retail sector from the United States.
Victim Interaction:
- Red Ransomware provides victims with a unique TOR URL to facilitate negotiations. Victims access a login panel titled “Company Recovery,” where they input their unique “Hash” ID and solve a captcha to access the chat window.
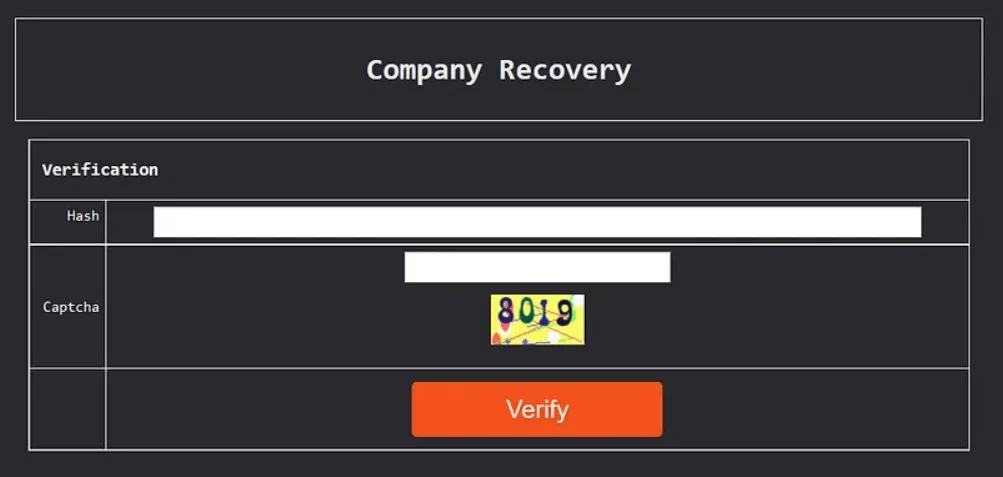
Victim contact interface (Medium)
- Chat Interface:
- Left Pane: Displays crucial victim information, including Victim Name, Negotiation Timeframe, Ransom Demand, Data Size, and Bitcoin Wallet Address.
- Right Pane: AI-generated text is utilized for communication, indicating the group’s adoption of AI tools.
- Ransom Demand:
- In one instance, a ransom demand of $5 million was observed, showcasing the group’s substantial financial demands.
Use of AI Tools:
- The use of AI-generated text in communications serves as concrete evidence of Red Ransomware’s utilization of AI tools, highlighting the evolving sophistication of ransomware operations.
Global Impact:
- Red Ransomware’s victims span across various countries, including the United States, Canada, Singapore, Mexico, Spain, and Denmark, demonstrating an international reach that is not that wide for now.
Latest Victim
Red Ransomware group featured Targus on its dark leak site “Wall of Shame,” displaying a red “Coming Soon” banner beneath the company’s name in early April and now its data has allegedly been published.
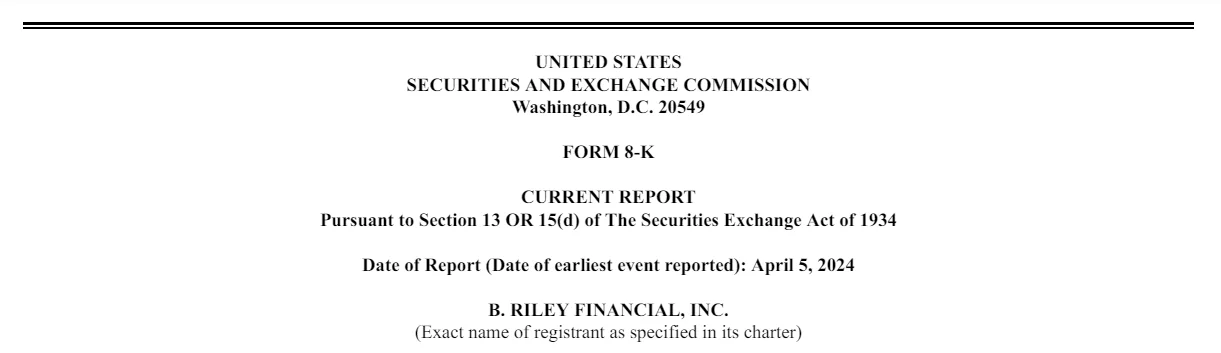
SEC Filing by the company
On April 8th, Targus’ parent company, B. Riley Financial, submitted an 8K breach disclosure to the US Securities and Exchange Commission (SEC). The Los Angeles-based financial investment firm, which acquired Targus in October 2022, revealed that an unauthorized threat actor gained access to certain file systems on April 5th.
Upon detection, Targus promptly shut down its systems to mitigate damage and isolate the attacker. B. Riley noted in the SEC disclosure that while this action temporarily disrupted business operations, external experts were already engaged in restoring the compromised systems.
The filing did not specify whether B. Riley was aware of the identity of the attackers or the duration of their presence within the network. Furthermore, details regarding the affected systems or the extent of data compromise were not disclosed in the filing.
But it has definitively shown that this small-scale and seemingly not very sophisticated group can cause real harm.
Conclusion
Red Ransomware’s modus operandi encompasses somewhat regular infection methods, narrow industry targeting and international operation. The integration of AI tools in victim interactions and combination of regular tactics underscores the group’s novice capabilities but still highlights the ongoing threat posed by ransomware groups in the cybersecurity landscape.
How Can SOCRadar Assist Against Ransomware?
SOCRadar offers a robust defense strategy tailored to counter the ransomware threat. Our proactive approach to threat monitoring and intelligence solutions is crafted to enhance your organization’s security posture effectively. Using our platform, you can actively monitor and analyze threat actors, gaining comprehensive insights into their tactics, targeted vulnerabilities, affiliations, and indicators of compromise. This proactive methodology enables you to anticipate and mitigate potential threats efficiently, safeguarding your critical assets.
SOCRadar Company Vulnerabilities, Ransomware Check
Moreover, our Attack Surface Management module, incorporating the Ransomware Check function, ensures continuous monitoring of all potential attack vectors. This guarantees real-time alerts regarding any suspicious activities related to ransomware. By staying ahead of these threats, you can swiftly respond and fortify your cybersecurity defenses, minimizing the risk posed by emerging threats.




































